Refer to the exhibit. A growing company with an increasing international presence requires a secure and scalable solution for inter-office data transfer across their geographically dispersed locations. To ensure departmental privacy, the network must enforce granular access control. BGP is running in the network, and two VRF instances with unique route distinguishers and route targets have been configured to segregate critical financial data from regular network traffic. A network engineer with an employee ID: 5086:72:617 must find a solution that allows for future network expansion while maintaining robust security and data privacy between departments. The solution must comply with the RFC 4364 standard. Which action must the engineer take to meet the requirements?
Refer to the exhibit.
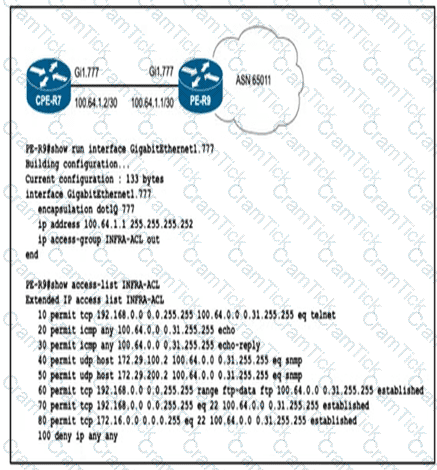
To protect in-band management access to CPE-R7, an engineer wants to allow only SSH management and provisioning traffic from management network 192.168.0.0/16. Which infrastructure ACL change must be applied to router PE-R9 to complete this task?
A)

B)
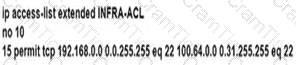
C)
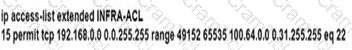
D)

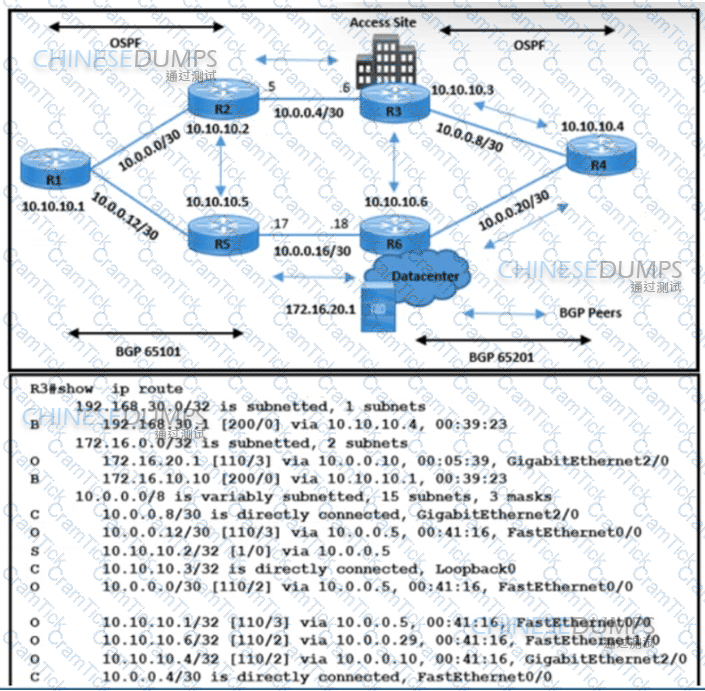
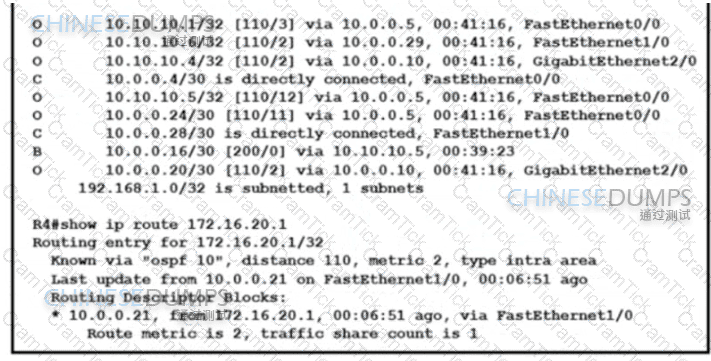
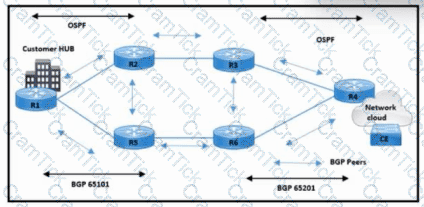
Refer to the exhibit. The network operations team reported that the access site that is connected to R3 is not connecting to the application server in the data center and that all packets that are sent from the application server to the access site are dropped. The team verified that OSPF and BGP peerings are up in BGP AS 65101 and BGP AS 65201. R4 is expected to receive traffic from the application server route via OSPF. Which action resolves this issue?
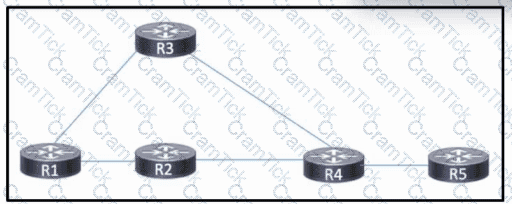
Refer to the exhibit. OSPF is running in the core, with MPLS configured on all links. A Cisco MPLS TE tunnel is configured with R1 as the headend and R4 as the tail-end router. As traffic on the network increases, the network engineering team is concerned about identifying failures between the tunnel endpoints.
Which action should the engineering team take that will allow them to identify and locate any faults in the path?
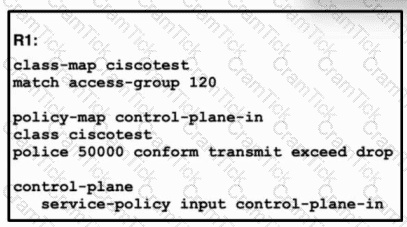
Refer to the exhibit. A network engineer installed router R1 as the new core router and must secure the control plane. The configuration has been applied, and now the engineer is creating ACL 120. Only hosts 192.168.1.1 and 192.168.2.2 should be allowed to access the router using Telnet. All other hosts should be rate-limited, with excess traffic dropped. Which configuration accomplishes this goal?
Refer To the exhibit:

On R1, which output does the show isis neighbors command generate?
A)

B)

C)
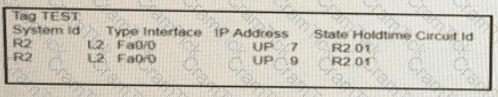
D)

Refer to the exhibit.

