Joe, a user, notices someone use his computer while he was on break, Joe’s browser history reveals searches for websites he did not visit. The local print also has document in the output tray with someone else’s PII. Which of the following steps should Joe take to prevent unauthorized access of his account.
A Windows user is trying to print a large number of documents to a network printer, but the printer is no longer printing. A technician investigates and notices all the jobs are stuck in the print queue. Which of the following should the technician perform to resolve the issue?
Which of the following security tools can leverage the onboard TPM to protect data at rest?
After purchasing an Ultrabook. Ann. a home user, has a technician come to her home and install an operating system. Which of the following OS retaliation methods will the technician MOST likely use?
A technician is attempting to resolve an issue with a customer's smartphone. The customer can no longer unlock the smartphone due to an “incorrect pattern" message appearing onscreen,
The customer explains that the option to "make pattern visible” is unchecked in the security settings. The customer has also unsuccessfully tried to unlock the smartphone using a PIN. The
customer is certain the pattern and PIN being entered are both correct. The technician is unable to click the proper options onscreen to perform a reset, but can select it without issue using
the side buttons designed for volume and power. Which of the following describes the root cause of the issue?
A user notices recent print jobs are not printing to the local printer despite printing fine yesterday. There are no errors indicated on the taskbar printer icon. Which of the following actions should the user take FIRST?
A desktop technician is attempting to upgrade several machines to Windows 10. After releasing there is only one disc for the installation, the technician decides to upgrade over the network. Which of the following boot methods initiates such an upgrade?
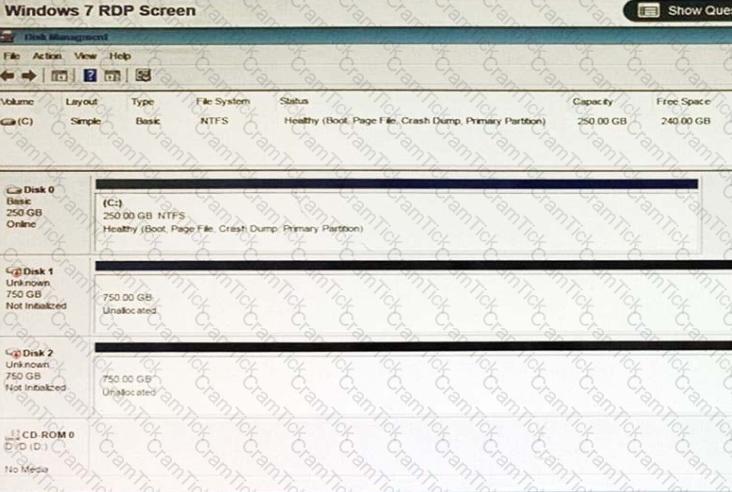
A user has installed two new drives in one of the computers in the computer lab and has been unable to format Disk1 from the command prompt.
The lab requires that Disk1 be a dynamic disk configured with two partitions. The first partition must be 256,000 MB in size and mapped to drive F. The second partition must be 512,000 MB in size and mapped to drive G.
The new partitions must be formatted to ensure that user’s files can be secured from other users and that the disk must be configured to account for future redundancy.
Make sure to maintain a consistent file system.
INSTRUCTIONS:
Conduct the necessary steps within the Disk Manager to accomplish these tasks.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A small office calls a technician to investigate some “invalid certificate” errors from a concerned user. The technician observes that whenever the user to access a secure website from the Windows desktop, this error is encountered. No other users in the office are experiencing this error. Which of the following should the technician do NEXT? (Choose two.)
Which of the following features has undergone the most significant changes from Windows 7 to Windows 10 and greatly simplified the operating system installation process?
Joe, a user who is travelling for business, reports that his mobile phone was getting approximately 35 Mbps for the first few days of his trip, but now it is only getting around 500 Kbps. Joe uses the device as a GPS to visit customers and as a hot-spot to check work email and watch movies online. Which of the following is the MOST likely cause of Joe’s slow data speeds?
