Which type of control minimizes the impact of an attack and restores normal operations as quickly as possible?
The method of distributing network traffic equally across a pool of resources is called:
Duke would like to restrict users from accessing a list of prohibited websites while connected to his network. Which control would BEST achieve his objective?
An attack in which an attacker listens passively to the authentication protocol to capture information that can be used in a subsequent active attack to masquerade as the claimant is known as:
A collection of actions that must be followed to complete a task or process in accordance with a set of rules is known as:
Shaun is planning to protect data in all states (at rest, in motion, and in use), defending against data leakage. What is the BEST solution to implement?
Which aspect of cybersecurity is MOST impacted by Distributed Denial of Service (DDoS) attacks?
Embedded systems and network-enabled devices that communicate with the Internet are:
A hacker intercepts network traffic to steal login credentials. Which OSI layer is being attacked?
The magnitude of harm expected from unauthorized disclosure, modification, destruction, or loss of information is known as:
Which technology should be implemented to increase the work effort required for buffer overflow attacks?
Removing the design belief that the network has any trusted space. Security is managed at each possible level, representing the most granular asset. Microsegmentation of workloads is a tool of the model.
A weighted factor based on the probability that a threat will exploit a vulnerability is called:
Which provides integrity services that allow a recipient to verify that a message has not been altered?
An employee launched a privilege escalation attack to gain root access on one of the organization’s database servers. The employee has an authorized user account on the server. What log file would MOST likely contain relevant information?
Finance Server and Transaction Server have restored their original facility after a disaster. What should be moved in FIRST?
What is a security token used to authenticate a user to a web application, typically after they log in?
The common term for systems that control temperature and humidity in a data center is:
_______ are virtual separations within a switch used mainly to limit broadcast traffic.
Which term describes a communication tunnel that provides point-to-point transmission of authentication and data traffic over an untrusted network?
Configuration settings or parameters stored as data and managed through a GUI are examples of:
An agreement between a cloud service provider and a customer based on cloud-specific terms is called:
John is concerned about a possible conflict of interest from a consulting side job. Which source should he consult?
A CISO documents a policy establishing acceptable cloud use for all staff. This is an example of:
The right of an individual to control the distribution of information about themselves is:
The prevention of authorized access to resources or delaying time-critical operations is known as:
Which type of database combines related records and fields into a logical tree structure?
Which zero-trust component breaks LANs into very small, localized security zones?
Which type of software testing focuses on examining the source code for vulnerabilities and security issues?
An unknown person obtains unauthorized access to the company file system. This is an example of:
Which of the following is NOT one of the three main components of an SQL database?
Which principle states that users should have access only to the specific data and resources needed to perform required tasks?
A set of rules that everyone must comply with and that usually carry monetary penalties for noncompliance are:
During an ISC2 CC exam, you observe another candidate cheating. What should you do?
Which element of the security policy framework includes recommendations that are NOT binding?
A security event in which an intruder gains or attempts unauthorized access to a system is called:
A DLP solution should be deployed so it can inspect all forms of data leaving the organization, including:
Which is the most efficient and effective way to test a business continuity plan?
A ________ creates an encrypted tunnel to protect your personal data and communications.
After an earthquake disrupts business operations, which document contains the reactive procedures required to return business to normal operations?
Which protocol would be most suitable to fulfill the secure communication requirements between clients and the server for a company deploying a new application?
A hacker launches a specific attack to exploit a known vulnerability. This is called:
An employee unintentionally shares confidential information with an unauthorized party. What term best describes this?
The DevOps team has updated the application source code. Tom discovered that many unauthorized changes have been made. What is the BEST control Tom can implement to prevent a recurrence of this problem?
The harmonization of automated computing tasks into reusable workflows is called:
A security event does not affect confidentiality, integrity, or availability. What is it?
The prevention of authorized access to resources or the delaying of time-critical operations is known as:
Which approach involves a continuous cycle of identifying, assessing, prioritizing, and mitigating cybersecurity risks?
Which one of the following controls is NOT particularly effective against the insider threat?
An attack in which a user authenticated to a server unknowingly invokes unwanted actions after visiting a malicious website is known as:
A one-way spinning door or barrier that allows only one person at a time to enter a building or area.
Exhibit.
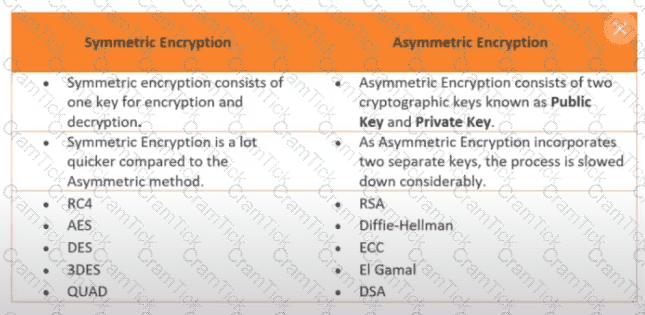
How many keys would be required to support 50 users in an asymmetric cryptography system?
Which access control method uses attributes and rules evaluated by a central Policy Decision Point (PDP)?