A company wants an administrator to perform a vulnerability test. The administrator finds the company has a POTS phone system. Which of the following can the administrator use to point out the phone system vulnerability?
At which of the following locations does the responsibility of a Telco provider cease?
A technician is configuring a new DSL router. The technician can communicate with the LAN, but not the WAN. Which of the following is the MOST likely cause?
A user is unable to connect to a remote computer using RDP. The technician checks the firewall rules and notes that there is no rule that blocks RDP. Which of the following features of the firewall is responsible for blocking RDP?
The wireless network inside a large training room has been saturated with client requests. Most of the client requests are coming from smartphones and laptops. The network technician has been tasked with increasing the performance of the wireless access point. Which of the following would BEST accomplish this?
An administrator is using a packet sniffer to try to determine what is causing the traffic on the network. The administrator sees a lot of packets on port 25. Which of the following traffic types is MOST likely using port 25?
Which of the following will allow a technician to monitor all network traffic when connected to a mirror port?
A company needs to find a way to best route latency-sensitive traffic appropriately on an already congested network. Which of the following would be BEST suited for this purpose?
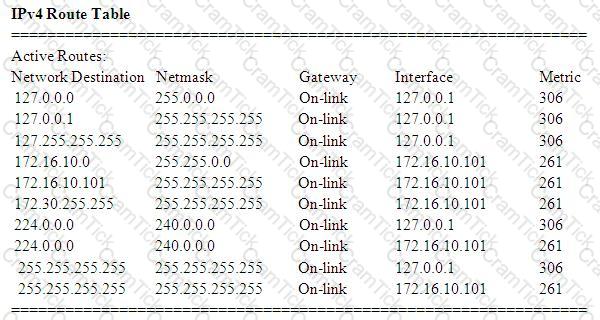
A technician is troubleshooting Internet connectivity for a PC. Which of the following is MOST likely the reason for Internet connectivity issues upon inspecting the routing table?
Which of the following can a technician use when installing a wireless network in a lounge to prevent inappropriate website images?
A company has a server with redundant power supplies. Which of the following is this an example of?
Which of the following should be installed to prevent inappropriate websites from being viewed?
A network technician is troubleshooting a user’s connectivity problem, and has determined a probable cause. The technician is at which step in the troubleshooting methodology?
In a newly installed LAN, the network administrator receives many calls about intermittent or slow connectivity to the authentication server. Which of the following could cause this problem? (Select TWO).
A small office is looking to deploy wireless to cover one half of the work area only. The technician is restricted to suspending the WAP in the middle of the office due to network jack limitations. Which of the following antenna types would BEST meet these requirements?
Which of the following network media connectors can use a MAXIMUM of two copper wire pairs?
A company has just installed a new network switch for an expanding department. The company is also piloting the use of a VoIP phone system for this department. Which of the following should be enabled on the new network switch?
A network administrator currently collects log files from several different servers. Which of the following would allow the network administrator to collect log files on a centralized host?
Which of the following reasons would MOST likely be used to implement QoS and traffic shaping solutions?
A user’s computer is unable to access the Internet. Which of the following utilities can a technician use to determine if DNS is working?
In a SOHO environment, placing a VoIP unit on the outside edge of a LAN router enhances which of the following network optimization methods?
A technician is looking to create a new network cable. Which of the following tools would assist in creating and testing a cable properly? (Select TWO).
A large company has experienced Internet slowdowns as users have increased their use of the Internet. Which of the following can the Network Administrator use to determine the amount of bandwidth used by type of application?
Which of the following tools would a technician use to terminate CAT6 wires to the inside of the wall jack?
A technician is upgrading the wiring in an older office building. The building currently contains some CAT3, CAT5, and CAT6 cables. The technician cannot visually distinguish between the cables because they are all the same color. Which of the following tools would help the technician determine which wires are the CAT3 and CAT5 cables needing to be replaced with CAT6 ones?
An administrator has added QoS settings to the LAN switches prioritizing RTP. Which of the following systems is the Administrator MOST concerned with in this scenario?
A user calls the helpdesk to report not being able to access network resources over the company’s Wi-Fi connection. During information gathering, the user mentions that the wireless network their computer is signed into is not the same name as it had been previously. Which of the following is the underlying cause?
A network technician is setting up a wireless access point that would only allow a certain laptop to be able to access the WAP. By using ACL, which of the following would be filtered to ensure only the authorized laptop can access the WAP?
A user reports that they keep getting disconnected on the wireless network. After further investigation, the technician confirms that this occurs only in that user’s office. Which of the following would MOST likely cause them to lose their connection?
A network technician is designing a SOHO environment where cost is a consideration. The requirements include access to the Internet and access to the guest house which is 100 feet away. The location of the Internet modem is located in the main house. Which of the following is the BEST option to accomplish these requirements?
The network support team is constantly getting calls from users in a specific area of an office building. The users are able to connect to the office wireless network, but they sometimes disconnect or experience very slow download speeds. Which of the following is MOST likely the problem?
