Which cytool command will look up the policy being applied to a Cortex XDR agent?
The following string is a value of a key named "Data2" in the context:
{"@admin":"admin","@dirtyld":"1","@loc":"Lab","@name":"default‑1","@oldname":"Test","@time":"2024/08/28 07:45:15","alert":{"@admin":"admin","@dirtyld":"2","@time":"2024/08/28 07:45:15","member":{"#text":"
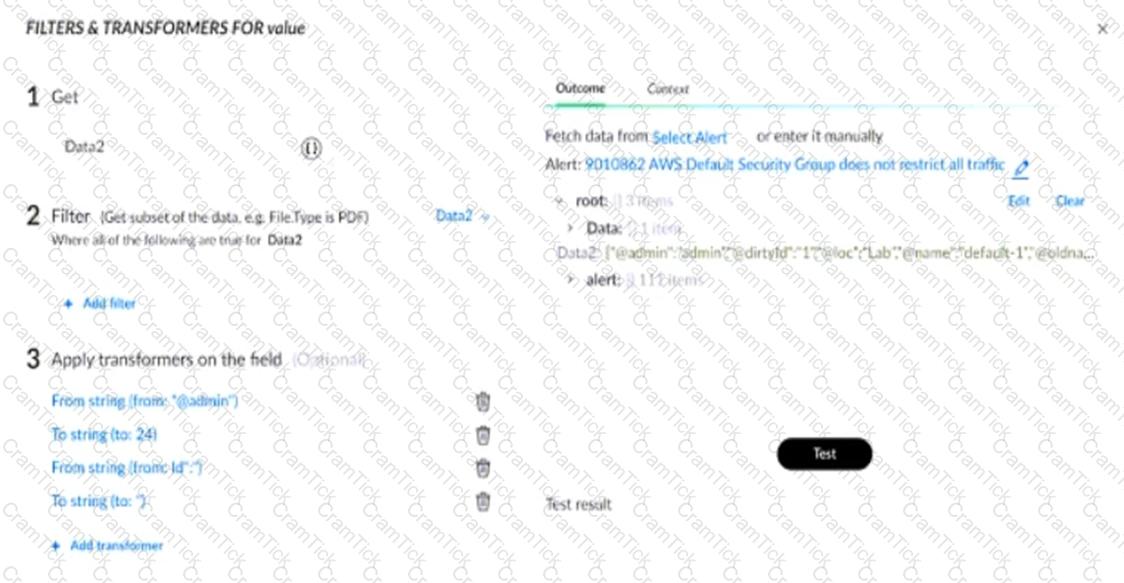
Based on the image below, what will be displayed in the "Test result" field when the "Test" button is pressed?
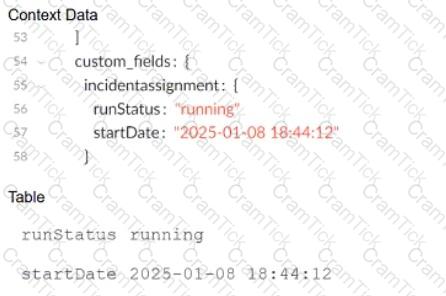
Based on the images below, which command will allow the context data to be displayed as a table when troubleshooting a playbook task?
Using the integrationContext object, how is data stored and retrieved between integration command runs in Cortex XSIAM?