An engineer is securing a customer's network. Which command completes this configuration and the engineer must use to prevent a DoS attack?
Refer to the exhibit.
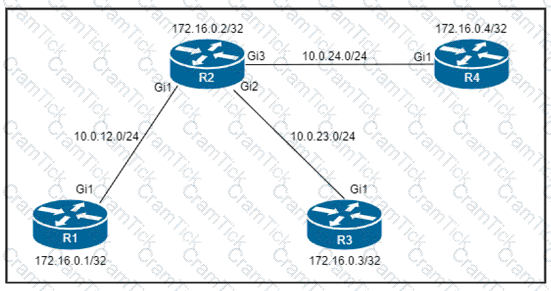
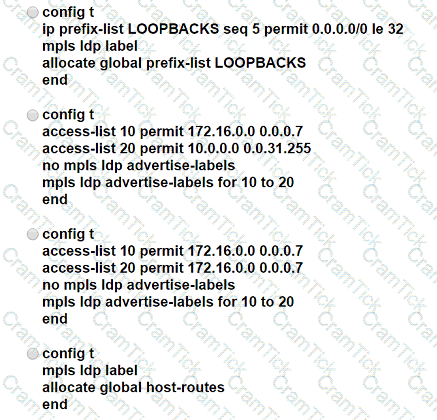
Which configuration must be applied to each of the four routers on the network to reduce LDP LIB size and advertise label bindings for the /32 loopback IP space only?
Which control plane protocol is used between Cisco SD-WAN routers and vSmart controllers?
Refer to the exhibit.
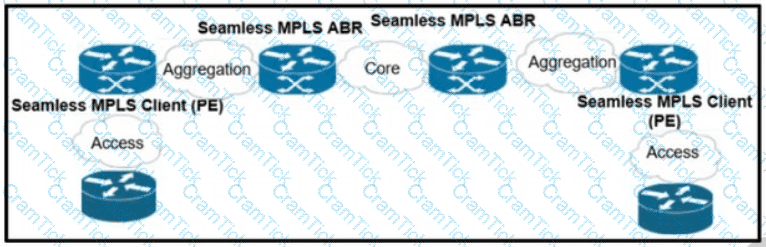
A network operator working for a telecommunication company with an employee 3994:37:650 is implementing a cisco Unified MPLS solution. What is the effect of this implementation?
What are two factors to consider when implementing NSR High Availability on an MPLS PE router? (Choose two.)
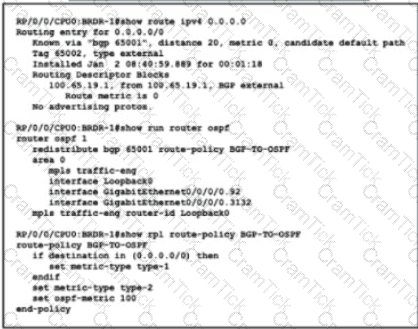
Refer to the exhibit. Router BRDR-1 is configured to receive the 0.0.0.0/0 and 172.17.1.0/24 network via BGP and advertise then into OSPF area 0. An engineer has noticed that the OSPF domain is receiving only the 172.17.1.0/24 route and default router 0.0.0.0/0 is still missing. Which configuration must an engineer apply to resolve this problem?

Option A
Option B
Option C
Refer to the exhibit. The enterprise is running BGP between sites to provide connectivity to users across the company's geographic regions. A network engineer must update the configuration so that the operations team can confirm that BGP prefixes that are received on each router originated from the correct autonomous system.
Which configuration must the engineer apply?
A network team has failed to implement IS-IS multitopology. What is the reason for it?
Refer to the exhibit.
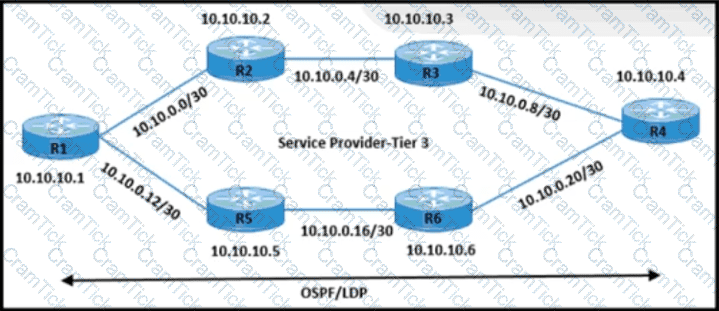
The network engineer is performing end-to-end MPLS path testing with these conditions:
• Users must perform MPLS OAM for all available same-cost paths from R1 to R4.
• Traceroute operations must return all of the next-hop IP details.
Which configuration meets these requirements?
An engineer working for a telecommunication company with an employee ID: 4460:35:466 must configure an OSPF router in a multivendor network so that it performs NSF in the event of a route processor switchover. Which configuration must the engineer apply?
An engineer working for a private service provider with employee id: 3994 37 650 is configuring a Cisco device to redistribute OSPF into BGP. Which task enables the device to filter routes?
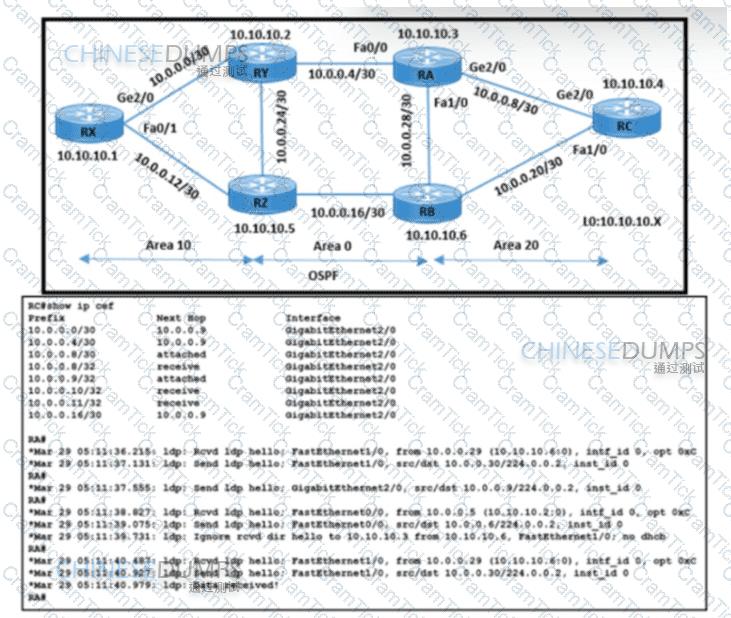
Refer to the exhibit. The operations team is implementing an LDP-based configuration in the service-provider core network with these requirements:
RC must establish LDP peering with the loopback IP address as its Router ID
RA must establish LDP peering with RB. RC, and RY.
How must the team update the network configuration to successfully enable LDP peering between RA and RC?
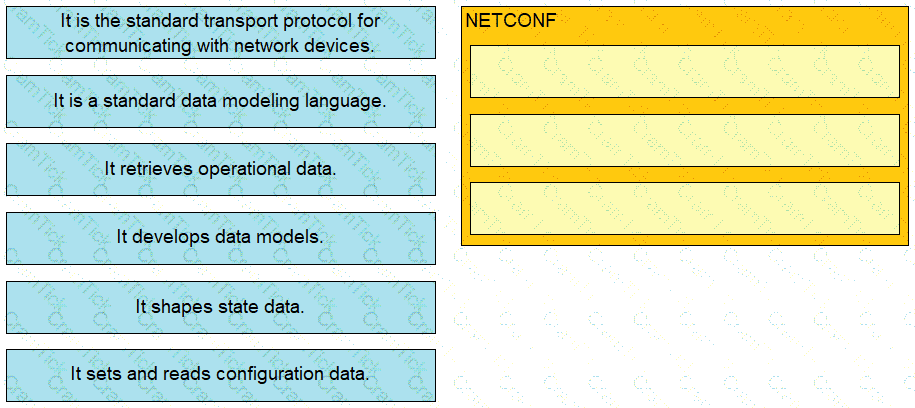
A network engineer is testing an automation platform that interacts with Cisco networking devices via NETCONF over SSH. In accordance with internal security requirements:
NETCONF sessions are permitted only from trusted sources in the 172.16.20.0/24 subnet.
CLI SSH access is permitted from any source.
Which configuration must the engineer apply on R1?
Refer to the exhibit.
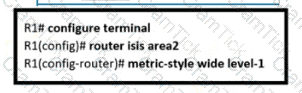
An engineer is configuring multitopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to the router to complete the task?

