(Refer to the exhibits.
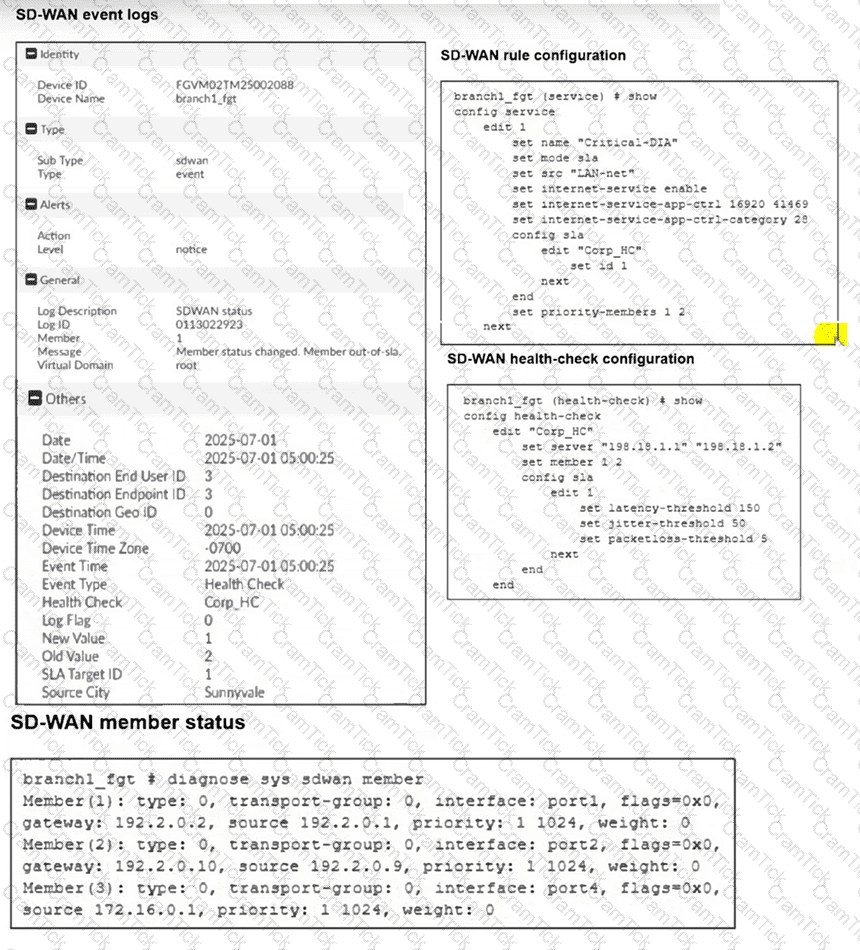
Two SD-WAN event logs, the member status, the SD-WAN rule configuration, and the health-check configuration for a FortiGate device are shown.
Immediately after the log messages are displayed, how will the FortiGate steer the traffic based on the information shown in the exhibits? Choose one answer.)
An administrator is configuring SD-WAN to load balance their network traffic. Which two things should they consider when setting up SD-WAN? (Choose two.)
Refer to the exhibits.
