Company policy dictates that full backups are taken every Sunday evening, and incremental backups occur Monday through Saturday in the evening. If data loss were to occur on a Thursday before the backup window, which of the following is the number of backup sets that would be needed to retrieve the lost data come Friday morning?
A customer wants to set up a guest wireless network for visitors. The customer prefers to not have a password on the network. Which of the following should a technician set up to force guests to provide information before using the network?
A technician restored network connectivity on a user’s laptop. After validating full system functionality, which of the following steps should the technician take NEXT?
A network administrator has configured the network on each floor of a four-story building to have the following different subnets: 10.0.10.0/24, 127.0.0.0/24, 172.16.0.0/24, and 192.168.255.0/24. After implementing these networks, the administrator realizes there has been a mistake. Which of the following BEST describes the mistake?
Which of the following provides information about how often some devices fail so the IT department can take proactive measures?
A manufacturing company has signed an agreement with another company to collaborate on an upcoming project. Both companies require secure and persistent access to resources on each others' networks. Which of the following remote access technologies should the companies implement to satisfy their requirements?
Which of the following is a policy that communicates the guidelines for connecting personal employee devices to the corporate network?
A network administrator is deploying a new switch in an existing IDF. The current switch has only copper Ethernet ports available to use for the trunk ports. Which of the following cable types should the network administrator deploy?
A company has experienced a major security breach. Which of the following should the network administrator reference to determine the next steps?
A network technician needs to install the latest firmware on the switch to address a recently discovered vulnerability. Which of the following should the technician do to have a rollback plan in case of issues with the new firmware? (Choose two.)
A technician is required to install a new DOCSIS-based Internet connection. Which of the following medium types does this use?
Joe, a user, reports intermittent connectivity issues, but a technician notices that the only time Joe has issues is when he is logged into the database. Losing connection after authenticating to a database, but still having access to network resources such as file/print services and email, would MOST likely be caused by:
A network team at a large company has received funding for a WiFi refresh. One of the requirements in the RFP is the new WLAN infrastructure must provide APs that support multiple streams of information at the same time. For which of the following WiFi features is the network team looking?
Which of the following manages the delegation of physical equipment to the virtual components?
An attacker quickly gains administrative access to a network device. Which of the following MOST likely allowed the attacker to guess the password?
A network technician is coordinating the upgrade of the company’s WAP firmware with all the remote locations. The company has occasionally experienced errors when transferring large files to some of the remote offices. Which of the following should be used to ensure files arrive without modifications?
A small business utilizes a SOHO router and wishes to secure its existing wireless infrastructure. The business has fewer than ten devices, which are a mixture of old and new machines. Due to the varying ages of the machines, the latest wireless encryption methods may not be supported on all devices. Which of the following would be the MOST cost-effective method to add a layer of security while allowing all machines to connect?
A corporation has been the target of hackers who exploited TCP port 80. The network administrator is tasked with securing connections to the web server. Which of the following protocols should be implemented to BEST secure the web server? (Choose two.)
A technician purchasing equipment for a company has determined that several new employees will require new wired workstations. Which of the following is the network technician likely to recommend to add the employees to the existing infrastructure?
Which of the following would be BEST for continually monitoring and alerting of possible attacks on a network?
A network technician is setting up a new web server on the company network. One of the requirements for the web server is to ensure the end users can securely authenticate to the application to perform their job duties. Which of the following ports should the network technician request from the firewall team to comply with this requirement?
A network technician is attempting to update firmware on a router but cannot physically locate the router. Which of the following would show where to locate router?
Which of the following BEST describe the differences between an IDS and an IPS? (Choose two.)
A network technician is reviewing the following output from a router:
Which of the following is this an example of?
A network technician is reviewing the company phone system to make the necessary changes to a firewall configuration. Which of the following protocols are used in VoIP communication? (Choose two.)
