During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
According to the NIST SP 800-86. which two types of data are considered volatile? (Choose two.)
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
Refer to the exhibit.
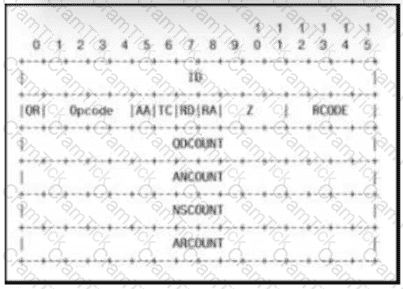
Which field contains DNS header information if the payload is a query or a response?
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
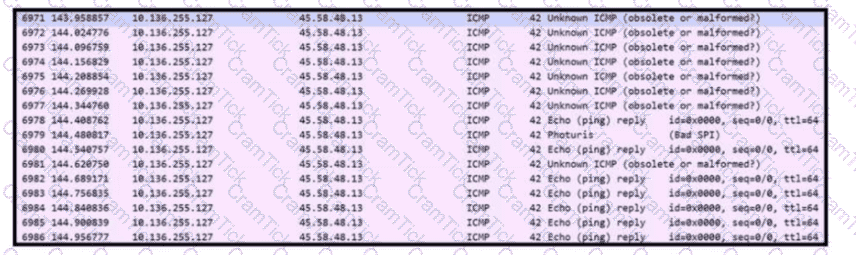
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is occurring?
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?
Refer to the exhibit.
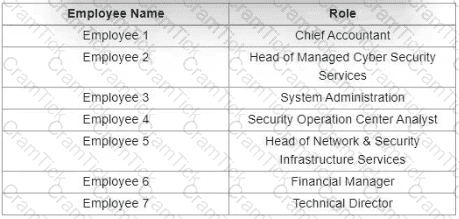
Which stakeholders must be involved when a company workstation is compromised?
An engineer must compare NIST vs ISO frameworks The engineer deeded to compare as readable documentation and also to watch a comparison video review. Using Windows 10 OS. the engineer started a browser and searched for a NIST document and then opened a new tab in the same browser and searched for an ISO document for comparison
The engineer tried to watch the video, but there 'was an audio problem with OS so the engineer had to troubleshoot it At first the engineer started CMD and looked fee a driver path then locked for a corresponding registry in the registry editor The engineer enabled "Audiosrv" in task manager and put it on auto start and the problem was solved Which two components of the OS did the engineer touch? (Choose two)
Refer to the exhibit.
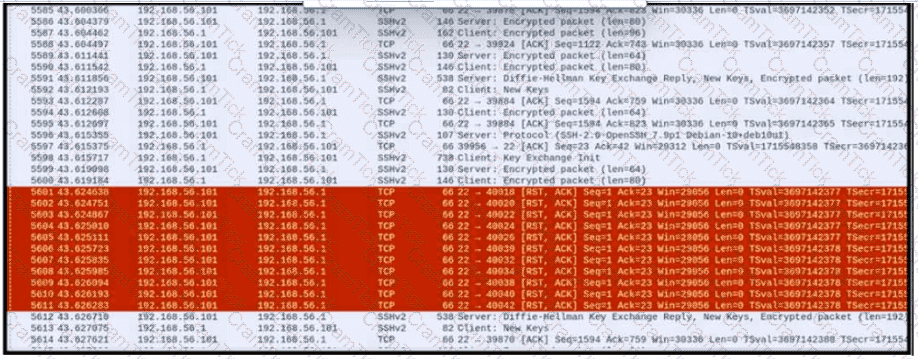
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access How did the attacker gain access?
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet Endpoints are sending multiple DNS requests but with spoofed IP addresses of valid external sources What kind of attack are infected endpoints involved in1?
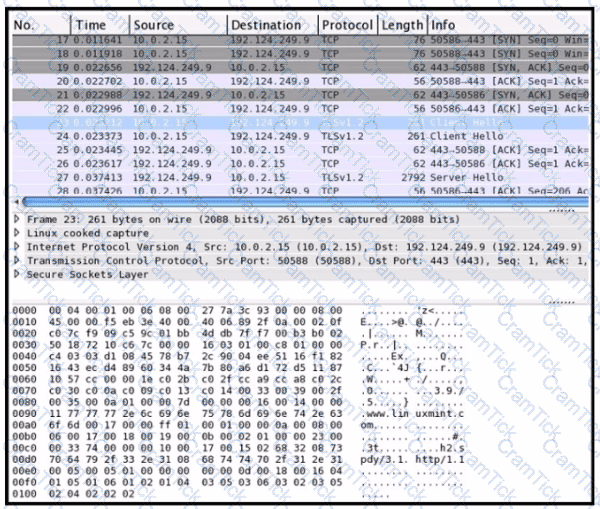
Refer to the exhibit Drag and drop the element names from the left onto the corresponding pieces of the PCAP file on the right.