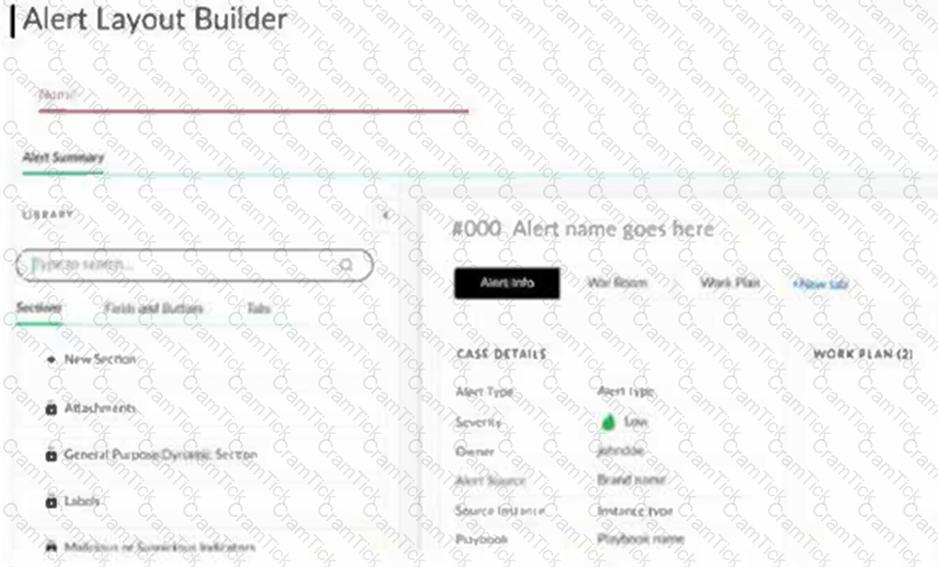
Based on the image below, which statement applies to the ability to remove tabs when creating a new alert layout?
A sub-playbook is configured to loop with a For Each Input. The following inputs are given to the sub-playbook:
Input x: W,X,Y,Z
Input y: a,b,c,d
Input z: 9
Which inputs will be used for the second iteration of the loop?
Which type of parsing error is categorized in the dataset "parsing_rules_errors"?
Which installer type should be used when upgrading a non-Linux Kubernetes cluster?
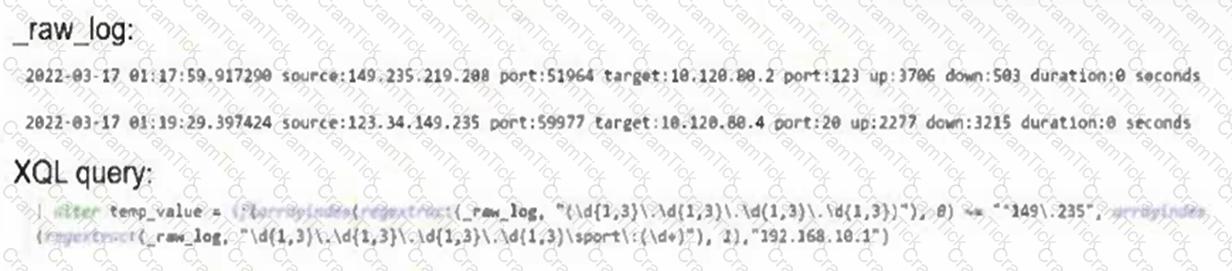
Based on the _raw_log and XQL query information below, what will be the result(s) of the temp_value?
A Cortex XSIAM engineer is developing a playbook that uses reputation commands such as '!ip' to enrich and analyze indicators.
Which statement applies to the use of reputation commands in this scenario?
A Behavioral Threat Protection (BTP) alert is triggered with an action of "Prevented (Blocked)" on one of several application servers running Windows Server 2022. The investigation determines the involved processes to be legitimate core OS binaries, and the description from the triggered BTP rule is an acceptable risk for the company to allow the same activity in the future.
This type of activity is only expected on the endpoints that are members of the endpoint group "AppServers," which already has a separate prevention policy rule with an exceptions profile named "Exceptions-AppServers" and a malware profile named "Malware-AppServers."
The CGO that was terminated has the following properties:
SHA256: eb71ea69dd19f728ab9240565e8c7efb59821e19e3788e289301e1e74940c208
File path: C:\Windows\System32\cmd.exe
Digital Signer: Microsoft Corporation
How should the exception be created so that it is scoped as narrowly as possible to minimize the security gap?
A Cortex XSIAM engineer at a SOC downgrades a critical threat intelligence content pack from the Cortex Marketplace while performing routine maintenance. As a result, the SOC team loses access to the latest threat intelligence data.
Which action will restore the functionality of the content pack to its previously installed version?


