Company ABC has decided to deploy the controllers using the On-Prem method. How does the administrator upload the WAN Edge list to the vManage?
A)
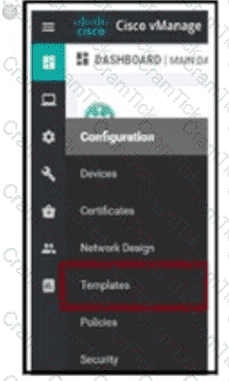
B)
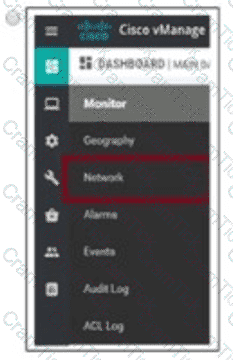
C)
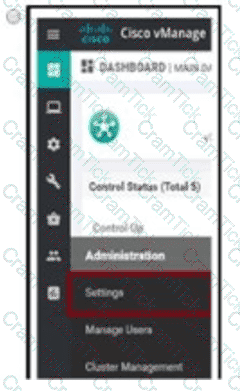
D)
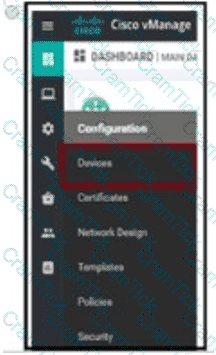
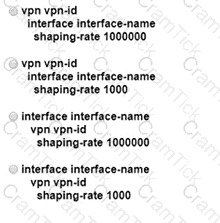
An engineer is configuring a shaping rate of 1 Mbps on the WAN link of a WAN Edge router Which configuration accomplishes this task’?
Which TLOC color is used for site-to-site communication in a Google Cloud integration with Cisco SD-WAN?
Which protocol Is used by the REST API to communicate with network services in the Cisco SO-WAN network?
Which VPN must be present on at least one interface to install Cisco vManage and integrate it with WAN Edge devices in an overlay network site ID:S4307T7E78F29?
Which type of connection is created between a host VNet and a transit VNet when configuring Cloud OnRamp for laaS?
Which website allows access to visualize the geography screen from vManager using the internet?
An enterprise needs DIA on some of its branches with a common location ID: A041:B70C: D78E::18 Which WAN Edge configuration meets the requirement?
A)
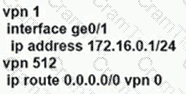
B)
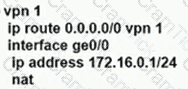
C)
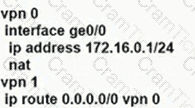
D)
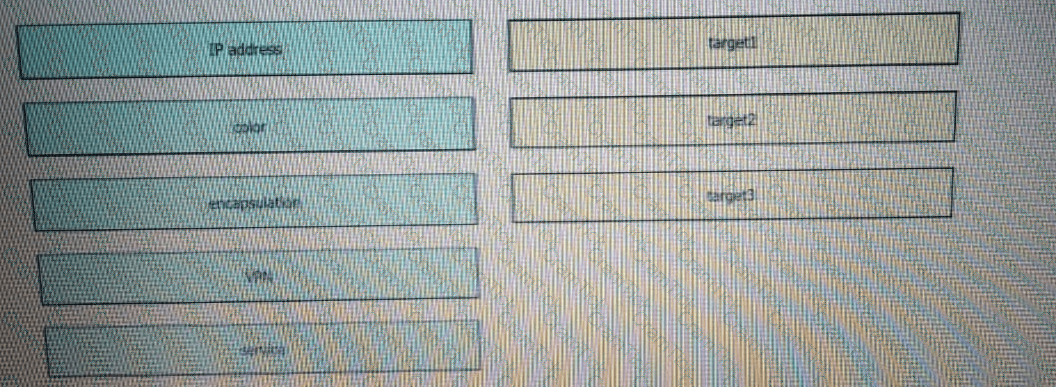
Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used.
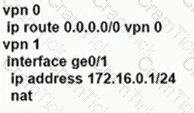
Which service VPN must be reachable from all WAN Edge devices and the controllers?
Which component of the Cisco SD-WAN secure extensible network provides a single pane of glass approach to network monitoring and configuration?
An administrator needs to configure SD-WAN to divert traffic from the company's private network to an ISP network. What action should be taken to accomplish this goal?
Which device information is requited on PNP/ZTP to support the zero-touch onboarding process?
Refer to the exhibit.
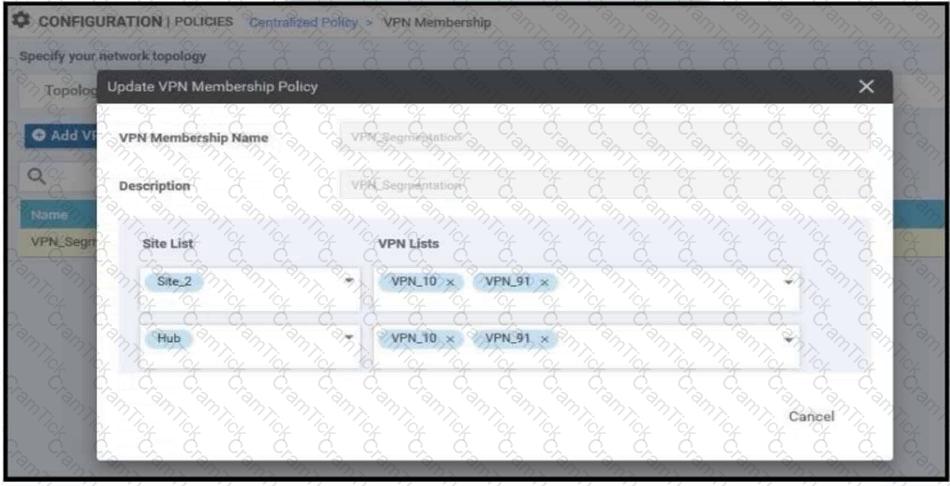
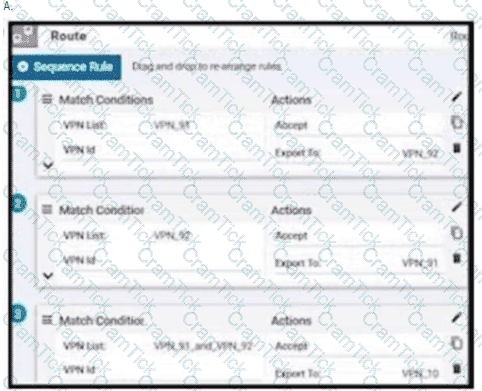
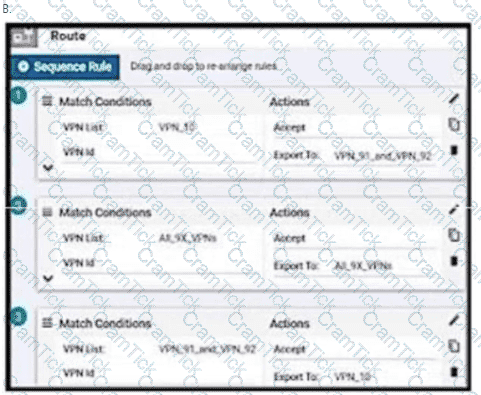
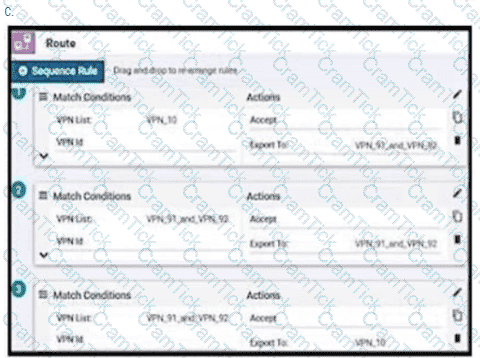
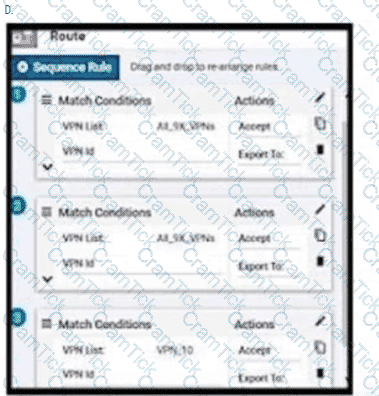
An enterprise has hub and spoke topology where it has several VPNs. An engineer must allow users in VPN91 to reach users in VPN92 and VPN10 to reach VPN91 and VPN92. Which configuration meets these requirements?
Which set of elements are verified by the controller to confirm the identity of edge devices?
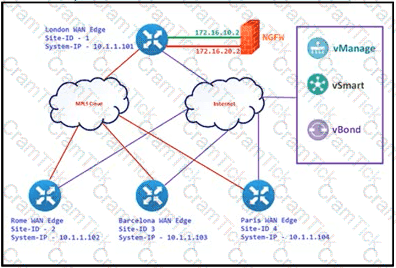
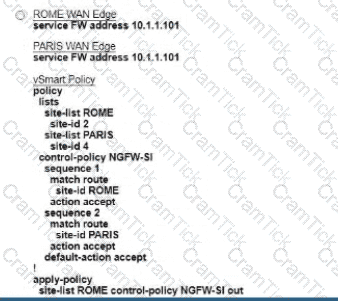
Refer to the exhibit. The Cisco SD-VYAN is deployed using the default topology. The engineer v/ants to configure a service insertion policy such that all data traffic between Rome to Paris is forwarded through the NGFW located in London. Which configuration fulfills this requirement, assuming that the Sen/ice VPN ID is 1?
A)

