The new Chief Technology Officer (CTO) is seeking recommendations for network monitoring services for the local intranet. The CTO would like the capability to monitor all traffic to and from the gateway, as well as the capability to block certain content. Which of the following recommendations would meet the needs of the organization?
Law enforcement has contacted a corporation’s legal counsel because correlated data from a breach shows the organization as the common denominator from all indicators of compromise. An employee overhears the conversation between legal counsel and law enforcement, and then posts a comment about it on social media. The media then starts contacting other employees about the breach. Which of the following steps should be taken to prevent further disclosure of information about the breach?
A cybersecurity analyst has received the laptop of a user who recently left the company. The analyst types ‘history’ into the prompt, and sees this line of code in the latest bash history:

This concerns the analyst because this subnet should not be known to users within the company. Which of the following describes what this code has done on the network?
An analyst has initiated an assessment of an organization’s security posture. As a part of this review, the analyst would like to determine how much information about the organization is exposed externally. Which of the following techniques would BEST help the analyst accomplish this goal? (Select two.)
After scanning the main company’s website with the OWASP ZAP tool, a cybersecurity analyst is reviewing the following warning:
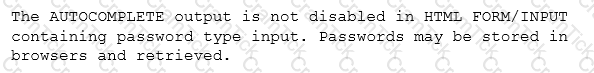
The analyst reviews a snippet of the offending code:
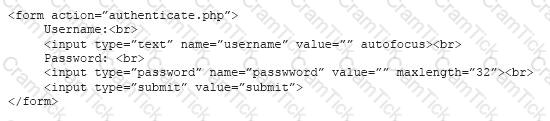
Which of the following is the BEST course of action based on the above warning and code snippet?
Which of the following remediation strategies are MOST effective in reducing the risk of a network-based compromise of embedded ICS? (Select two.)
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancement to the company’s cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices. Which of the following industry references is appropriate to accomplish this?
The primary difference in concern between remediating identified vulnerabilities found in general-purpose IT network servers and that of SCADA systems is that:
A software patch has been released to remove vulnerabilities from company’s software. A security analyst has been tasked with testing the software to ensure the vulnerabilities have been remediated and the application is still functioning properly. Which of the following tests should be performed NEXT?
Following a recent security breach, a post-mortem was done to analyze the driving factors behind the breach. The cybersecurity analysis discussed potential impacts, mitigations, and remediations based on current events and emerging threat vectors tailored to specific stakeholders. Which of the following is this considered to be?
An analyst has noticed unusual activities in the SIEM to a .cn domain name. Which of the following should the analyst use to identify the content of the traffic?
Which of the following has the GREATEST impact to the data retention policies of an organization?
A small company Is publishing a new web application to receive customer feedback related to Its products. The web server will only host a form to receive the customer feedback and store It In a local database. The web server is placed In a DMZ network, and the web service and filesystem have been hardened. However, the cybersecurity analyst discovers data from the database can be mined from over the Internet. Which of the following should the cybersecurity analyst recommend be done to provide temporary mitigation from unauthorized access to the database?
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Select two.)
Various devices are connecting and authenticating to a single evil twin within the network. Which of the following are MOST likely being targeted?
When reviewing network traffic, a security analyst detects suspicious activity:
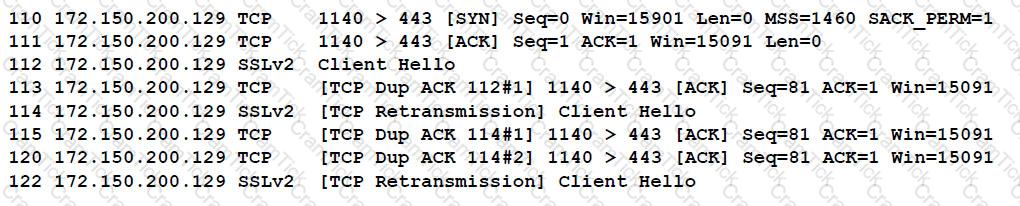
Based on the log above, which of the following vulnerability attacks is occurring?
A cybersecurity analyst is reviewing log data and sees the output below:
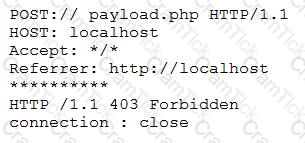
Which of the following technologies MOST likely generated this log?
