A correlation rule is created to detect potential insider threats by correlating user login events from one dataset with file access events from another dataset. The rule must retain all user login events, even if there are no matching file access events, to ensure no login activity is missed.
text
Copy
dataset = x
| join (dataset = y)
Which type of join is required to maintain all records from dataset x, even if there are no matching events from dataset y?
When using Kerberos as the authentication method for Pathfinder, which two settings must be validated on the DNS server? (Choose two.)
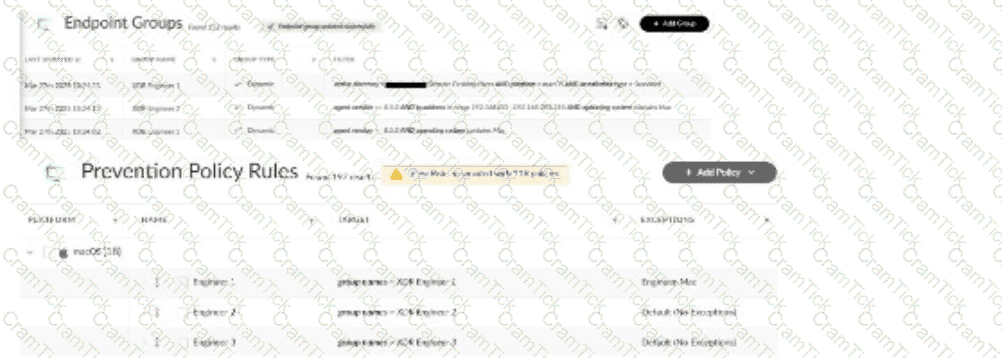
Multiple remote desktop users complain of in-house applications no longer working. The team uses macOS with Cortex XDR agents version 8.7.0, and the applications were previously allowed by disable prevention rules attached to the Exceptions Profile "Engineer-Mac." Based on the images below, what is a reason for this behavior?
Which two steps should be considered when configuring the Cortex XDR agent for a sensitive and highly regulated environment? (Choose two.)
Using the Cortex XDR console, how can additional network access be allowed from a set of IP addresses to an isolated endpoint?
What happens when the XDR Collector is uninstalled from an endpoint by using the Cortex XDR console?
Based on the Malware profile image below, what happens when a new custom-developed application attempts to execute on an endpoint?

What is the earliest time frame an alert could be automatically generated once the conditions of a new correlation rule are met?
An XDR engineer is creating a correlation rule to monitor login activity on specific systems. When the activity is identified, an alert is created. The alerts are being generated properly but are missing the username when viewed. How can the username information be included in the alerts?
An administrator wants to employ reusable rules within custom parsing rules to apply consistent log field extraction across multiple data sources. Which section of the parsing rule should the administrator use to define those reusable rules in Cortex XDR?