B)

C)

D)
What is the result during a WAN Edge software upgrade process if the version of the WAN Edge software is higher than the one running on a controller device?
An organization wants to use the cisco SD-WAN regionalized service-chaining feature to optimize cost and user experience with application in the network, which allows branch routers to analyze and steer traffic toward the required network function. Which feature meets this requirement?
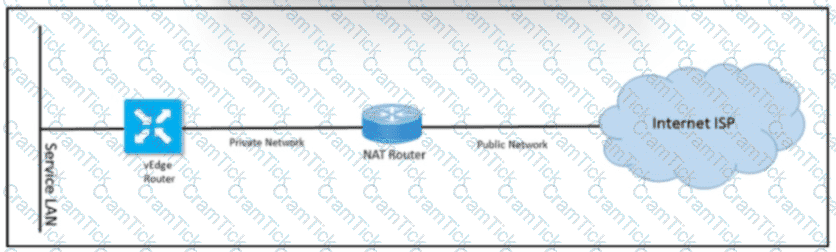
Refer to the exhibit Which NAT types must the engineer configure for the vEdge router to bring up the data plane tunnels?
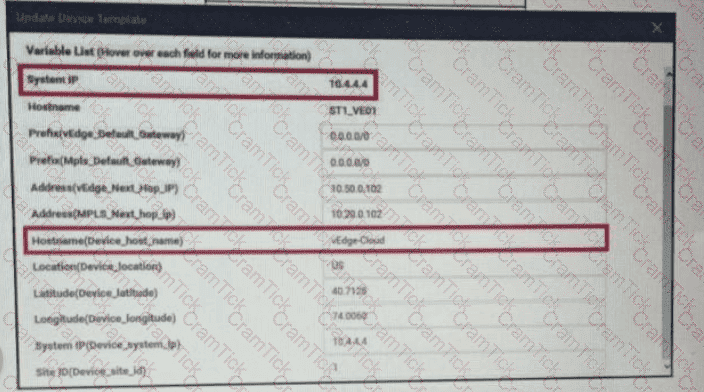
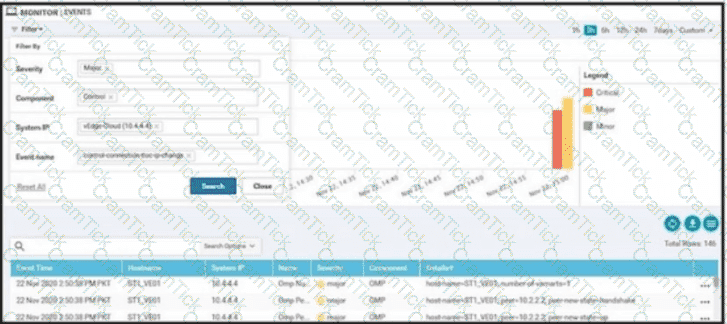
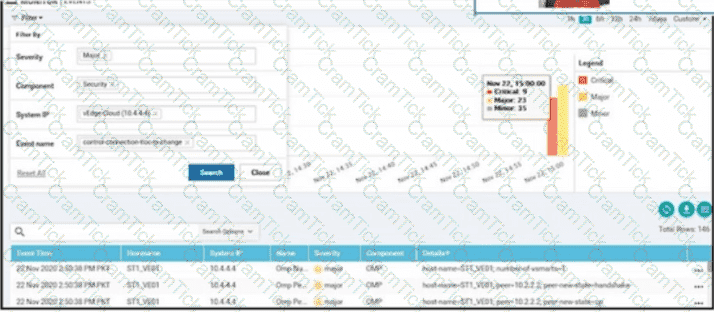
Refer to the exhibit. vManage logs are available for the past few months. A device name change deployed mistakenly at a critical site. How is the device name change tracked by operation and design teams?
A)
B)
C)
Which component is used for stateful inspection of TCP, UDP. and ICMP flows in Cisco SD-WAN firewall policies?
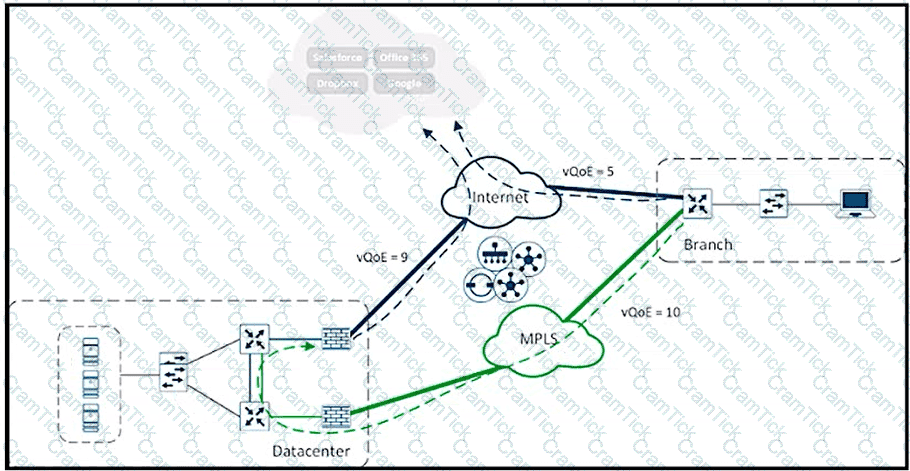
Refer to the exhibit. A user in the branch is connecting to Office 365 for the first time. Over which path does the branch WAN Edge router traffic follow?
In the Cisco SD_WAN solution, vSmart controller is responsible for which two actions? (Choose two.)
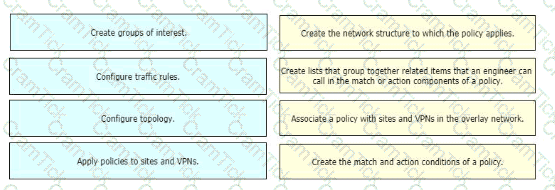
Drag and drop the vManage policy configuration procedures from the left onto the correct definitions on the right.
Which controller is excluded from the process of checking against the authorized, allowed list?
Exhibit.
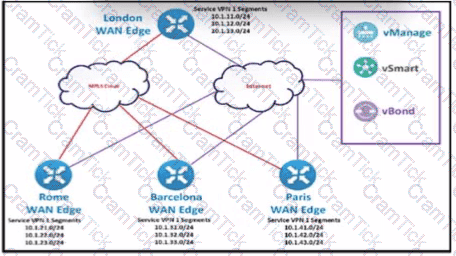
The SD-WAN network is configured with a default full-mash topology. An engineer wants Barcelona and Paris to communicate to each other through the London site using a control Which control policy configuration accomplishes the task?
A)

B)

C)

D)
Which on-the-box security feature supported by the Cisco ISR 4451 SD-WAN device and not on vEdge?
WAN Edge routers are configured manually to use UDP port offset to use nondefault offset values when IPsec tunnels are created. What is the offse range?
Drag and drop the devices from the left into order on the right to upgrade the software from version 19 to version 20.
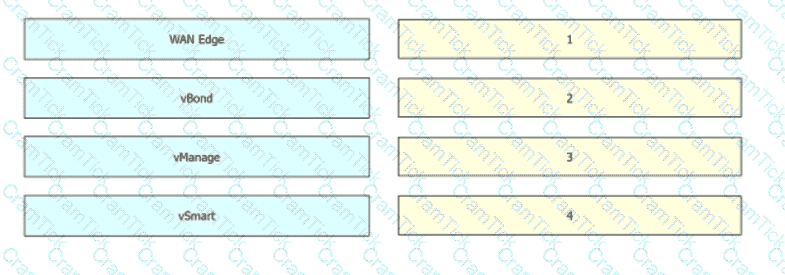
Which attributes are configured to uniquely Identify and represent a TLOC route?
A network administrator is creating an OMP feature template from the vManage GUI to be applied to WAN edge routers. Which configuration attribute will avoid the redistribution of the routes back into the OMP from the LAN side?
An engineer wants to automate the onboarding process for a WAN Edge router with vManage. Which command will accomplish this?
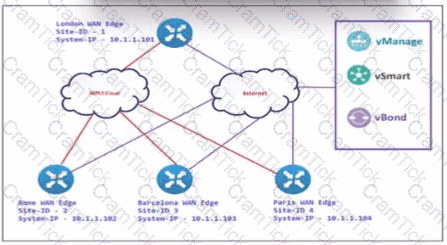
An engineer configures Rome WAN Edge 10 use MPLS cloud as the preferred link to reach Paris WAN Edge and use biz-internet as a backup. Which policy configuration must be led in the outbound direction toward Rome to accomplish the task?
A)

B)

C)

D)

