The NAT/ASPF log in the session log and the DPI traffic monitoring log provide a “binary” output technology for this type of log. The use of binary input output can greatly reduce the impact on system performance, but The binary form output needs to be configured with the elog log management system.
DDoS is an abnormal packet that an attacker sends a small amount of non-traffic traffic to the attack target (usually a server, such as DNS or WEB) through the network, so that the attacked server resolves the packet when the system crashes or the system is busy.
In the IDC room, a USG firewall can be used to divide into several virtual firewalls, and then the root firewall administrator generates a virtual firewall administrator to manage each virtual firewall.
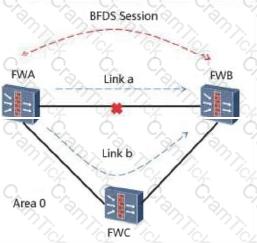
As shown in the following figure, the BFD for OSPF network is as follows: 1. OSPF is running between the three devices: FW_A, FW_B, and FW_C. The neighbors are in the FULL state. The association between BFD and OSPF is complete. BFD is complete. To establish a BFD session, the following instructions are correct?
The virtual firewall forwards multiple instances. The firewall has multiple routing tables and forwarding tables. The addresses are overlapped and are implemented on the same configuration interface. Users with configuration rights can configure and view all data.
The method of defending a FIN/RST flood attack is to perform a session check. The workflow is to discard the packet and then start the session check when the FIN/RST packet rate exceeds the threshold.
What actions will be performed when the firewall hot standby sends the active/standby switchover?
When an IPSec VPN is set up on both ends of the firewall, the security ACL rules of both ends are mirrored.
The management control information and service information of the out-of-band management interface are sent on the same channel.
Accessing the headquarters server through the IPSec VPN from the branch computer. The IPSec tunnel can be established normally, but the service is unreachable. What are the possible reasons?
112. The ESP only verifies the IP payload and can perform NAT traversal, but the ESP encrypts the Layer 4 port information and causes the PAT function to be unusable. This problem can be solved by using the IPSec transparent NAT function, which encapsulates the ESP packet in the UDP header and comes with the necessary port information to make the PAT work normally.
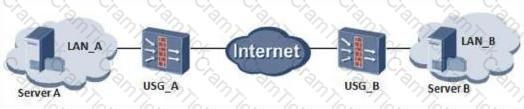
The network of an enterprise is as follows. At this time, server A cannot access the web service of server B. The administrator performs troubleshooting and finds that there is no problem in the routing mode of firewall A. The corresponding routing table has been established, but the firewall mode of firewall A is set. error. What is the method used by the administrator to troubleshoot the problem?
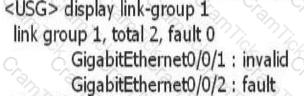
After the link-group is configured on the device, use the display link-group 1 command to obtain the following information. What information can I get?
The DHCP snooping function needs to maintain the binding table. What are the contents of the binding table?
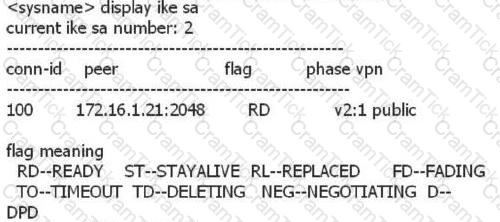
Run the display ike sa command to check the IKE SA information. The following statement is correct?
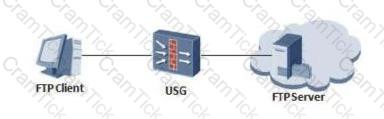
The FTP network diagram is as follows. The FTP server wants to use the 21000 control port to provide external FTP services. The FTP client cannot access the FTP server.
When configuring the USG hot standby, (assuming the backup group number is 1), the configuration command of the virtual address is correct?
What are the correct statements about the IP address scanning attack and prevention principles?
In the TCP/IP protocol, the TCP protocol provides a reliable connection service, which is implemented using a 3-way handshake. First handshake: When establishing a connection, the client sends a SYN packet (SYN=J) to the server and enters the SYN_SENT state, waiting for the server to confirm; the second handshake: the server receives the SYN packet and must send an ACK packet (ACK=1) To confirm the SYN packet of the client, and also send a SYN packet (SYN=K), that is, the SYN-ACK packet, the server enters the SYN_RCVD state; the third handshake: the client receives the SYN-ACK packet of the server. Send the acknowledgement packet ACK (SYN=2 ACK=3) to the server. After the packet is sent, the client and server enter the ESTABUSHED state and complete the handshake. Regarding the three parameters in the 3-way handshake process, which one is correct?
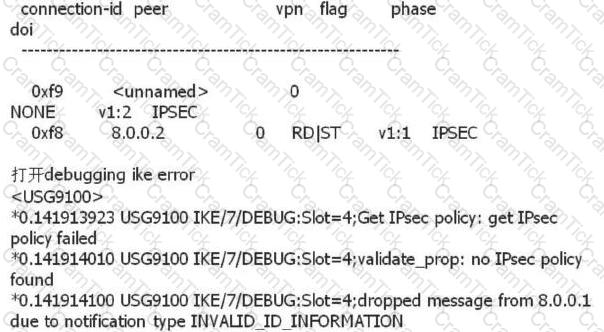
An administrator can view the IPSec status information and Debug information as follows. What is the most likely fault?
Which of the following protocol messages cannot be propagated in an IPSec tunnel by default?
The ip-link sends a probe packet to the specified IP address. By default, after 3 probe failures, the link to this IP address is considered faulty.
With regard to the Radius agreement, what are the following statements correct?
When using the SSL VPN client to start the network extension, the prompt "Connection gateway failed", what are the possible reasons for the failure?
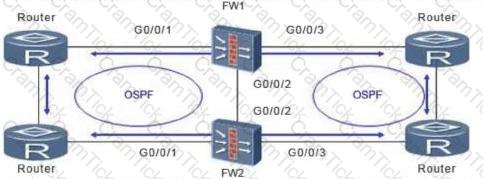
As shown in the figure, the firewall is dual-system hot standby. In this networking environment, all service interfaces of the firewall work in routing mode, and OSPF is configured on the upper and lower routers. Assume that the convergence time of OSPF is 30s after the fault is rectified. What is the best configuration for HRP preemption management?
Huawei Certified Network Professional HCNP | H12-721 Questions Answers | H12-721 Test Prep | HCNP-Security-CISN (Huawei Certified Network Professional - Constructing Infrastructure of Security Network) Questions PDF | H12-721 Online Exam | H12-721 Practice Test | H12-721 PDF | H12-721 Test Questions | H12-721 Study Material | H12-721 Exam Preparation | H12-721 Valid Dumps | H12-721 Real Questions | Huawei Certified Network Professional HCNP H12-721 Exam Questions