Which difficulty occurs when log messages are compared from two devices separated by a Layer 3 device that performs Network Address Translation?
A developer is working on a project using a Linux tool that enables writing processes to obtain these required results:
If the process is unsuccessful, a negative value is returned.
If the process is successful, 0 value is returned to the child process, and the process ID is sent to the parent process.
Which component results from this operation?
A cyberattacker notices a security flaw in a software that a company is using They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software To which category of the Cyber Kill Cham model does this event belong?
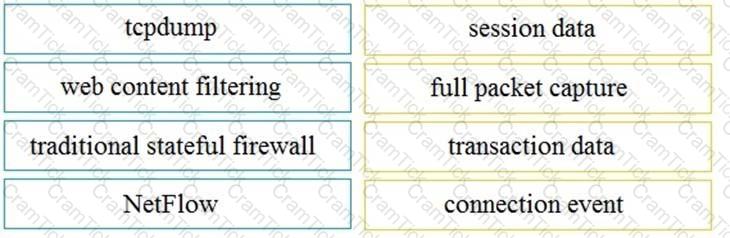
Drag and drop the technologies from the left onto the data types the technologies provide on the right.
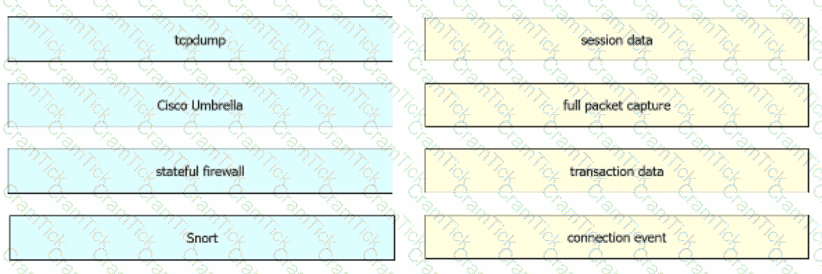
Which event artifact is used to identify HTTP GET requests for a specific file?
An automotive company provides new types of engines and special brakes for rally sports cars. The company has a database of inventions and patents for their engines and technical information Customers can access the database through the company's website after they register and identify themselves. Which type of protected data is accessed by customers?
Refer to the exhibit.
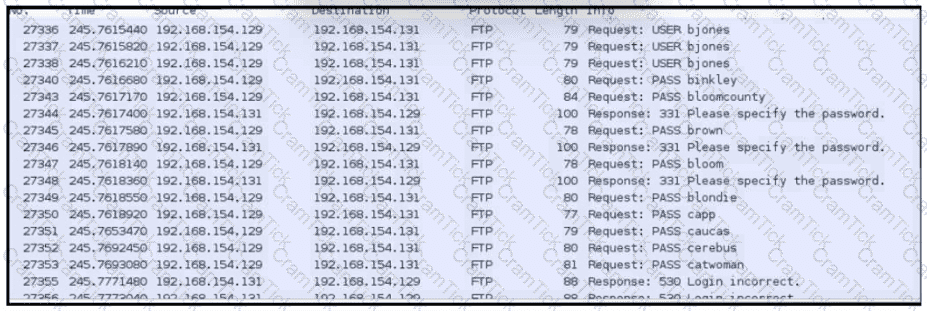
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
Which evasion method involves performing actions slower than normal to prevent detection?
An analyst received a ticket about degraded processing capability for one of the HR department's servers. On the same day, an engineer noticed disabled antivirus software and could not determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
An engineer configured regular expression “.”\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]" on Cisco ASA firewall. What does this regular expression do?