An engineer must configure a centralized policy on a site in which all HTTP traffic should use the Public Internet circuit if the loss on this circuit is below 10%. otherwise MPLS should be used Which configuration wizard fulfils this requirement?
Which command displays BFD session summary information per TLOC on vEdge routers?
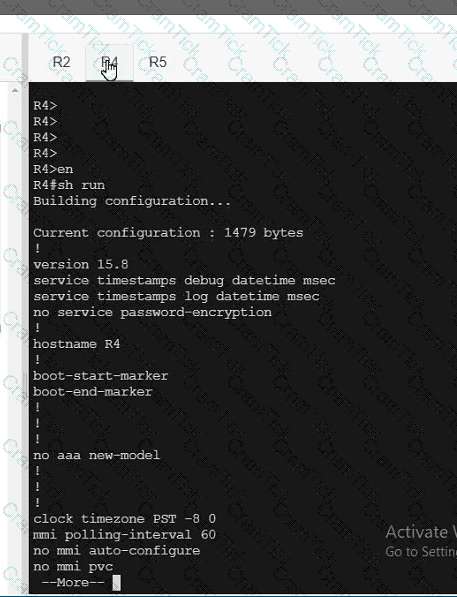
A network is configured with IP connectivity, and the routing protocol between devices started having problems right after the maintenance window to implement network changes. Troubleshoot and resolve to a fully functional network to ensure that:
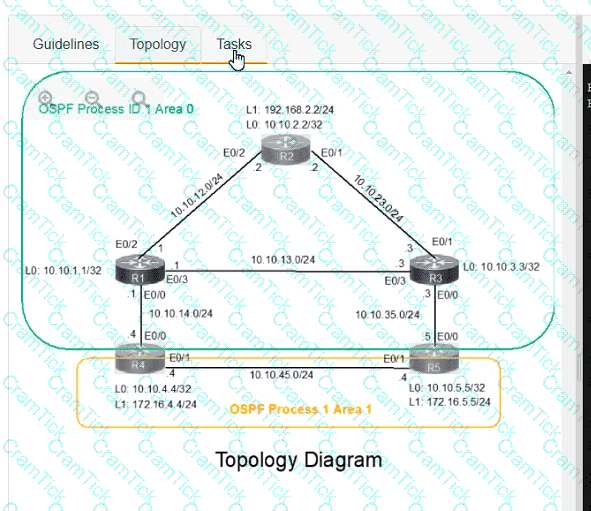
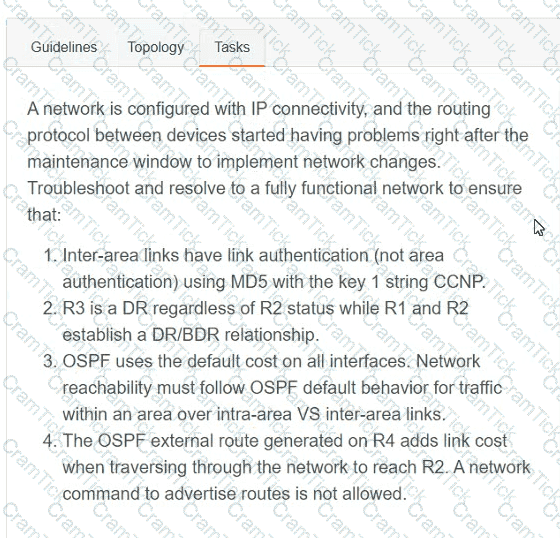
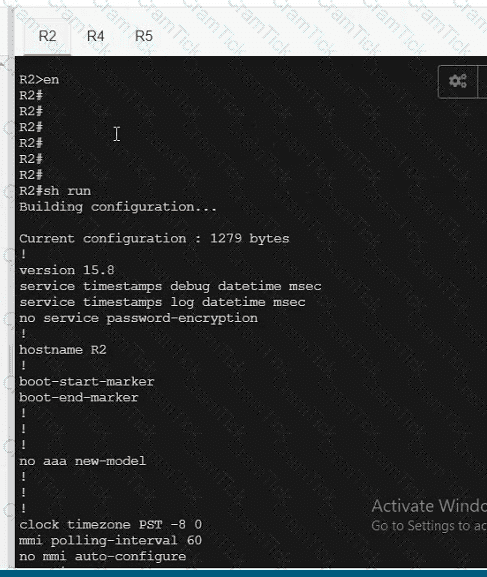
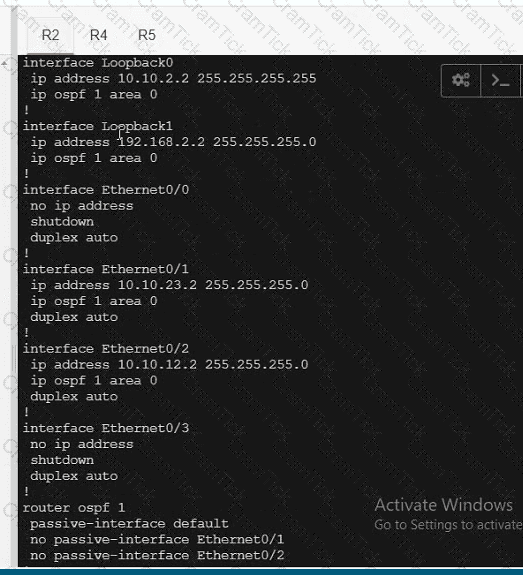
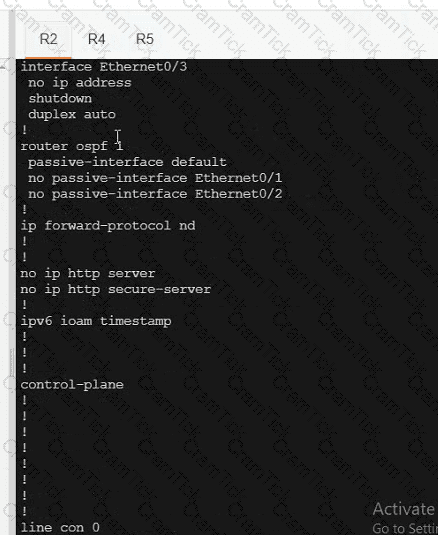
R4
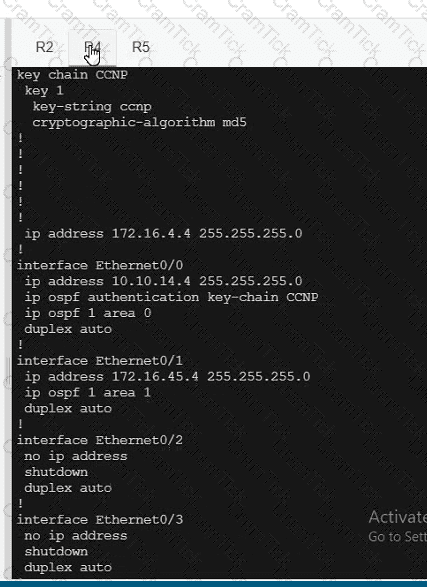
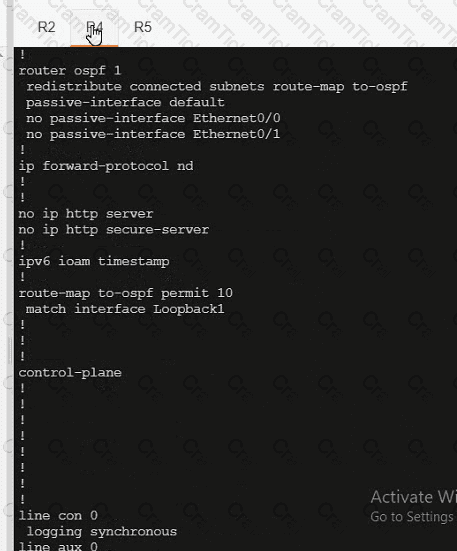
R5
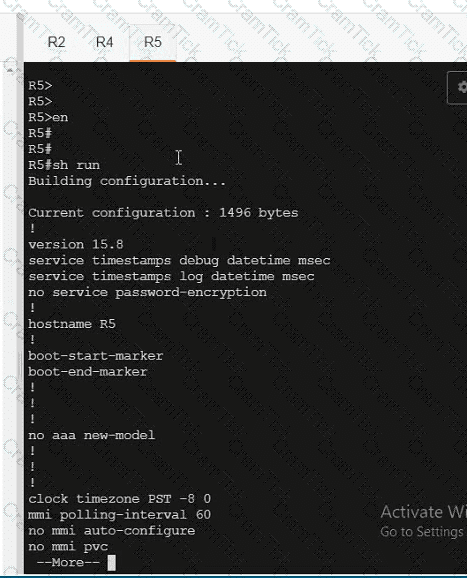
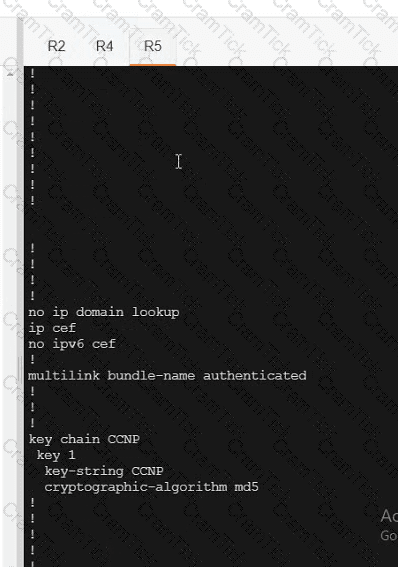
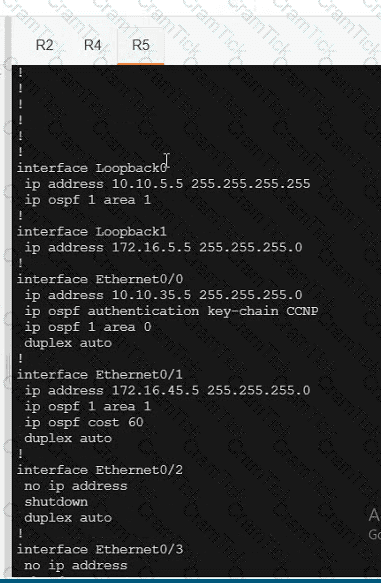
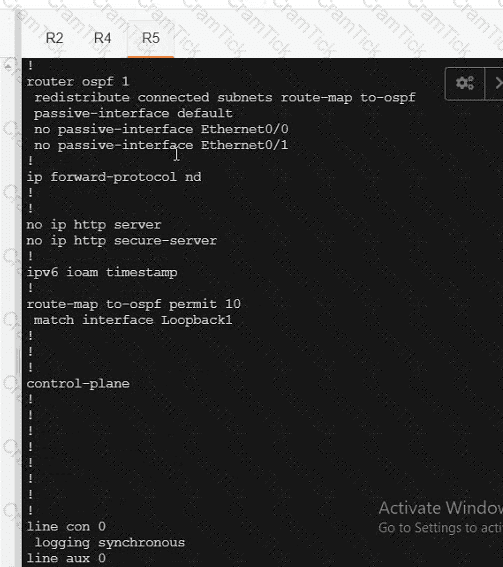
Which SD-WAN devices require multicast PIM and IGMP configurations when setting up SD-WAN multicast?
In which VPN is the NAT operation on an outgoing interface configured for direct Interne! access?
Which protocol is configured on tunnels by default to detect loss, latency, jitter, and path failures in Cisco SD-WAN?
What is the default value for the Multiplier field of the BFD basic configuration in vManage?
Which routing protocol is used to exchange control plane information between vSmart controllers and WAN Edge routers in the Cisco SD-WAN secure extensible network?
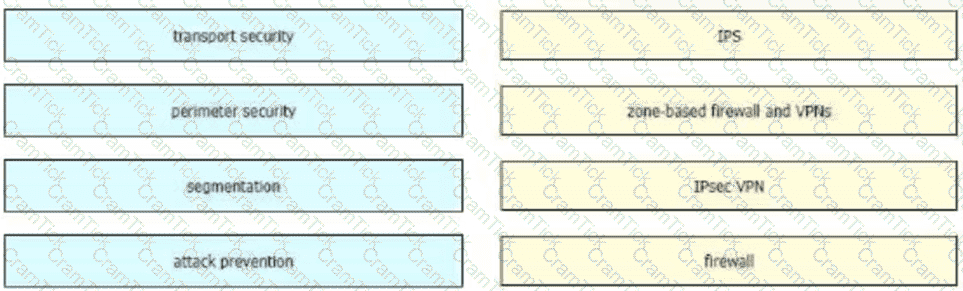
The branch users of an organization must be prevented from accessing malicious destinations, and the local files on users' systems must be protected from malware. Which two Cisco products must the organization deploy? (Choose two.)
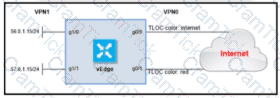
Refer to the exhibit. The ge0/0 interface connects to a 30-MB link. A network administrator wants to always have 10 MB available for high priority traffic. When lower-priority traffic busts exceed 20 MB. Traffic should be redirected to the second WAN interface ge0/1. Which set of configurations accomplishes this task?
A)

