A company's man web application is no longer accessible via the internet. The cloud administrator investigates and discovers the application is accessible locally and only via an IP access. Which of the following was misconfigured?
Which of the following describes the main difference between public and private container repositories?
A cloud engineer has provisioned a VM for a high-frequency trading application. After the VM is put into production, users report high latency in trades. The engineer checks the last six hours of VM metrics and sees the following:
• CPU utilization is between 30% to 60%.
• Networkln is between 50Kbps and 70Kbps.
• NetworkOut is between 3.000Kpbs and 5.000Kbps.
• DiskReadOps is at 30.
• DiskWriteOps is at 70
• Memory utilization is between 50% and 70%.
Which of the following steps should the engineer take next to solve the latency issue?
Which of the following network protocols is generally used in a NAS environment?
A cloud server needs to automatically allocate more resources during sudden peak times. This allocation does not need to occur in regular intervals. Which of the following scaling
approaches should be used?
A SaaS provider introduced new software functionality for customers as part of quarterly production enhancements. After an update is implemented, users cannot locate certain transactions from an inbound integration. During the investigation, the application owner finds the following error in the logs:
Error: REST API - Deprecated call is no longer supported in this release.
Which of the following is the best action for the application owner to take to resolve the issue?
A cloud security analyst is concerned about security vulnerabilities in publicly available container images. Which of the following is the most appropriate action for the analyst to
recommend?
A cloud developer receives a security vulnerability scan report and needs to analyze and record the true positives. Which of the following vulnerability management steps is this an example of?
An IT security team wants to ensure that the correct parties are informed when a specific user account is signed in. Which of the following would most likely allow an administrator to address this concern?
A software engineer is integrating an application lo The cloud that is web socket based. Which of the following applications is the engineer most likely deploying?
A user's assigned cloud credentials are locked, and the user is unable to access the project's application. The cloud administrator reviews the logs and notices several attempts to log in with the user's account were made to a different application after working hours. Which of the following is the best approach for the administrator to troubleshoot this issue?
During a project kickoff meeting, the project manager wants to set expectations for all of the team members. Which of the following actions should the project manager take to accomplish this goal?
A company is developing a new web application that requires a relational database management system with minimal operational overhead. Which of the following should the company choose?
A cloud engineer is designing a high-performance computing cluster for proprietary software. The software requires low network latency and high throughput between cluster nodes.
Which of the following would have the greatest impact on latency and throughput when designing the HPC infrastructure?
A cloud developer is creating a static website that customers will be accessing globally. Which of the following services will help reduce latency?
A DevOps engineer is integrating multiple systems. Each system has its own API that exchanges data based on different application-level transactions. Which of the following
delivery mechanisms would best support this integration?
The performance of an e-commerce website decreases dramatically during random periods. The IT team is evaluating available resources to mitigate the situation. Which of the following is the best approach to effectively manage this scenario'?
Which of the following cloud deployment models is the best way to replicate a workload non-disruptively between on-premises servers and a public cloud?
A company has decided to adopt a microservices architecture for its applications that are deployed to the cloud. Which of the following is a major advantage of this type of architecture?
Which of the following is the best type of database for storing different types of unstructured data that may change frequently?
A cloud deployment uses three different VPCs. The subnets on each VPC need to communicate with the others over private channels. Which of the following will achieve this objective?
A company needs to deploy its own code directly in the cloud without provisioning additional infrastructure. Which of the following is the best cloud service model for the company to use?
A company wants to use a solution that will allow for quick recovery from ransomware attacks, as well as intentional and unintentional attacks on data integrity and availability. Which of the following should the company implement that will minimize administrative overhead?
Which of the following requirements are core considerations when migrating a small business's on-premises applications to the cloud? (Select two).
During project initiation, a project manager needs to identify goals and deliverables that should be completed by the end of the project and also meet certain cost and time factors. Which of the following would best align with these needs?
A project team is deciding how to break up a large project into smaller components so the project can be delivered without increasing the duration of the iteration cycles. Which of the following describes the grouping of the smaller components?
Between 11:00 a.m. and 1:00 p.m. on workdays, users report that the sales database is either not accessible, sluggish, or difficult to connect to. A cloud administrator discovers that during the impacted time, all hypervisors are at capacity. However, when 70% of the users are using the same database, those issues are not reported. Which of the following is the most likely cause?
