What steps are part of the Key Management workflow when a wireless device is roaming from AP1 to AP2? (Select two.)
A customer wants to provide wired security as close to the source as possible The wired security must meet the following requirements:
-allow ping from the IT management VLAN to the user VLAN
-deny ping sourcing from the user VLAN to the IT management VLAN
The customer is using Aruba CX 6300s
What is the correct way to implement these requirements?
You need to have different routing-table requirements with Aruba CX 6300 VSF configuration
Assuming the correct layer-2 VLAN already exists how would you create a new OSPF configuration for a separate routing table?
In an ArubaOS 10 architecture using an AP and a gateway, what happens when a client attempts to join the network and the WLAN is configured with OWE?
A company is in the planning stages to migrate to all their wireless domain laptops from WPA2 from WPA2 EAP-PEAP to EAP-TLS with machine Authentication. The administrator is testing a new Group Policy (GPO) that was pushed to only a few windows domain Laptops. The policy will configure the wireless profile to perform machine and certificate-based authentication.
To support this new initiative the administrator also configured a new HPE Aruba Networking ClearPass 802.1X wireless service that only allows devices that successfully perform machine and certificate-based authentication. After successfully pushing the GPO, the Windows laptops are unable to join the configured ‘’secure_wireless’’ SSID as shown below.
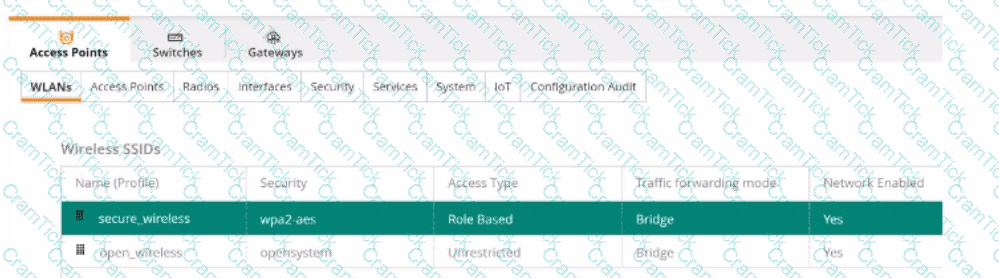
Which configuration setting would resolve this issue?
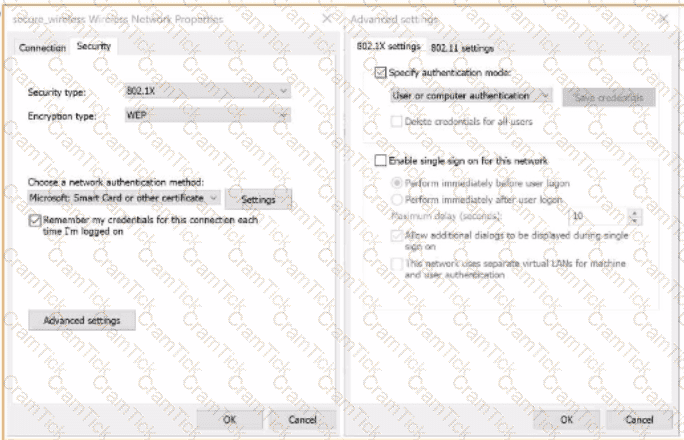
A)
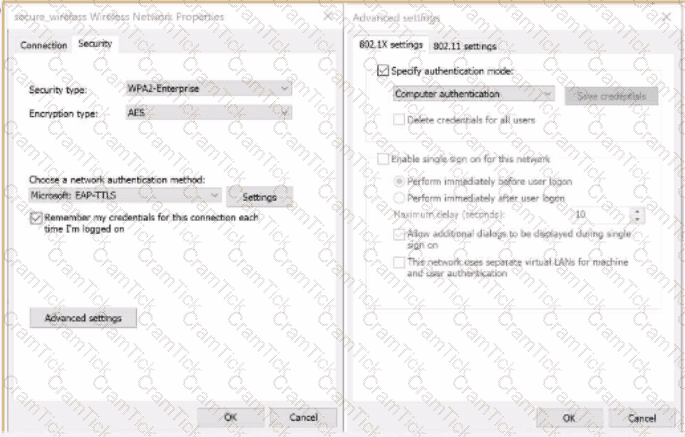
B)
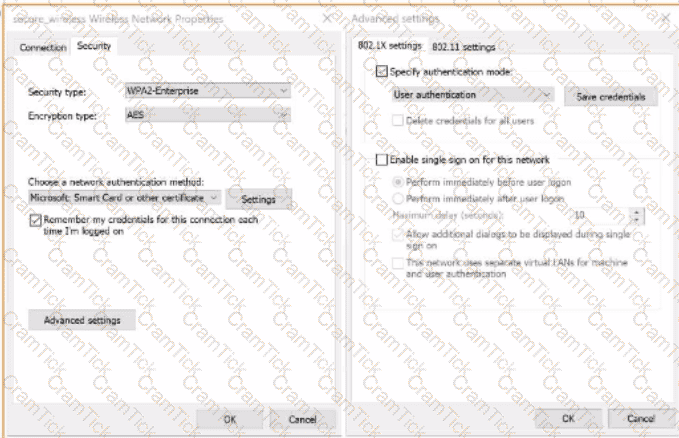
C)
D)

You are working on a network where the customer has a dedicated router with redundant Internet connections Tor outbound high-importance real-time audio streams from their datacenter All of this traffic.