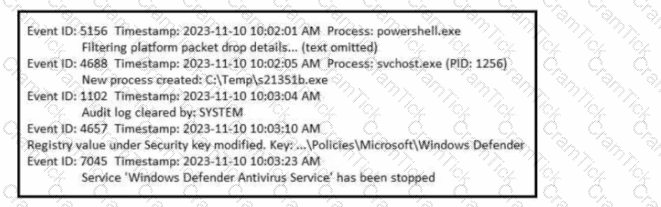
Refer to the exhibit. A SOC analyst is examining the Windows security logs of one of the endpoints. What is the possible reason for this event log?
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
What is a collection of compromised machines that attackers use to carry out a DDoS attack?

Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
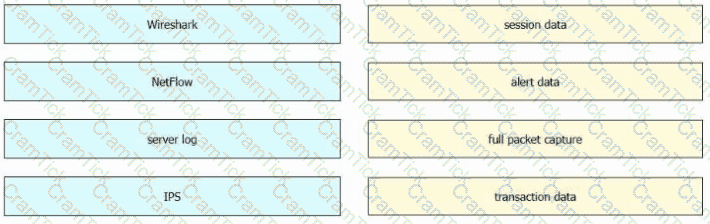
Drag and drop the data sources from the left onto the corresponding data types on the right.
Which security model assumes an attacker within and outside of the network and enforces strict verification before connecting to any system or resource within the organization?
Which element is included in an incident response plan as stated m NIST SP800-617
Refer to the exhibit.
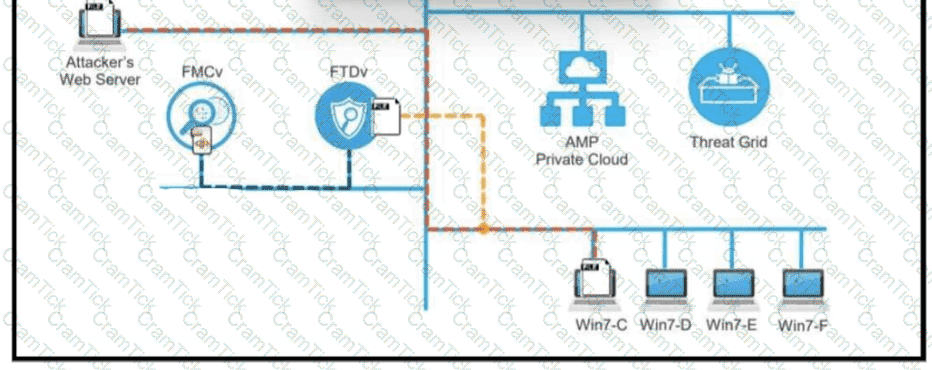
A workstation downloads a malicious docx file from the Internet and a copy is sent to FTDv. The FTDv sends the file hash to FMC and the tile event is recorded what would have occurred with stronger data visibility.
Refer to the exhibit.
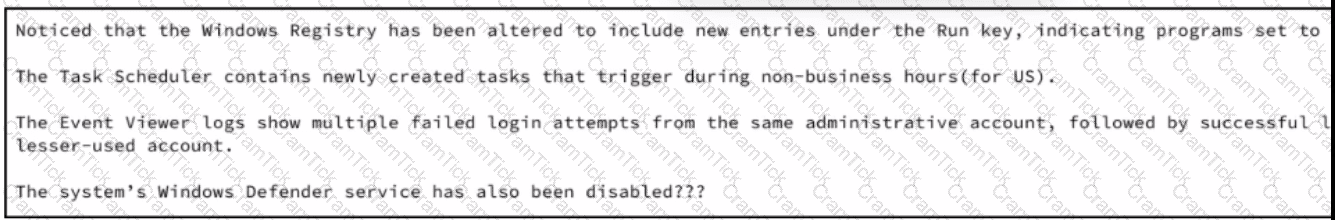
A security analyst wraps up the shift and passed open ticket notes to the night shift SOC team analyst. The ticket name in question is "Investigating suspicious activity on a Windows Server’’. Which operating system components must the analyst prioritize to uncover the attacker's persistence mechanisms?
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
Drag and drop the technology on the left onto the data type the technology provides on the right.
What is the difference between the rule-based detection when compared to behavioral detection?
Developers must implement tasks on remote Windows environments. They decided to use scripts for enterprise applications through PowerShell. Why does the functionality not work?
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?
A vulnerability analyst is performing the monthly scan data review Output data is very big and getting bigger each month The analyst decides to create a more efficient process to complete the task on time All false positives and true positives are excluded from the results The remaining findings will be assigned to a technical team for further remediation What is the result of such activity?