Two CVEs are discovered on servers in the company's public cloud virtual network. The CVEs are listed as having an attack vector value of network and CVSS score of 9.0. Which
of the following actions would be the best way to mitigate the vulnerabilities?
Which of the following is a field of computer science that enables computers to identify and understand objects and people in images and videos?
Which of the following is used to detect signals and measure physical properties, such as the temperature of the human body?
A cloud administrator learns that a major version update. 4.6.0. is available for a business-critical application. The application is currently on version 4.5.2. with additional minor versions 3, 4, and 5 available. The administrator needs to perform the update while minimizing downtime. Which of the following should the administrator do first?
A security engineer recently discovered a vulnerability in the operating system of the company VMs. The operations team reviews the issue and decides all VMs need to be updated
from version 3.4.0 to 3.4.1. Which of the following best describes the type of update that will be applied?
A company's website suddenly crashed. A cloud engineer investigates the following logs:
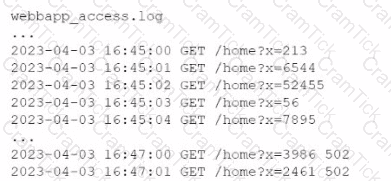
Which of the following is the most likely cause of the issue?
Which of the following cloud deployment strategies is best for an organization that wants to run open-source workloads with other organizations that are sharing the cost?
An administrator is setting up a cloud backup solution that requires the following features:
• Cost effective
• Granular recovery
• Multilocation
Which of the following backup types best meets these requirements?
A company hosts various containerized applications for business uses. A client reports that one of its routine business applications fails to load the web-based login prompt hosted in the company cloud.
Click on each device and resource. Review the configurations, logs, and characteristics of each node in the architecture to diagnose the issue. Then, make the necessary changes to the WAF configuration to remediate the issue.
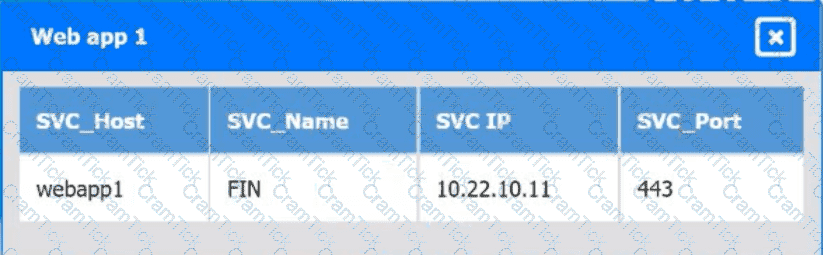
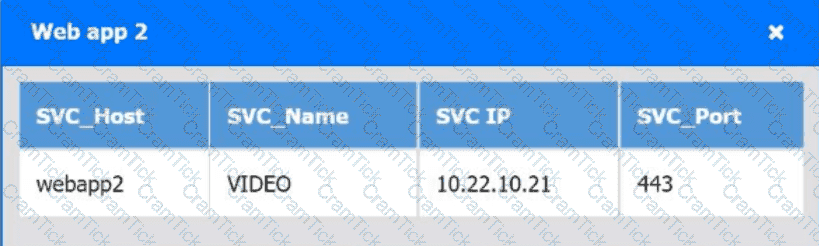
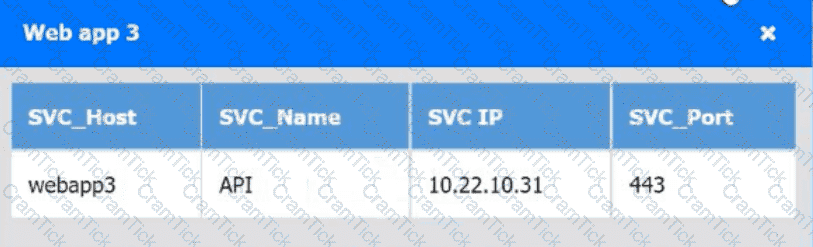
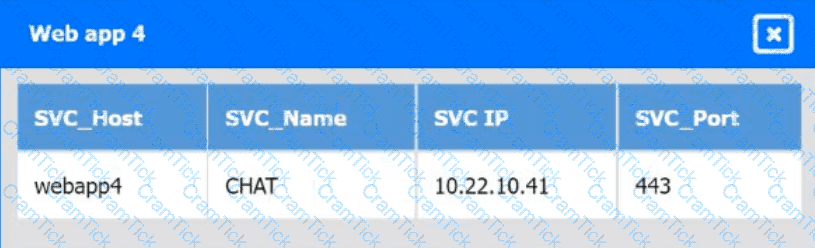
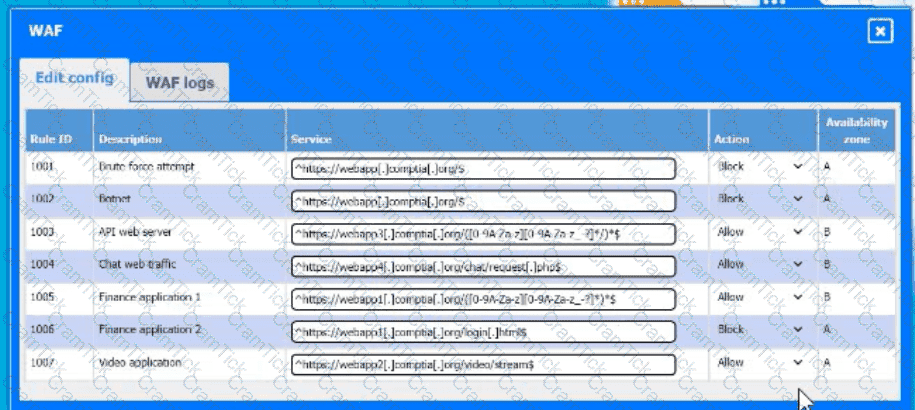
Which of the following is an auditing procedure that ensures service providers securely manage the data to protect the interests of the organization and the privacy of its clients?
An e-commerce store is preparing for an annual holiday sale. Previously, this sale has increased the number of transactions between two and ten times the normal level of
transactions. A cloud administrator wants to implement a process to scale the web server seamlessly. The goal is to automate changes only when necessary and with minimal cost.
Which of the following scaling approaches should the administrator use?
