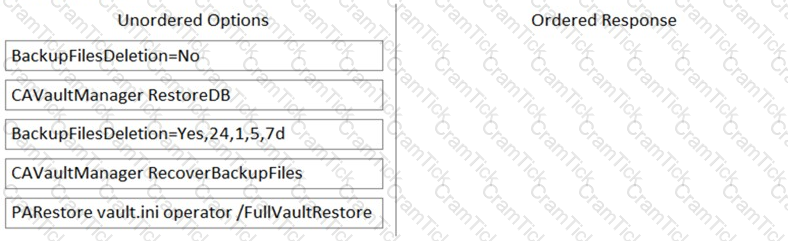
Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.
In a default CyberArk installation, which group must a user be a member of to view the “reports” page in PVWA?
Which option in the Private Ark client is used to update users’ Vault group memberships?
The Active Directory User configured for Windows Discovery needs which permission(s) or membership?
You are configuring CyberArk to use HTML5 gateways exclusively for PSM connections.
In the PVWA, where do you set DefaultConnectionMethod to HTML5?
Which of the following are secure options for storing the contents of the Operator CD, while still allowing the contents to be accessible upon a planned Vault restart? (Choose three.)
Time of day or day of week restrictions on when password verifications can occur configured in ____________________.
During a High Availability node switch you notice an error and the Cluster Vault Manager Utility fails back to the original node.
Which log files should you check to investigate the cause of the issue? (Choose three.)
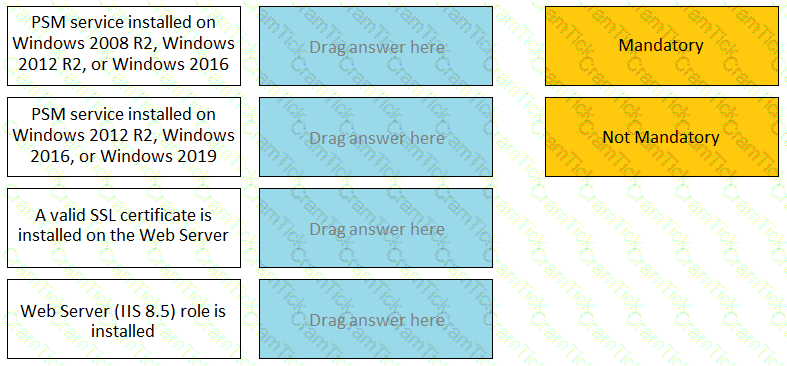
For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check.
What is required to enable access over SSH to a Unix account through both PSM and PSMP?
In order to connect to a target device through PSM, the account credentials used for the connection must be stored in the vault?
If the AccountUploader Utility is used to create accounts with SSH keys, which parameter do you use to set the full or relative path of the SSH private key file that will be attached to the account?
When an account is unable to change its own password, how can you ensure that password reset with the reconcile account is performed each time instead of a change?
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
An auditor initiates a live monitoring session to PSM server to view an ongoing live session. When the auditor’s machine makes an RDP connection the PSM server, which user will be used?
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
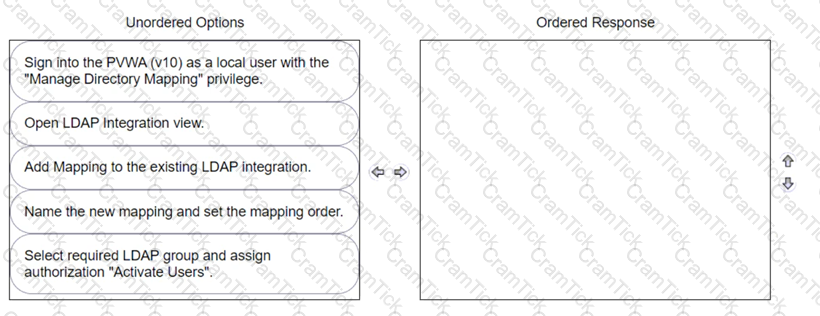
You have been asked to delegate the rights to unlock users to Tier 1 support. The Tier 1 support team already has an LDAP group for its members.
Arrange the steps to do this in the correct sequence.
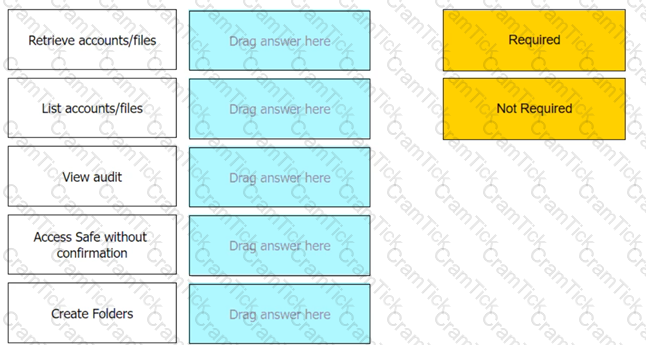
Which authorizations are required in a recording safe to allow a group to view recordings?
Target account platforms can be restricted to accounts that are stored m specific Safes using the Allowed Safes property.
You have been asked to identify the up or down status of Vault services.
Which CyberArk utility can you use to accomplish this task?
It is possible to leverage DNA to provide discovery functions that are not available with auto-detection.
To manage automated onboarding rules, a CyberArk user must be a member of which group?
Which CyberArk utility allows you to create lists of Master Policy Settings, owners and safes for output to text files or MSSQL databases?
What are the mandatory fields when onboarding from Pending Accounts? (Choose two.)
When a group is granted the 'Authorize Account Requests' permission on a safe Dual Control requests must be approved by
In your organization the “click to connect” button is not active by default.
How can this feature be activated?
Match each PTA alert category with the PTA sensors that collect the data for it.

You created a new safe and need to ensure the user group cannot see the password, but can connect through the PSM.
Which safe permissions must you grant to the group? (Choose two.)
Which methods can you use to add a user directly to the Vault Admin Group? (Choose three.)
You have been asked to create an account group and assign three accounts which belong to a cluster. When you try to create a new group, you receive an unauthorized error; however, you are able to edit other aspects of the account properties.
Which safe permission do you need to manage account groups?
You receive this error:
“Error in changepass to user domain\user on domain server(\domain.(winRc=5) Access is denied.”
Which root cause should you investigate?
For an account attached to a platform that requires Dual Control based on a Master Policy exception, how would you configure a group of users to access a password without approval.
If a password is changed manually on a server, bypassing the CPM, how would you configure the account so that the CPM could resume management automatically?
Which parameters can be used to harden the Credential Files (CredFiles) while using CreateCredFile Utility? (Choose three.)
As long as you are a member of the Vault Admins group, you can grant any permission on any safe that you have access to.
Which parameter controls how often the CPM looks for Soon-to-be-expired Passwords that need to be changed.
Customers who have the ‘Access Safe without confirmation’ safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
You want to give a newly-created group rights to review security events under the Security pane. You also want to be able to update the status of these events.
Where must you update the group to allow this?
The Vault administrator can change the Vault license by uploading the new license to the system Safe.
A new domain controller has been added to your domain. You need to ensure the CyberArk infrastructure can use the new domain controller for authentication.
Which locations must you update?
You are concerned about the Windows Domain password changes occurring during business hours.
Which settings must be updated to ensure passwords are only rotated outside of business hours?
Where can a user with the appropriate permissions generate a report? (Choose two.)
A Vault administrator have associated a logon account to one of their Unix root accounts in the vault. When attempting to verify the root account’s password the Central Policy Manager (CPM) will:
Defender |