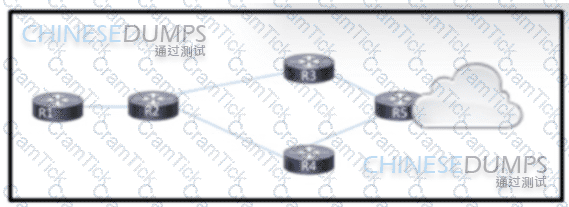
Refer to the exhibit. An engineer is scripting ACLs to handle traffic on the given network. The engineer must block users on the network between R1 and R2 from leaving the network through R5. but these users must still be able to access all resources within the administrative domain. How must the engineer implement the ACL configuration?
A network engineer must configure a router for Flexible NetFlow IPFIX export. The IP address of the destination server is 172.17.12.1. The source address must be set to the Loopback0 IPv4 address and exported packets must be set to DSCP CS3. The TTL must be 64 and the transport protocol must be set to UDP with destination port 4739. Which configuration must the engineer apply to the router?
How do intent APIs make it easier for network engineers to deploy and manage networks?

Refer to the exhibit.

A network engineer must implement SNMPv3 on a Cisco IOS XR router running BGP. The engineer configures SNMPv3 to use SHA for authentication and AES for privacy on the routers, which are in a different data center in the same exchange as other routers. The engineer must also verify the associated MIB view family name, storage type, and status. Which set of actions meets these requirements?
Refer to the exhibit:
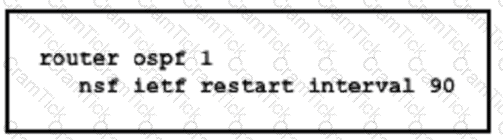
Which purpose of implementing NSF with this configuration is true?
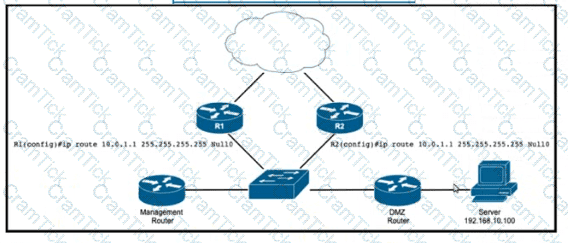

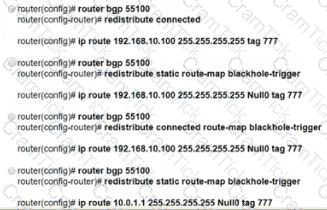
Refer to the exhibit. EIGRP a running across the core lo exchange Internal routes, and each router maintains 6GP adjacency with the other routers on the network. An operator has configured static routes on the edge routers R1 and R2 for IP address 10.0.1.1. which is used as a black hole route as shown. Which configuration should the operator Implement to me management rouler to create a route map that will redistribute lagged static routes into BGP and create a static route to blackhole traffic with tag 777 that Is destined to server at 192.168.10.100?
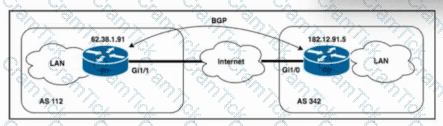
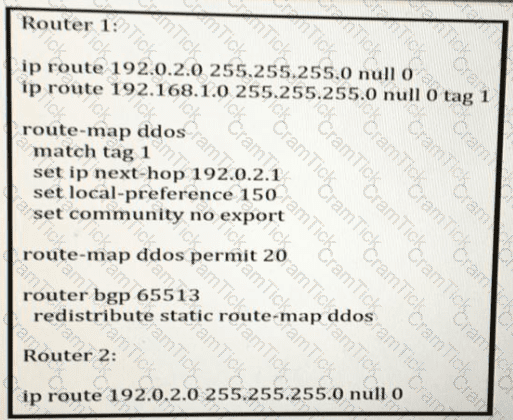
Refer to the exhibit. Routers R1 and R2 are connected over the internet, with the connection passing over four different autonomous systems. The company must mitigate potential DDoS attacks and protect the CPUs of the routers. A network engineer must secure all external connections on edge router R1 based on RFC 5082. R2 has already been secured. Which task should the engineer perform on R1 to achieve the goal?

