For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
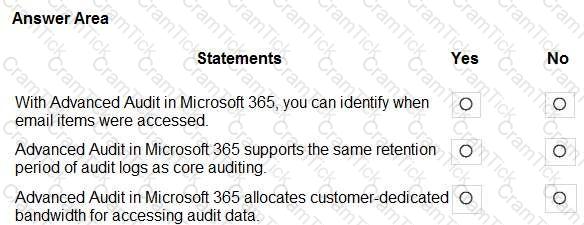
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What can you use to scan email attachments and forward the attachments to recipients only if the attachments are free from malware?
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution.
NOTE; Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Which two cards are available in the Microsoft 365 Defender portal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
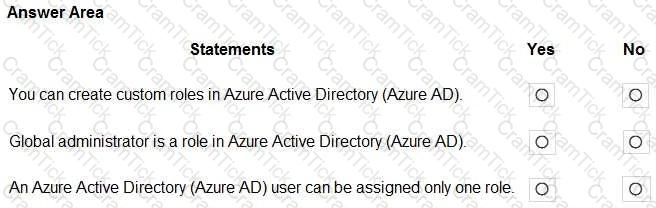
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
In the shared responsibility model, for what is Microsoft responsible when managing Azure virtual machines?
What is a use case for implementing information barrier policies in Microsoft 365?
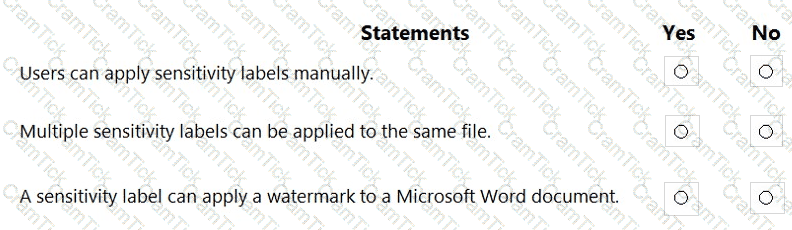
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
What should you use to ensure that the members of an Azure Active Directory group use multi-factor authentication (MFA) when they sign in?
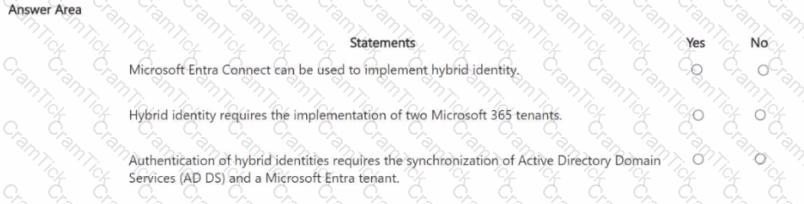
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
What do you use to provide real-time integration between Azure Sentinel and another security source?
Which compliance feature should you use to identify documents that are employee resumes?
When security defaults are enabled for an Azure Active Directory (Azure AD) tenant, which two requirements are enforced? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

To which three locations can a data loss prevention (DLP) policy be applied? Each correct answer presents a complete solution.
NOTE: Each correct answer is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What are two capabilities of Microsoft Defender for Endpoint? Each correct selection presents a complete solution.
NOTE: Each correct selection is worth one point.
What can you use to ensure that all the users in a specific group must use multi-factor authentication (MFA) to sign in to Azure AD?
What can you use to protect against malicious links sent in email messages, chat messages, and channels?
Match the types of compliance score actions to the appropriate tasks.
To answer. drag the appropriate action type from the column on the left to its task on the right. Each type may be used once. more than once, or not at all.
NOTE: Each correct match is worth one point.

What should you create to search and export content preserved in an eDiscovery hold?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
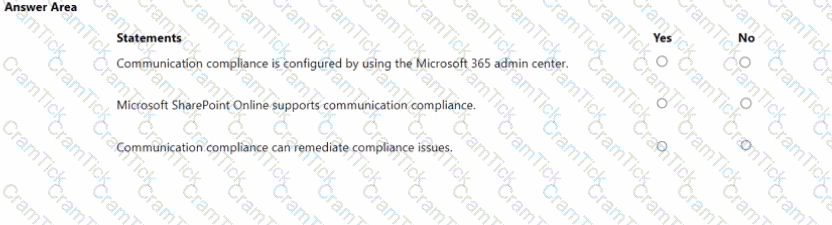
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources?
What should you use in the Microsoft 365 security center to view security trends and track the protection status of identities?
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
In the shared responsibility model for an Azure deployment, what is Microsoft solely responsible for managing?
You have an Azure subscription.
You need to implement approval-based, tiProme-bound role activation.
What should you use?
Microsoft Certified: Security Compliance and Identity Fundamentals | SC-900 Exam Topics | SC-900 Questions answers | SC-900 Test Prep | Microsoft Security Compliance and Identity Fundamentals Exam Questions PDF | SC-900 Online Exam | SC-900 Practice Test | SC-900 PDF | SC-900 Test Questions | SC-900 Study Material | SC-900 Exam Preparation | SC-900 Valid Dumps | SC-900 Real Questions | Microsoft Certified: Security Compliance and Identity Fundamentals SC-900 Exam Questions