B)
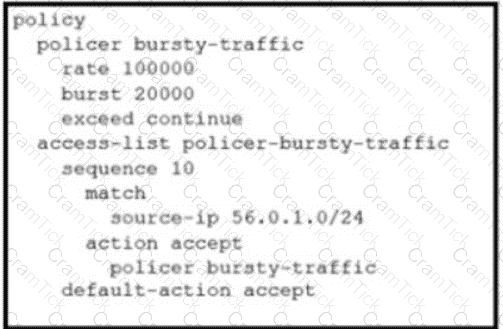
C)
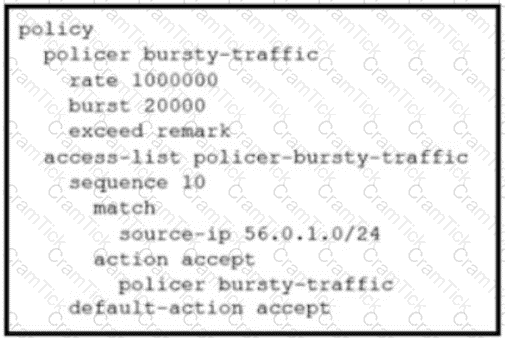
D)
How many cloud gateway instance(s) can be created per region when provisioning Cloud OnRamp for Multicloud from AWS in a multiregion environment?
How does the Cisco SD-WAN Cloud OnRamp solution rate the performance of a SaaS application from a branch office to the cloud via a given path?
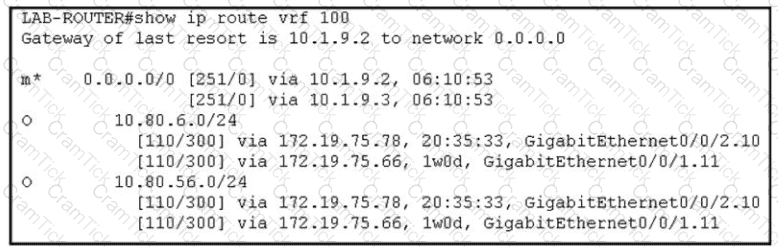
Refer to the exhibit. The network administrator has configured a centralized topology policy that results in the displayed routing table at a branch office. Which two configurations are verified by the output? [Choose two.)
Which cloud based component in cisco SD-WAN is responsible for establishing a secure connection to each WAN edge router and distributes routers and policy information via omp?
Which two different states of a WAN Edge certificate are shown on vManage? (Choose two.)
An engineer is modifying an existing data policy for VPN 115 to meet these additional requirements:
When browsing government websites, the traffic must use direct internet access.
The source address of the traffic leaving the site toward the government websites must be set to an IP range associated with the country itself, a particular TLOC.
The policy configuration is as follows:

Which policy sequence meets the requirements without interfering with other destinations?
An engineer is configuring a data policy for IPv4 prefixes for a single WAN Edge device on a site with multiple WAN Edge devices How is this policy added using the policy configuration wizard?
Which table is used by the vSmart controller to maintain service routes of the WAN Edge routers in the hub and local branches?
Refer to the exhibit.
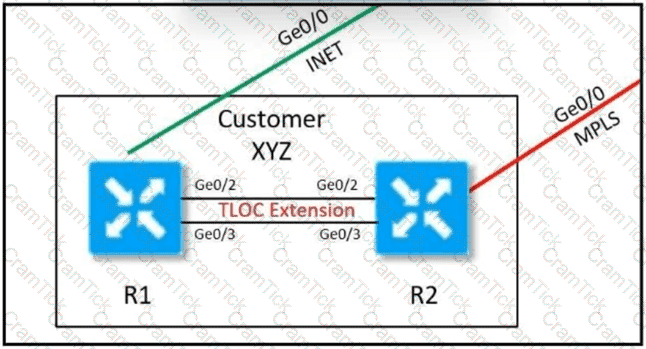
Customer XYZ cannot provision dual connectivity on both of its routers due to budget constraints but wants to use both R1 and R2 interlaces for users behind them for load balancing toward the hub site. Which configuration achieves this objective?


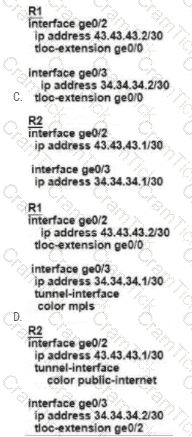
Which control policy assigned to Drenches in the out direction establishes a strict hub-and-spoke topology tor VPN2?
A)

B)

C)

D)
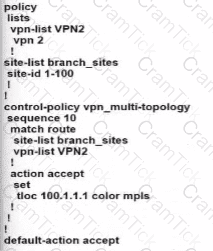
Which two vRoute attributes should be matched or set in vSmart policies and modified by data policies? (Choose two.)
An engineer wants to track tunnel characteristics within an SLA-based policy for convergence. Which policy configuration will achieve this goal?
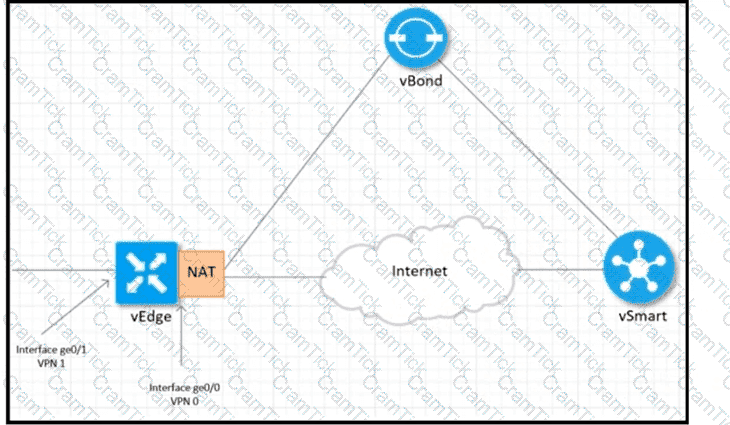
Refer to the exhibit Which configuration sets up direct Internet access for VPN 1?