A cybersecurity analyst is hired to review the security posture of a company. The cybersecurity analyst notices a very high network bandwidth consumption due to SYN floods from a small number of IP addresses.
Which of the following would be the BEST action to take to support incident response?
An organization is attempting to harden its web servers and reduce the information that might be disclosed by potential attackers. A security analyst is reviewing vulnerability scan results from a recent web server scan.
Portions of the scan results are shown below:
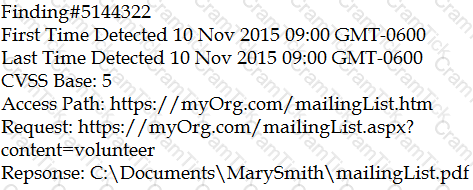
Which of the following lines indicates information disclosure about the host that needs to be remediated?
A technician receives the following security alert from the firewall’s automated system:
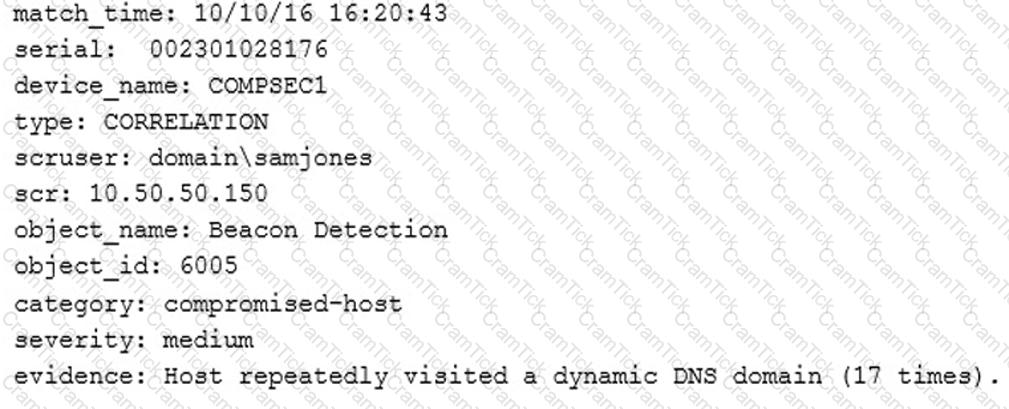
After reviewing the alert, which of the following is the BEST analysis?
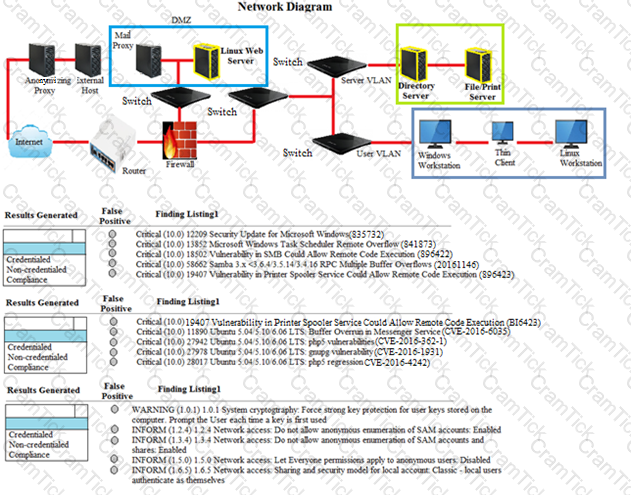
A security analyst performs various types of vulnerability scans.
Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
During which of the following NIST risk management framework steps would an information system security engineer identify inherited security controls and tailor those controls to the system?
A security analyst wants to scan the network for active hosts. Which of the following host characteristics help to differentiate between a virtual and physical host?
A systems administrator is trying to secure a critical system. The administrator has placed the system behind a firewall, enabled strong authentication, and required all administrators of this system to attend mandatory training.
Which of the following BEST describes the control being implemented?
A pharmacy gives its clients online access to their records and the ability to review bills and make payments. A new SSL vulnerability on a special platform was discovered, allowing an attacker to capture the data between the end user and the web server providing these services. After investigating the platform vulnerability, it was determined that the web services provided are being impacted by this new threat.
Which of the following data types are MOST likely at risk of exposure based on this new threat? (Choose two.)
A company invested ten percent of its entire annual budget in security technologies. The Chief Information Officer (CIO) is convinced that, without this investment, the company will risk being the next victim of the same cyber attack its competitor experienced three months ago. However, despite this investment, users are sharing their usernames and passwords with their coworkers to get their jobs done. Which of the following will eliminate the risk introduced by this practice?
