How does the FortiSASE security dashboard facilitate vulnerability management for FortiClient endpoints? (Choose one answer)
SD-WAN interacts with many other FortiGate features. Some of them are required to allow SD-WAN to steer the traffic.
Which three configuration elements must you configure before FortiGate can steer traffic according to SD-WAN rules? (Choose three.)
Refer to the exhibit.
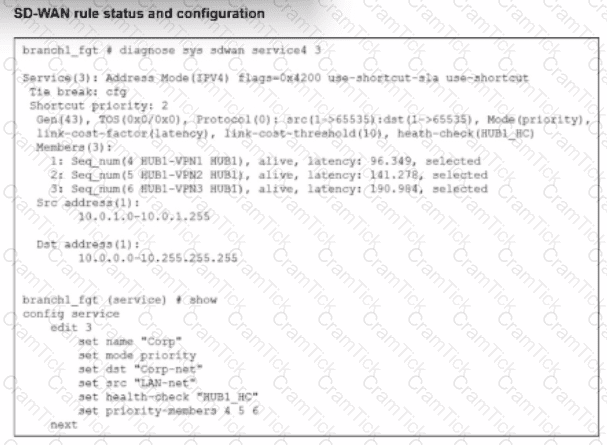
The SD-WAN rule status and configuration is shown. Based on the exhibit, which change in the measured latency will first make HUB1-VPN3 the new preferred member?
Which three factors about SLA targets and SD-WAN rules should you consider when configuring SD-WAN rules? (Choose three answers)
Which configuration is a valid use case for FortiSASE features in supporting remote users?