Refer to the exhibit. A network operator working for a private telecommunication company with an employee id: 7138: 13:414 just added new users to the network, which resides in VLANs connected to routers R1 and R4. The engineer now must configure the network so that routers R1 and R4 share routes to the VLANs, but routers R2 and R3 are prevented from including the routes in their routing tables. Which configuration must the engineer apply to R4 to begin implementing the request?
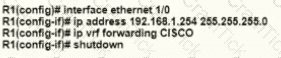
A network engineer is deploying VRF on ASBR router R1. The interface must have connectivity over an MPLS VPN inter-AS Option AB network. Which configuration must the engineer apply on the router to accomplish this task?
A)
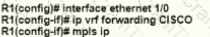
B)
C)

D)

Refer to the exhibit:
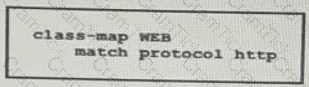
Which statement describes the effect of this configuration?
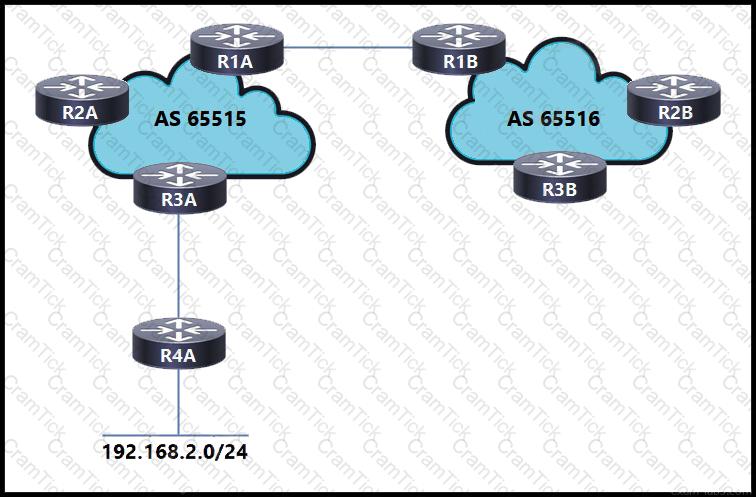
Refer to the exhibit. An engineer working for a private telecommunication company with an employee id: 3414:81:713 is implementing this network, in which:
Routers R1A and R1B are eBGP neighbors.
iBGP is configured within AS 65515 and AS 65516.
Network 192.168.2.0/24 is shared with AS 65516.
Router R3A has an iBGP relationship with router R2A only.
Router R2A has an iBGP relationship with routers R1A and R3A.
Which additional task must the engineer perform to complete the configuration?
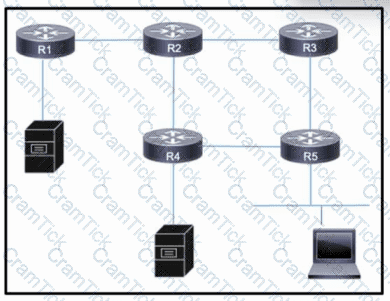
Refer to the exhibit. Users on a LAN connected to router R5 frequently open high-traffic connections with servers connected to R1 and R4. Users on R2 also require access to the servers, but performance is not a major concern and their traffic can be treated as secondary. As traffic on all links grows, the network architect wants to mitigate the potential for congestion on the link between R2 and R4.
Which action must the engineering team take to improve performance on the R2-R4 link for users on R5 while still allowing other traffic to flow?
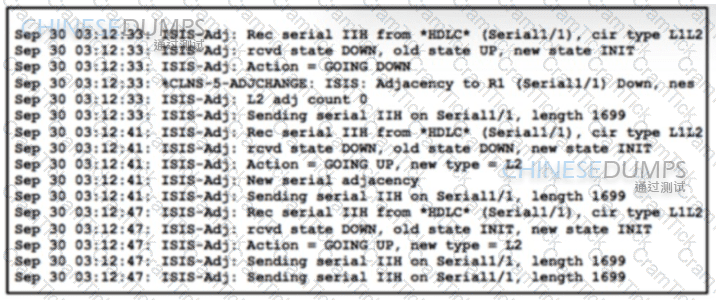
Refer to the exhibit Routers R1 and R2 are connected via a señal link and use the IS-IS routing protocol for route exchange After a configuration change on R2. IS-IS connectivity is interrupted A network engineer confirmed that the interfaces are in the UP state and connectivity exists between the two routers. Which two actions must the engineer perform to resolve the problem? (Choose two.)
An engineer needs to implement QOS mechanism on customer's network as some applications going over the internet are slower than others are. Which two actions must the engineer perform when implementing traffic shaping on the network in order to accomplish this task? (Choose two)
An engineer is implementing IGMP with SSM on a multicampus network that supports video streaming. Which task must the engineer perform as part of the process?