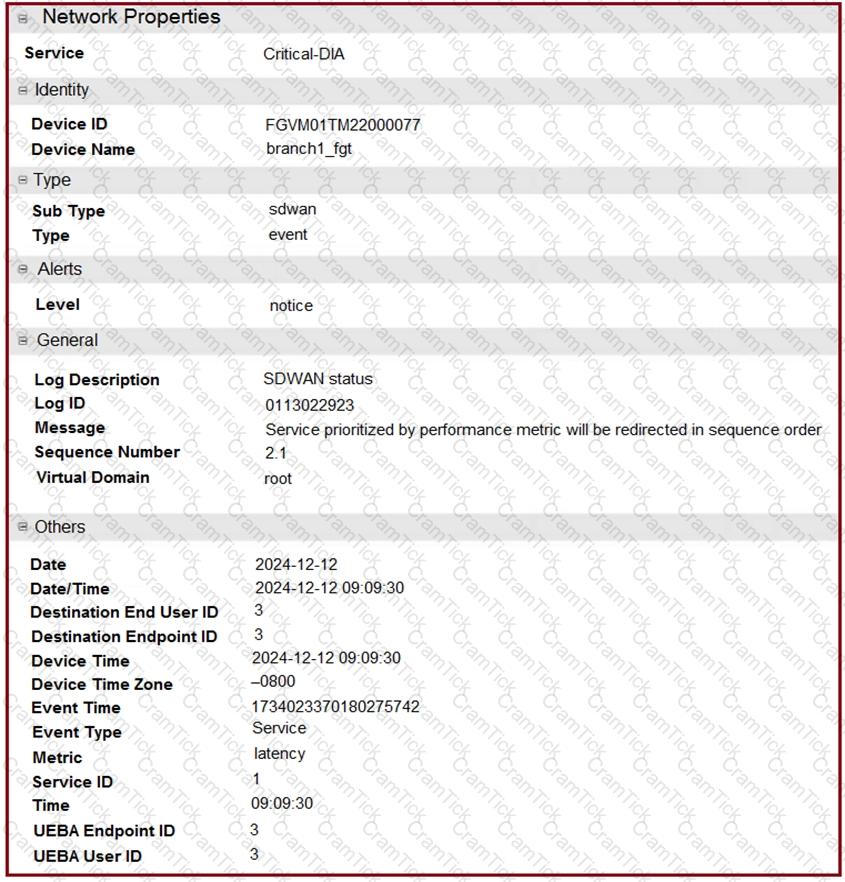
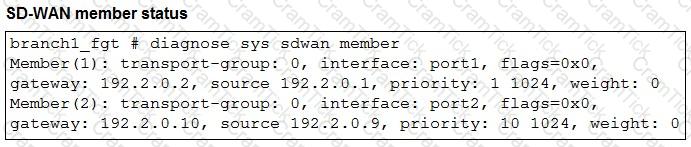
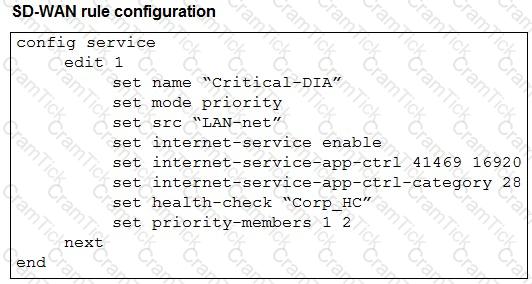
The exhibits show an SD-WAN event log, the member status, and the SD-WAN rule configuration.
Which two conclusions can you draw from the information shown? (Choose two.)
Refer to the exhibit.
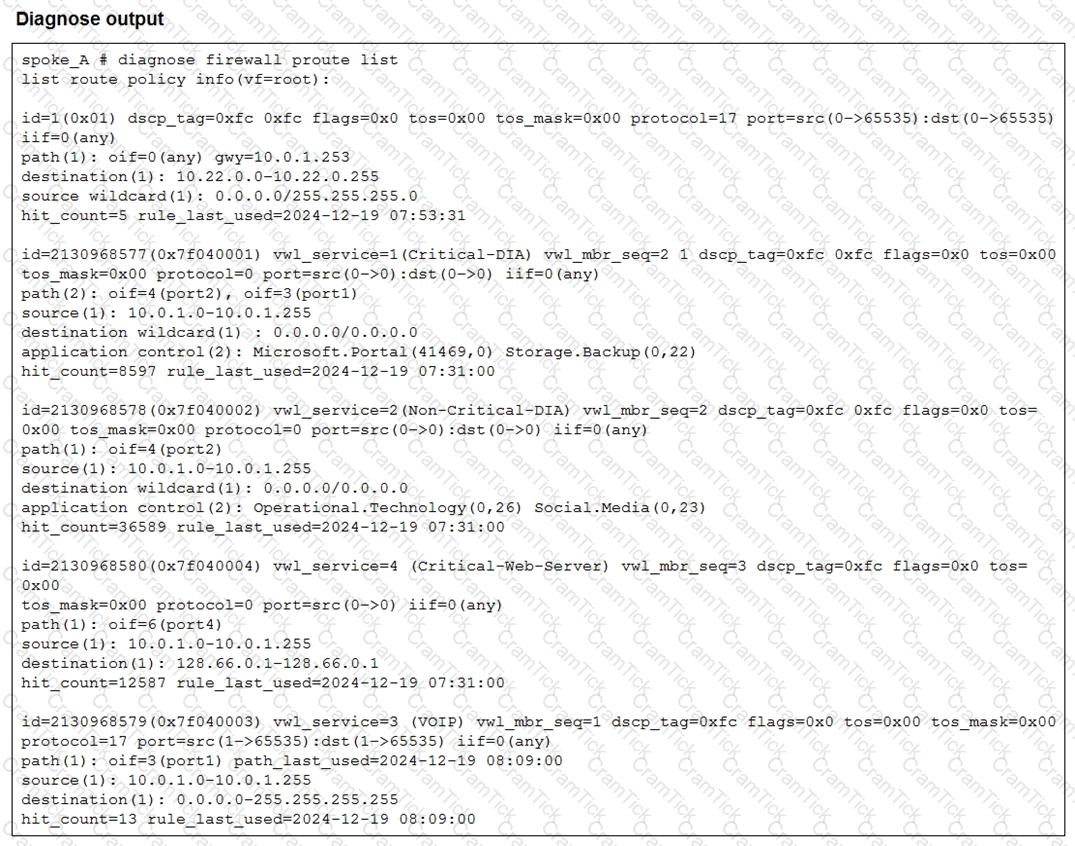
Which two conclusions can you draw from the output shown? (Choose two.)