A technician working for a company with a wireless network named WirelessA notices a second wireless network named WirelessB. WirelessB is MOST likely a:
A technician has determined that calls placed over a wireless connection are breaking up and the speaker’s voices are delayed. This is making conversation difficult. This is a symptom of which of the following network issues?
A client has just leased a new office space in a busy commercial building and would like to install a wireless network. Several other tenants are on the same floor. Multiple wireless networks are present in the building. Which of the following can be changed on the client’s wireless network to help ensure that interference from other wireless networks is at a minimum?
If a technician does not assign an IP address to a device, the DHCP server will assign the device a:
Which of the following WAN technology types are mainly used over POTS lines to provide Internet connectivity? (Select TWO).
Which of the following is a square shaped fiber connector that is slightly smaller than a standard copper network cable connector?
The network administrator installed a new dipole antenna that extends 100 feet (30.48 meters) from the existing AP. All components are correct, functional, and installed properly. However, during validation, there is a very weak signal coming from the antenna.
Which of the following is the MOST likely cause of the issue?
A technician needs to setup an Internet connection for a small office. There are five users that need the ability to use email and do online research. The office manager wants the connection to be always on and be as inexpensive as possible. Which of the following would BEST fit the needs of this office?
A technician testing an Ethernet card uses a cable wired with pins 1,2 to pins 3,6 on the same RJ-45 plug. Which of the following describes what the technician is using?
A user does not have network connectivity. While testing the cable the technician receives the below reading on the cable tester:
1-----------1
2-----------2
3-----------3
4-----------4
5-----------5
6-----------6
7-----------7
8-----------8
Which of the following should the technician do NEXT?
Several users are reporting that they are unable to connect to the network. After further investigation, the network administrator notices that a newly configured Layer 2 device lost its configuration. Which of the following MOST likely caused the issue?
A technician is having issues accessing the Internet from the workstation. They are able to ping the DNS server and their default gateway. Which of the following commands can be used to verify DNS is functioning properly?
A company has recently allowed its employees to telecommute two days a week. The employees MUST have a minimum of 1Mbps non-shared connection to the Internet. Which of the following MUST the employees have at their home in order to connect to the Internet?
A technician is installing a switch that will be used for VoIP and data traffic. The phones do not support the 802.3af standard. Which of the following should the technician configure on the switch?
A technician has been dispatched to investigate connectivity problems of a recently renovated office. The technician has found that the cubicles were wired so that the network cables were run inside the conduit with the electrical cabling. Which of the following would MOST likely resolve the connectivity issue?
After a network technician has added a new workstation and cabling to the network, users report the network is very slow. The activity lights on all switches are blinking rapidly, showing large amounts of traffic. Which of the following is the BEST explanation for the traffic?
Ann, a technician, is installing network cables for an office building. Some of the cables are not showing active on the switch even when moved to different ports. Which of the following is MOST likely the cause?
Compare the settings below to determine which of the following issues is preventing the user from connecting to a wireless network.
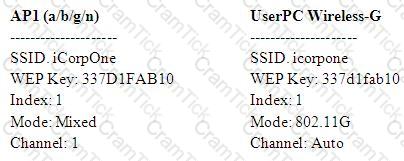
Which of the following settings is incorrect on the client?
A technician installs a wireless router on an existing network by connecting it directly to the firewall. By default, the main network is a Class A network, while the wireless network is a Class C network. After the wireless router is installed, users connected to the wireless network report they are unable to connect to the Internet. Which of the following needs to be configured to BEST resolve this issue?
Which of the following must a technician enable on a switch in order to be able to view all of the packets traversing a switch using a packet sniffer?
A technician is assigned the task of connecting two buildings 125 meters apart (410 ft.). Which of the following cable types should the technician consider?
Which of the following types of technologies should be used to provide a MAXIMUM 10 GB speed to a multi-mode fiber network?
Which of the following WAN technologies uses an analog phone line to transmit data?
Which of the following wiring distribution is used to connect wiring from equipment inside a company to carrier cabling outside a building?
A security appliance is blocking a DDoS attack on the network. Which of the following logs would be used to troubleshoot the traffic patterns trying to go across the network?
Which of the following is the MOST secure way to prevent malicious changes to a firewall?
A server administrator, Ann, is deploying a server that she wants to mitigate intrusions from zero day exploits. Which of the following should be deployed?
A network administrator is responding to a statement of direction made by senior management to implement network protection that will inspect packets as they enter the network. Which of the following technologies would be used?
Which of the following network appliances will only detect and not prevent malicious network activity?
Which of the following protocols provides a secure connection between two networks?
Which of the following would be the BEST solution for an IDS to monitor known attacks?
A network technician is doing a wireless audit and finds an SSID that does not match the company’s SSID. The company uses the SSID of ABC123, and the SSID the technician found is Default. Which of the following threats did the network technician find?