• originates from a single subnet
• uses a unique range of UDP ports
• is required to be routed to the dedicated router
All other traffic should route normally The SVI for the subnet containing the servers originating the traffic is located on the core routing switch in the datacenter What should be configured?
Your Director of Security asks you to assign AOS-CX switch management roles to new employees based on their specific job requirements. After the configuration was complete, it was noted that a user assigned with the auditors role did not have the appropriate level of access on the switch.
The user was not allowed to perform firmware upgrades and a privilege level of 15 was not assigned to their role. Which default management role should have been assigned for the user?
A customer wants to enable wired authentication across all their CX switches One of the requirements is that the switch must be able to authenticate a single computer connected through a VoIP phone.
Which feature should be enabled to support this requirement?
A customer is using a legacy application that communicates at layer-2. The customer would like to keep this application working across the campus which is connected via layer-3. The legacy devices are connected to Aruba CX 6300 switches throughout the campus.
Which technology minimizes flooding so the legacy application can work efficiently?
Your customer is having connectivity issues with a newly-deployed Microbranch group The access points in this group are online in Aruba Central, but no VPN tunnels are forming.
What is the most likely cause of this issue?
Refer to the image.
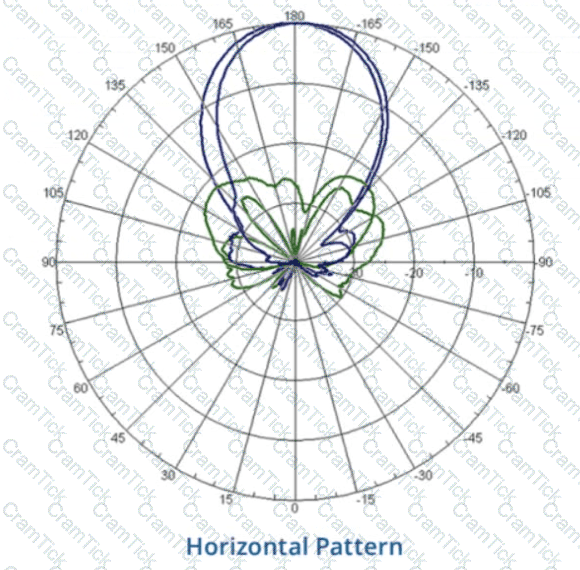
Your customer is complaining of weak Wi-Fi coverage in their office. They mention that the office on the other side of the hall has much better signal What is the likely cause of this issue7
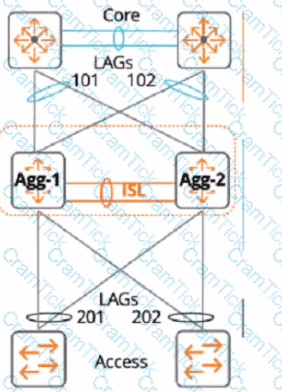
A customer just upgraded aggregation layer switches and noticed traffic dropping for 120 seconds after the aggregation layer came online again. What is the best way to avoid having this traffic dropped given the topology below?
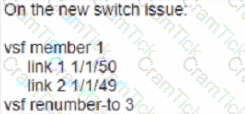
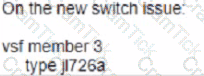
Your customer has an Aruba CX 6200F VSF stack with two switches. A third member (JL726A) needs to be added to the VSF configuration. What e the configuration that enables the new devices to join the VSF?