(In the context of SD-WAN, the terms underlay and overlay are commonly used to categorize links.
Which two statements about underlay and overlay links are correct? Choose two answers.)
Refer to the exhibit.
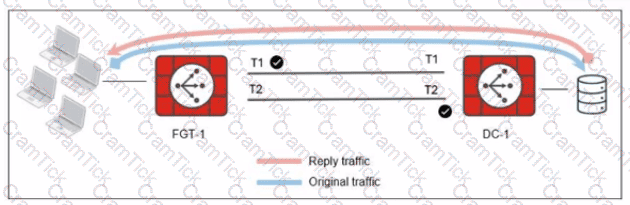
The administrator analyzed the traffic between a branch FortiGate and the server located in the data center, and noticed the behavior shown in the diagram.
When the LAN clients located behind FGT1 establish a session to a server behind DC-1, the administrator observes that, on DC-1, the reply traffic is routed overT2. even though T1 is the preferred member in
the matching SD-WAN rule.
What can the administrator do to instruct DC-1 to route the reply traffic through the member with the best performance?
You configured an SD-WAN rule with the best quality strategy and selected the predefined health check, Default_FortiGuard, to check the link performances against FortiGuard servers.
For the quality criteria, you selected Custom-profile-1.
Which factors does FortiGate use, and in which order. to determine the link that it should use to steer the traffic?
As an IT manager for a healthcare company, you want to delegate the installation and management of your SD-WAN deployment to a managed security service provider (MSSP). Each site must maintain direct internet access and ensure that it is secure. You expected significant traffic flow between the sites and want to delegate as much of the network administration and management as possible to the MSSP.
Which two MSSP deployment blueprints best address the customer’s requirements? (Choose two.)
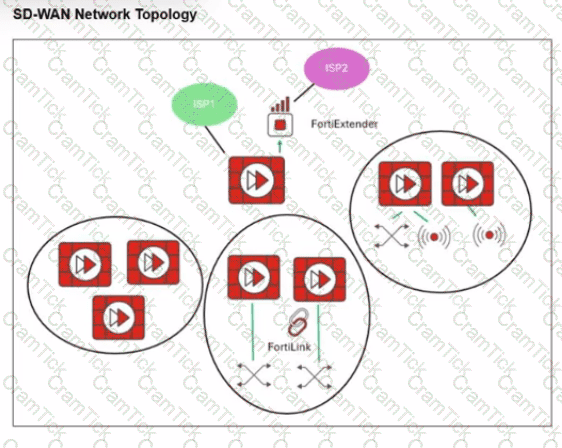
Refer to the exhibit.
You want to configure SD-WAN on a network as shown in the exhibit.
The network contains many FortiGate devices. Some are used as NGFW, and some are installed with extensions such as FortiSwitch. FortiAP. or Forti Ex tender.
What should you consider when planning your deployment?
(Refer to the exhibit.