A bank informs an administrator that changes must be made to backups for long-term reporting purposes. Which of the following is the most important change the administrator
should make to satisfy these requirements?
A cloud engineer is exploring options to reduce the management overhead of the servers and network. Which of the following cloud service models should the engineer implement?
A cross-site request forgery vulnerability exploited a web application that was hosted in a public laaS network. A security engineer determined that deploying a WAF in blocking mode at a CDN would prevent the application from being exploited again. However, a week after implementing the WAF, the application was exploited again. Which of the following should the security engineer do to make the WAF control effective?
Which of the following types of storage provides the greatest performance advantage for a traditional relational database?
A high-usage cloud resource needs to be monitored in real time on specific events to guarantee its availability. Which of the following actions should be used to meet this requirement?
Which of the following is the most cost-effective and efficient strategy when migrating to the cloud?
A cloud engineer is concerned about command-and-control (C2) communication out of a cloud network over HTTPS. Which of the following should the cloud engineer implement to most efficiently identify the type of communication?
Which of the following will best reduce the cost of running workloads while maintaining the same performance? (Select two).
The change control board received a request to approve a configuration change 10 deploy in the cloud production environment. Which of the following should have already been competed?
A software engineer notices that the newest update to the reporting software includes many new features that were not defined in the requirements document. Which of the following steps should the engineer take next?
A company has been using a CRM application that was developed in-house and is hosted on local servers. Due to internal changes, the company wants to migrate the application to the cloud without having to manage the infrastructure. Which of the following services should the company consider?
A company uses containers to implement a web application. The development team completed internal testing of a new feature and is ready to move the feature to the production
environment. Which of the following deployment models would best meet the company's needs while minimizing cost and targeting a specific subset of its users?
A cloud consultant needs to modernize a legacy application that can no longer address user demand and is expensive to maintain. Which of the following is the best migration
strategy?
An IT manager needs to deploy a cloud solution that meets the following requirements:
. Users must use two authentication methods to access resources.
· Each user must have 10GB of storage space by default.
Which of the following combinations should the manager use to provision these requirements?