A nuclear facility manager determined the need to monitor utilization of water within the facility. A startup company just announced a state-of-the-art solution to address the need for integrating the business and ICS network. The solution requires a very small agent to be installed on the ICS equipment. Which of the following is the MOST important security control for the manager to invest in to protect the facility?
A security analyst is running a routine vulnerability scan against a web farm. The farm consists of a single server acting as a load-balancing reverse proxy and offloads cryptographic processes to the backend servers. The backend servers consist of four servers that process the inquiries for the front end.
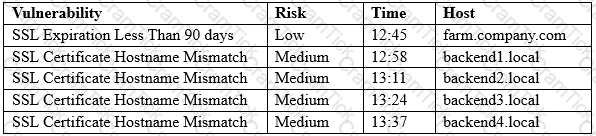
A web service SSL query of each server responds with the same output:
Connected (0x000003)
depth=0 /0=farm.company.com/CN=farm.company.com/OU=Domain Control Validated
Which of the following results BEST addresses these findings?
There have been several exploits to critical devices within the network. However, there is currently no process to perform vulnerability analysis.
Which of the following should the security analyst implement during production hours to identify critical threats and vulnerabilities?
Joe, a penetration tester, used a professional directory to identify a network administrator and ID administrator for a client’s company. Joe then emailed the network administrator, identifying himself as the ID administrator, and asked for a current password as part of a security exercise. Which of the following techniques were used in this scenario?
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
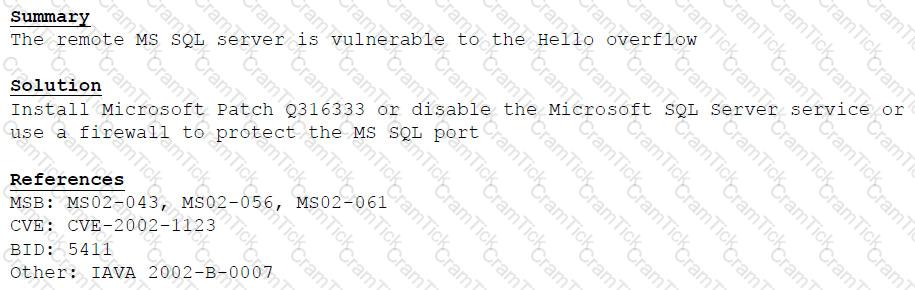
Based on the above information, which of the following should the system administrator do? (Select TWO).
A security analyst is reviewing a report from the networking department that describes an increase in network utilization, which is causing network performance issues on some systems. A top talkers report over a five-minute sample is included.
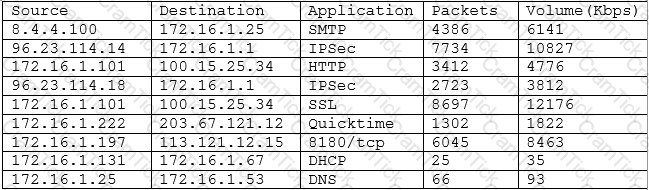
Given the above output of the sample, which of the following should the security analyst accomplish FIRST to help track down the performance issues?
A recently issued audit report highlighted exceptions related to end-user handling of sensitive data and access credentials. A security manager is addressing the findings. Which of the following activities should be implemented?
A security analyst is performing a routine check on the SIEM logs related to the commands used by operators and detects several suspicious entries from different users. Which of the following would require immediate attention?
Given the following code:
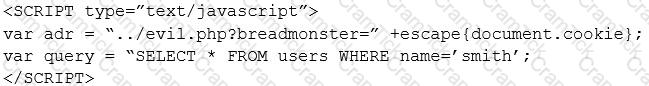
Which of the following types of attacks is occurring in the example above?