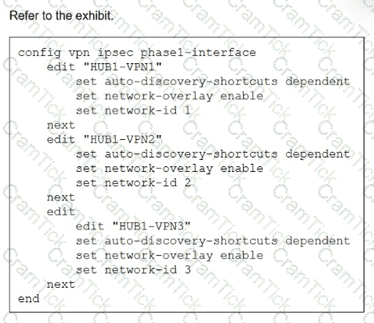
You update the spokes configuration of an existing auto-discovery VPN (ADVPN) topology by adding the parameters shown in the exhibit.
Which is a valid objective of those settings? Choose one answer.)
Refer to the exhibit, which shows the SD-WAN rule status and configuration.
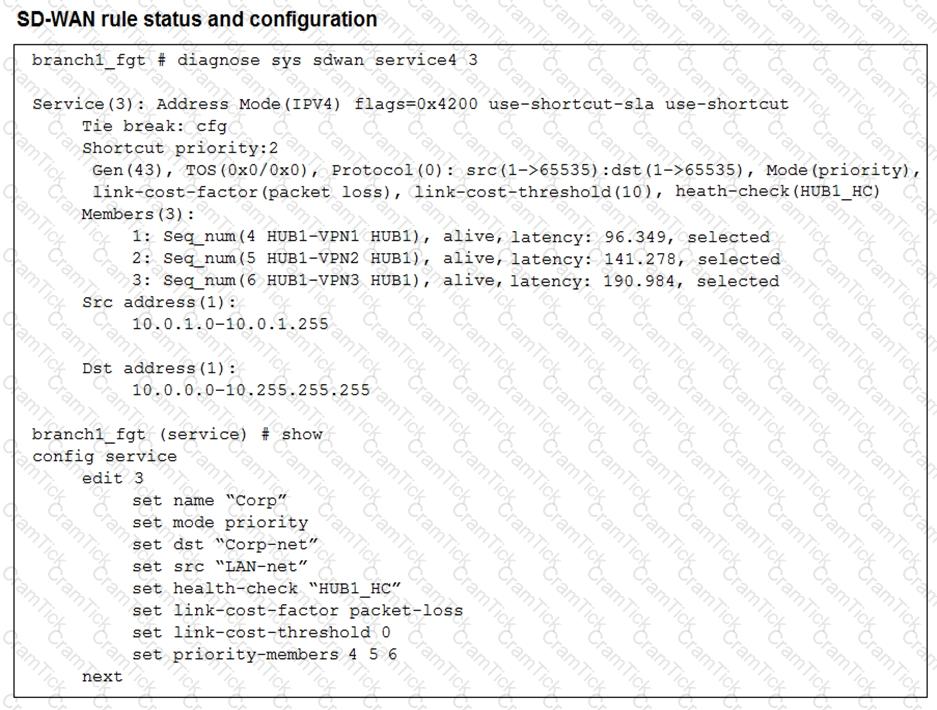
Based on the exhibit, which change in the measured latency will first make HUB1-VPN3 the new preferred member?
Refer to the exhibit.
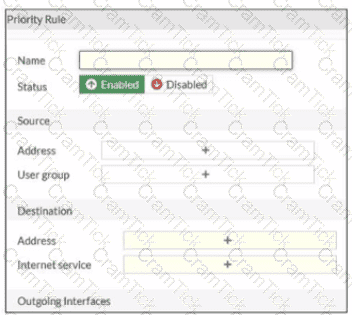
An administrator configures SD-WAN rules for a DIA setup using the FortiGate GUI. The page to configure the source and destination part of the rule looks as shown in the exhibit. The GUI page shows no option to configure an application as the destination of the SD-WAN rule Why?
Refer to the exhibits.