A list of CVEs was identified on a web server. The systems administrator decides to close the ports and disable weak TLS ciphers. Which of the following describes this vulnerability management stage?
A project team that handles sensitive data analysis recently onboarded three new employees. Which of the following should the PM do first?
A system surpasses 75% to 80% of resource consumption. Which of the following scaling approaches is the most appropriate?
Which of the following is the most cost-effective way to store data that is infrequently accessed?
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A – The end user accesses the application through a web browser to enter and view clinical data.
2A – The CTM application server reads/writes data to/from the database server.
1B – The end user accesses the application through a web browser to run reports on clinical data.
2B – The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B – The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: “Browser cannot display the webpage.” The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
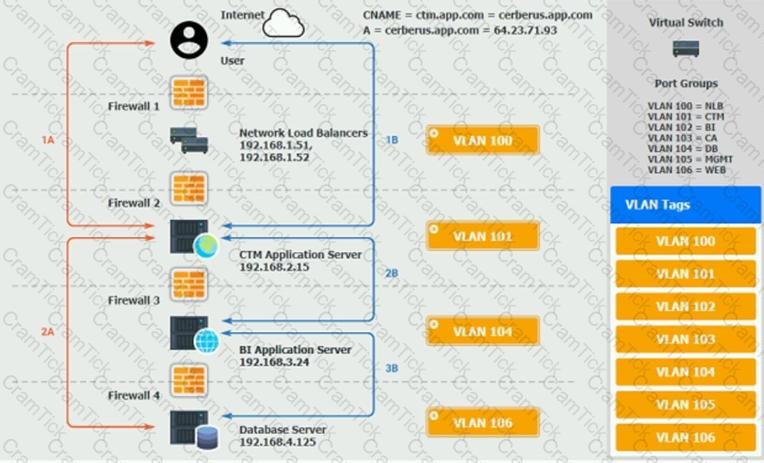
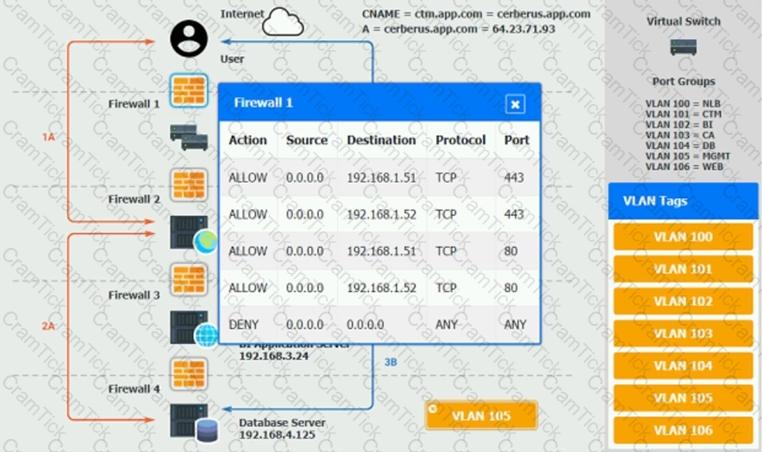
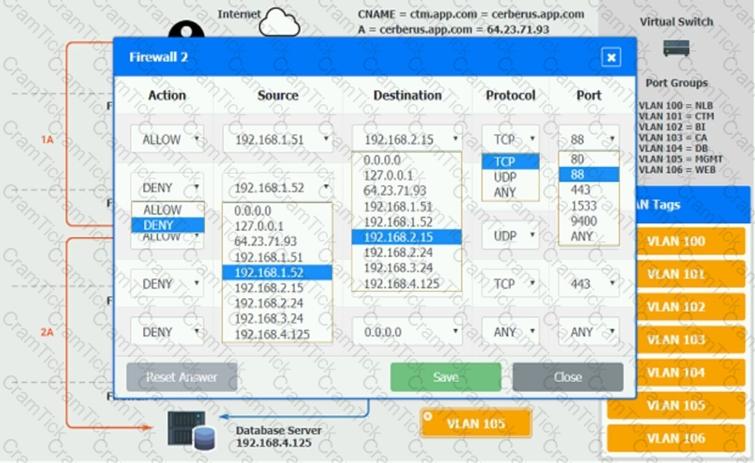
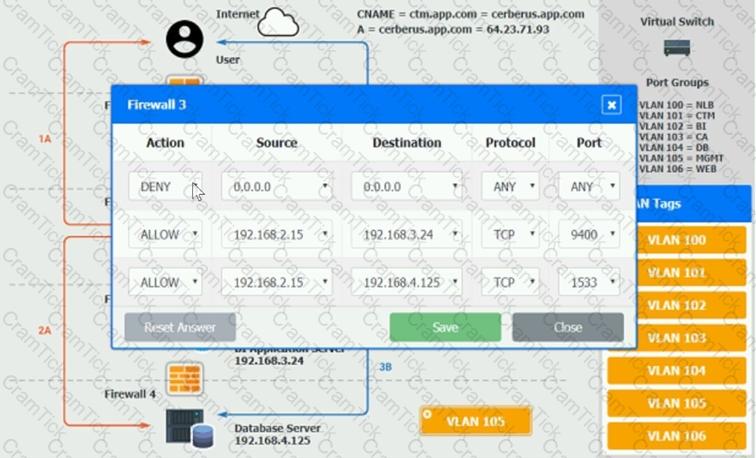
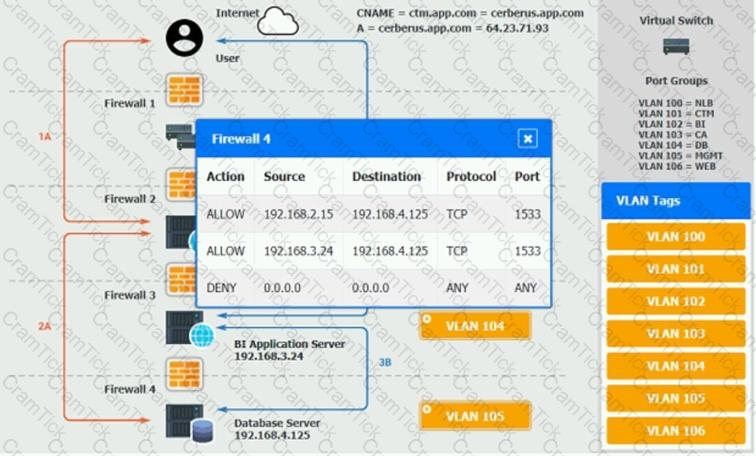
An IT manager is migrating the production environment to the cloud but needs to keep control of the operating systems, patches, and settings of all resources. Which of the following deployment models will best meet the requirements?
Which of the following is a customer be responsible for in a provider-managed database service? (Select two).
Which of the following are best practices when working with a source control system? (Select two).
A cloud engineer is receiving multiple alerts from the infrastructure monitoring agent. The alerts state that all the VMs in the public subnet are at 100% CPU utilization. However, when the engineer checks the network utilization of the VMs, the network throughput is at normal levels. Which of the following is the most likely cause of this issue?