A junior Linux system administrator needs to update system software. Which of the following shell commands would allow the administrator to gain the necessary permissions to update the software?
A technician is investigating the cause of a Windows 7 PC running very slow. While reviewing Task Manager, the technician finds one process is using more than 90% of the CPU. Outbound network traffic on port 25 Is very high, while Inbound network traffic Is low. Which of the following tasks should be done FIRST?
A technician logs on to a Linux computer and runs the following command:
ps -aux | grep vi
Which of the following MOST accurately describes the effect of the command?
A technician is troubleshooting a print issue on a Windows computer and want to disable the printer to test a theory, Which of the following should the technician use to accomplish this?
A client wants a technician to create a PC naming convention that will make the client’s PCs easier to track and identify while in use. Which of the following naming convention formats should the technician follow?
A user is attempting to install an application and receives an error stating there is not enough space to install the application. Which of the following did the user overlook?
A network administrator notifies a technician that the company is experiencing a DDoS attack. Several internal Windows PCs are the source of the traffic. The network administrator gives the technician the Windows computer names and states they be scanned and cleaned immediately. With which of the following types of infections are the PCs MOST likely infected? (Select two.)
A company has just experienced a data breach that affected all mobile devices. Which of the following would BEST secure access to users' mobile devices? (Select TWO).
A technician is installing Windows 7 64-bit OS on a VM but keeps getting errors. The specifications for the malware are:
Two 1GHz CPUs
2GB of memory
15GB hard drive
800x600 screen resolution
Which of the following should the technician do to resolve the problem?
Every time a user manually runs an antivirus scan, the workstation becomes unresponsive, and the user has to reboot A technician is dispatched and sees an antivirus pop-up in the system tray, indicating the computer is severely damaged, and a "click here" button to resolve it. There is a timer in the pop-up. counting down the time until the computer is no longer usable. Which of the following should the technician do NEXT?
A technician is installing a private PC in a public workspace. Which of the following password practices should the technician implement on the PC to secure network access?
A user is working with the command line interface on a Linux computer To show the contents of the current directory, which of the following commands should be used'
A technician Is troubleshooting network connectivity and receives the following output:
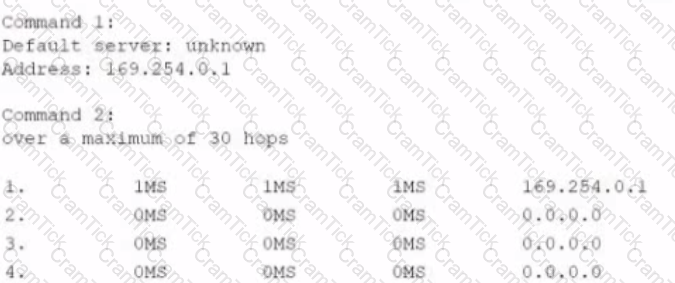
Which of the following tools is the technician MOST likely using? (Select TWO)
A user installed an application that now requires a license key to enable lull functionality. The user contacts support, and the technician decides to enter a license key in the software GUI on behalf of the user. Which of the following will support this task''
Joe, a user, did not receive emails over the weekend like he usually does. Productivity software is functioning properly. Joe never powers off his computer and typically leaves all applications open. No other users are reporting
email issues. Which of the following is MOST likely the cause of the issue?
Joe, a user, calls the help desk from a coffee shop while on a business trip to report the WiFi hot-spot on his phone is extremely slow. The technician runs a speed test from a laptop connected to the hot-spot and gets 200Kbps. Ann, Joe’s coworker with whom he is travelling, also has a hot-spot on her phone, and the speed test result on that hot-spot is 15Mbps. The technician checks the hot-spot settings on Joe’s phone and sees the following:

Which of the following is the MOST likely cause of the problem?
An end user set up a gaming server on an extra Windows PC. The user wants the PC to restart automatically during the night using the shutdown -r -£ command
Which of the following is the BEST tool to accomplish this?