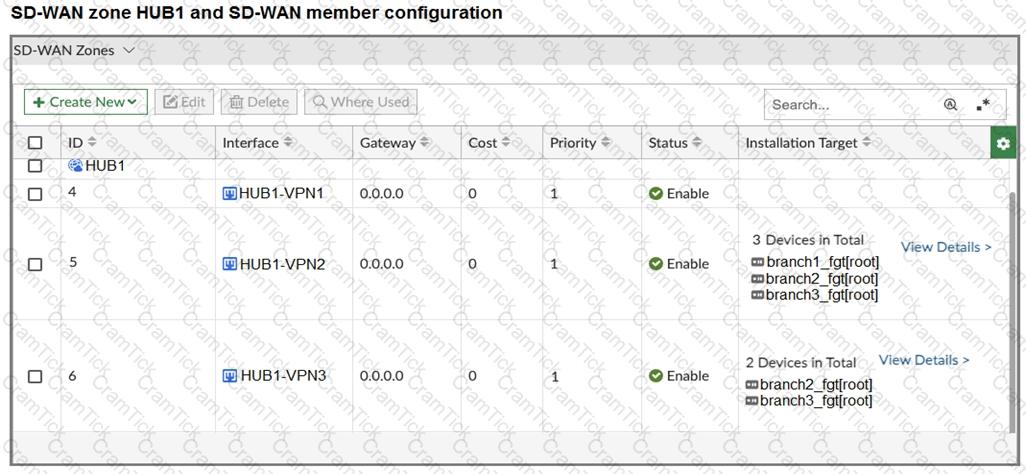
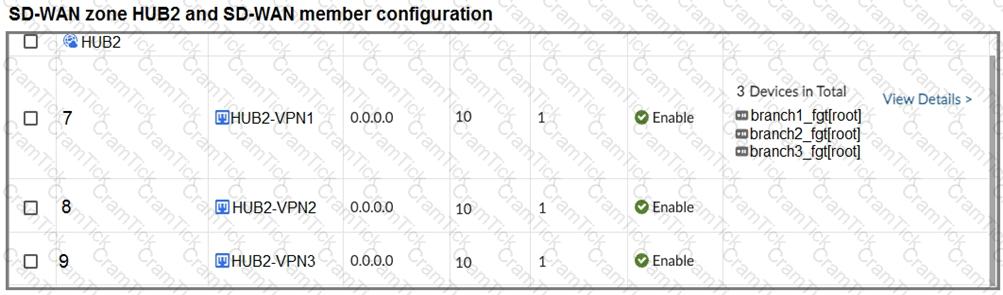
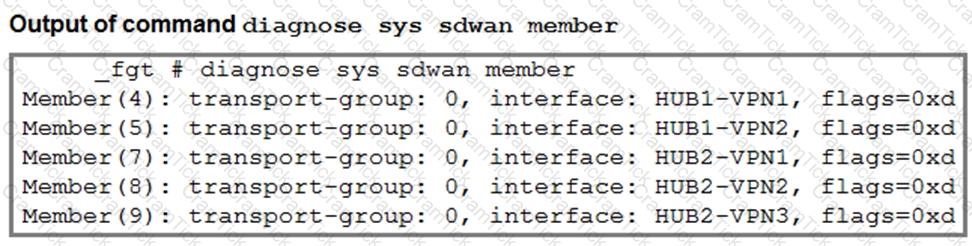
The first exhibit shows the SD-WAN zone HUB1 and SD-WAN member configuration from an SD-WAN template, and the second exhibit shows the output of command diagnose sys sdwan member collected on a FortiGate device.
Which statement best describes what the diagnose output shows?
Which three characteristics apply to provisioning templates available on FortiManager? (Choose three.)
When a customer delegate the installation and management of its SD-WAN infrastructure to an MSSP, the MSSP usually keeps the hub within its infrastructure for ease of management and to share costly resources.
In which two situations will the MSSP install the hub in customer premises? (Choose two.)
(Which two features must you configure before FortiGate can steer traffic according to SD-WAN rules? Choose two answers.)
(Refer to the exhibit.