Which of the following do developers use to keep track of changes made during software development projects?
A healthcare organization must follow strict compliance requirements to ensure that Pll is not leaked. The cloud administrator needs to ensure the cloud email system can support this requirement Which of the following should the organization enable?
A technician receives an email from a vendor who is requesting payment of an invoice for human resources services. The email contains a request for bank account numbers. Which of the following types of attacks does this behavior most likely indicate?
A company has developed an online trading platform. The engineering team selected event-based scaling for the platform's underlying resources. The platform resources scale up
with every 2,000 subscribed users. The engineering team finds out that although compute utilization is low, scaling is still occurring. Which of the following statements best explains
why this is the case?
Given the following command:
Sdocker pull images.comptia.org/user1/myimage:latest
Which of the following correctly identifies images.comptia.org?
Which of the following situations would require a project manager to revise the communication plan during a project's execution?
A company's VMs that are created using the noncritical application tag are automatically shut down at 5:00 p.m. using a cronjob. Which of the following actions would allow a cloud engineer to stop all unresponsive instances with the least effort in case the automation fails?
A project team is reviewing the project plan and related documents and identifies tasks that could be spread into smaller deliverables. Which of the following documents should the team edit first?
A cloud solutions architect is designing a VM-based solution that requires reducing the cost as much as possible. Which of the following solutions will best satisfy this requirement?