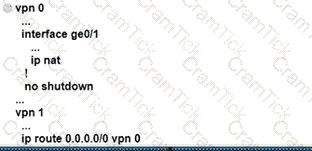
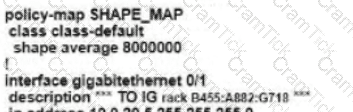
Refer to the exhibit. An enterprise network is connected with an ISP network on an 80 Mbps bandwidth link. The network operation team observes 100 Mbps traffic on the 1Gig-ISP link during peak hours Which configuration provides bandwidth control to avoid traffic congestion during peak hours?
A)
B)
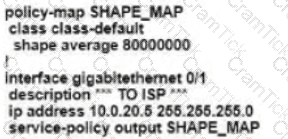
C)
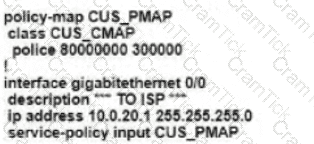
D)
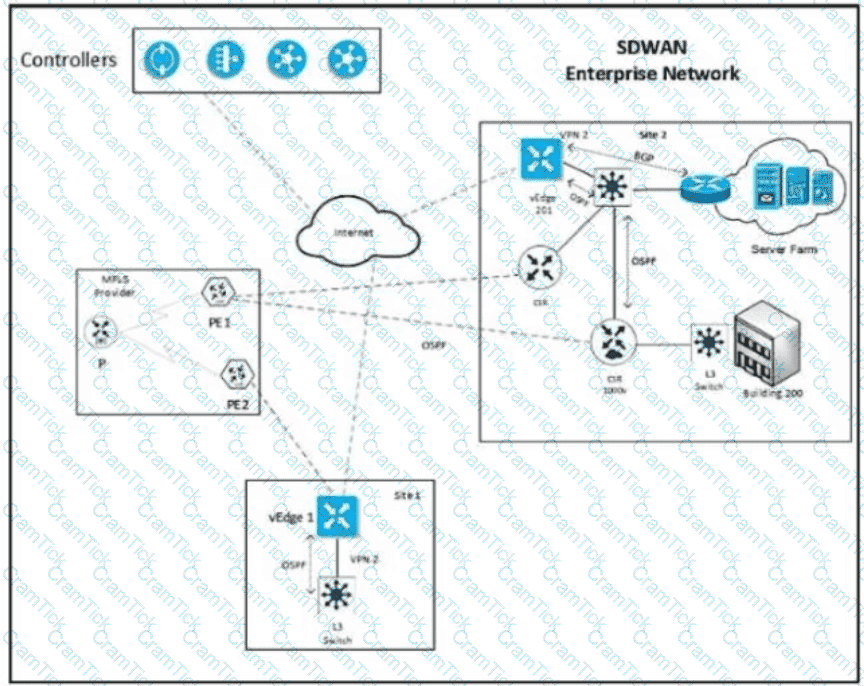
Refer to the exhibit Which configuration ensures that OSPF routes learned from Site2 are reachable at Sitel and vice-versa?
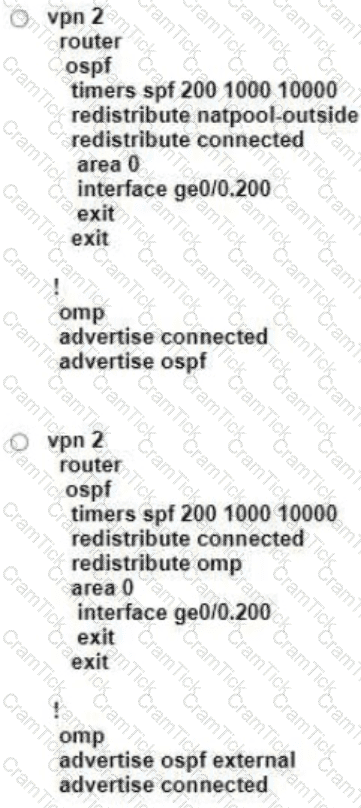
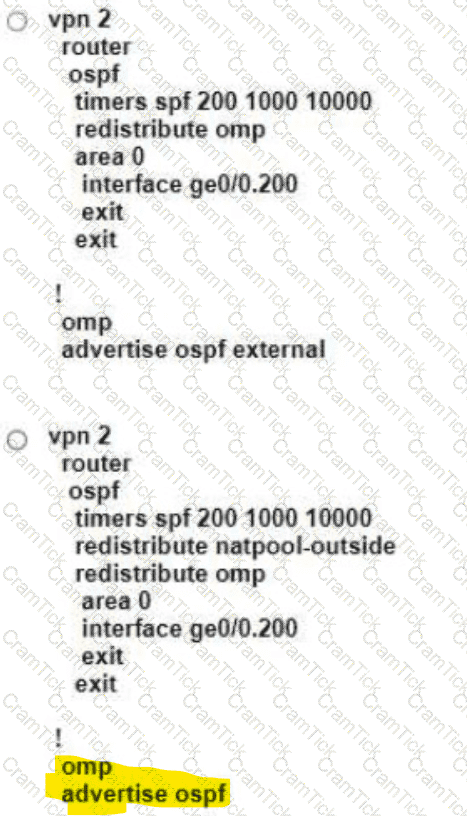
Refer to the exhibit. An engineer must block FTP traffic coming in from a particular Service VPN on a WAN Edge device Which set of steps achieves this goal?
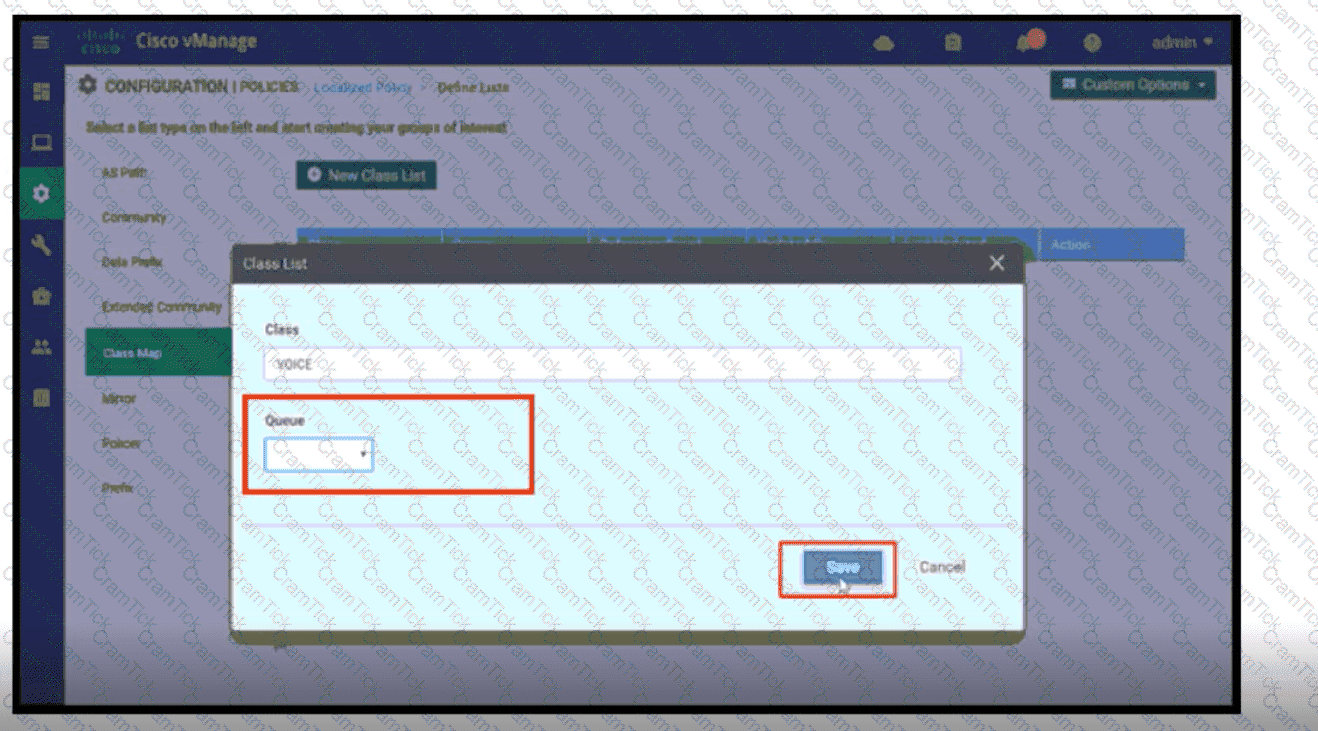
Refer to the exhibit. A network administrator is setting the queueing value for voice traffic for one of the WAN Edge routers using vManager GUI. Which queue value must be set to accomplish this task?
Which scheduling method is configured by default for the eight queues in the cloud vEdge router1?
Drag and drop the security terminologies from the left onto the PCI-compliant network features and devices on the right.
Which action is performed during the onboarding process when a WAN Edge router is connected to ZTP server ztp.viptela com?
Which configuration defines the groups of interest before creation of the access list or route map?
A)
B)
C)
D.
An engineer provisions a WAN Edge router. Which command should be used from the WAN Edge router to activate it with vManage?
What is the default value for the number of paths advertised per prefix in the OMP feature template?
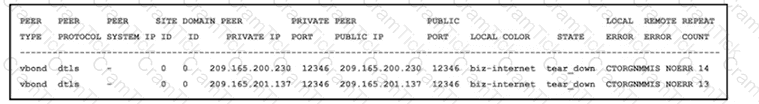
Refer to the exhibit An engineer is getting a CTORGNMMIS error on a controller connection Which action resolves this issue?
How many network interface cards are needed to add in virtual machine settings when installing vSmart controller on VMware vSphere ESXi Hypervisor software?
In Cisco SD-WAN, what protocol is used for control connections between SD-WAN devices?
An engineer must configure local redundancy on a site. Which configuration accomplish this task?