A Computer Management
2B Task Scheduler b
C. Task Manager
D. Control Panel
A new company policy states that all end-user access to network resources will be controlled based on the users’ roles and responsibilities within the organization. Which of the following security concepts has the company just enabled?
A systems administrator needs to add security to the server room.
Which of the following would provide the BEST security for the room? (Choose two.)
A team needs to deploy a temporary server room at a site to provide support during construction.
Which of the following should they use at this site while setting up the server room?
A technician needs to edit a protected .dll file but cannot find the file in the System32 directory. Which of the following Control Panel utilities should the technician use?
An employee contacts the help desk because the battery in a company-provided smartphone lasts only a short period of time when the worker is in the office. Which of the following would MOST likely reduce this symptom? (Select TWO).
A customer’s computer is having difficulty opening programs and regularly receives error messages regarding low system resources. Which of the following performance settings changes would BEST help customer temporarily until upgrade can be made?
Which of the following types of scripts would be seen on the user end of a web page?
Which of the following operating systems utilizes the web browser named Edge, replacing its older browser software?
Which of the following are typically too dangerous to be disassembled by an in-house technician? (Choose two.)
A technician is troubleshooting an issue affecting all company laptops. All the laptops have exactly the same hardware. The screens present glitches every time the users move their mouse pointers over the screen. The technician discovers there was a recent OS update deployed throughout the company, which includes new versions for video drivers. Restarting the laptop in safe mode will not present the issue. Which of the following should the technician do NEXT?
A technician is acquiring hardware devices and setting up a computer lab with virtual desktops. The lab computers must have the ability to connect automatically to the remote session upon boot and must be started remotely. Which of the following solutions must the hardware be able to support? (Choose two.)
The IT department has installed new software in the folder C:\Program Files\Business Application\. Ann, a user, runs the business application and tries to save her work. When doing so, Ann receives the following error:
Cannot save file C: \Program Files\Business Application\file1.wrk – Access is denied.
Which of the following would be the MOST secure solution to this error?
An IT professional recently assisted Ann, a customer, with updating her password and regaining access to a
hijacked email account. Shortly afterward, Ann notices dozens of unwanted emails, thanking her for
subscribing to an organization’s mailing list. Which of the following should be performed to remove and prevent
any further emails from this organization?
A user calls the corporate help desk to report a malware detection message that is displayed on the user's screen Which of the following should the technician instruct the user to do FIRST?
A user is unable to open a document on a shared drive from a Linux workstation. Which of the following commands would help the user gain access to the document?
A user is surprised that a newly installed third-party smartphone application requires permissions to access the camera, location, and microphone. Unaware of a reason why permissions are needed for the application to function as advertised, the user contacts the help desk for assistance. Which of the following should the help desk team recommend the user do in this situation?
A technician is having issues with the WiFi connection while working on a Mac. The technician wants to check which SSID the computer is connected to and some statistics about the connection. Which of the following terminal commands should the technician use?
A technician is working on a desktop computer that is not performing as expected. Program windows sometimes open and close without user intervention. Windows cannot check for OS updates, and some websites are not accessible. Which of the following tasks should the technician perform FIRST?
A user’s desktop will not run an accounting program. The program’s splash screen pops up, and then the software freezes. Which of the following actions should a technician take FIRST to help resolve the issue?
A user's PC has become infected with malware that has a known remediation, Which of the fallowing would MOST likely prevent this from happening again?
A technician submitted a change control request to upgrade the firmware on all company switches at the same time, during off hours, and through automation. Which of the following change management documents is MOST important to create to ensure the upgrade will not adversely affect the business?
A technician receives a call from an end user in the human resources department who needs to load an older stand-alone application on a computer to retrieve employee information. The technician explains the application can be run in compatibility mode, but it will need to be removed as soon as the user obtains the required information. Which of the following BEST describes the technician’s concern with loading this application on the user’s computer?
A user has changed the MAC address of a laptop to gain access to a network. This is an instance of:
A customer built a computer with the following specifications:
Single hexa-core processor
8GB DDR4 memory
256GB SSD drive
Built-in graphics card
32-bit Windows OS
Audio editing software
The computer seems to be working, but the OS reports only 3.5GB of RAM is available. Which of the following
would correct the issue?