Refer to the exhibit.
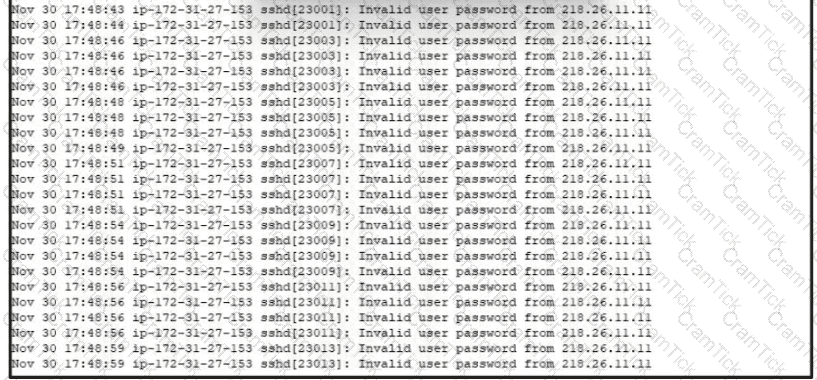
A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?
What is the difference between indicator of attack (loA) and indicators of compromise (loC)?
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
What is the name of the technology that searches for and reports on known weaknesses and flaws present in an organization’s IT infrastructure?
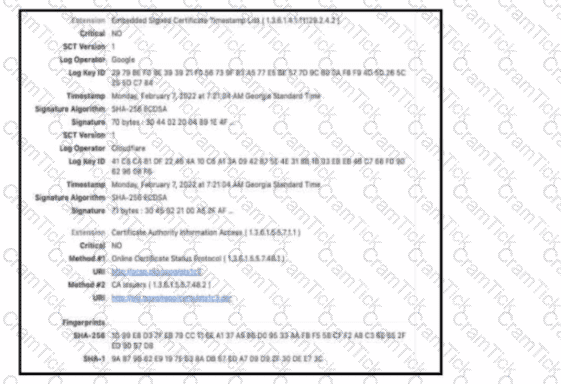
Refer to the exhibit. The figure shows an X 509 certificate. Which field represents the digital cryptographic algorithm used by the issuer to sign the certificate?
Which signature impacts network traffic by causing legitimate traffic to be blocked?
What is the impact of false negative alerts when compared to true negative alerts?
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
Refer to the exhibit.
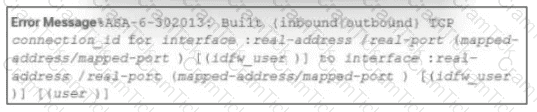
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
Refer to the exhibit.
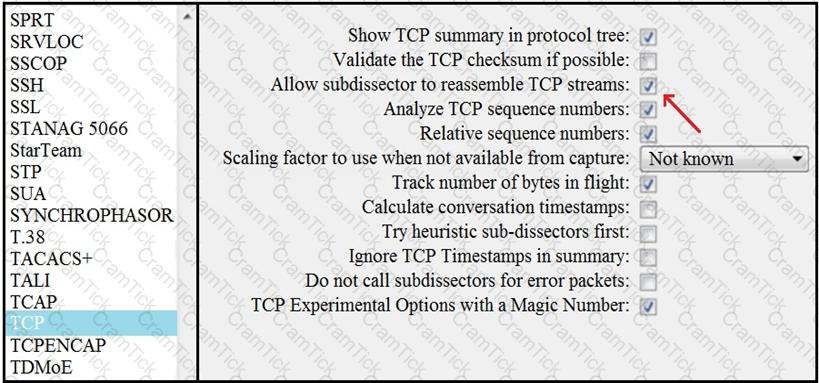
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
What describes the concept of data consistently and readily being accessible for legitimate users?
What describes the impact of false-positive alerts compared to false-negative alerts?
A security consultant must change the identity access management model fof their organization The new approach will put responsibility on the owner, who will decide whichusers will have access to which resources Which low-cost model must be used for this purpose?
A company encountered a breach on its web servers using IIS 7 5 Dunng the investigation, an engineer discovered that an attacker read and altered the data on a secure communication using TLS 1 2 and intercepted sensitive information by downgrading a connection to export-grade cryptography. The engineer must mitigate similar incidents in the future and ensure that clients and servers always negotiate with the most secure protocol versions and cryptographic parameters. Which action does the engineer recommend?