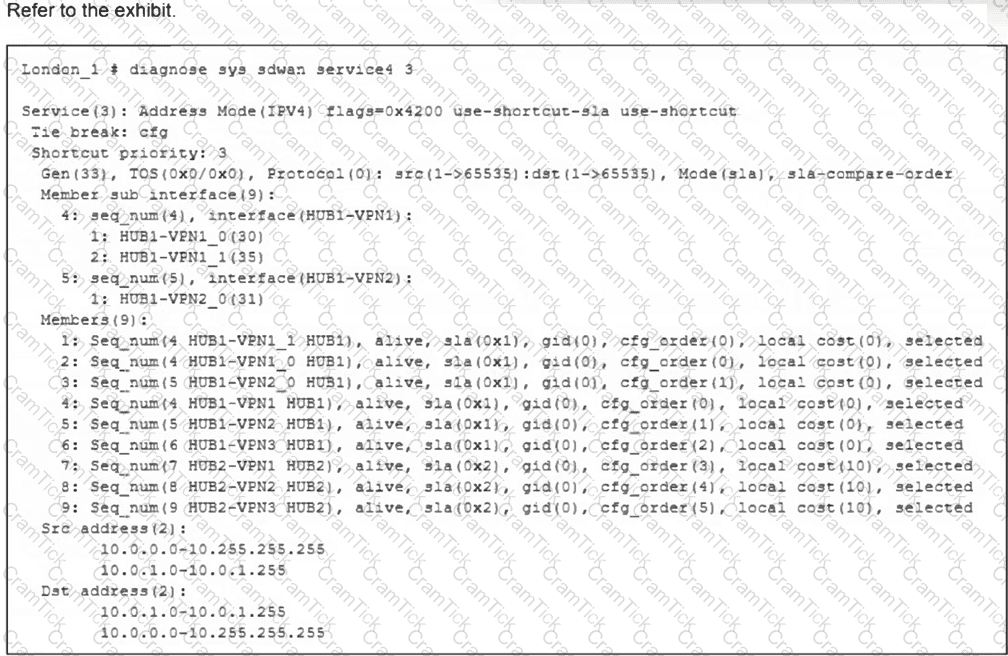
What can you conclude from the output shown? Choose one answer.)
When you use the command diagnose sys session list, how do you identify the sessions that correspond to traffic steered according to SD-WAN rules?
Which three factors about SLA targets and SD-WAN rules should you consider when configuring SD-WAN rules? (Choose three.)
Exhibit.
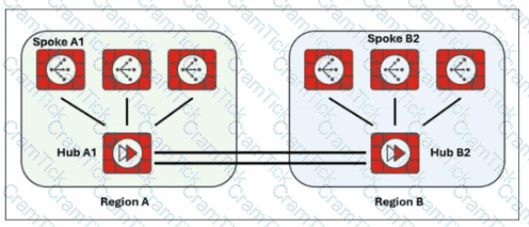
Two hub-and-spoke groups are connected through redundant site-to-site IPsec VPNs between Hub 1 and Hub 2
Which two configuration settings are required for the spoke A1 to establish an ADVPN shortcut with the spoke B2? (Choose two.)
Refer to the exhibit.
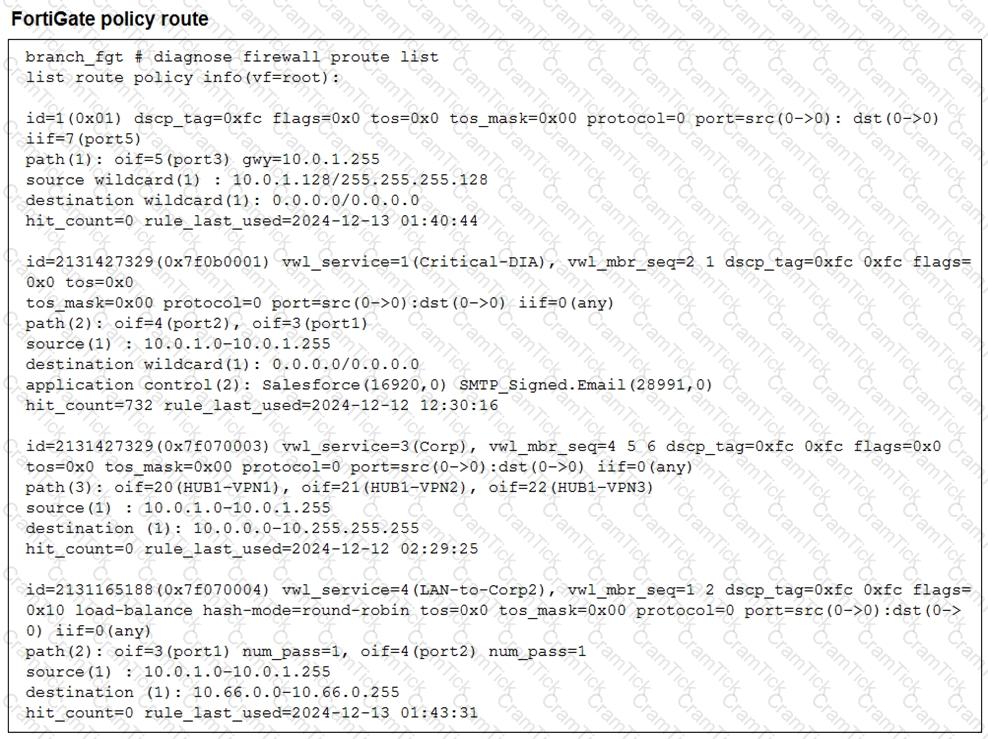
What conclusions can you draw about the traffic received by FortiGate originating from the source LAN device 10.0.1.133 and destined for the company’s SMTP mail server at 10.66.0.125?