Guidelines
-
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology
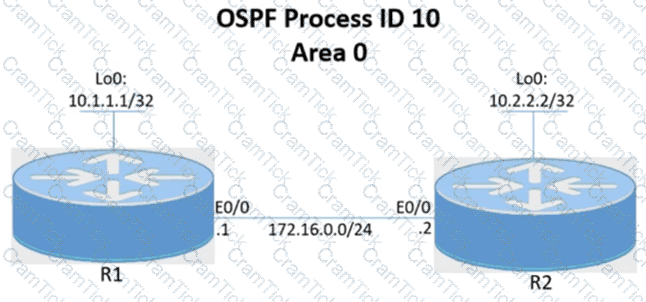
Tasks
-
Configure and verify the OSPF neighbor adjacency between R1 and R2 in OSPF area 0 according to the topology to achieve these goals:
1. Establish R1 and R2 OSPF adjacency. All interfaces must be advertised in OSPF by using the OSPF interface command method. Use Loopback0 as the OSPF ID.
2. There must be no DR/BDR elections in OSPF Area 0 when establishing the neighbor relationship between R1 and R2. OSPF must not generate the host entries /32 for the adjacent interfaces.
3. Enable OSPF MD5 Authentication between both routers at the interface level with password C1sc0!.
Refer to the exhibit.
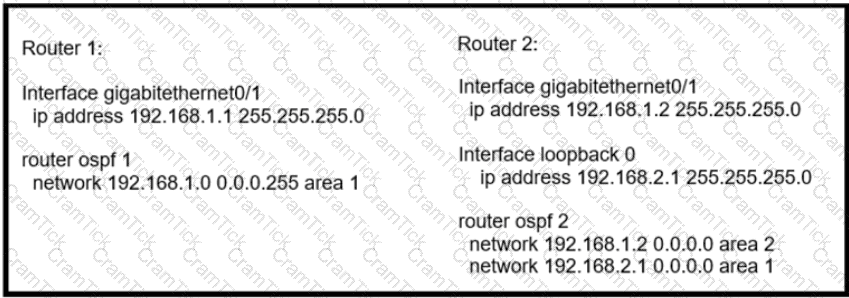
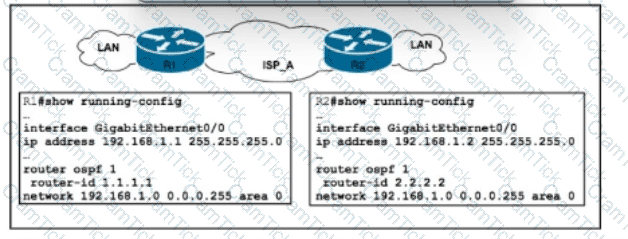
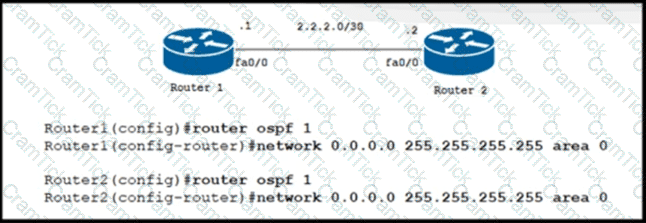
Router 1 is missing the route for the router 2 loopback 0. What should the engineer change to fix the problem?
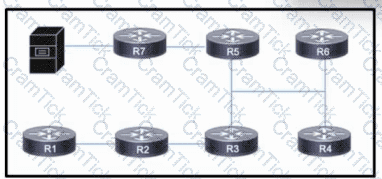
Refer to the exhibit. The network is configured with OSPF. A networking team just connected a streaming multicast server to router R7, and they now must enable access for users throughout the network to stream video from the server.
Which action must the team take so that users can stream video without overloading the network?
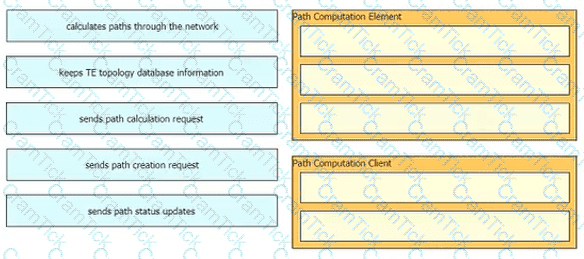
Drag and drop the functions from the path computation element protocol roles on the right.
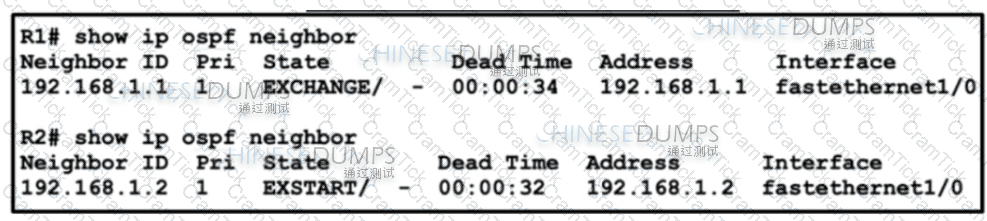
Refer to the exhibit. A company recently deployed a new network using OSPF in the core to share routes. The network administrator selected OSPF as the routing protocol because of its ability to maintain a route database. When the new network was started up, all routers booted normally, but the link between routers R1 and R2 failed to come up. The two routers are located in the same rack at the data center. Which task should an engineer perform to correct the problem?
Refer to the exhibit.
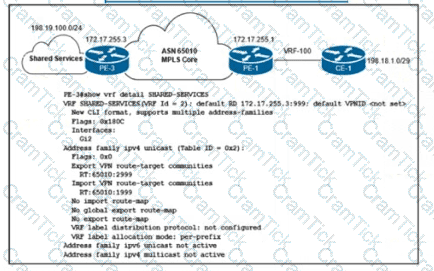
Refer to the exhibit. An ISP provides shared VoIP Extranet services to a customer in VRF-100 with these settings:
The VoIP services are hosted in the 198.19.100.0/24 space.
The customer has been assigned the 198.18.1.0/29 IP address block.
VRF-100 is assigned import and export route target 65010:100.
Which configuration must the engineer apply to PE-1 to provision VRF-100 and provide access to the shared services?
How does Inter-AS Option-A function when two PE routers in different autonomous systems are directly connected?
A network administrator must monitor network usage to provide optimal performance to the network end users when the network is under heavy load. The administrator asked the engineer to install a new server to receive SNMP traps at destination 192.168.1.2. Which configuration must the engineer apply so that all traps are sent to the new server?
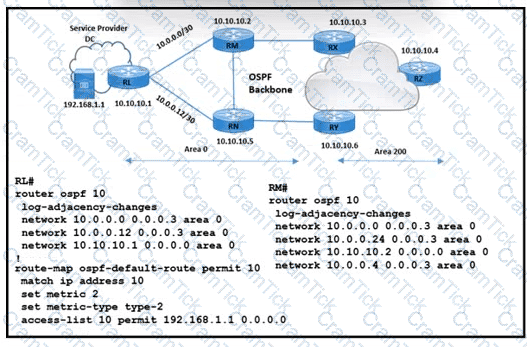
Refer to the exhibit. The operations team for a service provider network is implementing a route map policy. OSPF area 0 should originate the default route with a type 2 metric of 2 when the application server on the connected interface (192.168.1.1) is up. Routers RL and RM have set up OSPF peering with other adjacent routers. Which action meets this requirement?
Refer to the exhibit:

