Identify the event severity level in Windows logs for the events that are not necessarily significant, but may indicate a possible future problem.
Which of the following technique involves scanning the headers of IP packets leaving a network to make sure
thatthe unauthorized or malicious traffic never leaves the internal network?
A mid-sized healthcare organization is facing frequent phishing and ransomware attacks. They lack an internal SOC and want proactive threat detection and response capabilities. Compliance with HIPAA regulations is essential. The organization seeks a solution that includes both monitoring and rapid response to incidents. Which service best meets their needs?
Identify the attack in which the attacker exploits a target system through publicly known but still unpatched vulnerabilities.
Harley is working as a SOC analyst with Powell Tech. Powell Inc. is using Internet Information Service (IIS) version 7.0 to host their website.
Where will Harley find the web server logs, ifhe wants to investigate them for any anomalies?
A manufacturing company is deploying a SIEM system and wants to improve both security monitoring and regulatory compliance. During planning, the team uses an output-driven approach, starting with use cases that address unauthorized access to production control systems. They configure data sources and alerts specific to this use case, ensuring actionable alerts without excessive false positives. After validating success, they move on to use cases related to supply chain disruptions and malware detection. What is the primary advantage of using an output-driven approach in SIEM deployment?
A financial services company implements a SIEM solution to enhance cybersecurity. Despite deployment, it fails to detect known attacks or suspicious activities. Although reports are generated, the team struggles to interpret them. Investigation shows that critical logs from firewalls, IDS, and endpoint devices are not reaching the SIEM. What is the reason the SIEM is not functioning as expected?
Secuzin Corp. is a large enterprise performing millions of financial transactions daily, making it critical to analyze security logs efficiently, detect suspicious activities, and respond to incidents in real time. Its SOC is responsible for managing security logs from various network devices, including firewalls, intrusion detection systems (IDS), authentication servers, and cloud services. To fulfill compliance and regulatory requirements that mandate long-term archival of logs, you need to provide a log storage solution that is scalable to handle increasing log volumes, provides encryption for data security, and is seamlessly accessible. Which storage solution should you choose to meet these long-term log storage requirements?
Which of the following steps of incident handling and response process focus on limiting the scope and extent of an incident?
Sarah Chen is a Level 1 SOC analyst at Centex Healthcare. The SOC detected a potential data breach involving unauthorized access to patient records. Multiple departments need constant updates: Legal needs HIPAA compliance implications, HR needs to coordinate staff training responses, and the MSSP requires technical details to assist containment. Which role serves as the central point of communication between these stakeholders?
David is a SOC analyst responsible for monitoring critical infrastructure. He detects unauthorized applications running on a high-privilege Windows server accessible only by a restricted set of users. The applications were not part of approved deployments, and installations occurred outside business hours. Logs indicate potential system configuration changes around the same timeframe. Which log should he examine to determine when and how these installations occurred?
NationalHealth, a government agency responsible for managing sensitive patient health records, is subject to strict data sovereignty regulations requiring all data to be stored and processed within the country’s borders. Leadership is concerned about outsourcing security operations and needs complete control over patient data handling. The agency faces increasing cyber threats and requires 24/7 security monitoring. They have a large budget and can hire many security professionals. Which SOC model is most suitable?
An organization with a complex IT infrastructure is planning to implement a SIEM solution to improve its threat detection and response capabilities. Due to the scale and complexity of its systems, the organization opts for a phased deployment approach to ensure a smooth implementation and reduce potential risks. Which of the following should be the first phase in their SIEM deployment strategy?
Mark Reynolds, a SOC analyst at a global financial institution, is working on the eradication phase after detecting phishing attacks targeting employees. To ensure attackers cannot reuse malicious infrastructure, Mark implements a technique that blocks known malicious IP addresses used for sending spam emails at the Domain Name System (DNS) level. Which technique is best suited?