A)
B)
C)
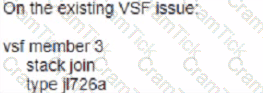
D)
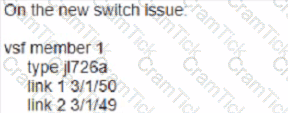
You are building a configuration in Central that will be used for a standardized network design for small sites for your company, you want to use GUI configuration for gateways and Aps, while template configuration for switches. You need to align with Aruba best practices.
Which set of actions will satisfy these requirements?
With the Aruba CX switch configuration, what is the Active Gateway feature that is used for and is unique to VSX configuration?
The administrator notices that wired guest users that have exceeded their bandwidth limit are not being disconnected Access Tracker in ClearPass indicates a disconnect CoA message is being sent to the AOS-CX switch.
An administrator has performed the following configuration
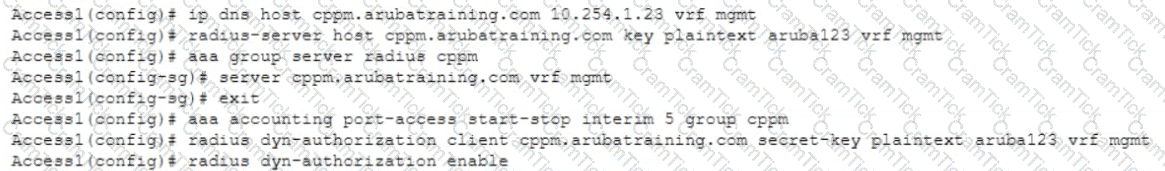
What is the most likely cause of this issue?
Match the solution component of HPE Aruba network Central NetConductor. (Options may be used more than once or not at all.)

You are are doing tests in your lab and with the following equipment specifications:
• AP1 has a radio that generates a 16 dBm signal.
• AP2 has a radio that generates a 13 dBm signal.
• AP1 has an antenna with a gain of 8 dBi.
• AP2 has an antenna with a gain of 12 dBi. The antenna cable for AP1 has a 4 dB loss. The antenna cable for AP2 has a 3 dB loss.
What would be the calculated Equivalent Isotropic Radiated Power (EIRP) for AP1?
Which Aruba AP mode is sending captured RF data to Aruba Central for waterfall plot?
A company recently upgraded its campus switching infrastructure with Aruba 6300 CX switches. They have implemented 802.1X authentication on edge ports where laptop and loT devices typically connect An administrator has noticed that for PoE devices the pons are delivering the maximum wattage instead of what the device actually needs Upon connecting the loT devices, the devices request their specific required wattage through information exchange
A network administrator is troubleshooting some issues guest users are having when connecting and authenticating to the network The access switches are AOS-CX switches.
What command should the administrator use to examine information on which role the guest user has been assigned?
A customer is looking Tor a wireless authentication solution for all of their loT devices that meet the following requirements
- The wireless traffic between the IoT devices and the Access Points must be encrypted
- Unique passphrase per device
- Use fingerprint information to perform role-based access
Which solutions will address the customer's requirements? (Select two.)
You are deploying Aruba CX 6300's with the customers requirement to only allow one (1) VoIP phone and one (1) device.
The following local role gets assigned to the phone
port-access rote VoIP device-traffic-class voice
What set of commands best fits this requirement?
Your customer currently has two (2) 5406 modular switches with MSTP configured as their core switches. You are proposing a new solution. What would you explain regarding the AOS-CX VSX switch pair when the Spanning-tree needs to be set up?
You are doing tests in your lab and with the following equipment specifications
• AP1 has a radio that generates a 10 dBm signal
• AP2 has a radio that generates a 11 dBm signal
• AP1 has an antenna with a gain of 9 dBi
• AP2 has an antenna with a gain of 12 dBi.
• The antenna cable for AP1 has a 2 dB loss
• The antenna cable for AP2 has a 3 dB loss
What would be the calculated Equivalent Isotropic Radiated Power (EIRP) for APT?
Your customer is interested in hearing more about how roles can help keep consistent policy enforcement in a distributed overlay fabric How would you explain this concept to them''
A customer is using Aruba Cloud Guest, but visitors keep complaining that the captive portal page keeps coming up after devices go to sleep Which solution should be enabled to deal with this issue?
What are two advantages of splitting a larger OSPF area into a number of smaller areas? (Select two )
A customer wants to deploy a Gateway and take advantage of all the SD-WAN features. Which persona role option should be selected?