P3 and PE4 are at the edge of the service provider core and serve as ABR routers Aggregation areas are on either side of the core.
Which statement about the architecture is true?
Exhibit:
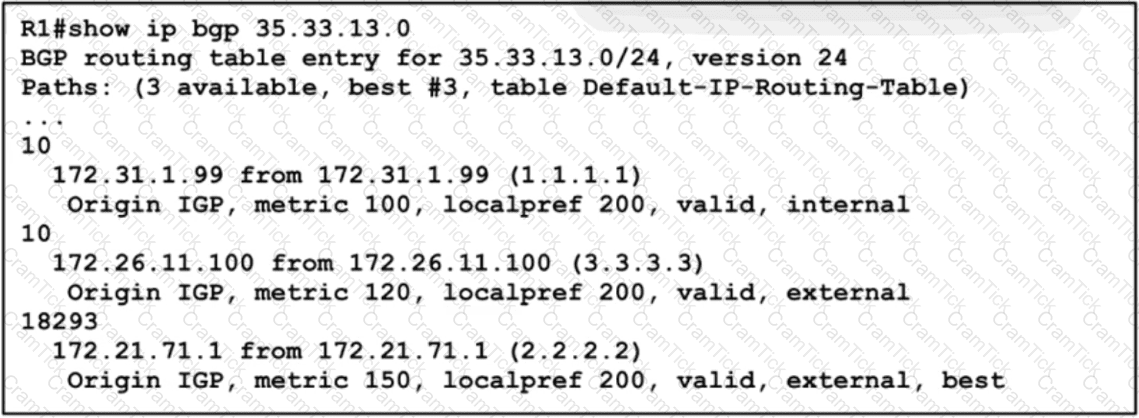
A network engineer must update the routing toward the web server with IP address 35.22.13.1. The primary path must be configured via the neighbor router with ID 1.1.1.1. However, local-preference configuration is not permitted on R1. Which task must the engineer perform on R1 to complete the implementation?
A network architect must implement CSC VPN services for a new backbone carrier. Which two benefits does the architecture provide? (Choose two.)
Refer to the exhibit.
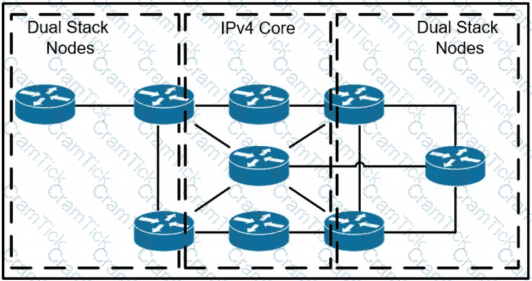
A network operator has two IPv4 and IPv6 dual-stacked network on each side of the IPv4 core network. The operator must be able to provide connectivity between them while using specific assigned IPv6 space provided from the company IP administrator team. Which technology should the network operator use to accomplish this goal?
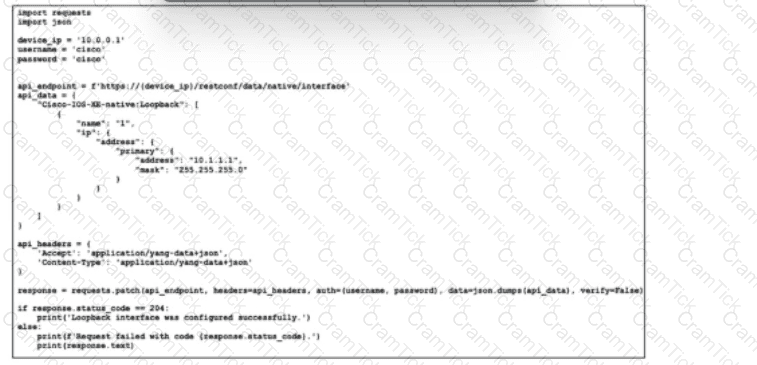
Refer to the exhibit. An operations team recently located an archive of scripts for deploying routine network changes with an error-free approach. A junior network engineer, who is working to modify the scripts to support RESTCONF, has been asked to document the purpose of each updated script. Which two actions does the given script take? (Choose two.)
Why is the keyword none needed when implementing management plane security using TACACS?
Refer to the exhibit:

R1 and R2 are directly connected with Fast Ethernet interfaces and have the above configuration applied OSPF adjacency is not formed. When the debug ip ospf hello command is issued on R1. these log messages are seen.

Which command can be configured on routers R1 and R2 on fO/O interfaces to form OSPF adjacency?

Guidelines
-
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology
Tasks
-
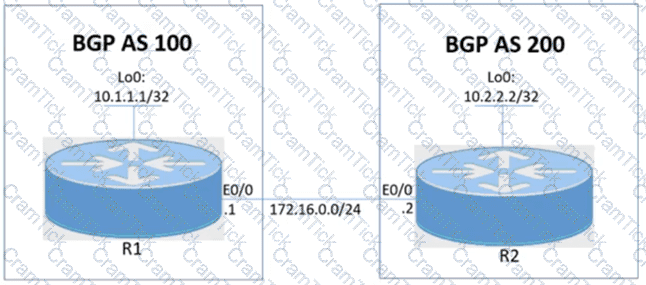
R1 and R2 are having issues forming an eBGP neighbor relationship. Troubleshoot and resolve the issue to achieve these goals:
1. Configure R1 and R2 to form a BGP neighborship using their Loopback interfaces.
2. Form the neighbor relationship using a BGP multihop mechanism. Use minimal values to solve the issue.
A network engineer must enable the helper router to terminate the OSPF graceful restart process if it detects any changes in the LSA. Which command enables this feature?
An engineer is developing a configuration script to enable dial-out telemetry streams using gRPC on several new devices. TLS must be disabled on the devices. Which configuration must the engineer apply on the network?
A)
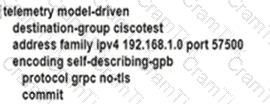
B)
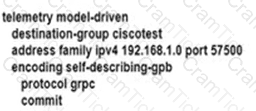
C)
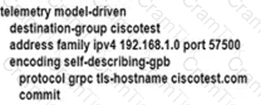
D)
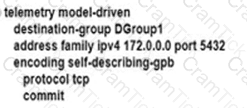
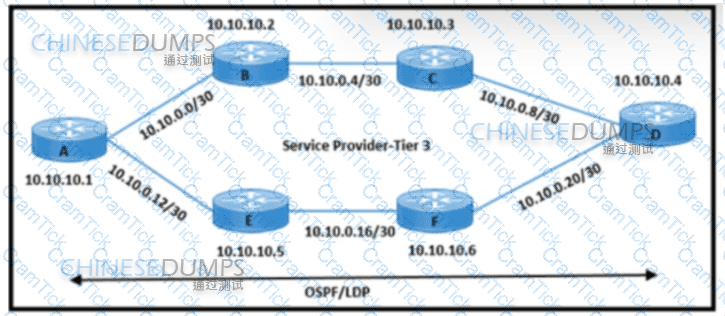
Refer to the exhibit. An engineering team must update the network configuration so that data traffic from router A to router D continues in case of a network outage between routers B and C. During a recent outage on the B-C link, the IGP traffic path was switched to the alternate path via routers E and F. but label forwarding did not occur on the new path. Which action ensures that traffic on the end-to-end path continues?
Refer to the exhibit:

This configuration is being applied on an IOS XR router.
Which statement about this configuration is true?
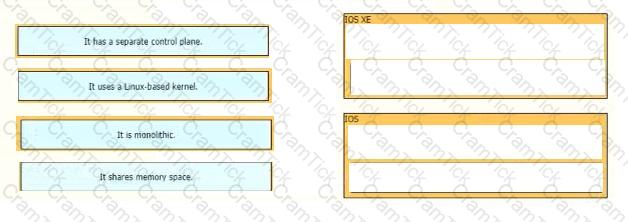
Drag and drop the descriptions from the left onto the corresponding OS types on the right.
An engineer is implementing a router redistribution within BGP. The route map must be configured to permit all unmatched routes. Which action must the engineer perform to complete this task?