The SOC team at CyberSecure Corp is conducting a security review to identify anomalous log entries from firewall logs. The team needs to extract patterns such as email addresses, IP addresses, and URLs to detect unauthorized access attempts, phishing activities, and suspicious external communications. The SOC analyst applies various regular expressions (regex) patterns to filter and analyze logs efficiently. For example, they use \b\d{1,3}.\d{1,3}.\d{1,3}.\d{1,3}\b to match IPv4 addresses. Which regex pattern should the SOC analyst use to extract all hexadecimal color codes found in the logs?
Which of the following command is used to view iptables logs on Ubuntu and Debian distributions?
Charline is working as an L2 SOC Analyst. One day, an L1 SOC Analyst escalated an incident to her for furtherinvestigation and confirmation. Charline, after a thorough investigation, confirmed the incident and assigned it with an initial priority.
What would be her next action according to the SOC workflow?
Mark Reynolds, a SOC analyst at a healthcare organization, is monitoring the SIEM system when he detects a potential security threat: a series of unusual login attempts targeting critical patient data servers. After investigating the alerts and collaborating with the incident response team, the SOC determines that the threat has a “Likely” chance of occurring and could cause “Significant” damage, including operational disruptions, financial loss due to data breaches, and regulatory penalties under HIPAA. Using a standard Risk Matrix, how would this risk be categorized in terms of overall severity?
A mid-sized financial institution’s SOC is overwhelmed by thousands of daily alerts, many based on Indicators of Compromise (IoCs) such as suspicious IPs, hashes, and domains. These alerts lack context about whether they truly pose a threat. Analysts waste time on low-priority incidents while severe threats may be missed. The team lacks tools and intelligence to correlate IoCs with real-world threats, making prioritization difficult and causing alert fatigue. Which poses the greatest challenge in this environment?
DNS logs in the SIEM show an internal host sending many DNS queries with long, encoded subdomains to an external domain. The queries predominantly use TXT records and occur during off-business hours. The external domain is newly registered and has no known business association. Which option best explains this behavior?
Which one of the following is the correct flow for Setting Up a Computer Forensics Lab?
During a routine security audit, analysts discover several web servers still use a vulnerable third-party library flagged for a zero-day exploit. The vulnerability was identified previously and patches were deployed, but the application team rolled back patches due to instability and compatibility issues. The vulnerability remains unaddressed, and no alternative mitigations are in place. How should the security team classify this risk in the context of web application security?
John, a threat analyst at GreenTech Solutions, wants to gather information about specific threats against the organization. He started collecting information from various sources, such as humans, social media, chat room, and so on, and created a report that contains malicious activity.
Which of the following types of threat intelligence did he use?
Which of the following attack can be eradicated by using a safe API to avoid the use of the interpreter entirely?
Emmanuel is working as a SOC analyst in a company named Tobey Tech. The manager of Tobey Tech recently recruited an Incident Response Team (IRT) for his company. In the process of collaboration with the IRT, Emmanueljust escalated an incident to the IRT.
What is the first step that the IRT will do to the incident escalated by Emmanuel?
Ray is a SOC analyst in a company named Queens Tech. One Day, Queens Tech is affected by a DoS/DDoS attack. For the containment of this incident, Ray and his team are trying to provide additional bandwidth to the network devices and increasing the capacity of the servers.
What is Ray and his team doing?
Which of the following data source will a SOC Analyst use to monitor connections to the insecure ports?
Katie is a SOC analyst at an international financial corporation. Her team needs functionality so the system continuously scans logs for anomalies, identifies suspicious activities, notifies analysts when predefined security thresholds are reached, and generates incidents or tickets to ensure immediate response. It must provide details such as event type, duration, affected device, and OS version. Which function should she configure to achieve this?
Which of the following event detection techniques uses User and Entity Behavior Analytics (UEBA)?
During a threat intelligence briefing, a SOC analyst comes across a classified report detailing a sophisticated cybercrime syndicate targeting executives of high-profile financial institutions. These adversaries rarely leave digital footprints and seem to anticipate security measures. Several breaches began with seemingly innocent conversations: a foreign journalist requesting an interview with a CEO and a “security consultant” offering free risk assessments. Further investigation reveals attackers socially engineered employees, manipulated trust, and extracted critical security details long before launching technical attacks. The analyst decides to focus on intelligence involving deception detection and psychological profiling to uncover true intent and methods. Which type of intelligence is the analyst leveraging?
