Question:
What is the main advantage of 5G technology over previous generations of mobile networks?
Question:
Which operations management process is responsible for maintaining information about configuration items (CIs)?
Question:
What is a key benefit for deploying a remote data protection and recovery solution in a data center environment?
Question:
What is the most common technique used by malware protection software to detect malware?
Question:
A storage administrator needs to track the performance and availability of storage components and services. Which storage management function would provide this information?
Question:
A company wants to implement a security strategy that uses firewall, VPN, malware protection, and encryption. Which approach is most suitable for achieving this goal?
Question:
What is the maximum number of VLANs that can be supported with one VLAN tag field?
Question:
Which RAID level consists of two disk drives and every write is written to both disks?
Question:
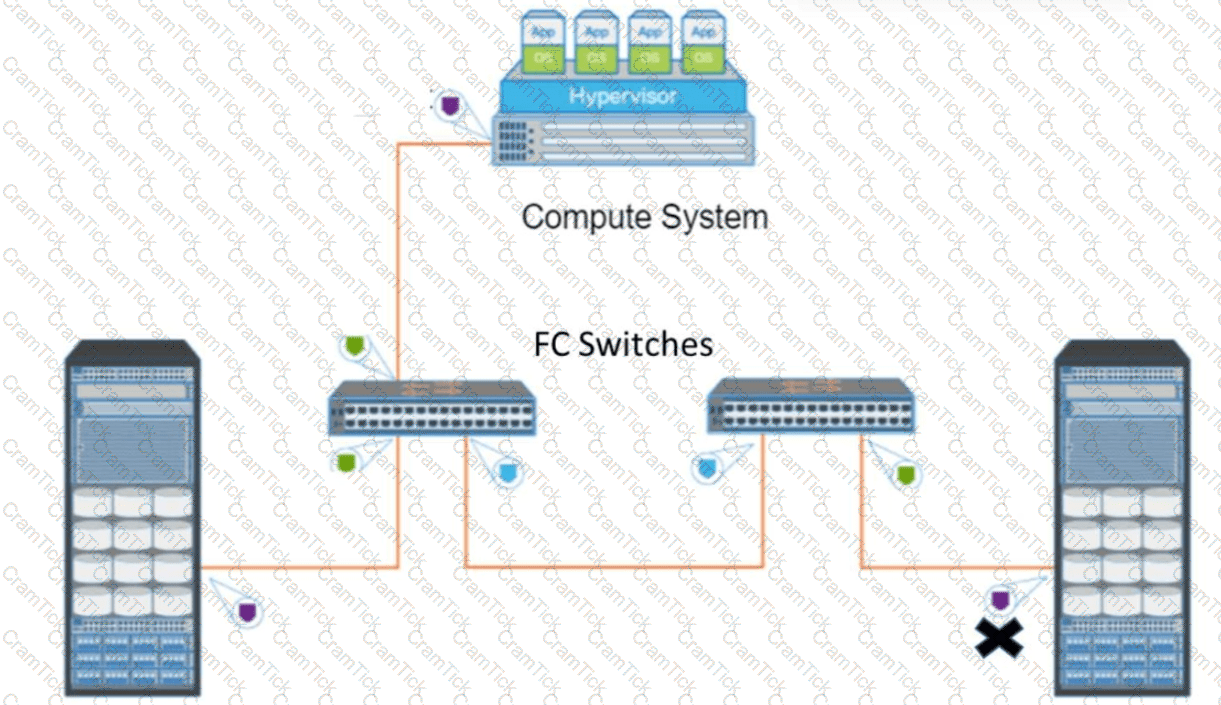
Refer to the Exhibit (Port marked "X"): What type of FC port does the "X" represent?
Question:
A company is concerned about the risk of data loss due to accidental deletion and hardware failures. What is theprimaryreason for implementing a data backup solution?
Question:
A company needs to rebuild a failed disk in its RAID 5 array. Which two factors would significantly impact the rebuild time?
Question:
A company is looking for a backup solution that can reduce its IT management overhead and offer scalability and flexibility. Which type of backup solution would meet these requirements?
Question:
A company is concerned about unauthorized access to its sensitive data. They want to implement security measures to ensure that only authorized users can access the data. Which goal of information security are they primarily addressing?
DCA-ISM |


