Which statement is true about MySQL Enterprise Transparent Data Encryption (TDE)?
Which two statements are true about MySQL server multi-source replication? (Choose two.)
Which four are types of information stored in the MySQL data dictionary? (Choose four.)
Examine this command, which executes successfull
mysqlbackup --defaults-file=/backups/server-my.cnf --backup-dir=/backups/full
copy-back
Which statement is true about the copy-back process?
You must configure the MySQL command-line client to provide the highest level of trust and security when connecting to a remote MySQL Server.
Which value of --ssl-mode will do this?
Where is the default data directory located after installing MySQL using RPM on Oracle Linux 7?
Examine this snippet from the binary log file named binlog.000036:

The rental table was accidentally dropped, and you must recover the table.
You have restored the last backup, which corresponds to the start of the binlog.000036 binary log.
Which command will complete the recovery?
Which two statements are true about using backups of the binary log? (Choose two.)
Examine this statement, which executes successfully:
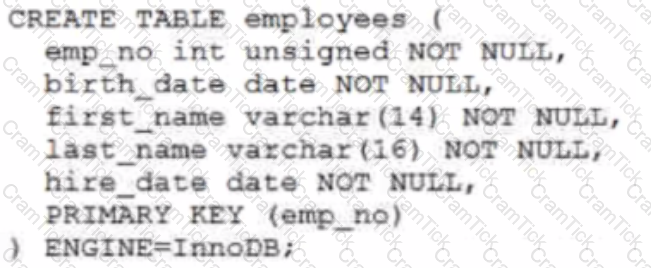
Now examine this query:
Which two statements can do this? (Choose two.)
Which two queries are examples of successful SQL injection attacks? (Choose two.)
There are five MySQL instances configured with a working group replication.
Examine the output of the group members:
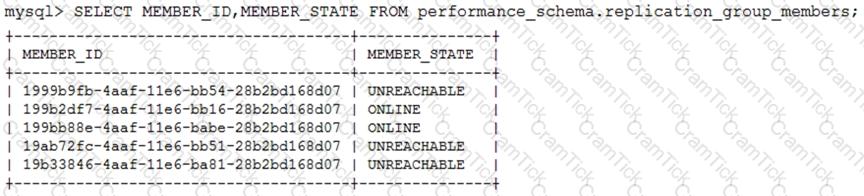
Which two statements are true about network partitioning in the cluster? (Choose two.)
You want to dump all databases with names that start with "db".
Which command will achieve this?
Your MySQL instance is capturing a huge amount of financial transactions every day in the finance database.
Company policy is to create a backup every day.
The main tables being updated are prefixed with transactions-.
These tables are archived into tables that are prefixed with archives- each month. mysqlbackup --optimistic-busy-tables="^finance\.transactions-.*" backup
Which optimization process best describes what happens with the redo logs?
You recently upgraded your MySQL installation to MySQL 8.0.
Examine this client error:

Which option will allow this client to connect to MySQL Server?
Your MySQL server is running on the Microsoft Windows platform.
Which three local connection protocols are available to you? (Choose three.)