A network administrator has signed up for service with a new ISP. The administrator was given the IP address of 172.17.10.254/30 to use on the external interface of the Internet-facing router. However, the network administrator cannot reach the Internet using that address. Which of the following is the MOST likely?
A vendor is installing an Ethernet network in a new hospital wing. The cabling is primarily run above the ceiling grid near air conditioning ducts and sprinkler pipes. Which of the following cable types is required for this installation'?
A network technician is reviewing switch ACLs to determine if they are causing communication issues with one PC. The PC’s IP address is 192.168.12.66. Which of the following is the network range found in the ACL that could have affected this PC?
Which of the following would a network technician MOST likely connect to power wireless access points in drop ceilings?
After several changes to the network, a technician needs to ensure a client is checking for new hostname and IP pairings. Which of the following commands should the technician use to force new lookups?
A network administrator Is configuring the 172.16.40.0/22 network for a new building. Which of the following is the number of hosts that will be supported on this network?
Ann. a user, reports that her desktop phone is not working on one cable. However, that cable provides connectivity to her laptop. A technician determines PoE is not provided to the end device. Which of the following is MOST likely the cause?
A technician has been asked to diagnose problems with DHCP addressing on a VLAN. The DHCP server responds to pings from the technician's machine. Which of the following should the technician use to help diagnose the problem?
A technician is installing a SOHO router. Which of the following should be performed on every installation and periodically maintained to prevent unauthorized access? (Choose two.)
Which of the following is used to purposely attack a system to exploit vulnerabilities?
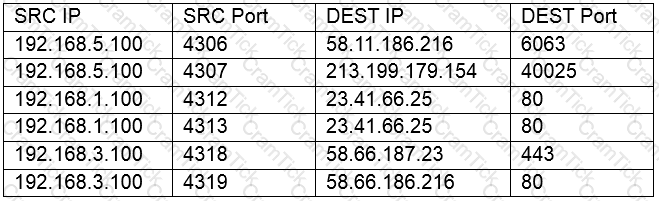
You have been tasked with testing a CAT5e cable. A summary of the test results can be found on the screen.
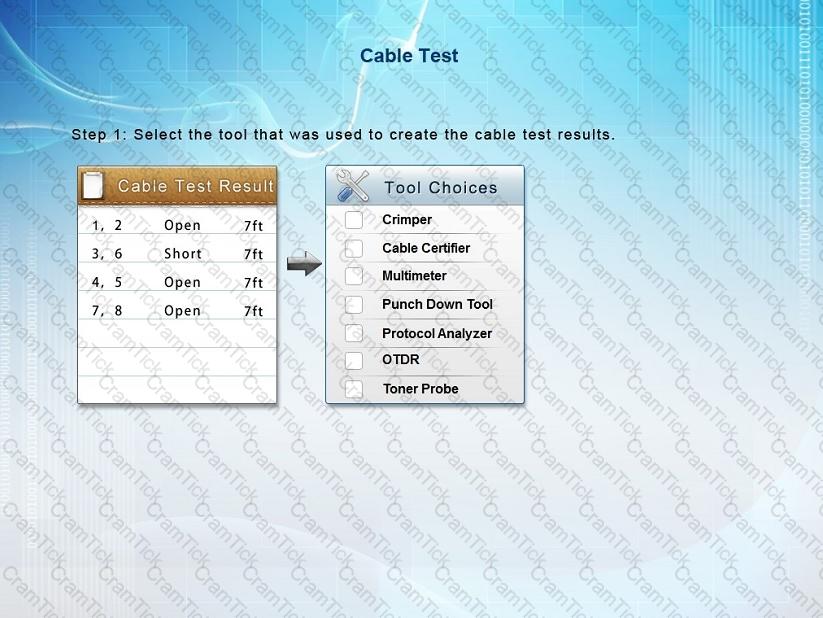
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the test results and select the option that explains the results. After you are done with your analysis, click the 'Submit Cable Test Analysis' button.
