Which element of the security operations process is concerned with using external functions to help achieve goals?
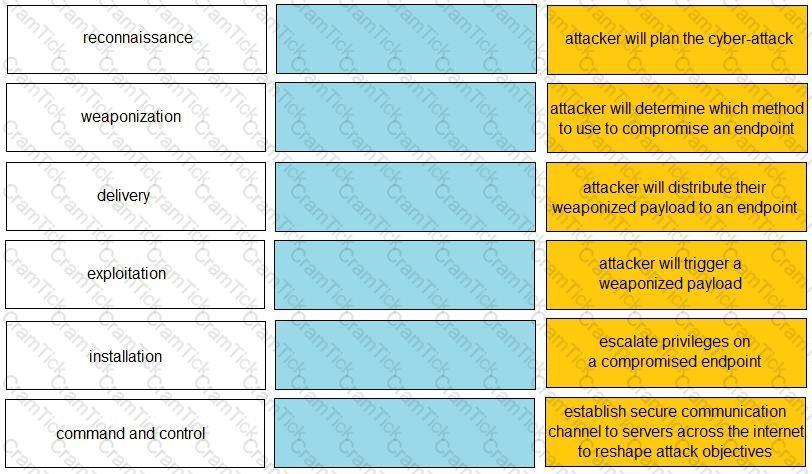
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

Which three layers of the OSI model correspond to the Application Layer (L4) of the TCP/IP model?
Which type of malware takes advantage of a vulnerability on an endpoint or server?
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
What is the recommended method for collecting security logs from multiple endpoints?
What should a security operations engineer do if they are presented with an encoded string during an incident investigation?
Which aspect of a SaaS application requires compliance with local organizational security policies?
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
An Administrator wants to maximize the use of a network address. The network is 192.168.6.0/24 and there are three subnets that need to be created that can not overlap. Which subnet would you use for the network with 120 hosts?
Requirements for the three subnets: Subnet 1: 3 host addresses
Subnet 2: 25 host addresses
Subnet 3: 120 host addresses
A doctor receives an email about her upcoming holiday in France. When she clicks the URL website link in the email, the connection is blocked by her office firewall because it's a known malware website. Which type of attack includes a link to a malware website in an email?
You have been invited to a public cloud design and architecture session to help deliver secure east west flows and secure Kubernetes workloads.
What deployment options do you have available? (Choose two.)
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
In which situation would a dynamic routing protocol be the quickest way to configure routes on a router?
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
What does Palo Alto Networks Cortex XDR do first when an endpoint is asked to run an executable?
Which activities do local organization security policies cover for a SaaS application?
Which two pieces of information are considered personally identifiable information (PII)? (Choose two.)
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
Which characteristic of serverless computing enables developers to quickly deploy application code?
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
Which technique uses file sharing or an instant messenger client such as Meebo running over Hypertext Transfer Protocol (HTTP)?
Which protocol is used by both internet service providers (ISPs) and network service providers (NSPs)?
Certified Cybersecurity Associate | PCCET Questions Answers | PCCET Test Prep | Palo Alto Networks Certified Cybersecurity Entry-level Technician Questions PDF | PCCET Online Exam | PCCET Practice Test | PCCET PDF | PCCET Test Questions | PCCET Study Material | PCCET Exam Preparation | PCCET Valid Dumps | PCCET Real Questions | Certified Cybersecurity Associate PCCET Exam Questions


