A company designed a specialized Amazon EC2 instance configuration for its Data Scientists. The Data Scientists want to create end delete EC2 instances on their own, but are not comfortable with configuring all the settings for EC2 instances without assistance. The configuration runs proprietary software that must be kept private within the company's AWS accounts and should be available to the Data Scientists, but no other users within the accounts.
Which solution should a SysOps Administrator use to allow the Data Scientists to deploy their workloads with MINIMAL effort?
A company received its latest bill with a large increase in the number of requests against Amazon SQS as compared to the month prior. The company is not aware of any major changes in its SQA usage. The company is concerned about the cost increase and who or what was making these calls.
What should a sysops administrator use to validate the calls mode to SQS?
A SysOps administrator must deploy a company's infrastructure as code (laC) The administrator needs to write a single template that can be reused for multiple environments in a safe, repeatable manner
How should the administrator meet this requirement by using AWS Cloud Formation?
A company uses AWS CloudFotmatlon to provision ils VPC. Amazon EC2 instances, and Amazon RDS DB instance The DB instance was deleted manually. When the stack was updated, it (ailed. During rollback, the stack returned the UPDATE_ROLLBACK_FAILEO state. A SysOps administrator must return the AWS Cloud Formation stack to a working state without interrupting existing resources.
Which solution will meet this requirement?
A SysOps Administrator is notified that an Amazon EC2 instance has stopped responding The AWS Management Console indicates that the system status checks are failing What should the SysOps Administrator do first to resolve this issue?
An application is being developed that will be served across a fleet of Amazon EC2 instances, which require a consistent view of persistent data. Items stored vary in size from 1 KB lo 300MB; the items are read frequently, created occasionally, and often require partial changes without conflict. The data store is not expected to grow beyond 2TB. and items will be expired according to age and content type.
Which AWS service solution meets these requirements?
An application is running on multiple EC2 instances. As part of an initiative to improve overall infrastructure security, the EC2 instances were moved to a private subnet. However, since moving, the EC2 instances have not been able to automatically update, and a SysOps Administrator has not been able to SSH into them remotely.
Which two actions could the Administrator take to securely resolve these issues? (Choose two.)
A company using AWS Organizations requires that no Amazon S3 buckets in its production accounts should ever be deleted.
What is the SIMPLEST approach the SysOps Administrator can take to ensure S3 buckets in those accounts can never be deleted?
A SysOps Administrator is maintaining a web application using an Amazon Cloud Front web distribution, an Application Load Balancer (ALB), Amazon RDS, and Amazon EC2 in a VPC. All services have services have logging enabled. The Administrator needs to investigate HTTP Layer 7 status codes from the web application.
Which log source contain the status codes? (Select TWO.)
A SysOps Administrator needs an Amazon EBS volume type for a big data application. The application data is accessed infrequently and stored sequentially.
What EBS volume type will be the MOST cost-effective solution?
A SysOps Administrator must find a way to set up alerts when Amazon EC2 service limits are close to being reached.
How can the Administrator achieve this requirement?
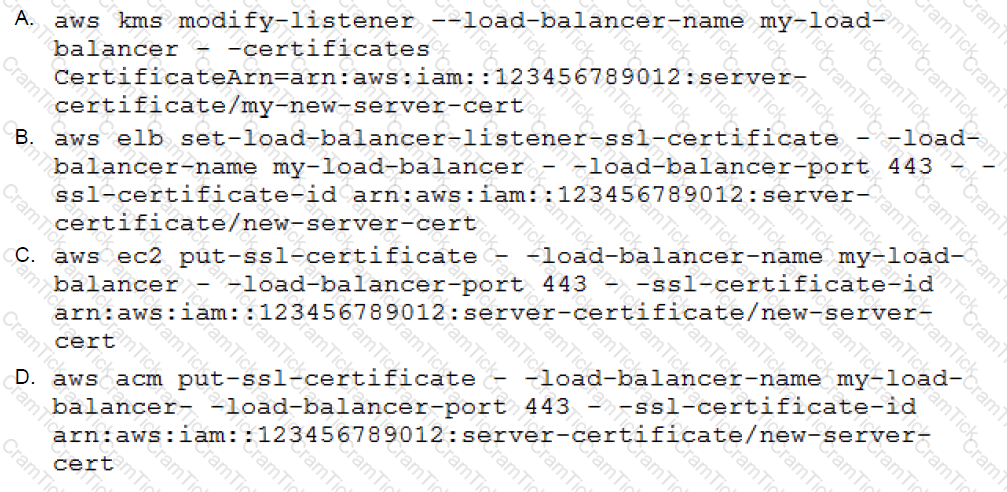
A SysOps Administrator has been able to consolidate multiple, secure websites onto a single server, and each site is running on a different port. The Administrator now wants to start a duplicate server in a second Availability Zone and put both behind a load balancer for high availability.
What would be the command line necessary to deploy one of the sites’ certificates to the load balancer?
The Security team has decided that there will be no public internet access to HTTP (TCP port 80) because if it is moving to HTTPS for all incoming web traffic. The team has asked a SysOps Administrator to provide a report on any security groups that are not compliant.
What should the SysOps Administrator do to provide near real-time compliance reporting?
Website users report that an application's pages are loading slowly at the beginning of the workday The application runs on Amazon EC2 instances and data is stored in an Amazon RDS database The SysOps Administrator suspects the issue is related to high CPU usage on a component of this application
How can the Administrator find out which component is causing the performance bottleneck?
A company wants to create a new Network Load Balancer (NLB) (or an existing interface VPC endpoint. A SysOps administrator tries to remove the existing NLB but sees the error "existing VPC Endpoint connections and cannot be removed."