The network support team is responsible for managing connections in a large, multipurpose venue where maintaining physical security is difficult. Implementing which of the following standards would BEST help to prevent unauthorized connections to the wired network?
A large company uses an AAA server to manage network device access. The engineers can use their domain credentials to access all other servers. Currently, the network engineers cannot access the AAA server using domain credentials, but they can access it using a local account. Which of the following should the engineers update?
During a weekend event, several people reported they were unable to get onto the wireless network. On Monday, the technician could not find a problem. Which of the following is the MOST likely cause?
A network administrator has deployed a secure wireless network that authenticates using Active Directory network credentials so individual users are uniquely identified when connected to the WLAN. Which of the following wireless technologies has the administrator configured?
A technician has been assigned to capture packets on a specific switchport. Which of the following switch feature MUST be used to accomplish this?
An employee reports an error when visiting a website using SSL, and a message is displayed warning of an invalid certificate. Which of the following could be occurring?
A network administrator wants to ensure all traffic is inspected and abides by the AUP, and that malicious traffic is stopped. Which of the following features should be enabled on a firewall to meet this requirement?
A network technician has purchased a 10GBase-T switch and wishes to connect it to 30 computers with 10GB network cards. The computers are 225ft (69m) away, and all need to establish a 10 Gbps connection to meet business requirements. To minimize costs while still meeting these requirements, which of the following cable types should the technician choose?
A customer has submitted a request for a new wireless connection In the main office so visitors can reach the Internet to check their email. The customer is concerned about security and does not want visitors to be able to access the internal finance server. Which of the following BEST describes the correct configuration?
A technician is preparing to dispose of old network devices. Which of the following policies and best practices would outline procedures for removing sensitive information and configurations from surplus equipment?
A technician Is reviewing network device logs in an attempt to trace an attack that occurred on the network. Which of the following protocols would affect whether or not the technician can properly trace the attack through the network using the logs?
Which of the following protocols is used to transport outgoing mail across networks?
Which of the following policies prohibits a network administrator from using spare servers in the datacenter to mine bitcoins?
A network technician sets up a new schedule on the backup server. Management has informed the technician that a full backup does not need to be completed every day. The technician sets up weekly full backups. Which of the following should the technician configure for the remaining days to MINIMIZE the daily backup size?
A small company has decided to use a single virtual appliance to filter spam as well as reverse proxy and filter traffic to its internal web server. Which of the following has the company MOST likely deployed?
A network technician is setting up the wireless network for a company's new branch office. After doing a site survey, the technician discovers there is a lot of interference from 2.4GHz devices at the location on channel 11. Which of the following would be the BEST channel on which to set up the WAPs?
A Chief Information Security Officer (CISO) has decided to implement a secure and user-friendly way to connect to the corporate wireless network Each workstation will be authenticated individually using a unique certificate that will be deployed to the workstation by the organization's certificate authority. Which of the following authentication methods would meet this requirement?
Which of the following technologies should be used in high-throughput networks to reduce network overhead?
To achieve a more efficient and secure work environment, a company needs a way to control what is being accessed on the Internet using corporate resources. Which of the following devices should be used to accomplish this task? (Choose two.)
A network technician is assisting a user who has relocated to a newly constructed office space. The user has no network connectivity. A cable tester was used on the port and is reporting that the pairs are open. Which of the following should be used to remedy this problem?
A user in the marketing department reports the email server is down. The user has not received email for more than 24 hours. Which of the following should the network technician do to investigate this issue?
Which of the following DNS records would a technician need to update after migrating an organization's email server to a cloud-hosting provider?
A network administrator is responding to a help desk ticket, which states an unknown wireless access point is broadcasting in a specific area. Upon investigation, the administrator finds that a user brought a wireless access point from home and plugged it into the corporate network. This resulted in an attacker using the unsecured wireless LAN to gain access to the network. Which of the following should the network administrator have done to BEST prevent this problem?