Which type of data must an engineer capture to analyze payload and header information?
What is the key difference between mandatory access control (MAC) and discretionary access control (DAC)?
What does an attacker use to determine which network ports are listening on a potential target device?
What is the impact of false positive alerts on business compared to true positive?
What is the communication channel established from a compromised machine back to the attacker?
The Cisco Zero Trust Architecture simplifies the zero trust journey into three critical areas. Drag and drop the definitions onto the graphic to describe zero trust from the Cisco perspective.
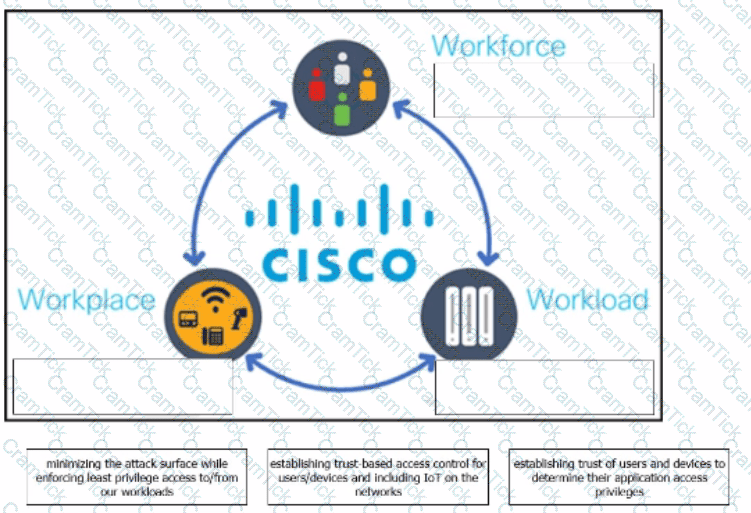
Refer to the exhibit.
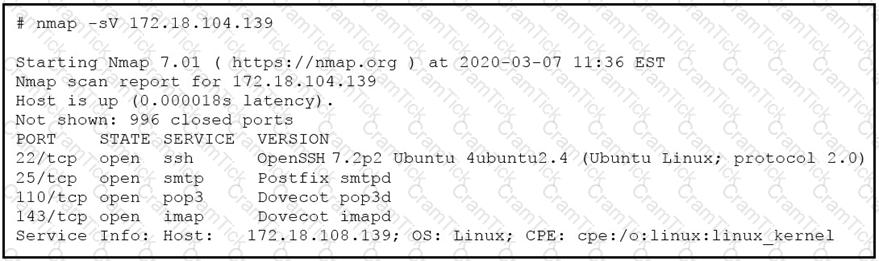
What does the output indicate about the server with the IP address 172.18.104.139?
What describes the difference when comparing attack surface and vulnerability in practice?
According to the September 2020 threat intelligence feeds a new malware called Egregor was introduced and used in many attacks. Distnbution of Egregor is pnmanly through a Cobalt Strike that has been installed on victim's workstations using RDP exploits Malware exfiltrates the victim's data to a command and control server. The data is used to force victims pay or lose it by publicly releasing it. Which type of attack is described?
Why should an engineer use a full packet capture to investigate a security breach?
A security specialist is investigating an incident regarding a recent major breach in the organization. The accounting data from a 24-month period is affected due to a trojan detected in a department's critical server. A security analyst investigates the incident and discovers that an incident response team member who detected a trojan during regular AV scans had made an image of the server for evidence purposes. The security analyst made animage again to compare the hashes of the two images, and they appeared to differ and do not match. Which type of evidence is the security analyst dealing with?
Refer to the exhibit.
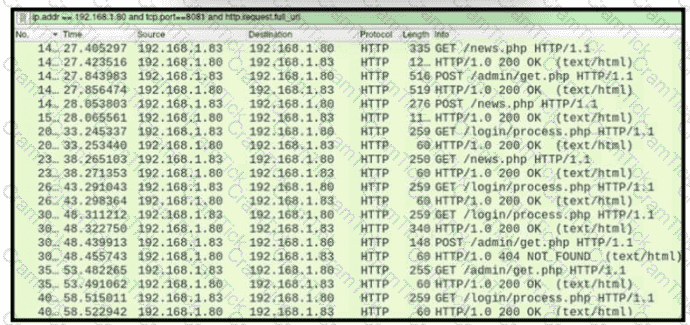
A network administrator is investigating suspicious network activity by analyzing captured traffic. An engineer notices abnormal behavior and discovers that the default user agent is present in the headers of requests and data being transmitted What is occurring?