Daniel Clark is a cybersecurity specialist in the Cloud SOC for a government agency. His team needs a security solution that can enforce access policies to prevent unauthorized access to cloud-based applications, monitor and restrict data sharing within SaaS, PaaS, and IaaS environments, ensure compliance with government regulations for data security and privacy, and apply security controls to prevent sensitive data exposure in the cloud. Which Cloud SOC technology is his team using?
Jannet works in a multinational corporation that operates multiple data centers, cloud environments, and on-premises systems. As a SOC analyst, she notices that security incidents are taking too long to detect and investigate. After analyzing this, she discovers that logs from firewalls, endpoint security solutions, authentication servers, and cloud applications are scattered across different systems in various formats. Her team has to manually convert logs into a readable format before investigating incidents. What approach should she implement to accept logs from heterogeneous sources with different formats, convert them into a common format, and improve incident detection and response time?
A security analyst in a multinational corporation’s Threat Intelligence team is tasked with enhancing detection of stealthy malware infections. During an investigation, the analyst observes an unusually high volume of DNS requests directed toward domains that follow patterns commonly associated with Domain Generation Algorithms (DGAs). Recognizing that these automated domain queries could indicate malware attempting to establish communication with command-and-control (C2) infrastructure, the analyst realizes existing detection may be insufficient. The security team needs to define intelligence requirements, including identifying critical data sources, refining detection criteria, and improving monitoring strategies. Which stage of the Cyber Threat Intelligence (CTI) process does this align with?
Where will you find the reputation IP database, if you want to monitor traffic from known bad IP reputation using OSSIM SIEM?
A threat hunter analyzing an infected endpoint finds that malicious processes keep reappearing even after termination, making traditional remediation ineffective. The user reports slowdowns, abnormal pop-ups, and unauthorized application launches. Deeper inspection reveals multiple scheduled tasks executing unknown scripts at intervals, along with suspicious registry modifications enabling automatic execution on startup. The endpoint makes intermittent encrypted outbound connections to an unclassified external server. The organization also observed multiple failed privileged logins from the same subnet. Which signs should the threat hunter look for to confirm and mitigate the threat?
Which of the following process refers to the discarding of the packets at the routing level without informing the source that the data did not reach its intended recipient?
Shawn is a security manager working at Lee Inc Solution. His organization wants to develop threat intelligent strategy plan. As a part of threat intelligent strategy plan, he suggested various components, such as threat intelligence requirement analysis, intelligence and collection planning, asset identification, threat reports, and intelligence buy-in.
Which one of the following components he should include in the above threat intelligent strategy plan to make it effective?
A SOC analyst monitoring authentication logs detects a sudden and significant spike in failed login attempts targeting multiple critical servers during non-business hours. These repeated authentication failures are abnormal compared to typical login activity. All attempts originate from a single external IP address, indicating a targeted attack rather than random scanning. Some login attempts use legitimate employee usernames, suggesting credential stuffing using previously compromised credentials or an ongoing brute-force attempt. Given this suspicious activity and its potential to escalate into unauthorized access, what is the appropriate next step in the threat-hunting process to assess the situation further?
What type of event is recorded when an application driver loads successfully in Windows?
You are working in a Cybersecurity Operations Center for PayOnline, which handles payment gateways for multiple applications. Your team monitors logs across firewalls, authentication servers, and endpoint detection tools. The team currently relies on manual log reviews, but the volume of raw, unstructured logs makes the process inefficient and error-prone. During a recent incident, the team struggled to extract relevant details from disorganized logs, delaying detection and response. The team decides to implement an automated log parsing solution that can transform unstructured logs into a structured format. Which log parsing technique should you implement to improve log data structuring and enable efficient querying and analysis?
