Refer to the exhibit, which shows a partial output of the real-time LDAP debug.
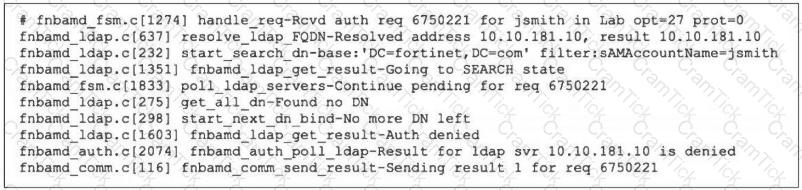
What two actions can the administrator take to resolve this issue? (Choose two.)
Refer to the exhibits.
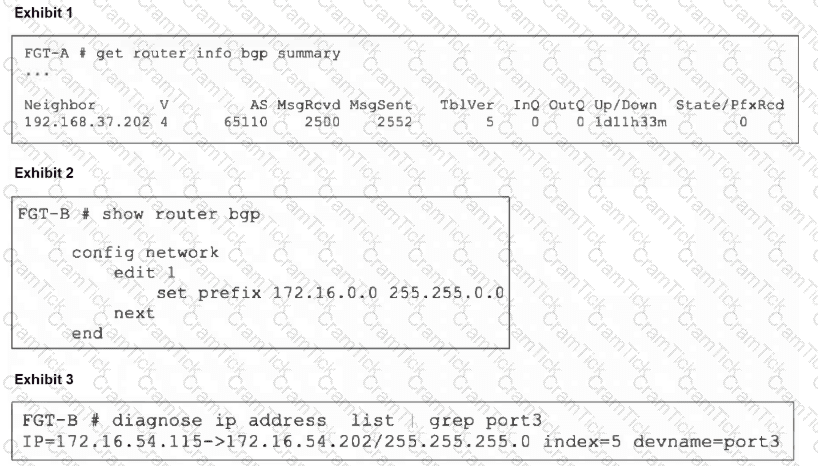
An administrator is attempting to advertise the network configured on port3. However, FGT-A is not receiving the prefix.
Which two actions can the administrator take to fix this problem? (Choose two.)
Exhibit.
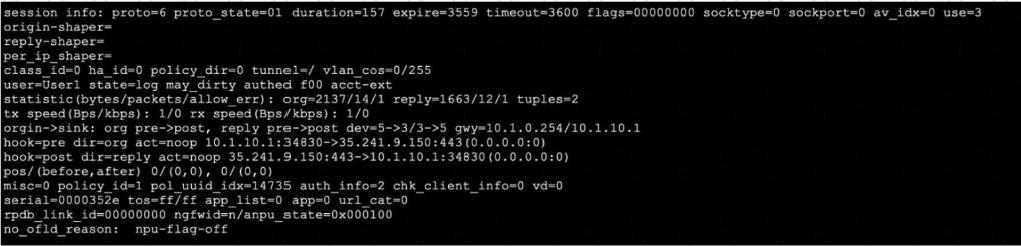
Refer to the exhibit, which shows the output of a session. Which two statements are true? (Choose Iwo.)
Which three common FortiGate-to-collector-agent connectivity issues can you identify using the FSSO real-time debug? (Choose three.)
An administrator wants to capture encrypted phase 2 traffic between two FotiGate devices using the built-in sniffer.
If the administrator knows that there Is no NAT device located between both FortiGate devices, which command should the administrator run?
Exhibit.
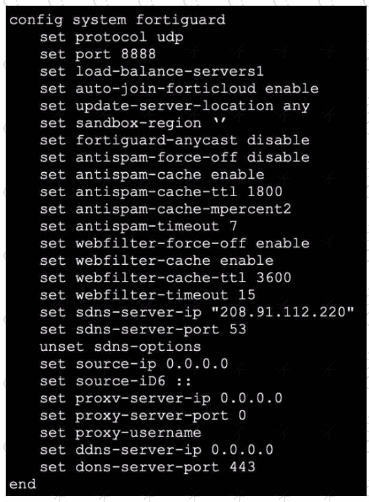
Refer to the exhibit, which shows a FortiGate configuration.