Refer to the exhibit that shows an SD-WAN zone configuration on the FortiManager GUI.
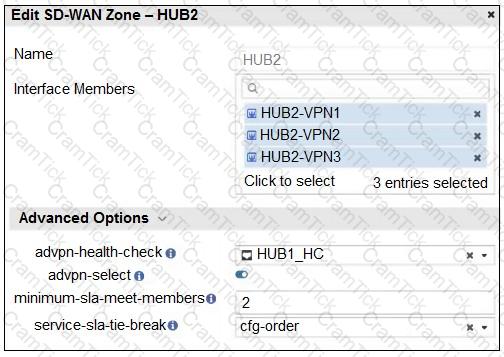
Based on the exhibit, how will the FortiGate device behave after it receives this configuration?
(Refer to the exhibit.
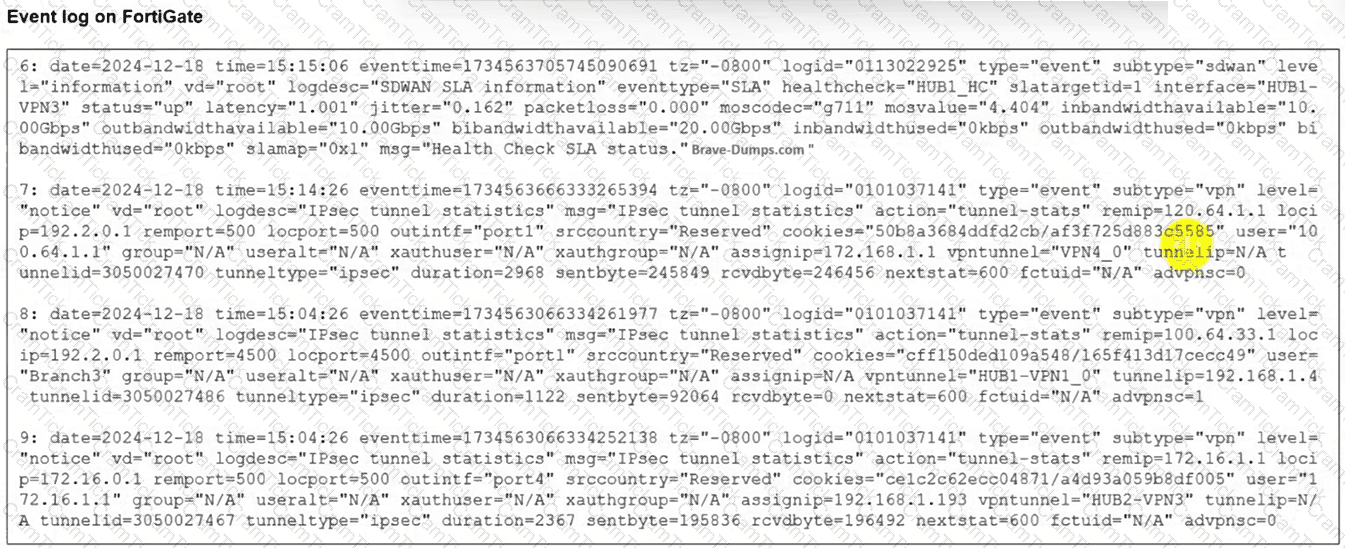
The event log on a FortiGate device is shown.
Based on the output shown in the exhibit, what can you conclude about the tunnels on this device? (Choose one answer))
Exhibit.
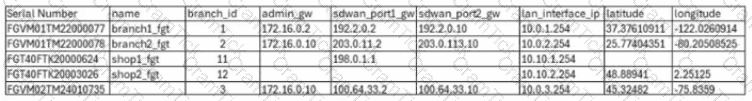
For your ZTP deployment, you review the CSV file shown in exhibit and note that it is missing important information. Which two elements must you change before you can import it into FortiManager? (Choose two.)