The SOC team at a national cybersecurity agency detects anomalous network traffic from a sensitive government server and escalates to forensics. The forensic team discovers a trojan suspected of data exfiltration and persistence. The lead malware analyst must determine capabilities and persistence mechanisms by analyzing the trojan’s binary code at the instruction level without executing it. Which technique should the analyst use?
During routine monitoring, the SIEM detects an unusual spike in outbound data transfer from a critical database server. The typical outbound traffic for this server is around 5 MB/hour, but in the past 10 minutes, it has sent over 500 MB to an external IP address. No predefined signatures match this activity, but the SIEM raises an alert due to deviations from the server’s normal behavior profile. Which detection method is responsible for this alert?
According to the Risk Matrix table, what will be the risk level when the probability of an attack is very high, and the impact of that attack is major?
NOTE: It is mandatory to answer the question before proceeding to the next one.
Banter is a threat analyst in Christine Group of Industries. As a part ofthe job, he is currently formatting and structuring the raw data.
He is at which stage of the threat intelligence life cycle?
Rinni, SOC analyst, while monitoring IDS logs detected events shown in the figure below.
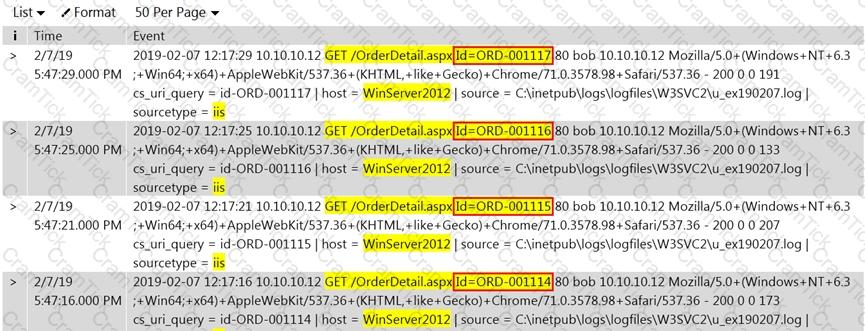
What does this event log indicate?
Which of the following formula is used to calculate the EPS of the organization?
Which of the following threat intelligence is used by a SIEM for supplying the analysts with context and "situational awareness" by using threat actor TTPs, malwarecampaigns, tools used by threat actors.
1.Strategic threat intelligence
2.Tactical threat intelligence
3.Operational threat intelligence
4.Technical threat intelligence
As a SOC Administrator at a mid-sized financial institution, you noticed intermittent network slowdowns and unexplained high memory usage across multiple critical systems. Your initial analysis found no traces of malware, but a forensic investigation revealed unauthorized scheduled tasks that executed during off-peak hours. These tasks ran obfuscated scripts that connected to an external command-and-control (C2) server. Further investigations showed that the adversary had gained access months ago through a compromised VPN account, leveraging stolen credentials from a phishing campaign. Which phase of the Advanced Persistent Threat (APT) lifecycle does this scenario align with?
The SOC team is tasked with enhancing the security of an organization's network infrastructure. The organization's public-facing web servers, which handle customer transactions, need to be isolated from the internal private network containing sensitive employee data and proprietary systems. The goal is to create a buffer zone that limits exposure of internal systems if the web servers are compromised during a cyberattack, such as a DDoS or SQL injection attempt. As a SOC analyst, which network architecture component would you recommend implementing to establish this isolated region?
A rapidly growing e-commerce company wants to implement a SIEM solution to improve its security posture and comply with PCI DSS requirements. They need a solution that offers both the necessary technological features and the expertise to manage the system effectively. They also need continuous compliance support and data security assistance. Which SIEM solution is appropriate for this company?
ABC is a multinational company with multiple offices across the globe, and you are working as an L2 SOC analyst. You are implementing a centralized logging solution to enhance security monitoring. You must ensure that log messages from routers, firewalls, and servers across multiple remote offices are efficiently collected and forwarded to a central syslog server. To streamline this process, an intermediate component is deployed to receive log messages from different devices and forward them to the main syslog server. Which component in the syslog infrastructure performs this function?
In which of the following incident handling and response stages, the root cause of the incident must be found from the forensic results?