At which layer does the application-aware firewall block applications on a WAN Edge?
Which policy is configured to ensure that a voice packet is always sent on the link with less than a 50 msec delay?
How many concurrent sessions does a vManage REST API have before it invalidates the least recently used session if the maximum concurrent session number is reached?
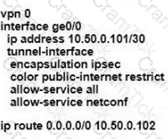
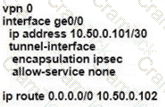
Refer to the exhibit.
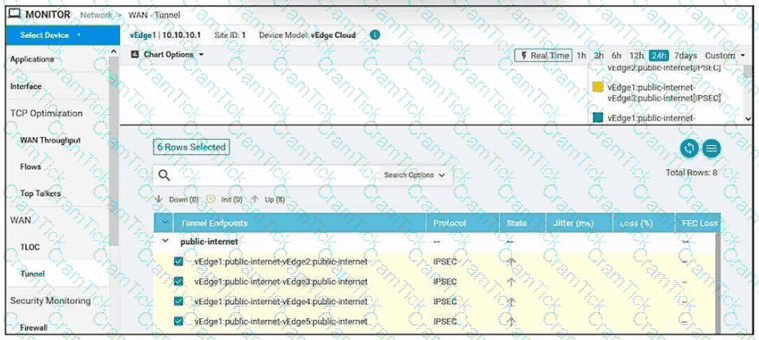
Which command-line configuration on a WAN Edge device achieves these results?
A)
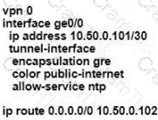
B)
C)
D)
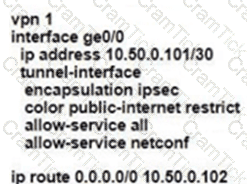
Which two architectural components are part of an SD-WAN high availability vManage cluster? (Choose two.)
How must the application-aware enterprise firewall policies be applied within the same WAN Edge router?
What are the two impacts of losing vManage connectivity to fabric in the Cisco SD-WAN network? (Choose two)
What is the role of the Session Traversal Utilities for NAT server provided by the vBond orchestrator?
Refer to the exhibit.
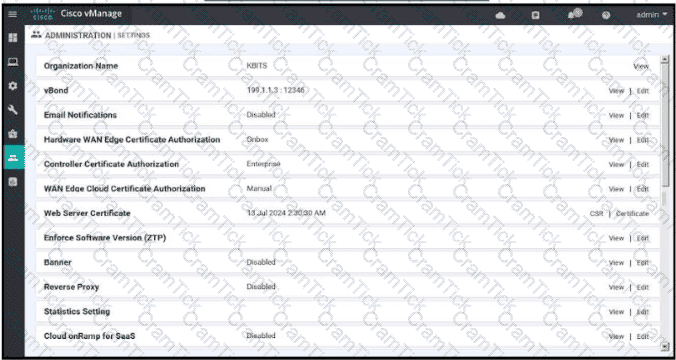
Which two configurations are needed to get the WAN Edges registered with the controllers when certificates are used? (Choose two)
Which protocol is used between redundant vSmart controllers to establish a permanent communication channel?
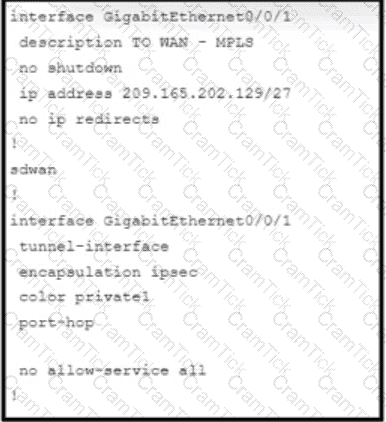
Refer to the exhibit. An engineer is enabling command line access via MPLS for in-band management. Which command completes the partial SD-WAN interface configuration with the highest degree of security?
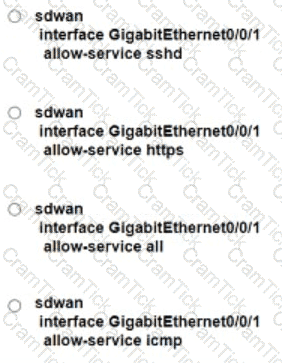
An enterprise has these three WAN connections:
public Internet
business internet
MPLS
An engineer must configure two available links to route traffic via both links. Which configuration achieves this objective?
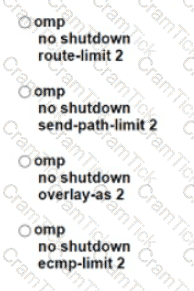
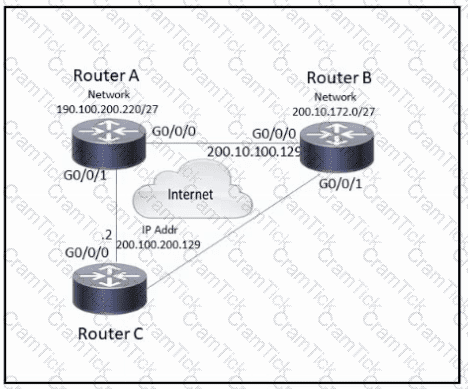
Refer to the exhibit. An engineer configures a hub-and-spoke SD-WAN topology with the requirement that traffic from router A branch to router B branch is guaranteed to flow through the network hub, router C. Which configuration meets the requirement for router A?

