Refer to the exhibits.
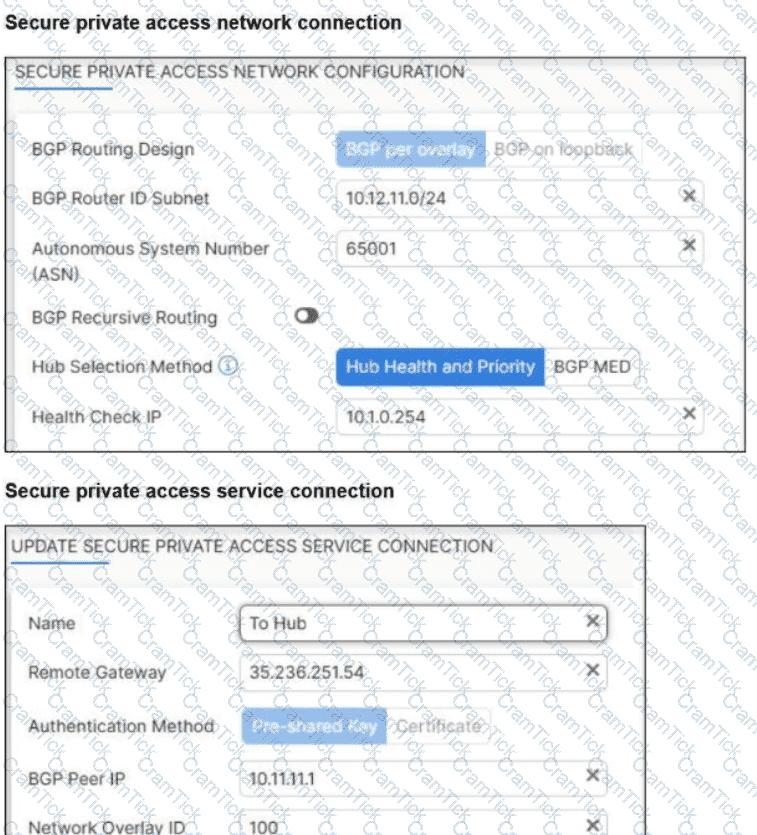
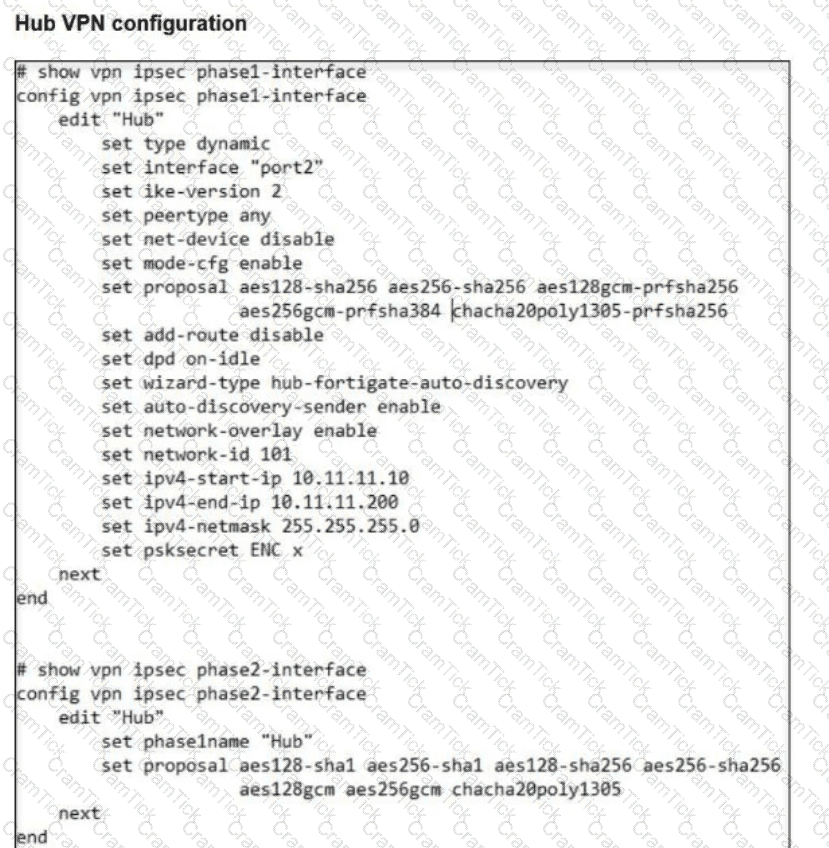
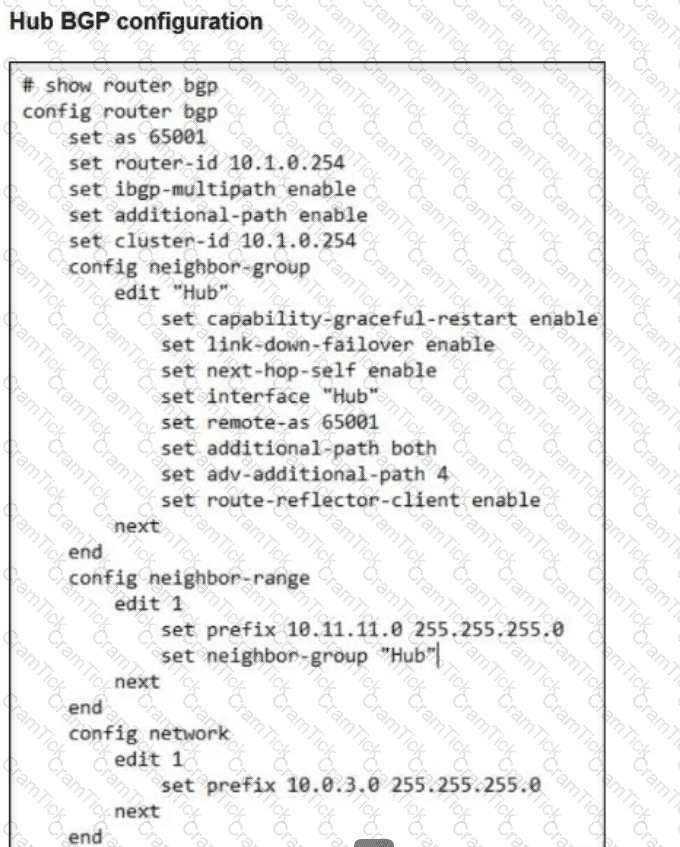

A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub.
The VPN tunnel does not establish.
Which configuration needs to be modified to bring the tunnel up?
Refer to the exhibit.
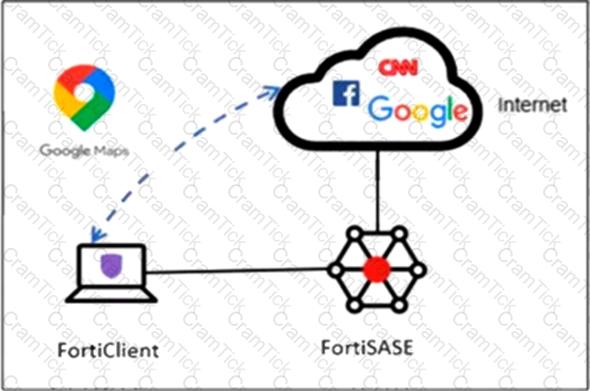
An organization must inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical interface.
Which configuration must you apply to achieve this requirement?
Which two purposes is the dedicated IP address used for in a FortiSASE deployment? (Choose two.)
What can be configured on FortiSASE as an additional layer of security for FortiClient registration?
Which two additional features does FortiClient integration provide with FortiSASE, when compared to secure web gateway (SWG) deployment? (Choose two.)
Which service is included in a secure access service edge (SASE) solution, but not in a security service edge (SSE) solution?
How can digital experience monitoring (DEM) on an endpoint assist in diagnosing connectivity and network issues?
An organization must block user attempts to log in to non-company resources while using Microsoft Office 365 to prevent users from accessing unapproved cloud resources.
Which FortiSASE feature can you implement to meet this requirement?
In a FortiSASE SD-WAN deployment with dual hubs, what are two benefits of assigning hubs with different priorities? (Choose two.)
An administrator must restrict endpoints from certain countries from connecting to FortiSASE.
Which configuration can achieve this?


