You have been instructed to look in the ArubaOS Security Dashboard's client list Your goal is to find clients mat belong to the company and have connected to devices that might belong to hackers
Which client fits this description?
What is an Authorized client as defined by ArubaOS Wireless Intrusion Prevention System (WIP)?
You are troubleshooting an authentication issue for Aruba switches that enforce 802 IX10 a cluster of Aruba ClearPass Policy Manager (CPPMs) You know that CPPM Is receiving and processing the authentication requests because the Aruba switches are showing Access-Rejects in their statistics However, you cannot find the record tor the Access-Rejects in CPPM Access Tracker
What is something you can do to look for the records?
You have an HPE Aruba Networking Mobility Controller (MC) that is locked in a closet. What is another step that HPE Aruba Networking recommends to protect the MC from unauthorized access?
What is an Authorized client, as defined by AOS Wireless Intrusion Prevention System (WIP)?
Device A is contacting https://arubapedia.arubanetworks.com. The web server sends a certificate chain. What does the browser do as part of validating the web server certificate?
What is a consideration for using MAC authentication (MAC-Auth) to secure a wired or wireless connection?
Refer to the exhibit, which shows the settings on the company’s MCs.
— Mobility Controller
Dashboard General Admin AirWave CPSec Certificates
Configuration
WLANsv Control Plane Security
Roles & PoliciesEnable CP Sec
Access PointsEnable auto cert provisioning:
You have deployed about 100 new Aruba 335-APs. What is required for the APs to become managed?
What is one difference between EAP-Tunneled Layer security (EAP-TLS) and Protected EAP (PEAP)?
Your AOS solution has detected a rogue AP with Wireless Intrusion Prevention (WIP). Which information about the detected radio can best help you to locate the rogue device?
The monitoring admin has asked you to set up an AOS-CX switch to meet these criteria:
Send logs to a SIEM Syslog server at 10.4.13.15 at the standard TCP port (514)
Send a log for all events at the "warning" level or above; do not send logs with a lower level than "warning"The switch did not have any "logging" configuration on it. You then entered this command:AOS-CX(config)# logging 10.4.13.15 tcp vrf defaultWhat should you do to finish configuring to the requirements?
What is a benefit of Protected Management Frames (PMF). sometimes called Management Frame Protection (MFP)?
What is a guideline for creating certificate signing requests (CSRs) and deploying server Certificates on ArubaOS Mobility Controllers (MCs)?
Refer to the exhibit.
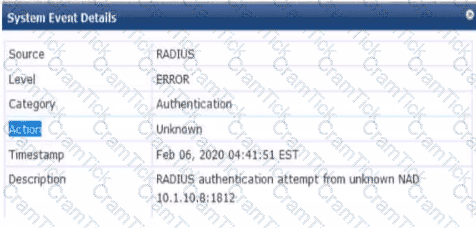
You are deploying a new ArubaOS Mobility Controller (MC), which is enforcing authentication to Aruba ClearPass Policy Manager (CPPM). The authentication is not working correctly, and you find the error shown In the exhibit in the CPPM Event Viewer.
What should you check?
What is one way that Control Plane Security (CPSec) enhances security for the network?
You have been instructed to look in an AOS Security Dashboard’s client list. Your goal is to find clients that belong to the company and have connected to devices that might belong to hackers.
Which client fits this description?
A client has accessed an HTTPS server at myhost1.example.com using Chrome. The server sends a certificate that includes these properties:
Subject name: myhost.example.com
SAN: DNS: myhost.example.com; DNS: myhost1.example.com
Extended Key Usage (EKU): Server authentication
Issuer: MyCA_SigningThe server also sends an intermediate CA certificate for MyCA_Signing, which is signed by MyCA. The client’s Trusted CA Certificate list does not include the MyCA or MyCA_Signing certificates.Which factor or factors prevent the client from trusting the certificate?
You have configured a WLAN to use Enterprise security with the WPA3 version.
How does the WLAN handle encryption?
What is a reason to set up a packet capture on an Aruba Mobility Controller (MC)?
You are configuring ArubaOS-CX switches to tunnel client traffic to an Aruba Mobility Controller (MC). What should you do to enhance security for control channel communications between the switches and the MC?
A customer has an AOS-10 network infrastructure. The customer is looking for a solution that can classify many different types of devices, including IoT devices. Which solution should you explain can provide these capabilities?
What is one practice that can help you to maintain a digital chain of custody in your network?
How can hackers implement a man-in-the-middle (MITM) attack against a wireless client?
What is a use case for tunneling traffic between an Aruba switch and an AruDa Mobility Controller (MC)?
Refer to the exhibit, which shows the current network topology.
