Which product enables the discovery, exchange, and contribution of security automation playbooks, built into Cortex XSOAR?
A customer is hesitant to directly connect their network to the Cortex platform due to compliance restrictions.
Which deployment method should the customer use to ensure secure connectivity between their network and the Cortex platform?
Which attack method is a result of techniques designed to gain access through vulnerabilities in the code of an operating system (OS) or application?
Which two actions are required to add indicators to the whitelist? (Choose two.)
Which command-line interface (CLI) query would retrieve the last three Splunk events?
A Cortex XSOAR customer has a phishing use case in which a playbook has been implemented with one of the steps blocking a malicious URL found in an email reported by one of the users.
What would be the appropriate next step in the playbook?
When preparing the golden image in a Cortex XDR Virtual Desktop Infrastructure (VDI) deployment, which step is required?
A Cortex XSOAR customer wants to ingest emails from a single mailbox. The mailbox brings in reported phishing emails and email requests from human resources (HR) to onboard new users. The customer wants to run two separate workflows from this mailbox, one for phishing and one for onboarding.
What will allow Cortex XSOAR to accomplish this in the most efficient way?
What allows the use of predetermined Palo Alto Networks roles to assign access rights to Cortex XDR users?
A prospective customer is interested in Cortex XDR but is enable to run a product evaluation.
Which tool can be used instead to showcase Cortex XDR?
Which two troubleshooting steps should be taken when an integration is failing to connect? (Choose two.)
Which two types of indicators of compromise (IOCs) are available for creation in Cortex XDR? (Choose two.)
Which aspect of Cortex Xpanse allows for visibility over remote workforce risks?
How does a clear understanding of a customer’s technical expertise assist in a hand off following the close of an opportunity?
What is the size of the free Cortex Data Lake instance provided to a customer who has activated a TMS tenant, but has not purchased a Cortex Data Lake instance?
In Cortex XDR Prevent, which three matching criteria can be used to dynamically group endpoints? (Choose three )
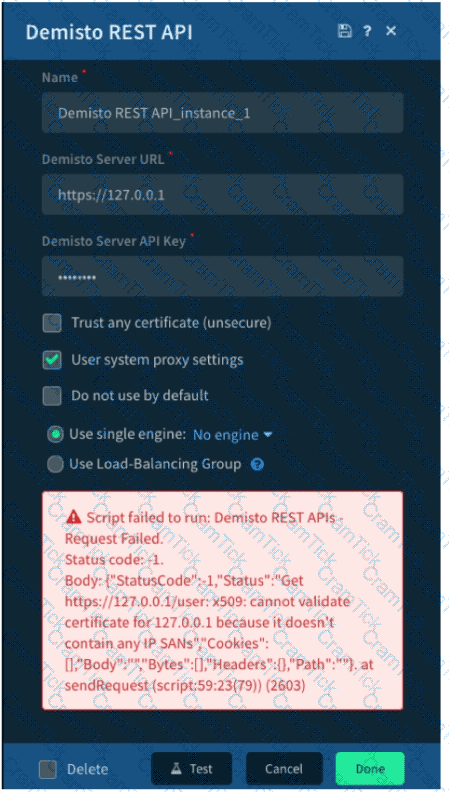
Given the exception thrown in the accompanying image by the Demisto REST API integration, which action would most likely solve the problem?
Which two playbook functionalities allow looping through a group of tasks during playbook execution? (Choose two.)
Which Cortex XSIAM license is required if an organization needs to protect a cloud Kubernetes host?
Why is it important to document notes from the Proof of Value (POV) for post-sales hand off?
In the DBotScore context field, which context key would differentiate between multiple entries for the same indicator in a multi-TIP environment?
Which two Cortex XSOAR incident type features can be customized under Settings > Advanced > Incident Types? (Choose two.)
When initiated, which Cortex XDR capability allows immediate termination of the process-or entire process tree-on an anomalous process discovered during investigation of a security event?