An administrator is troubleshooting a web filter issue on FortiGate. The administrator has configured a web filter profile and applied it to a policy; however the web filter is not inspecting any traffic that is passing through the policy.
What must the administrator do to fix the issue?
What are two reasons you might see iprope_in_check() check failed, drop when using the debug flow? (Choose two.)
In the SAML negotiation process, which section does the Identity Provider (IdP) provide the SAML attributes utilized in the authentication process to the Service Provider (SP)?
Refer to the exhibits.
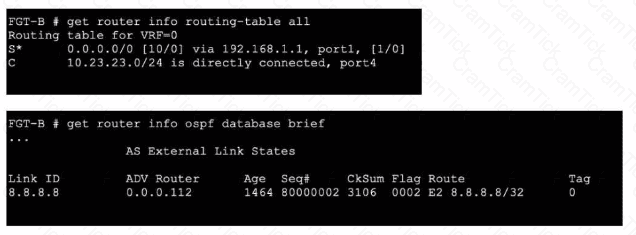
An administrator Is expecting to receive advertised route 8.8.8.8/32 from FGT-A. On FGT-B, they confirm that the route is being advertised and received, however, the route is not being injected into the routing table. What is the most likely cause of this issue?
Refer to the exhibit, which shows the omitted output of a session table entry.
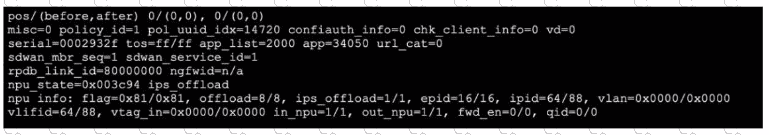
Which two statements are true? (Choose two.)
Refer to the exhibit.
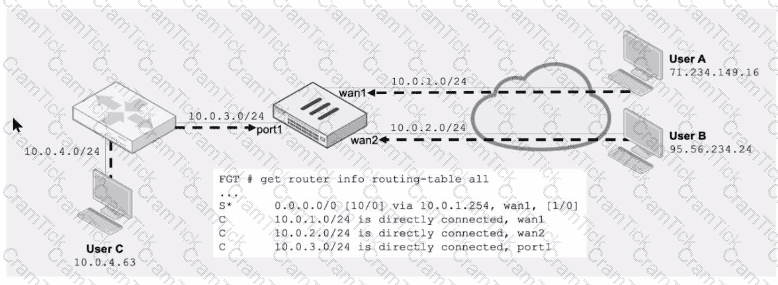
Assuming a default configuration, which three statements are true? (Choose three.)
Refer to the exhibit, which shows the output of diagnose sys session list.
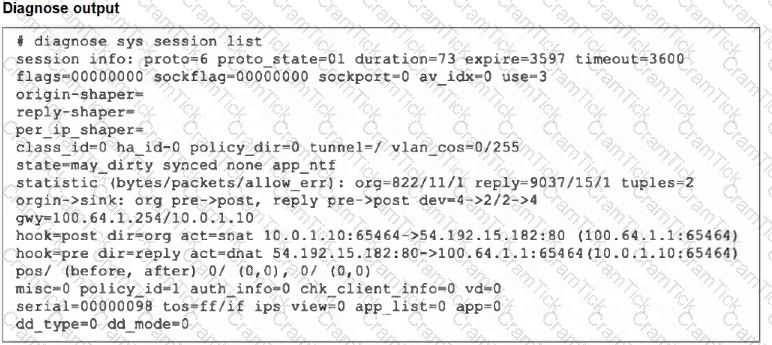
If the HA ID for the primary device is 0, what happens if the primary fails and the secondary becomes the primary?