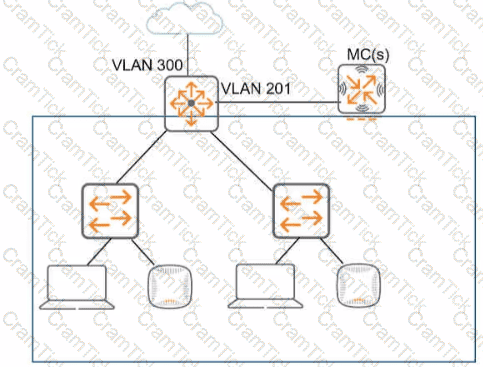
You are deploying a new wireless solution with an Aruba Mobility Master (MM). Aruba Mobility Controllers (MCs). and campus APs (CAPs). The solution will Include a WLAN that uses Tunnel for the forwarding mode and Implements WPA3-Enterprise security
What is a guideline for setting up the vlan for wireless devices connected to the WLAN?
What is one way that Control Plane Security (CPsec) enhances security for me network?
A company is deploying ArubaOS-CX switches to support 135 employees, which will tunnel client traffic to an Aruba Mobility Controller (MC) for the MC to apply firewall policies and deep packet inspection (DPI). This MC will be dedicated to receiving traffic from the ArubaOS-CX switches.
What are the licensing requirements for the MC?
An MC has a WLAN that enforces WPA3-Enterprise with authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). The WLAN's default role is set to guest. A Mobility Controller (MC) has these roles configured on it:
authenticated
denyall
guest
general-access
guest-logon
logon
stateful-dot1x
switch-logon
voiceA client authenticates. CPPM returns an Access-Accept with an Aruba-User-Role VSA set to general_access. What role does the client receive?
An organization has HPE Aruba Networking infrastructure, including AOS-CX switches and an AOS-8 mobility infrastructure with Mobility Controllers (MCs) and APs. Clients receive certificates from ClearPass Onboard. The infrastructure devices authenticate clients to ClearPass Policy Manager (CPPM). The company wants to start profiling clients to take their device type into account in their access rights.
What is a role that CPPM should play in this plan?
A company has Aruba Mobility Controllers (MCs). Aruba campus APs. and ArubaOS-CX switches. The company plans to use ClearPass Policy Manager (CPPM) to classify endpoints by type The ClearPass admins tell you that they want to run Network scans as part of the solution
What should you do to configure the infrastructure to support the scans?
What is a consideration for implementing wireless containment in response to unauthorized devices discovered by ArubaOS Wireless Intrusion Detection (WIP)?
Refer to the exhibit.
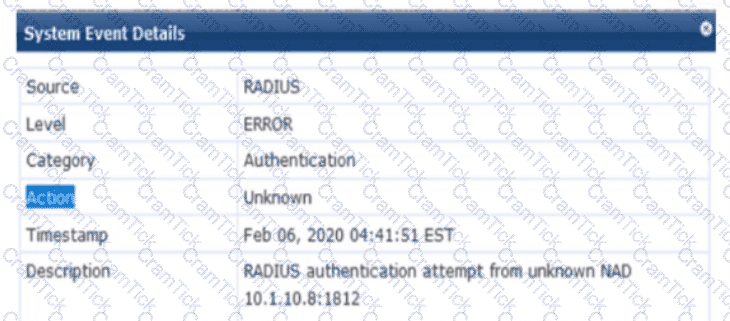
You are deploying a new HPE Aruba Networking Mobility Controller (MC), which is enforcing authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). The authentication is not working correctly, and you find the error shown in the exhibit in the CPPM Event Viewer.
What should you check?
A company has added a new user group. Users in the group try to connect to the WLAN and receive errors that the connection has no Internet access. The users cannot reach any resources. The first exhibit shows the record for one of the users who cannot connect. The second exhibit shows the role to which the ArubaOS device assigned the user's client.
What is a likely problem?
A company has a WLAN that uses Tunnel forwarding mode and WPA3-Enterprise security, supported by an Aruba Mobility Controller (MC) and campus APs (CAPs). You have been asked to capture packets from a wireless client connected to this WLAN and submit the packets to the security team.
What is a guideline for this capture?
Aruba-ACNSA | HPE6-A78 Questions Answers | HPE6-A78 Test Prep | Aruba Certified Network Security Associate Exam Questions PDF | HPE6-A78 Online Exam | HPE6-A78 Practice Test | HPE6-A78 PDF | HPE6-A78 Test Questions | HPE6-A78 Study Material | HPE6-A78 Exam Preparation | HPE6-A78 Valid Dumps | HPE6-A78 Real Questions | Aruba-ACNSA HPE6-A78 Exam Questions