Which of the following OSI model layers are present in the application layer of the TCP/IP model? (Select TWO).
A technician has been tasked to set-up a managed switch. Which of the following will the technician need to accomplish this task?
A technician, Joe, visits a site that has reported a network down emergency. He immediately reboots the switches and the router since the network is down. Which of the following network troubleshooting methodology steps should Joe have performed FIRST?
A user reports lack of network connectivity on their desktop. Which of the following is the FIRST step of the network troubleshooting methodology that the technician should perform?
Layers 5, 6, and 7 from the OSI model correspond to which of the following layers of the TCP/IP model?
When a loop occurs, which of the following STP components determines which port to disable?
Which of the following port numbers needs to be open on a firewall to allow FTP traffic?
Which of the following network topologies describes a network where each node is connected to multiple devices?
A small office needs to connect one new system to their network in a distant office, but does not have the resources to install a new Ethernet wall jack, and does not want to use wireless. Which of the following is a simple, cost effective option for providing connectivity?
An organization only has a single public IP address and needs to host a website for its customers. Which of the following services is required on the network firewall to ensure connectivity?
A technician enters a username and password once and can access multiple databases without being prompted to reenter their password. This is an example of which of the following?
Which of the following would be used to check whether a DoS attack is taking place from a specific remote subnet?
A network administrator decides to secure their small network by allowing only specific MAC addresses to gain access to the network from specific switches. Which of the following is described by this example?
Which two layers of the OSI model make up the TCP/IP model Network Interface layer?
A technician replaces a failed router in an office with the same model unit using the default settings. After the installation, the technician reboots all of the PCs and servers. Upon reboot some of the PCs are receiving IP addresses on the same subnet as the new router; other PCs are receiving addresses on the same subnet as the servers. Which of the following most likely describes the issue?
A network where all traffic feeds through a centralized gateway uses which of the following topologies?
Which of the following subnet masks indicate a subnet with exactly 254 assignable IP addresses?
Which of the following commands will provide an administrator with the number of hops a packet takes from host to host?
Which of the following authentication solutions use tickets that include valid credentials to access additional network resources?
A network technician is assigned to view websites that a user has visited. Which of the following should the technician review to find this information?
A client’s computer is unable to access any network resources. Which of the following utilities can a technician use to determine the IP address of the client’s machine?
Which of the following allows for groups of ports on the same switch to operate as a part of different segmented networks?
Which of the following STP states indicates an inactivated port due to a loop?
Which of the following OSI model layers is used to order packets which may have arrived out of order?
Which of the following correctly lists the layers of the OSI model starting at Layer 1?
Which of the following features can BEST be used to facilitate authorized remote access to a network?
Joe, a technician, is attempting to connect two hubs to add a new segment to his local network. He uses one of his CAT5 patch cables to connect them; however, he is unable to reach the new network segment from his workstation. He can only connect to it from a workstation within that segment. Which of the following is MOST likely the problem?
A user is connecting to the Internet at an airport through an ad-hoc connection. Which of the following is the MOST likely security threat?
An administrator would like to provide outside access to the company web server and separate the traffic from the local network. Which of the following would the administrator use to accomplish this?
A network administrator wants to add the firewall rule to allow SSH traffic to the FTP server with the assigned IP 192.168.0.15 from the Internet. Which of the following is the correct firewall rule?
Which of the following are considered AAA authentication methods? (Select TWO).
Which of the following security appliances would be used to only analyze traffic and send alerts when predefined patterns of unauthorized traffic are detected on the network?
Which of the following monitoring devices are used only to recognize suspicious traffic from specific software?
An administrator wants to restrict traffic to FTP sites regardless of which PC the request comes from. Which of the following would BEST accomplish this?
Which of the following is the radio frequency and data rate for 802.11g as specified by the IEEE standards?
A technician installs a new CAT6 cable from one end of the office building to another, a total distance of 600 feet (182.88 meters). When a laptop is connected to the cable, it cannot connect to the Internet. Which of the following is MOST likely the cause of this problem?
Which of the following cable types use pins 1 and 2 to transmit and 3 and 6 to receive?
Which of the following wireless standards is the only one capable of operating in any of the 802.11 wireless spectrums?
An administrator has added four switches to a campus network. The switch in wiring closet A is only connected to the switch in wiring closet C. The switch in wiring closet B is connected to the switch in wiring closet C as well as wiring closet D. The switch in wiring closet D is only connected to the switch in wiring closet B. Which of the following topologies is represented in this design?
Which of the following is the only standard that can operate at either frequency?
CompTIA Network+ | JK0-019 Questions Answers | JK0-019 Test Prep | CompTIA E2C Network + Certification Exam Questions PDF | JK0-019 Online Exam | JK0-019 Practice Test | JK0-019 PDF | JK0-019 Test Questions | JK0-019 Study Material | JK0-019 Exam Preparation | JK0-019 Valid Dumps | JK0-019 Real Questions | CompTIA Network+ JK0-019 Exam Questions