During a review of security controls, an analyst was able to connect to an external, unsecured FTP server from a workstation. The analyst was troubleshooting and reviewed the ACLs of the segment firewall the workstation is connected to:
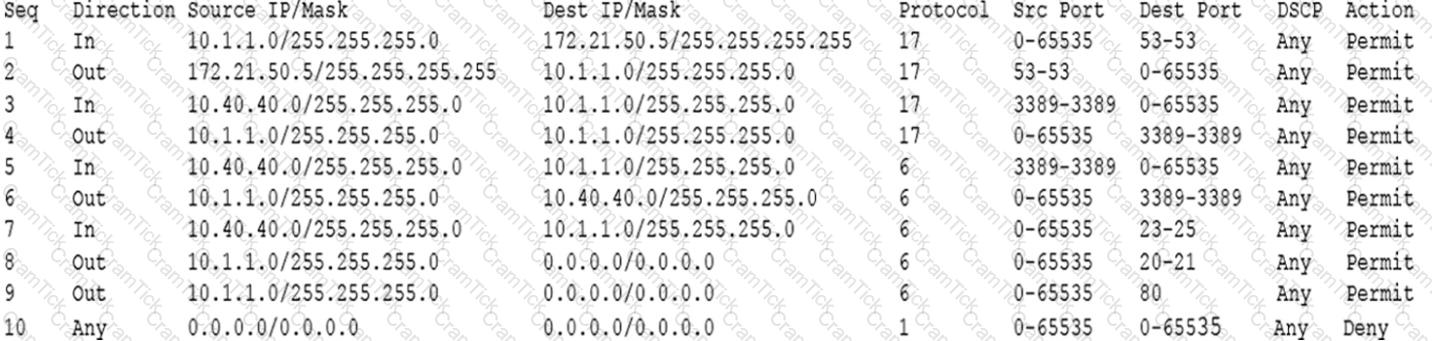
Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?
Which of the following command line utilities would an analyst use on an end-user PC to determine the ports it is listening on?
A security analyst is assisting in the redesign of a network to make it more secure. The solution should be low cost, and access to the secure segments should be easily monitored, secured, and controlled. Which of the following should be implemented?
The development team currently consists of three developers who each specialize in a specific programming language:
Developer 1 – C++/C#
Developer 2 – Python
Developer 3 – Assembly
Which of the following SDLC best practices would be challenging to implement with the current available staff?
NOTE: Question IP must be 192.168.192.123
During a network reconnaissance engagement, a penetration tester was given perimeter firewall ACLs to accelerate the scanning process. The penetration tester has decided to concentrate on trying to brute force log in to destination IP address 192.168.192.132 via secure shell.

Given a source IP address of 10.10.10.30, which of the following ACLs will permit this access?
A security analyst received an email with the following key:
Xj3XJ3LLc
A second security analyst received an email with following key:
3XJ3xjcLLC
The security manager has informed the two analysts that the email they received is a key that allows access to the company’s financial segment for maintenance. This is an example of:
A company office was broken into over the weekend. The office manager contacts the IT security group to provide details on which servers were stolen. The security analyst determines one of the stolen servers contained a list of customer PII information, and another server contained a copy of the credit card transactions processed on the Friday before the break-in. In addition to potential security implications of information that could be gleaned from those servers and the rebuilding/restoring of the data on the stolen systems, the analyst needs to determine any communication or notification requirements with respect to the incident. Which of the following items is MOST important when determining what information needs to be provided, who should be contacted, and when the communication needs to occur.
Following the development of a company's new online application, a security analyst Is brought In to test the site's security before going live. The analyst Is given the following URL and credentials:
htt ps://app.com pany.com/Guest User ID: UserBob Password: S#7h&sh*g
After logging In, the URL changes to the following, and the system displays a screen with graphs of various data points:
https;//opp.company.corn/User/dashboard.php?view=grophs
Which of the following Is the BEST choice for a reasonable test of circumventing the site's security?
While conducting research on malicious domains, a threat intelligence analyst received a blue screen of death. The analyst rebooted and received a message stating that the computer had been locked and could only be opened by following the instructions on the screen. Which of the following combinations describes the MOST likely threat and the PRIMARY mitigation for the threat?
Which of the following is the MOST secure method to perform dynamic analysis of malware that can sense when it is in a virtual environment?
A corporation employs a number of small-form-factor workstations and mobile devices, and an incident response team is therefore required to build a forensics kit with tools to support chip-off analysis. Which of the following tools would BEST meet this requirement?
A security analyst, who is working for a company that utilizes Linux servers, receives the following results from a vulnerability scan:
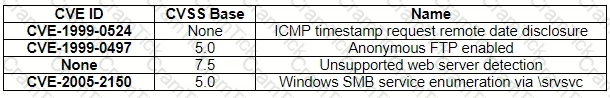
Which of the following is MOST likely a false positive?
Datacenter access is controlled with proximity badges that record all entries and exits from the datacenter.