Ann, a customer, calls a technician and states that she is very concerned about the privacy of her home computer and the security of her home network while browsing the Internet. Which of the following would the technician MOST likely discuss with Ann to educate her on security concepts addressing her concerns? (Choose two.)
Which of the following variable types should be used to store the data “Chicago” within a script or code?
A company needs to destroy several SSDs that contain sensitive information. Which of the following methods
is BEST suited for the total destruction of the SSDs?
Which of the following Windows versions introduced using applications in the Metro interface?
Which of the following steps should a technician perform when the Included Windows driver for a video card does not have the needed features?
Which of the following Microsoft operating systems comes with a PDF printer as part of the OS functionality?
After connecting to the corporate VPN, a user's workstation is no longer able to browse Internet websites A technician discovers launching a different web browser on the same computer reaches the websites correctly Which of the following should the technician do NEXT?
A technician is troubleshooting a network connectivity issue on a Linux workstation. Which of the following commands would help the technician gain information about the network settings on the machine?
When a computer accesses an HTTPS website, which of the following describes how the browser determines the authenticity of the remote site?
Which of the following is protected data that can be found in a medical record?
Joe, a technician, is installing a new internet connection at a customer’s site. While performing the installation, joe takes a cell from his manager and then responds to a social request. The customer become frustrated and asks and asks to speak with a supervisor. Which of the following should Joe do NEXT?
Ann. a network engineer is performing an after-hours upgrade on a network switch During the activity. Ann notices an unrelated setting she believes is misconfigured She decides to change the setting during the upgrade which causes an outage. Which of the following change management practices would MOST likely have prevented this outage?
A system administrator needs to submit a change request to the change control board for review and approved. The system administrator will be upgrading the production servers to the latest OS. Which of the following must the administrator include in the change request before the change control board will approve the request? (Select THREE.)
A remote user has reported a suspicious pop-up. and a technician is troubleshooting the user's laptop. The technician needs to connect securely to the computer to view the user's screen and investigate the issue Which of the following should the technician use?
Joe. a user, is receiving automated replies but does not remember sending any emails to those recipients He checks the sent items folder and sees email messages he did not send Which of the following would be the BEST way to resolve this issue?
A customer reports that a phone’s battery does not last as long as expected. Which of the following would be the BEST way to resolve the short battery life issue and maintain phone functionally?
Joe, a technician, has his daily plans forwarded to him by his supervisor. Upon arrival to the external to the second support call of the day, Joe realizes the issue will require much more time than initially scheduled, and several support calls will not be completed. Which of the following would be the appropriate action for Joe?
A user’s smartphone is experiencing limited bandwidth when at home. The user reports to a technician that the device functions properly when at work or in the car. Which of the following troubleshooting steps should the technician take NEXT?
A user calls a technician to report issues when logging in to a vendor's website. The technician is able to log in successfully before going to the office. However, the technician is unable to log in when in the user's office. The user also informs the technician of strange pop-up notifications. Which of the following are the MOST likely causes of these issues? (Select TWO).
A technician is investigating connectivity issues over the corporate network. The technician attempts to Telnet into an access point in the break room, which is labeled AP-1. but is unable to proceed any further or authenticate Which of the following commands will be MOST beneficial in determining the connectivity issues?
A technician is setting up a new corporate wireless network. One of the following requirements for the network is that connections must only be allowed for current account without giving a wireless key. Which of the following should the technician use?
A computer becomes infected with malware, which manages to steal all credentials stored on the PC. The malware then uses elevated credentials to infect all other PCs at the site. Management asks the IT staff to take action to prevent this from reoccurring. Which of the following would BEST accomplish this goal?
A user’s Windows laptop has become consistently slower over time. The technician checks the CPU utilization and sees that it varies between 95% and 100%. After the technician closes some running applications, the
CPU utilization drops to approximately 20%, and the laptop runs much faster. The next day the same user calls again with the same problem. Which of the following is a tool the technician can use to resolve the issue?
