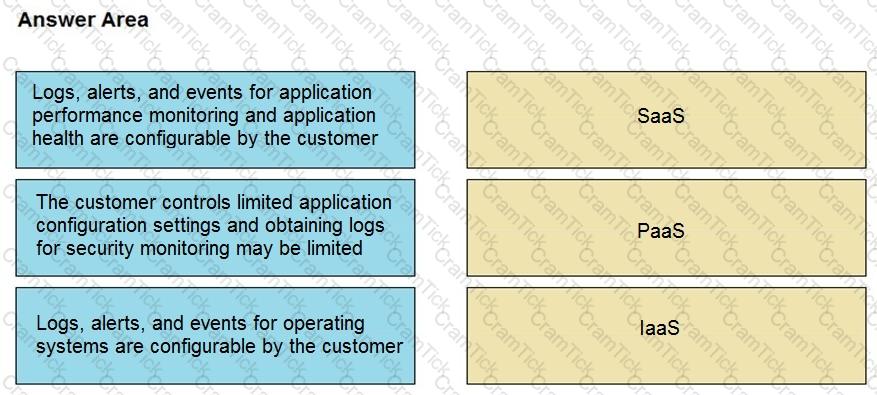
Drag and drop the telemetry-related considerations from the left onto their cloud service models on the right.
Employees receive an email from an executive within the organization that summarizes a recent security breach and requests that employees verify their credentials through a provided link. Several employees report the email as suspicious, and a security analyst is investigating the reports. Which two steps should the analyst take to begin this investigation? (Choose two.)
Refer to the exhibit.
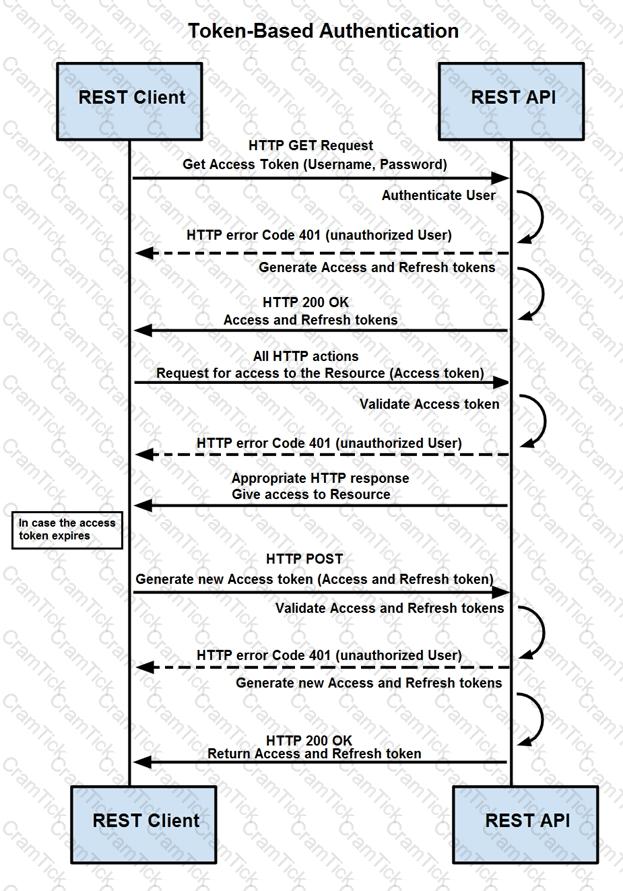
How are tokens authenticated when the REST API on a device is accessed from a REST API client?
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
A SOC analyst detected a ransomware outbreak in the organization coming from a malicious email attachment. Affected parties are notified, and the incident response team is assigned to the case. According to the NIST incident response handbook, what is the next step in handling the incident?
An engineer is analyzing a possible compromise that happened a week ago when the company? (Choose two.)
Refer to the exhibit.
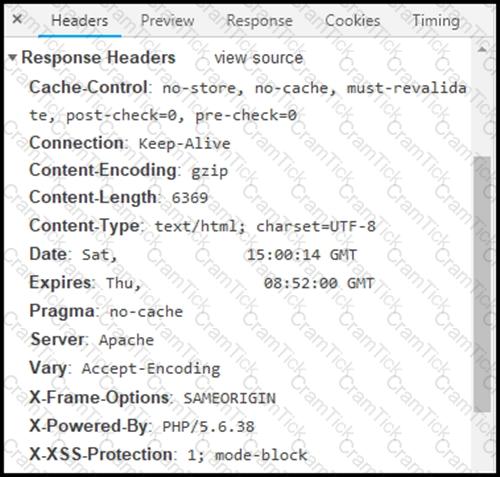
Where are the browser page rendering permissions displayed?