A network technician receives reports indicating some users are unable to gain access to any network resources. During troubleshooting, the technician discovers the workstations have an IP address of 169.254.x.x. Which of the following is the MOST likely cause?
A Chief Information Officer (CIO) wants to improve the availability of a company's SQL database Which of the following technologies should be utilized to achieve maximum availability?
A user's computer is having trouble reaching a certain website Other branch locations do not have any issues reaching this website, and the user can reach all other websites A technician suspects there is a failure at an upstream router under The ISPs control. Which of the following commands should the technician run to confirm this suspicion''
A network administrator installed a WAP to extend the network. However, the company wants to contain the signal so it does not extend beyond the company's parking structure. Which of the following solutions would work BEST?
A technician has started a major network project to upgrade to a higher throughput standard. The technician will need to install new patch panels and breakout boxes to support this infrastructure. Which of the following layers of the OSI model is the technician addressing at this stage of the upgrade?
APC cannot reach a server in the same VLAN with IP address 10.10.5.0. The PC has the following information:
IP address: 10,10.0.255
Net mask: 255.255 252.0
Gateway: 10.10.1.1
Which of the following is the reason for this issue?
A technician is planning a network wiring installation and must ensure all cabling meets the installation requirements for air-handling spaces in the celling in case of a fire. Which of the following characteristics does
plenum cabling have to meet this requirement?
Which of the following utilizes a circuit-switched network?
A Satellite
B. PPPoE
C. Wireless
D. MPLS
E. Frame relay
The Chief Information Officer (CIO) of a large company wants to migrate the ERP system into a cloud provider. Company policy states it is necessary to maintain control over the computer resources that run this software. Which of the following cloud models should be used in this scenario?
A network administrator is installing the company first external-facing web server and examining where to place it on the network. In which of the following zones should the server be configured?
A network technician needs to visit a datacenter. To be admitted, the security officer requests to see a driver's license, and then directs the technician to a fingerprint scanner. Which of the following authentication factors is the facility requiring for admittance? (Select TWO).
A network technician receives a help desk ticket indicating all users at a branch office are having problems connecting to the corporate wireless network, The technician verifies the wireless controller can see the WAPS at this
office and they are configured appropriately. After reviewing recently closed tickets, the network technician discovers a software upgrade was implemented to the wireless network at that branch office overnight. Which of the
following is MOST likely the cause of the issue?
A new printer was assigned a static IP address within the DHCP scope of a QA subnet. There are 243 workstations on the LAN five servers, and four existing printers on the network. The network administrator configured the network with the following parameters:
192.168.51 -192 168.5 5 static IPs assigned to servers
192.168.5.6 -192 168.5 250 DHCP scope for workstations
192.168.5.251 -192.168.5 254 static IPs assigned to printers
Which of the following should the network administrator perform to minimize the disruption to the users and keep the LAN secure while setting up the new printer?
A network administrator has discovered a low-end managed switch connoted to the company LAN. While reading about the device's specifications on the manufacturer's website, the administrator discovers the switch does not support a command line interface for administration. Which of the following remote access methods should the administrator use to log in the switch?
A technician wants to install a WAP in the center of a room that provides service in a radius surrounding a radio. Which of the following antenna types should the AP utilize?
A technician needs a way to allow clients to access a new application server on the network. Which of the following should the technician set up to achieve this objective? (Select TWO)
A technician is installing a cable modem In a SOHO. Which of the following cable types will the technician MOST likely use to connect a modem to the ISP?
A network technician is working to bring a new workstation onto the network. No lights come on when the technician plugs the Ethernet cable into the workstation. The technician checks the connection in the IDF and discovers the data jack is not labeled. Which of the following tools should the technician use to trace the network connection back to the IDF?
A user in the finance department can access the department printer and file server yet is unable to print to the marketing department’s printer. A technician runs ipconfig and sees the following output:
IPv4 Address. . . . . . . . . . . : 192.168.0.101
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.1
The technician has verified the user’s PC is in the proper VLAN and sees an UP/UP status on the switchport. Which of the following is MOST likely causing the issue?