Which of the following would MOST likely be used in secure client-server communication?
A technician is updating a Linux server that had been in storage. After booting into single-user mode, a command is issued that displays the technician's current location in the filesystem. Which of the following commands was issued?
A network support technician takes a call from an office manager who wants to change the wireless security
key on the access point in that particular office. The office manager explains that a label on the access point
indicates it has an IP address of 10.0.100.2. Which of the following should the technician use to connect
securely to the access point to make the change?
Which of the following OS installation types would a technician use for multiple workstations at the same time?
Which of the following uses a remote access server to forward a user's logon password to an authentication server, allowing or denying access to a system?
A user wants to use a computer to access files on a nearby laptop Both computers can ping each other, but the user is unable to access any remote files. Which of the following settings should the user change to resolve the issue?
Joe, a technician, recently installed drivers for a webcam, but he is now experiencing issues when trying to operate it. Which of the following should Joe check NEXT to troubleshoot the issue?
Several users at an office have noticed their computers have been behaving erratically over the past hour. A technician suspects there may be a network worm or a hardware failure because all the affected computers were purchased together. Which of the following should the technician perform FIRST?
While installing a hard drive in a server, the administrator installs an extra physical hard disk Which of the following technologies will allow the administrator to extend an existing volume onto the extra disk?
A user receives an email on a company smartphone. When trying to open the email, the user gets a message stating the email is encrypted, and the user cannot open it. The user forwards the email to a personal email account and receives the same message. The user calls the IT department to ask for help. To decrypt the message, the technician tells the user to contact the sender of the message to be able to exchange:
A technician is alerted to a virus on a PC. The technician isolates the PC from the network. After verifying there are no other infected PCs on the network, which of the following is the SAFEST method for the technician to use to clean the infected PC?
A technician is monitoring a network and notices an outage has occurred that could potentially cause a major disruption to the business workflow. Which of the following should the technician do NEXT? !•: A. Identify the issue and its impact to the business.
B. Report the incident to the proper teams or management for awareness.
C. Start a root cause analysts and create documentation
D. Create an action plan and implement the solution
A customer wants to format a 4TB external drive with a filesystem that is compatible with both Windows and
Linux OSs.
Which of the following should the technician suggest the customer use?
After receiving a replacement smartphone. a corporate user is able to open some emails but is unable to open encrypted emails. Which of the following troubleshooting steps should a technician take NEXT?
A technician installed a new video card into a computer but did not connect the second monitor. When the technician boots the computer, it shows a blue screen during boot and automatically restarts.
The technician is able to boot into safe mode successfully. Which of the following would MOST. likely resolve the issue?
A user calls the help desk to report an issue accessing a new application on a Windows PC When the user tries to launch the application, an error message appears and then quietly disappears before the user can read it, Which of the following protocols would a technician MOST likely use to help diagnose this issue?
A customer calls the help desk to report a computer that has become infected. While speaking with the technician, there is an audible siren coming from the computer. The browser window is flashing
red, stating the computer is infected, and then the computer becomes unresponsive. A technician is dispatched to determine a solution. After a reboot and a virus scan, the technician is unable to find
any issues, When the customer opens the browser, the homepage redirects to the same page, and the same issue occurs. Which of the following should be the NEXT step to resolve the issue?
Which of the following application installation methods requires the use of a valid IP address?
A technician is setting up a media server and wireless router that can stream video files to portable devices. The technician was asked to configure the system so the videos can be accessed by devices outside the LAN. Which of the following does the technician MOST likely need to configure to allow access?
A+ | 220-1002 Questions Answers | 220-1002 Test Prep | CompTIA A+ Certification Exam: Core 2 Questions PDF | 220-1002 Online Exam | 220-1002 Practice Test | 220-1002 PDF | 220-1002 Test Questions | 220-1002 Study Material | 220-1002 Exam Preparation | 220-1002 Valid Dumps | 220-1002 Real Questions | A+ 220-1002 Exam Questions