Which solution will resolve this issue?
A company has deployed a NAT instance to allow web servers to obtain software updates from the internet. There latency on the NAT instance as the network grows. A SysOps Administrator needs to reduce latency on the instance in a manner that a efficient, cost effective, and allow for scaling with future demand.
Which action should be taken to accomplish this?
A company is using an AWS KMS customer master key (CMK) with imported key material. The company references the CMK by its alias in the Java application to encrypt data. The CMK must be rotated every 6 months
What is the process to rotate the key?
A SysOps Administrate is building a process for sharing Amazon RDS database snapshots between different accounts associated with different business units within the same company All data must be encrypted at rest
How should the Administrate implement this process?
Which component of an Ethernet frame is used to notify a host that traffic is coming?
A SysOps Administrator needs to monitor all the object upload and download activity of a single Amazon S3 bucket. Monitoring most include tracking the AWS account of the catier, the IAM user role of the caller, the time of the API call, and the IP address of the API.
Where can the administrator find this information?
A company has multiple AWS accounts. The company uses AWS Organizations with an organizational unit (OU) tor the production account and another OU for the development account. Corporate policies state that developers may use only approved AWS services in the production account.
What is the MOST operationally efficient solution to control the production account?
A SysOps Administrator is creating additional Amazon EC2 instances and receives an InstanceLimitExceeded error.
What is the cause of the issue and how can it be resolved?
An application is running on Amazon EC2 Instances behind an Application Load Balancer (ALB). An operations team wants to be notified in near-teal time when the ALB has issues connecting to backend EC2 instances.
Which solution will meet these requirements with the LEAST amount of effort?
A SysOps Administrator is writing a utility that publishes resources from an AWS Lambda function in AWS account A to an Amazon S3 bucket in AWS Account B. The Lambda function is able to successfully write new objects to the S3 bucket, but IAM users in Account B are unable to delete objects written to the bucket by Account A.
Which step will fix this issue?
Developers are using 1AM access keys to manage AWS resources using AWS CL1 Company policy requires that access keys are automatically disabled when the access key age is greater than 90 days
Which solution will accomplish this?
A developer is deploying a web application on Amazon EC2 instances behind an Application Load Balancer (ALB) and notices that the application is not receiving all the expected elements from HTTP requests. The developer suspects users are not sending the correct query string
How should a sysops administrator verify this?
The Chief Financial Officer (CFO) of an organization has seen a spike in Amazon S3 storage costs over the last few months A sysops administrator suspects that these costs are related to storage for older versions of S3 objects from one of its S3 buckets
What can the administrator do to confirm this suspicion1?
A SysOps Administrator must secure AWS CloudTrail logs. The Security team is concerned that an employee may modify or attempt to delete CloudTrail log files from its Amazon S3 bucket.
Which practices ensure that the log files are available and unaltered? (Choose two.)
An organization is running multiple applications for their customers. Each application is deployed by running a base AWS CloudFormation template that configures a new VPC. All applications are run in the same AWS account and AWS Region A sysops administrator has noticed that when trying to deploy the same AWS CloudFormation stack, it fails to deploy
What is likely to be the problem?
A company is releasing a now static website hosted on Amazon S3. The static website hosting feature was enabled on the bucket and content was uploaded, however, upon navigating to the site, the following error message is received:
403 Forbiddan - Access Denied
What change should be made to fix this error'?
A sysops administrator is writing an AWS Cloud Formation template. The template will create a new Amazon S3 bucket and copy objects from an existing Amazon S3 bucket into the new bucket. The objects include data files, images, and scripts.
How should the CIoudFormation template be configured to perform this copy operation?
A company relies on a fleet of Amazon EC2 instances to support an application. One of the EC2 instances was scheduled for hardware maintenance by AWS. An operations team did not remove the EC2 instance from the fleet in advance of the scheduled maintenance, and an unplanned outage resulted. A SysOps administrator must configure notifications to let the operations team know about scheduled maintenance in the future.
Which action should the SysOps administrator take to meet this requirement?
A development team recently deployed new version of a web application to production. After the release, penetration testing revealed a cross-site scripting vulnerability that could expose user data.
Which AWS service will mitigate this issue?
A SysOps administrator is configuring an application on AWS to be used over the internet by departments in other countries For remote locations, the company requires a static public IP address to be explicitly allowed as a target for outgoing internet traffic
How should the SysOps administrator deploy the application to meet this requirement?
An e-commerce company wants to lower costs on its nightly jobs that aggregate the current day’s sales and store the results in Amazon S3. The jobs are currently run using multiple on-demand instances and the job take just under 2 hours to complete. If a job fails for any reason, it needs to be restarted from the beginning.
What method is the MOST cost effective based on these requirements?
A company has a sales department and a marketing department. The company uses one AWS account. There Is a need to determine what charges are incurred on the AWS platform by each department. There is also a need to receive notifications when a specified cost level is approached or exceeded.
Which actions must a SysOps administrator take to achieve both requirements with the LEAST amount of administrative overhead? (Select TWO.)
AWS Certified Associate | SOA-C01 Questions Answers | SOA-C01 Test Prep | AWS Certified SysOps Administrator - Associate Questions PDF | SOA-C01 Online Exam | SOA-C01 Practice Test | SOA-C01 PDF | SOA-C01 Test Questions | SOA-C01 Study Material | SOA-C01 Exam Preparation | SOA-C01 Valid Dumps | SOA-C01 Real Questions | AWS Certified Associate SOA-C01 Exam Questions