A network technician needs to manage a sensor at an unmanned location without incurring the cost of a dedicated Internet connection. Which of the following will the technician MOST likely implement?
An ARP request is broadcasted and sends the following request.
''Who is 192.168.1.200? Tell 192.168.1.55''
At which of the following layers of the OSI model does this request operate?
A network technician is utilizing DHCP. The technician has set a six-day lease time for all hosts. After which of the following time intervals should the hosts attempt to FIRST renew their address?
A technician is making the population of routers more secure. Which of the following are the BEST options for making authentication more secure? (Choose two.)
Internal users have been unable to access the web server on a local network that they are to use. qi have been to the help desk, and a technician has decided to apply the following commands to the equipment:
access-list 103 permit tcp any any eq 80
access-list 103 permit tcp any any eq 443
access-list 103 deny ip any any
On which of the following devices would the technician apply these commands?
D. Switch
B. Modem
C. Border router
D. Bridge
E. PDU
The security department is looking to install a new IP-based camera. Plugging the camera into the available Ethernet jack does not power on the camera. Upon further investigation, the cable tests fine, and it does provide power to a VoIP phone. Which of the following is MOST likely causing the issue?
A site was hit with ransomware on two occasions in the past month. Which of the following would be the BEST solution for a technician who wants to reduce this frequency?
A network administrator is reviewing security logs and notes a strange IP address logging into the management console of a switch. The administrator verifies the switch is not using default credentials. Which of the following steps should the administrator take NEXT?
A new datacenter is being created, and management is trying to control access to that area. Which of the following are the BEST choices for providing access to the new datacenter? (Choose two.)
administrator is reviewing the security logs from switches across the campus and notes multiple failed logon attempts on all the equipment. Which of the following should be implemented to restrict
the networks that can access the management interface on the switches?
A technician is performing a maintenance task on a weekly basis and wants to ensure the task is property documented and able to be performed by other technicians. Which of the following types of documentation should the technician complete?
Which of the following BEST explains why a firewall would be subject to international export controls?
A network technician is attempting to resolve an issue for two users. The users unplugged and moved their laptops to a different cubicle to work together. The NIC LED Is lit on both laptops, but the users are not able to access the network resources. Which of the following is MOST likely preventing access?
A company wants to implement a large number of WAPs throughout its building and allow users to be able to move around the building without dropping their connections. Which of the following pieces of equipment would be able to handle this requirement?
A company wants to provide its sales representatives with an easy-to-use method of securely connecting to the corporate network from any client network. Which of the following methods should the network technician implement?
Two buildings are connected with 802.11a wireless bridges using omnidirectional antennas However, the connection between the two bridges often drops Which of the following would be the BEST solution?
A network engineer is designing a new secure wireless network. The engineer has been given the following requirements:
1 Must not use plaintext passwords
2 Must be certificate based
3. Must be vendor neutral
Which of the following methods should the engineer select?
Ann, a network technician, has relocated a rack that contains the networking and server equipment from the third floor to the sixth floor. To connect the rack-mounted router to the media converter in the first-floor MDF, she extended the length of the original 197ft (60m) Cat5e cable to 395ft (120m) by attaching another 197ft (60m) cable with an RJ45 coupler. After the move, users report intermittent connectivity to external websites, although connectivity to internal hosts has not changed. Which of the following is a network performance issue that is MOST likely causing this issue?
CompTIA Network+ | N10-007 Questions Answers | N10-007 Test Prep | CompTIA Network+ N10-007 Questions PDF | N10-007 Online Exam | N10-007 Practice Test | N10-007 PDF | N10-007 Test Questions | N10-007 Study Material | N10-007 Exam Preparation | N10-007 Valid Dumps | N10-007 Real Questions | CompTIA Network+ N10-007 Exam Questions