When preparing for a Cortex XSOAR proof of value (POV), which task should be performed before the evaluation is requested?
A customer has purchased Cortex Data Lake storage with the following configuration, which requires 2 TB of Cortex Data Lake to order:
support for 300 total Cortex XDR clients all forwarding Cortex XDR data with 30-day retention
storage for higher fidelity logs to support Cortex XDR advanced analytics
The customer now needs 1000 total Cortex XDR clients, but continues with 300 clients forwarding Cortex XDR data with 30-day retention.
What is the new total storage requirement for Cortex Data Lake storage to order?
In addition to migration and go-live, what are two best-practice steps for migrating from SIEM to Cortex XSIAM? (Choose two.)
How can the required log ingestion license be determined when sizing a Cortex XSIAM deployment?
A customer has purchased Cortex XSOAR and has a need to rapidly stand up the product in their environment. The customer has stated that their internal staff are currently occupied with other projects.
Which Palo Alto Networks service offering should be recommended to the customer?
Which Linux OS command will manually load Docker images onto the Cortex XSOAR server in an air-gapped environment?
A customer has purchased Cortex XDR and requires phone support for the product.
Which Palo Alto Networks offering would fulfill this need?
A prospect has agreed to do a 30-day POC and asked to integrate with a product that Demisto currently does not have an integration with. How should you respond?
Cortex XSOAR has extracted a malicious Internet Protocol (IP) address involved in command-and-control (C2) traffic.
What is the best method to block this IP from communicating with endpoints without requiring a configuration change on the firewall?
An administrator of a Cortex XDR protected production environment would like to test its ability to protect users from a known flash player exploit.
What is the safest way to do it?
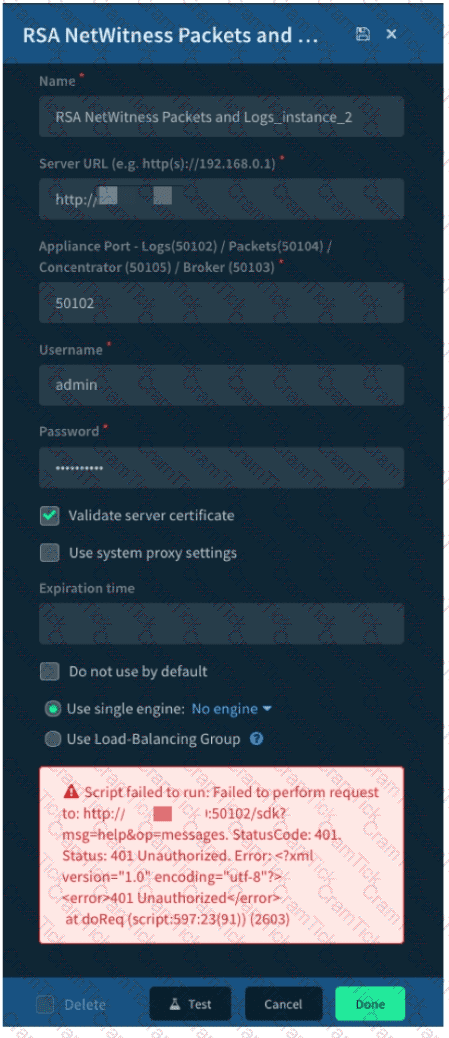
Given the integration configuration and error in the screenshot what is the cause of the problem?
PSE-Cortex Professional | PSE-Cortex Questions Answers | PSE-Cortex Test Prep | Palo Alto Networks System Engineer - Cortex Professional Questions PDF | PSE-Cortex Online Exam | PSE-Cortex Practice Test | PSE-Cortex PDF | PSE-Cortex Test Questions | PSE-Cortex Study Material | PSE-Cortex Exam Preparation | PSE-Cortex Valid Dumps | PSE-Cortex Real Questions | PSE-Cortex Professional PSE-Cortex Exam Questions


