FusionCompute adopts hardware-assisted virtualization technology to reduce memory virtualization overhead.
On FusionAccess, modifying or deleting a full copy template will affect the virtual machines created using the template.
Programs and data must be loaded into memory for CPU processing, and then be placed on external storage for long-term preservation.
In compute virtualization, which of the following is the operating system running on a virtual machine (VM)?
Which of the following statements aretrueabout the features and functions of the FusionCompute virtualization suite?
Which of the following statements are true about system encapsulation and Sysprep (system encapsulation tool) for creating a full copy template on FusionAccess?
In FusionCompute, which of the following statements are false about security groups?
Which of the following statements istrueabout the FusionCompute storage architecture?
Common storage networks include direct attached storage (DAS), network attached storage (NAS), and storage area network (SAN). SANs are divided into Fibre Channel storage area networks (FC SANs) and IP storage area networks (IP SANs).
Which of the following storage types isrecommendedfor VRM deployment during Huawei FusionCompute installation?
On FusionAccess software deployment, if multiple FusionAccess systems share a License, the License component should be deployed independently.
FusionCompute supports the following memory overcommitment technologies: memory sharing, memory swapping, and memory ballooning. After host memory overcommitment is enabled in cluster resource control, one of the preceding memory overcommitment technologies needs to be selected.
Which of the following statements isfalseabout the development of cloud computing architecture?
In virtualization, KVM and Xen are typical hardware-assisted virtualization technologies. They implement virtualization based on kernel modules in the operating system.
On FusionAccess, if a full copy VM cannot be re-assigned after being unassigned, which of the following assignment types does the full copy VM use?
FusionAccess application policies allow users to use VM desktops. Match the following application scenarios with their operations

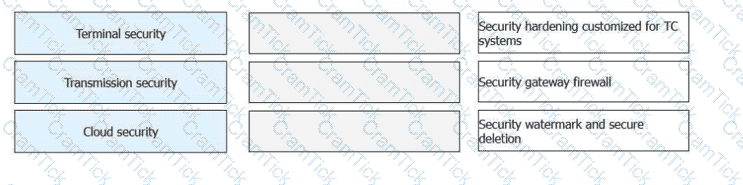
FusionAccess provides three protection mechanisms and 11 key measures to prevent data from being stored locally and make behaviors traceable and processes auditable, enhancing
end-to-end security. Match the key measures with the following protection mechanisms.
For a small enterprise with no more than 100 employees, using the FusionAccess gateway and load balancer deployment solution for office scenarios, which of the following plans isrecommended?
In Huawei FusionCompute, a VM running Linux is created. In this scenario, which of the following does the guest OS run in?
On FusionAccess, when creating afull copy, QuickPrep, or linked clone template, the template must be added to a domain.
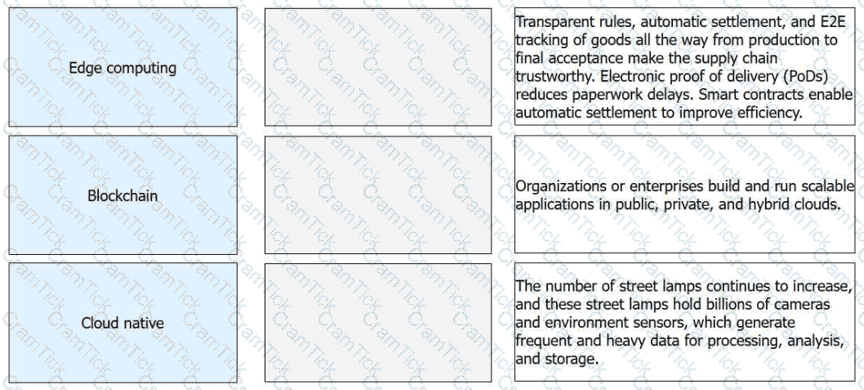
Match the emerging technologies with their respective features or application scenarios
FusionCompute integrates physical CPU and memory resources on hosts into a compute resource pool and divides the resources into virtual CPU and memory resources for VMs. The compute resources actually used by a VM cannot exceed the specifications of the hardware resources on the host because the CPU and memory resources used by the VM must be provided by the same host. If this host malfunctions, the system automatically assigns another host to the VM to provide compute resources.
Virtual Local Area Networks (VLANs) logically divide a physical LAN into multiple broadcast domains. Generally, hosts in a VLAN can directly communicate with each other, but those in different VLANs cannot. In this way, broadcast packets are confined within a single VLAN.
When FusionAccess is running properly, you are advised to restart infrastructure VMs once every quarter during off-peak hours. You can run the reboot command to restart Linux infrastructure VMs at the same time.
Which of the following statements aretrueabout deploying Compute Node Agent (CNA) and Virtual Resource Management (VRM) in Huawei FusionCompute?