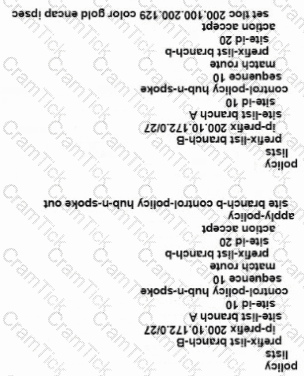
What is a requirement for a WAN Edge to reach vManage, vBond, and vSmart controllers in a data center?
Refer to the exhibit.
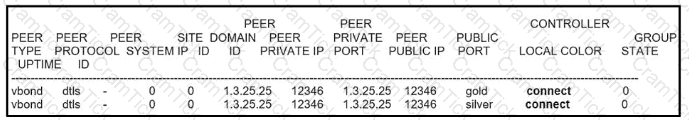
An engineer is troubleshooting a control connection Issue. What does "connect" mean in this how control connections output?
What is the threshold to generate a warning alert about CPU or memory usage on a WAN Edge router?
An engineer must apply the configuration for certificate installation to vBond Orchestrator and vSmart Controller. Which configuration accomplishes this task?
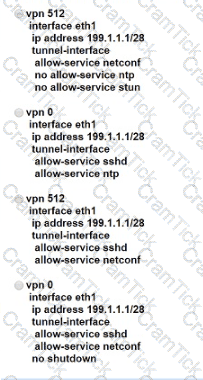
How do WAN Edge devices operate when vSmart is inaccessible or fails to be reached by the WAN Edge?
What is the main purpose of using TLOC extensions in WAN Edge router configuration?
A network administrator is configuring VRRP to avoid a traffic black hole when the transport side of the network is down on the master device. What must be configured to get the fastest failover to standby?
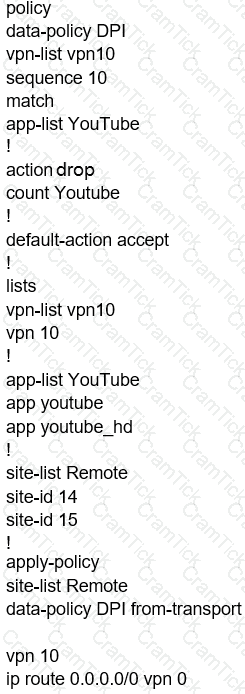
Which configuration allows users to reach YouTube from a local Internet breakout?
A)
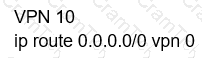
B)
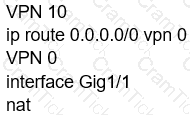
C)
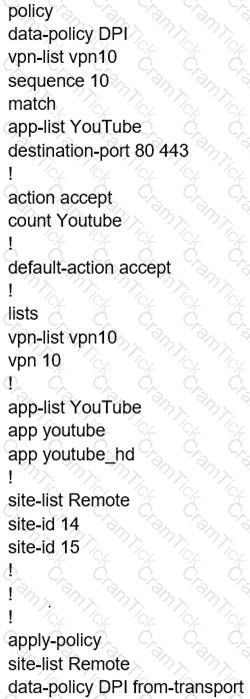
D)
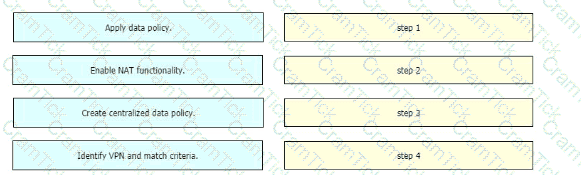
Drag and drop the actions from the left into the correct sequence on the right to create a data policy to direct traffic to the Internet exit.
Which SD-WAN component detects path performance information in the organization to report the issue to the service provider at site ID:S4288T5E44F04?
Refer to the exhibit.
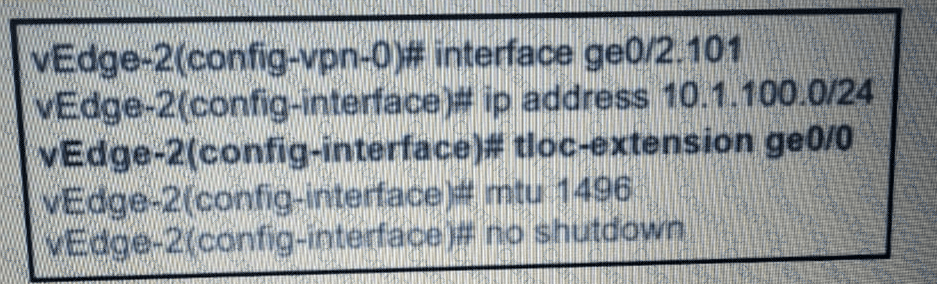
What binding is created using the tloc-extension command?
Which issue triggers the Cisco Umbrella resolver to toward DNS requests to the intelligent proxy?
Which issue triggers the Cisco Umbrella resolver to toward DNS requests to the intelligent proxy?
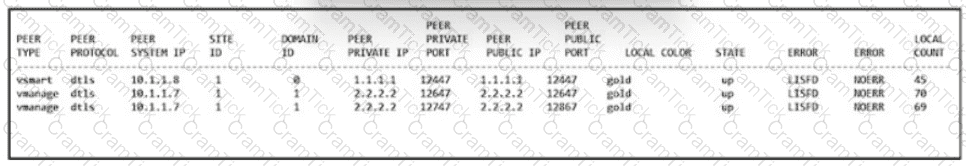
Refer to the exhibit. An engineer is troubleshooting a control connection issue on a WAN Edge device that shows socket errors. The packet capture shows some ICMP packets dropped between the two devices. Which action resolves the issue?
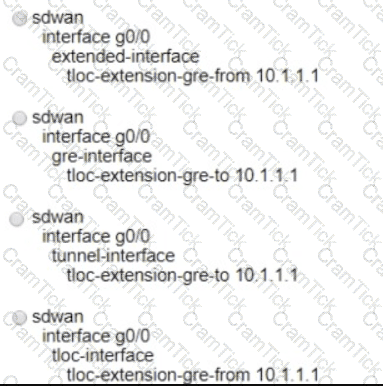
A network administrator is configuring a tunnel interface on a branch Cisco IOS XE router to run TLOC extensions. Which configuration will extend a TLOC over a GRE tunnel to another router in the branch?