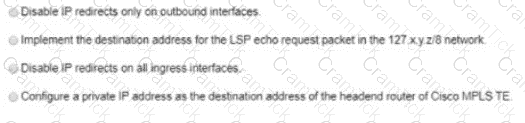
An engineer is implementing MPLS to monitor within the MPLS domain. Which must the engineer perform to prevent packets from being forwarded beyond the service provider domain when the LSP is down?
Refer to the exhibit.
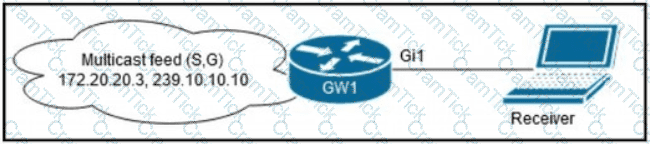
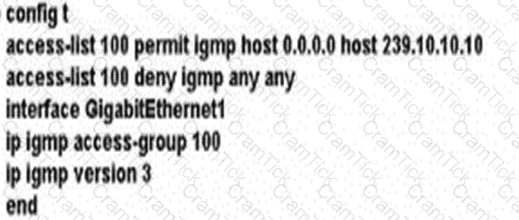
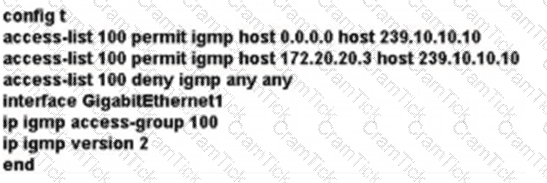
A network administrator is implementing IGMP to enable multicast feed transmission to the receiver. Which configuration must the administrator deploy on GW1 to permit IGMP Joins only to the assigned (S, G) feed?
A)
B)
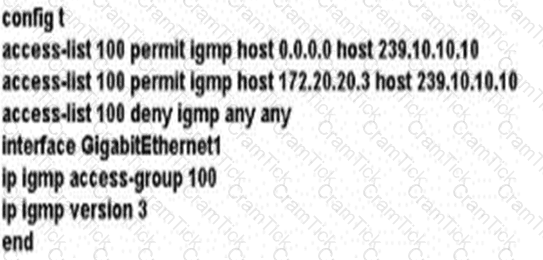
C)
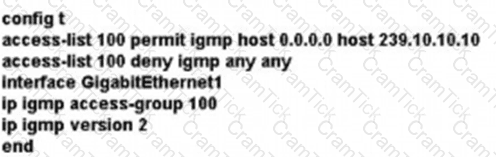
D)
A network operator needs to implement PIM-SSM multicast configuration on customer's network so that users in different domains are able to access and stream live traffic. Which two actions must the engineer perform on the network
to make the streaming work? (Choose two.)
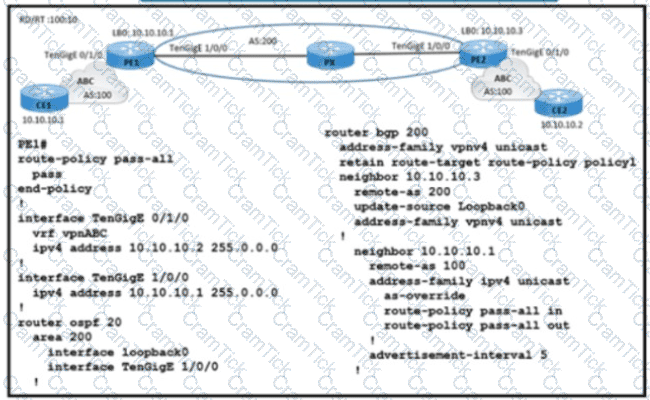
Refer to the exhibit. A service provider engineer Is configuring the connection between CE1 and CE2. AS 200 of the service provider and AS 100 of enterprise ABC should connect using BGP. The engineer already completed the configuration of VRF RT 100:10 of enterprise ABC. Which configuration must the engineer apply on PE1 to meet the requirement?
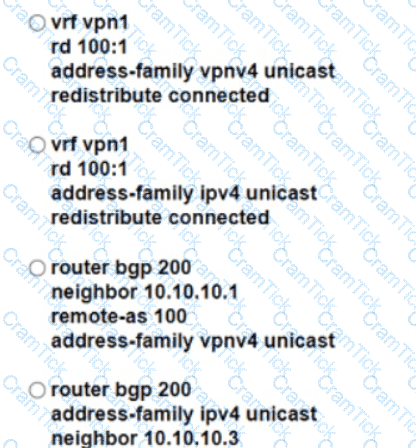
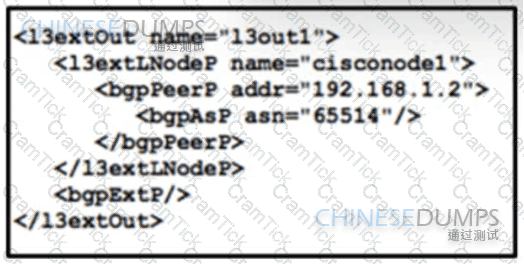
Refer to the exhibit. A global company plans to implement BGP at its newest location to provide connectivity to other offices. The global infrastructure of the company is a multivendor environment. An engineer must review the BGP core configurations at headquarters to determine if they can be repurposed at the new location. The engineer copied this JSON script for review. What is the effect of the script?
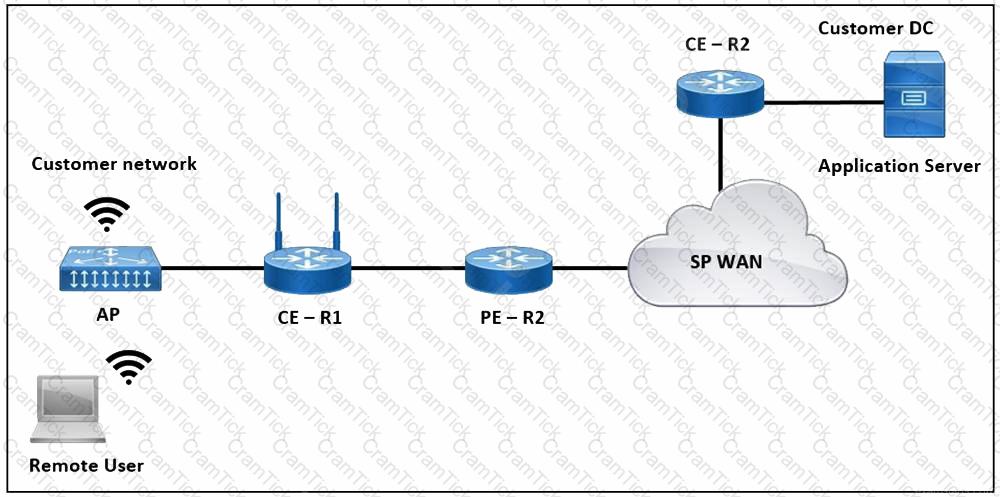
Refer to the exhibit. The application server in the data center hosts voice, video, and data applications over the internet. The data applications run more slowly than the voice and video applications. To ensure that all applications run smoothly, the service provider decided to implement a QoS policy on router PER 2 to apply traffic shaping. Which two actions must an engineer take to implement the task? (Choose two.)