The access records are used to identify which staff members accessed the data center in the event of equipment theft.
Which of the following MUST be prevented in order for this policy to be effective?
A cybersecurity analyst has received an alert that well-known “call home” messages are continuously observed by network sensors at the network boundary. The proxy firewall successfully drops the messages. After determining the alert was a true positive, which of the following represents the MOST likely cause?
A cybersecurity analyst is reviewing the current BYOD security posture. The users must be able to synchronize their calendars, email, and contacts to a smartphone or other personal device. The recommendation must provide the most flexibility to users. Which of the following recommendations would meet both the mobile data protection efforts and the business requirements described in this scenario?
Several users have reported that when attempting to save documents in team folders, the following message is received:
The File Cannot Be Copied or Moved – Service Unavailable.
Upon further investigation, it is found that the syslog server is not obtaining log events from the file server to which the users are attempting to copy files. Which of the following is the MOST likely scenario causing these issues?
A system administrator has reviewed the following output:
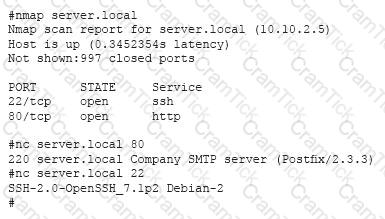
Which of the following can a system administrator infer from the above output?
A system administrator recently deployed and verified the installation of a critical patch issued by the company’s primary OS vendor. This patch was supposed to remedy a vulnerability that would allow an adversary to remotely execute code from over the network. However, the administrator just ran a vulnerability assessment of networked systems, and each of them still reported having the same vulnerability. Which of the following is the MOST likely explanation for this?
An organization wants to remediate vulnerabilities associated with its web servers. An initial vulnerability scan has been performed, and analysts are reviewing the results. Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities. Which of the following would be an indicator of a likely false positive?
Using a heuristic system to detect an anomaly in a computer’s baseline, a system administrator was able to detect an attack even though the company signature based IDS and antivirus did not detect it. Further analysis revealed that the attacker had downloaded an executable file onto the company PC from the USB port, and executed it to trigger a privilege escalation flaw. Which of the following attacks has MOST likely occurred?
A technician recently fixed a computer with several viruses and spyware programs on it and notices the Internet settings were set to redirect all traffic through an unknown proxy. This type of attack is known as which of the following?
A security analyst has determined that the user interface on an embedded device is vulnerable to common SQL injections. The device is unable to be replaced, and the software cannot be upgraded. Which of the following should the security analyst recommend to add additional security to this device?
A cybersecurity analyst has received a report that multiple systems are experiencing slowness as a result of a DDoS attack. Which of the following would be the BEST action for the cybersecurity analyst to perform?
Which of the following commands would a security analyst use to make a copy of an image for forensics use?
A cybersecurity analyst is reviewing Apache logs on a web server and finds that some logs are missing. The analyst has identified that the systems administrator accidentally deleted some log files. Which of the following actions or rules should be implemented to prevent this incident from reoccurring?
An analyst is reviewing a list of vulnerabilities, which were reported from a recent vulnerability scan of a Linux server.
Which of the following is MOST likely to be a false positive?
An alert is issued from the SIEM that indicates a large number of failed logins for the same account name on one of the application servers starting at 10:20 a.m. No other significant failed login activity is detected. Using Splunk to search for activity pertaining to that account name, a security analyst finds the account has been authenticating successfully for some time and started to fail this morning. The account is attempting to authenticate from an internal server that is running a database to an application server. No other security activity is detected on the network. The analyst discovers the account owner is a developer who no longer works for the company. Which of the following is the MOST likely reason for the failed login attempts for that account?
A security analyst has concluded that a breach occurred and data was exfilterated out of the network. Which of the following roles Is responsible for Identifying the location of the attackers and the stolen data?
A medical organization recently started accepting payments over the phone. The manager is concerned about the impact of the storage of different types of data. Which of the following types of data incurs the highest regulatory constraints?
CompTIA CySA+ | CS0-001 Questions Answers | CS0-001 Test Prep | CompTIA CSA+ Certification Exam Questions PDF | CS0-001 Online Exam | CS0-001 Practice Test | CS0-001 PDF | CS0-001 Test Questions | CS0-001 Study Material | CS0-001 Exam Preparation | CS0-001 Valid Dumps | CS0-001 Real Questions | CompTIA CySA+ CS0-001 Exam Questions