After enabling the IP policy, some services are found to be unavailable. Which of the following may be caused by? (multiple choice)
Fage attack means that the original address and target address of TOP are both set to the IP address of a certain victim. This behavior will cause the victim to report to it.
SYN-ACK message is sent from the address, and this address sends back an ACK message and creates an empty connection, which causes the system resource board to occupy or target
The host crashed.
The security management system is only optional, and anti-virus software or anti-hacking technology can be a good defense against network threats.
Which of the following options are common reasons for IPS detection failure? (multiple choices)
Which of the following attacks are attacks against web servers? (multiple choices)
Regarding intrusion prevention, which of the following option descriptions is wrong
The analysis and processing capabilities of traditional firewalls at the application layer are weak, and they cannot correctly analyze malicious codes that are mixed in the flow of allowed application teaching: many Attacks or malicious behaviors often use the firewall's open application data flow to cause damage, causing application layer threats to penetrate the firewall
A True
B. False
Information security is the protection of information and information systems to prevent unauthorized access, use, leakage, interruption, modification, damage, and to improve
For confidentiality, integrity and availability. ,
Which of the following iterations is correct for the description of the management center?
Regarding scanning and snooping attacks, which of the following descriptions is wrong?
The application behavior control configuration file takes effect immediately after being referenced, without configuration submission.
USG6000V software logic architecture is divided into three planes: management plane, control plane and
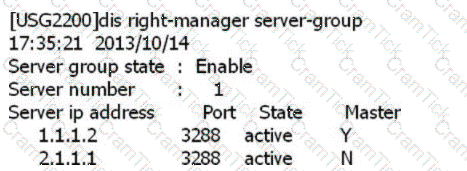
SACG query right-manager information as follows, which options are correct? (Select 2 answers)
What content can be filtered by the content filtering technology of Huawei USG6000 products?
Regarding the processing process of file overwhelming, which of the following statements is correct?
Viruses can damage computer systems. v Change and damage business data: spyware collects, uses, and disperses sensitive information of corporate employees.
These malicious pastoral software seriously disturb the normal business of the enterprise. Desktop anti-disease software can solve the problem of central virus and indirect software from the overall situation.
The most common form of child-like attack is to send a large number of seemingly legitimate packets to the target host through Flood, which ultimately leads to network bandwidth.
Or the equipment resources are exhausted. Which of the following options is not included in traffic attack packets?
When a data file hits the whitelist of the firewall's anti-virus module, the firewall will no longer perform virus detection on the file.
Which aspects of information security will be caused by unauthorized access? (multiple choice)
If the processing strategy for SMTP virus files is set to alert, which of the following options is correct?
Regarding the processing flow of file filtering, which of the following statements is wrong?
Regarding the description of intrusion detection technology, which of the following statements is correct?
An enterprise has 3 server, which is the most reasonable plan when deploy Policy Center system
planning?
In the security protection system of the cloud era, reforms need to be carried out in the three stages before, during and after the event, and a closed-loop continuous improvement should be formed.
And development. Which of the following key points should be done in "things"? (multiple choice)
HCIP-Security | H12-722_V3.0 Questions Answers | H12-722_V3.0 Test Prep | HCIP-Security-CSSN V3.0 Questions PDF | H12-722_V3.0 Online Exam | H12-722_V3.0 Practice Test | H12-722_V3.0 PDF | H12-722_V3.0 Test Questions | H12-722_V3.0 Study Material | H12-722_V3.0 Exam Preparation | H12-722_V3.0 Valid Dumps | H12-722_V3.0 Real Questions | HCIP-Security H12-722_V3.0 Exam Questions