Refer to the exhibit.
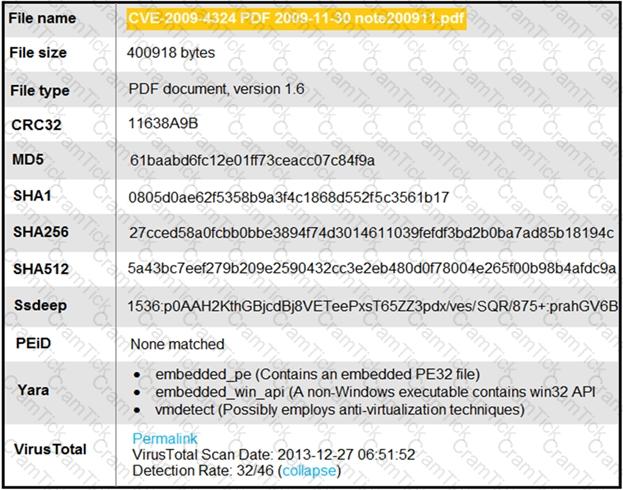
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
Refer to the exhibit.
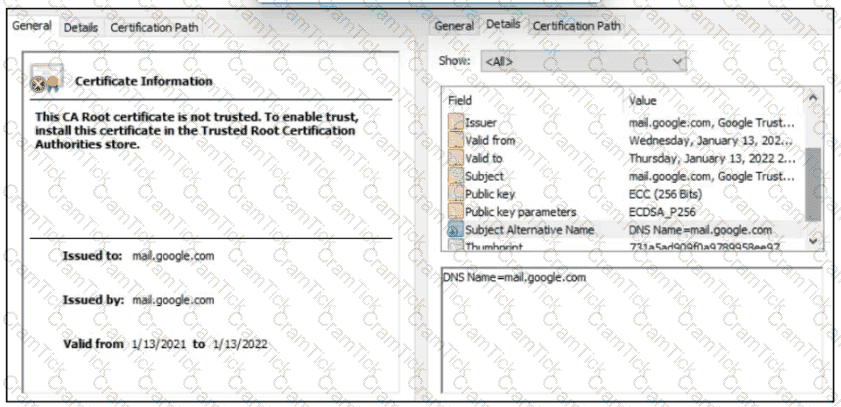
A company employee is connecting to mail google.com from an endpoint device. The website is loaded but with an error. What is occurring?
Which type of evidence supports a theory or an assumption that results from initial evidence?
An engineer received a ticket to investigate a potentially malicious file detected by a malware scanner that was trying to execute multiple commands. During the initial review, the engineer discovered that the file was created two days prior. Further analyses show that the file was downloaded from a known malicious domain after a successful phishing attempt on an asset owner. At which phase of the Cyber Kill Chain was this attack mitigated?
Which data type is necessary to get information about source/destination ports?
Which security technology allows only a set of pre-approved applications to run on a system?
What does this regular expression do?
192|172).(168|1[6-9]|2[0-9]|3[0-1]).[0-9]{1,3}.[0-9]{1,3}\b
What are two differences and benefits of packet filtering, stateful firewalling, and deep packet inspections? (Choose two.)
A security engineer must investigate a recent breach within the organization. An engineer noticed that a breached workstation is trying to connect to the domain "Ranso4730-mware92-647". which is known as malicious. In which step of the Cyber Kill Chain is this event?
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
CyberOps Associate | 200-201 Written Exam | 200-201 Questions Answers | 200-201 Test Prep | 200-201 CyberOps Associate Actual Questions | Understanding Cisco Cybersecurity Operations Fundamentals (200-201 CBROPS) Exam Questions PDF | CyberOps Associate Free Questions | 200-201 Online Exam | 200-201 Practice Test | 200-201 PDF | 200-201 CyberOps Associate Dumps | 200-201 Test Questions | 200-201 Study Material | 200-201 Exam Preparation | 200-201 Valid Dumps | 200-201 Real Questions | 200-201 CyberOps Associate Practice Test | CyberOps Associate 200-201 Dumps | Understanding Cisco Cybersecurity Operations Fundamentals (200-201 CBROPS) Exam Questions


