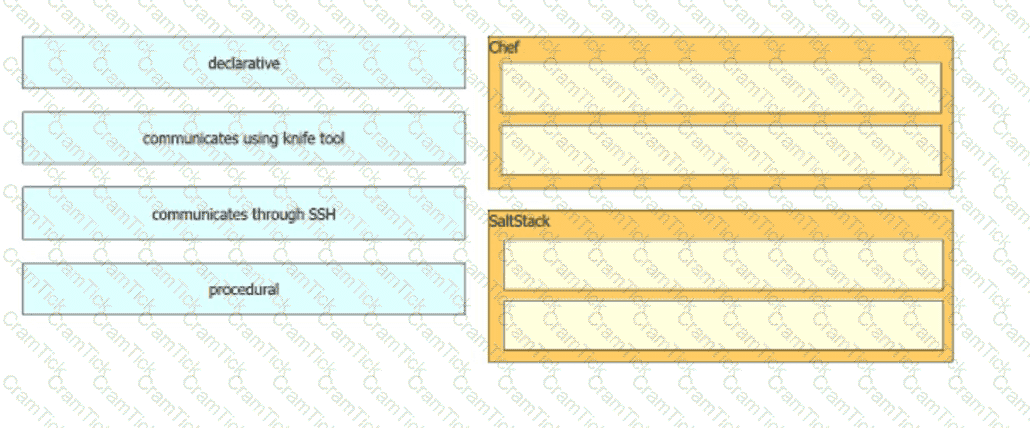
Drag and drop the characteristics from the left into the orchestration tools that they describe on the right.
Refer to the exhibit. A customer reports occasional brief audio dropouts on its Cisco Wi-Fi phones. The environment consists of a Cisco Catalyst 9800 Series WLC with Catalyst 9120 APs running RRM. The phones connect on the 5-GHz band. Which action resolves this issue?
Which RF value represents the decline of the RF signal amplitude over a given distance"?
On which protocol or technology is the fabric data plane based in Cisco SD-Access fabric?
Which tool functions in a push model, supports languages like Python or Ruby, and does not require an agent to be installed per host?
Which two actions are recommended as security best practices to protect REST API? (Choose two.)
Ascriptcontainsthe statement white loop != 999 ’ Which value terminates the loop?
Which language defines the structure or modelling of data for NETCONF and RESTCONF?

Refer to the exhibit. What is the value of the variable list after the code is run?
Drag anti drop the characteristics from the ten onto the configuration models on the right.
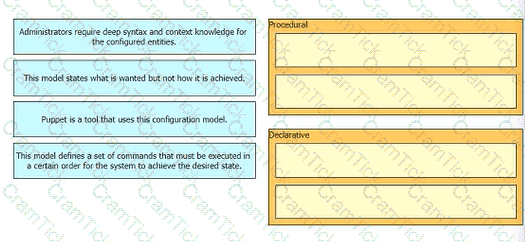
Exhibit.

Security policy requires all idle-exec sessions to be terminated in 600 seconds. Which configuration achieves this goal?
An engineer must configure a new WLAN that supports 802.11r and requires users to enter a passphrase. What must be configured to support this requirement?
Which feature allows HSRP to failover from the active route processor to the standby route processor without loss of data or path change?
Which feature is offered by the Cisco Advanced Malware Protection for Endpoints solution?
What is one characteristic of an AP that is operating in Mobility Express mode?

Refer to the exibit. How should the programmer access the list of VLANs that are recevied via the API call?
When a wireless client roams between two different wireless controllers, a network connectivity outage is experience for a period of time. Which configuration issue would cause this problem?
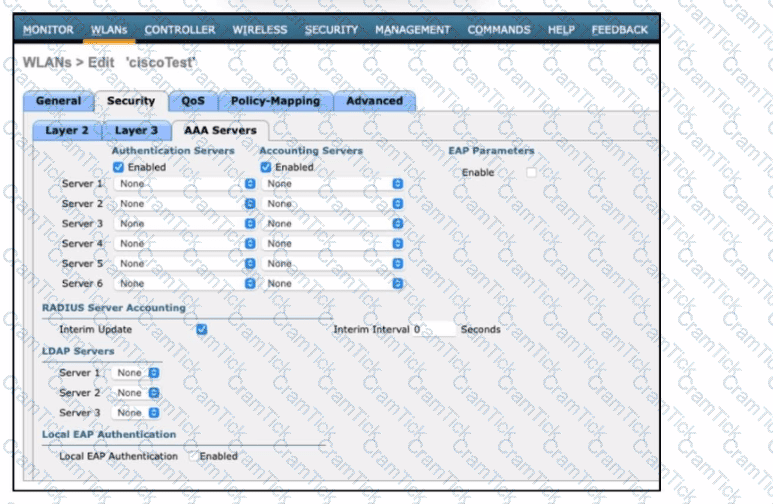
Refer to the exhibit. An engineer must configure a Cisco WLC with WPA2 Enterprise mode and avoid global server lists. Which action is required?
Which two nodes comprise a collapsed core in a two-tier Cisco SD-Access design? (Choose two.)
CCNP Enterprise | 350-401 Written Exam | 350-401 Questions Answers | 350-401 Test Prep | 350-401 CCNP Enterprise Actual Questions | Implementing Cisco Enterprise Network Core Technologies (ENCOR) Exam Questions PDF | 350-401 Online Exam | 350-401 Practice Test | 350-401 PDF | 350-401 CCNP Enterprise Dumps | 350-401 Test Questions | 350-401 Study Material | 350-401 Exam Preparation | 350-401 Valid Dumps | 350-401 Real Questions | 350-401 CCNP Enterprise Practice Test | CCNP Enterprise 350-401 Dumps | Implementing Cisco Enterprise Network Core Technologies (ENCOR) Exam Questions


