You want to control when cluster failovers occur.
In this scenario, which two specific parameters would you configure on an SRX Series device? (Choose two.)
Which two statements are true about the fab interface in a chassis cluster? (Choose two.)
Which two statements are true about mixing traditional and unified security policies? (Choose two.)
Which solution enables you to create security policies that include user and group information?
Which two devices would you use for DDoS protection with Policy Enforcer? (Choose two.)
Which two types of SSL proxy are available on SRX Series devices? (Choose two.)
You need to deploy an SRX Series device in your virtual environment.
In this scenario, what are two benefits of using a CSRX? (Choose two.)
You are asked to create an IPS-exempt rule base to eliminate false positives from happening.
Which two configuration parameters are available to exclude traffic from being examined? (Choose two.)
Exhibit
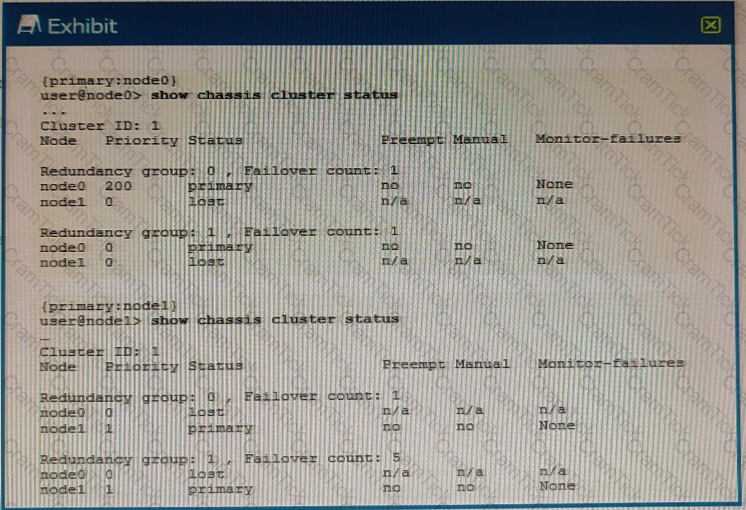
Referring to the exhibit, what do you determine about the status of the cluster.
You are configuring logging for a security policy.
In this scenario, in which two situations would log entries be generated? (Choose two.)
Exhibit
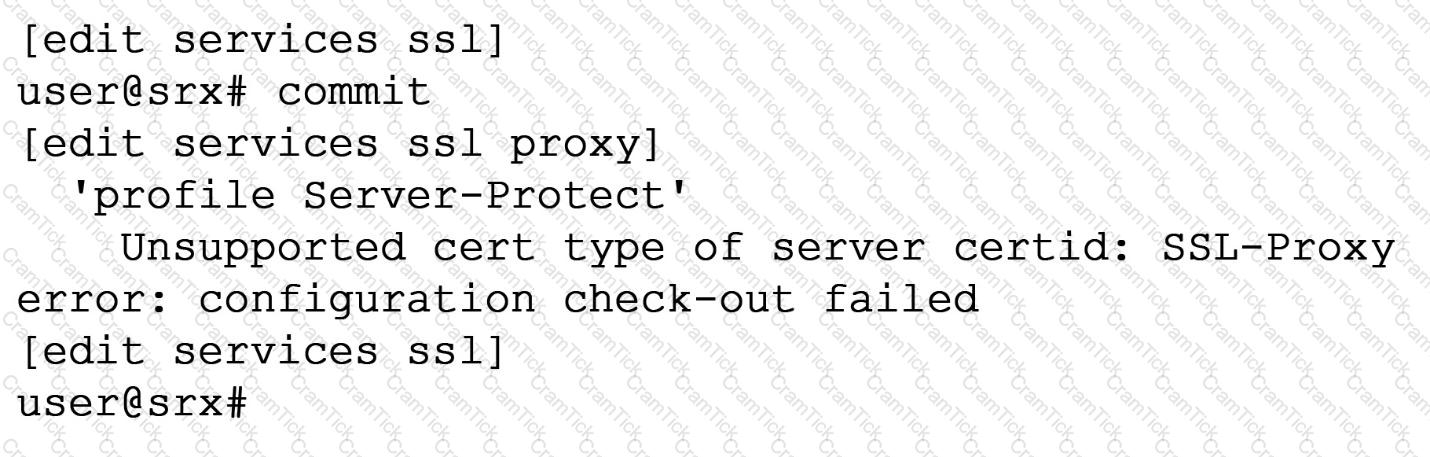
When trying to set up a server protection SSL proxy, you receive the error shown. What are two reasons for this error? (Choose two.)
While working on an SRX firewall, you execute the show security policies policy-name
Which function does this command accomplish?
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
Exhibit
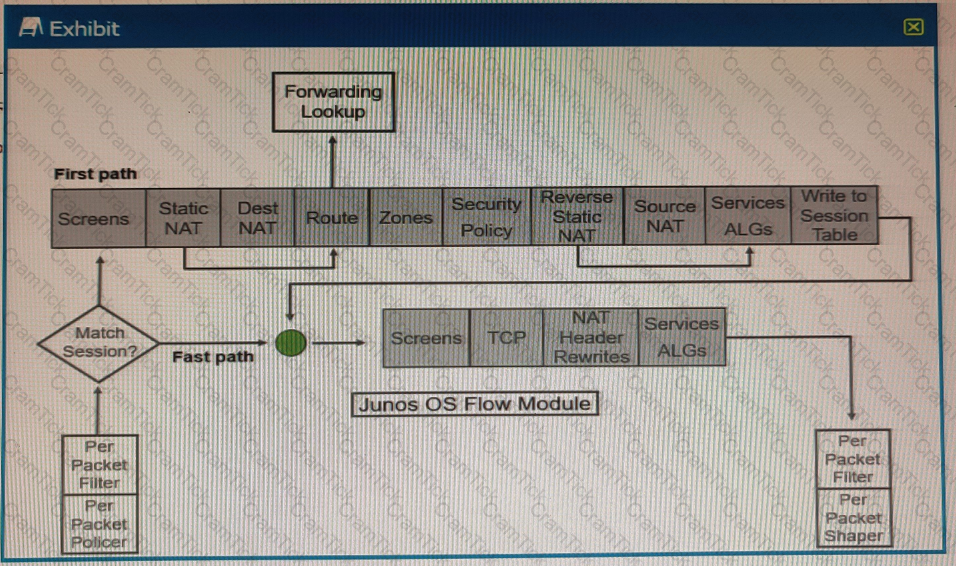
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?
Which two statements about SRX Series device chassis clusters are true? (Choose two.)
On an SRX Series firewall, what are two ways that Encrypted Traffic Insights assess the threat of the traffic? (Choose two.)
You want to permit access to an application but block application sub-Which two security policy features provide this capability? (Choose two.)
You are asked to determine how much traffic a popular gaming application is generating on your network.
Which action will you perform to accomplish this task?
Your JIMS server is unable to view event logs.
Which two actions would you take to solve this issue? (Choose two.)