Refer to the exhibit A user has selected the options while configuring a VPN Interface Ethernet feature template What is the required configuration parameter the user must set in this template for this feature to function?
Which encryption algorithm secures binding exchanges Between Cisco TrustSec SXP peers?
An organization requires the use of integrated preventative engines, exploit protection, and the most updated and advanced signature-based antivirus with sandboxing and threat intelligence to stop malicious attachments before they reach users and get executed. Which Cisco SD-WAN solution meets the requirements?
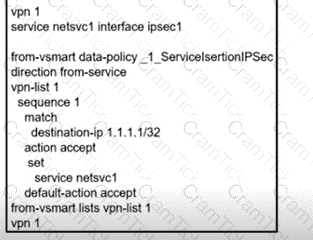
Refer to the exhibit Which command allows traffic through the IPsec tunnel configured in VPN 0?
Which type of policy must be applied on a WAN Edge application-aware firewall to control traffic between two or more VPNs?
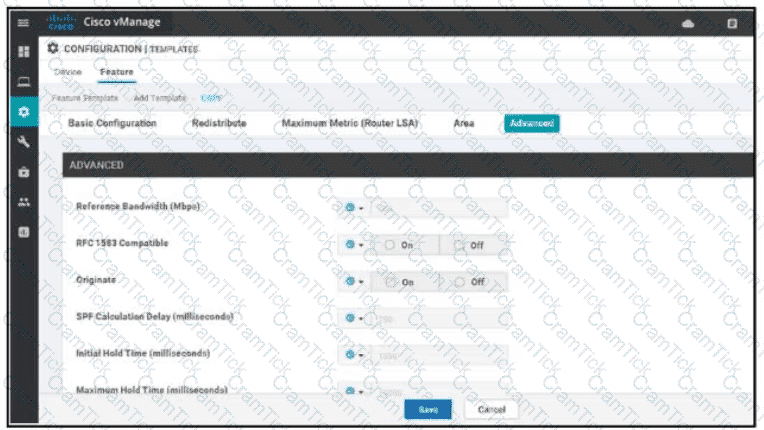
Refer to the exhibit. A network administrator is configuring OSPF advanced configuration pararmeters from a template using the vManager GUI for a branch WAN Edge router to calculate the cost of summary routes to an ASBR. Which action achieves this configuration?
Which component of the Cisco SD-WAN architecture oversees the control plane of overlay network to establish, adjust, and maintain the connections between the WAN Edge devices that form the Cisco SD-WAN fabric?
When VPNs are grouped to create destination zone in Zone-Based Firewall, how many zones can a single VPN be part of?
An engineer must improve video quality by limiting HTTP traffic to the Internet without any failover. Which configuration in vManage achieves this goal?
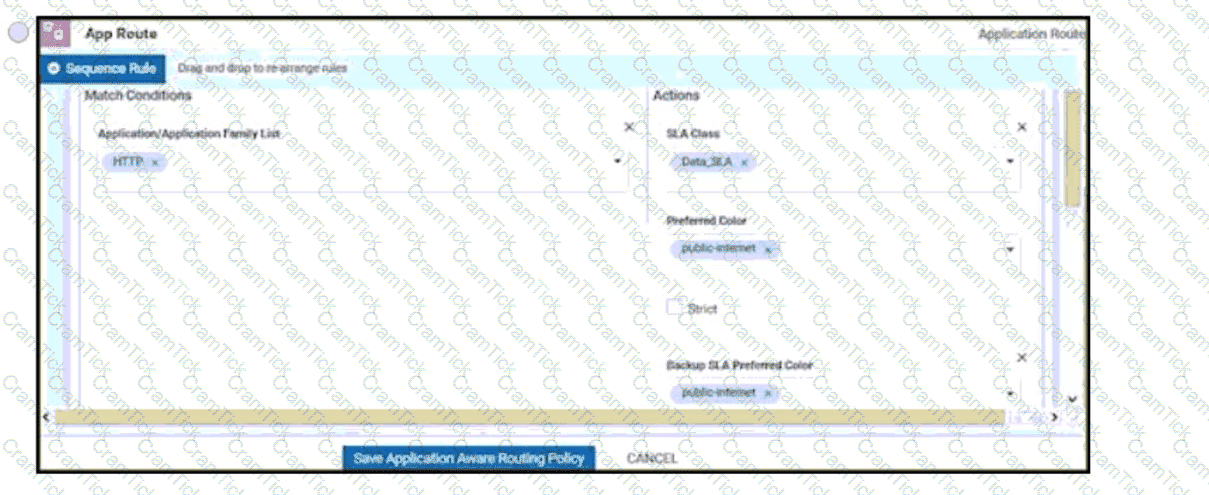
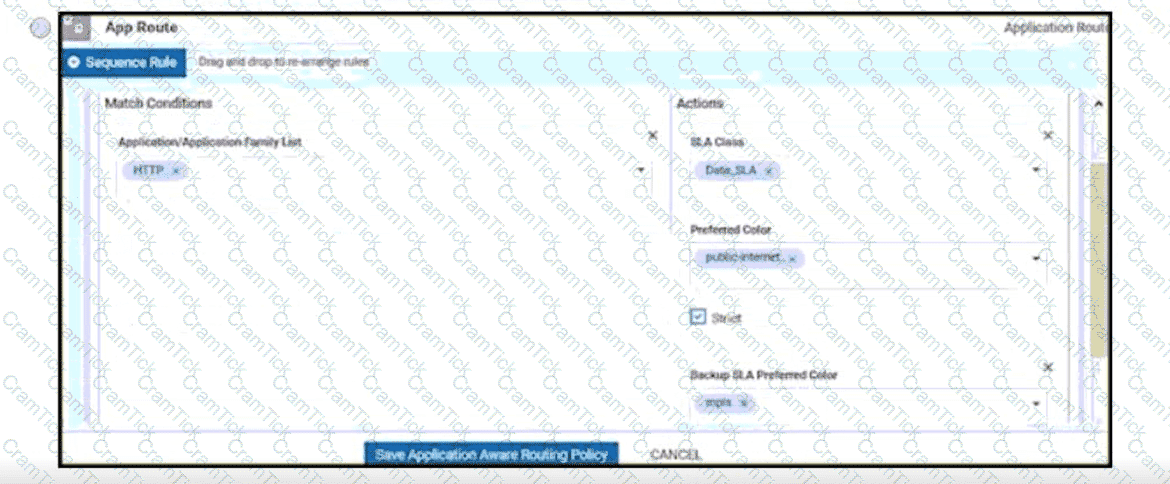
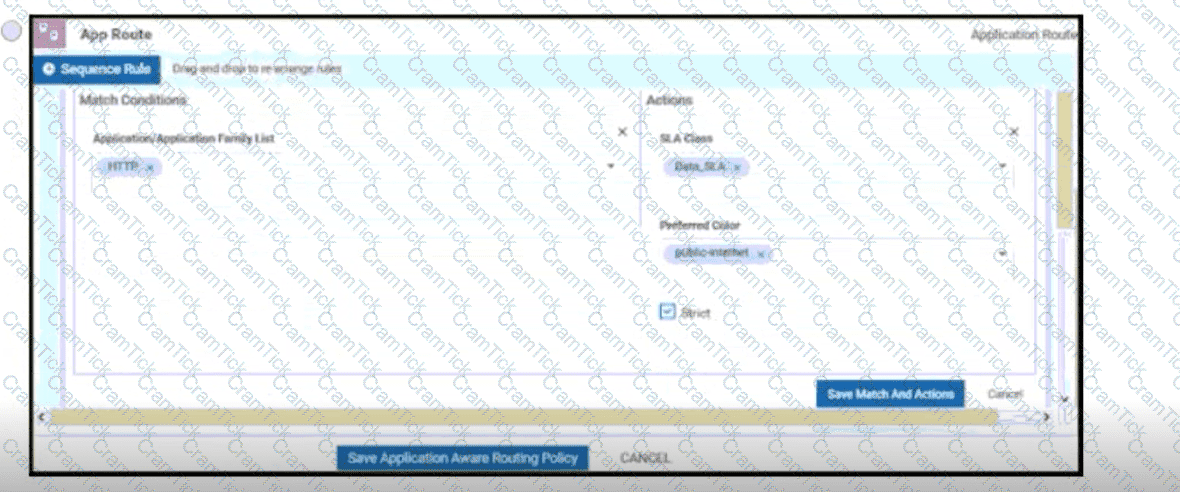
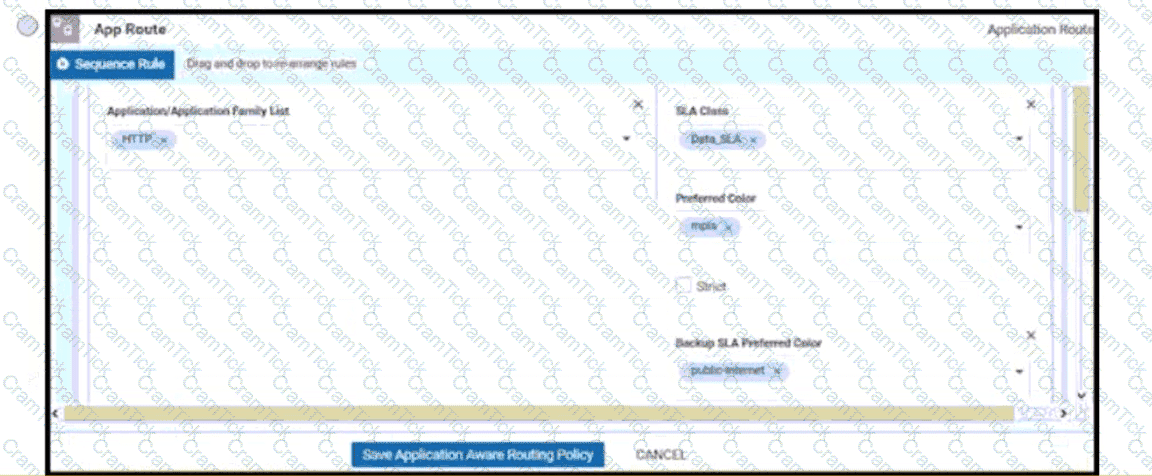
An engineer is configuring a data policy IPv4 prefixes for a site WAN edge device on a site with edge devices. How is this policy added using the policy configuration wizard?
Refer to the exhibit.
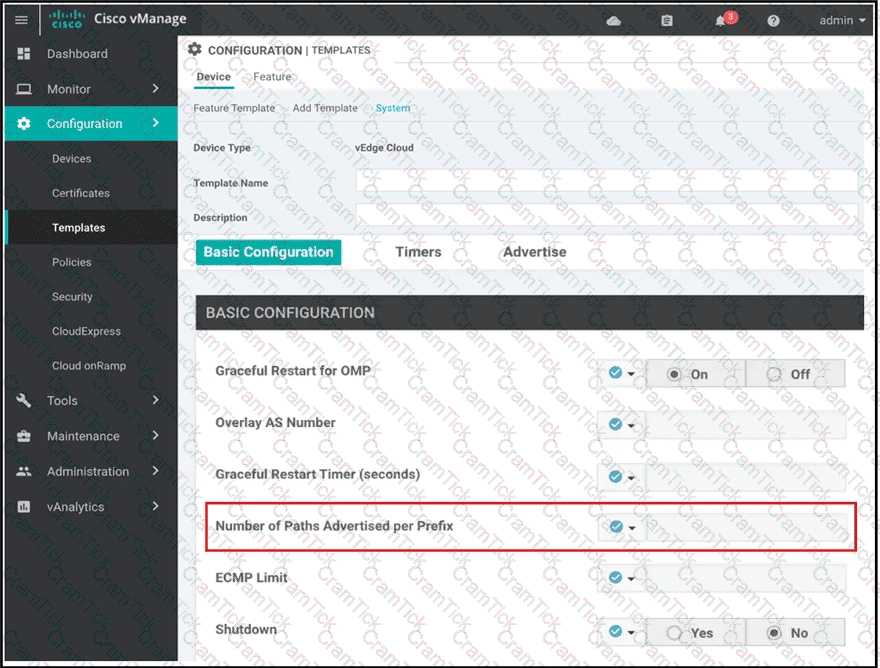
A network administrator is configuring OMP in vManage to advertise all the paths for the same prefix from a site that has two WAN Edge devices Each WAN Edge device is connected to three ISPs and two private MPLS transports. What is the minimum value for 'Number of Paths advertised per Prefix" that should be configured?
How many vManage NMSs should be installed in each domain to achieve scalability and redundancy?
Refer to the exhibit.
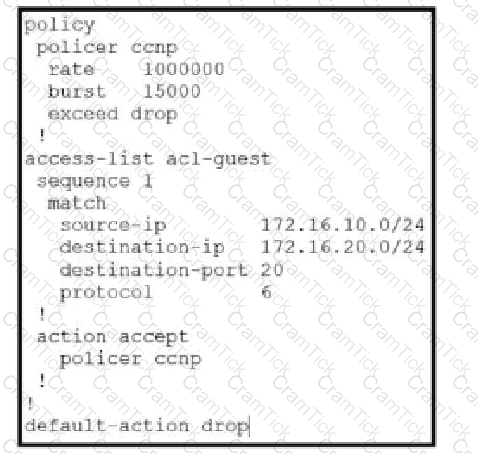
Which QoS treatment results from this configuration after the access list acl-guest is applied inbound on the vpn1 interface?
What are the default username and password for vSmart Controller when it is installed on a VMware ESXi hypervisor'?
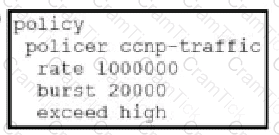
Which configuration changes the packet loss priority from low to highly?
A)
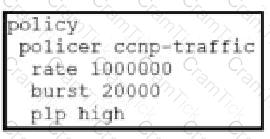
B)
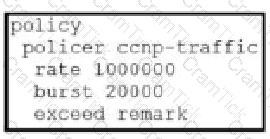
C)
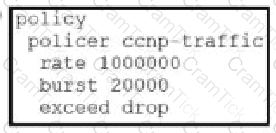
D)
When software is upgraded on a vManage NMS, which two image-adding options store images in a local vManage software repository? (Choose two.)
An engineer is configuring a WAN Edge router for DIA based on matching QoS parameters. Which two actions accomplish this task? (Choose two.)
CCNP Enterprise | 300-415 Written Exam | 300-415 Questions Answers | 300-415 Test Prep | 300-415 CCNP Enterprise Actual Questions | Implementing Cisco SD-WAN Solutions (ENSDWI) Exam Questions PDF | 300-415 Online Exam | 300-415 Practice Test | 300-415 PDF | 300-415 CCNP Enterprise Dumps | 300-415 Test Questions | 300-415 Study Material | 300-415 Exam Preparation | 300-415 Valid Dumps | 300-415 Real Questions | 300-415 CCNP Enterprise Practice Test | CCNP Enterprise 300-415 Dumps | Implementing Cisco SD-WAN Solutions (ENSDWI) Exam Questions