Which additional configuration is required for NetFlow to provide traceback information?
Drag and drop the characteristics from the left onto the automation tool on the right.
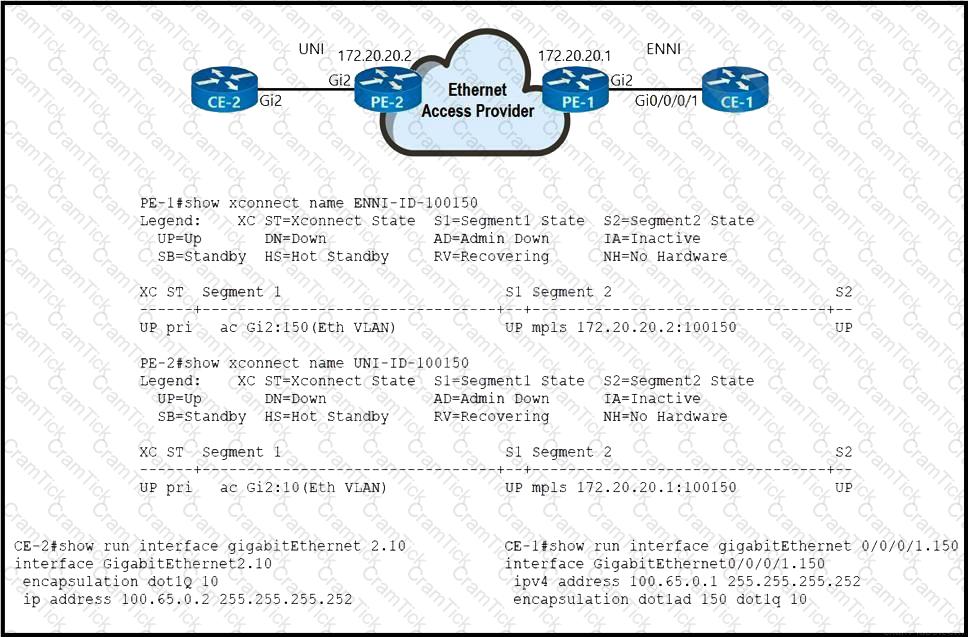
Refer to the exhibit. An Ethernet access provider is configuring routers PE-1 and PE-2 to provide E-Access EVPL service between UNI and ENNI. ENNI service multiplexing is based on 802.1ad tag 150, and service-multiplexed UNI is based on 802.1q tag 10. Which EFP configurations must the provider implement on PE-1 and PE-2 to establish end-to-end connectivity between CE-1 and CE-2?
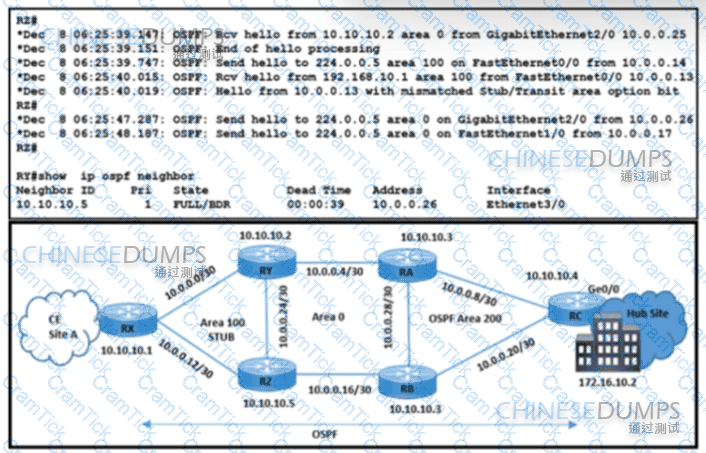
Refer to the exhibit. A network engineer received a complaint about these problems in OSPF stub area 100:
The Ethernet link is down between routers RX and RY because the fiber was cut.
CE site A traffic to the hub site is being dropped.
Which action resolves these issues?
Refer to the exhibit.
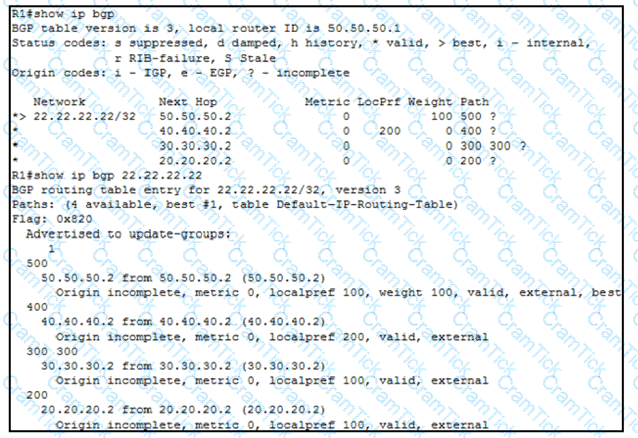
An engineer wants to determine which paths are best, second best, third best, and fourth best. Drag and drop the peer addresses on the left to the corresponding BGP best-path selection order on the right.
Refer to the exhibit. After a networking team configured this MPLS topology, the supervisor wants to view MPLS labels to verify the path that packets take from router R1 to router R7 The team already Issued an ICMP ping to verify connectivity between the devices. Which task must the team perform to allow the supervisor to view the label switch path?
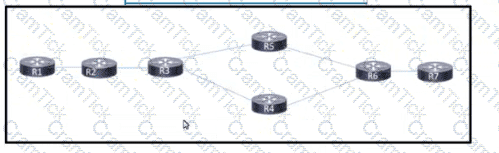
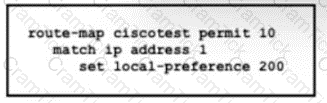
Refer to the exhibit. An engineer is implementing the BGP attribute on the customer's network to select the preferred path. Only BGP's well-known discretionary attribute must be used FTP prefixes should not be selected as part of this implementation. Which configuration must the engineer implement to complete the task?
Refer to the exhibit.
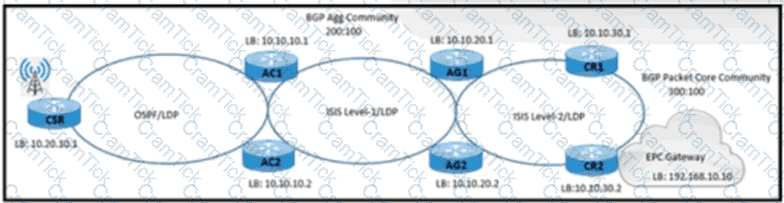
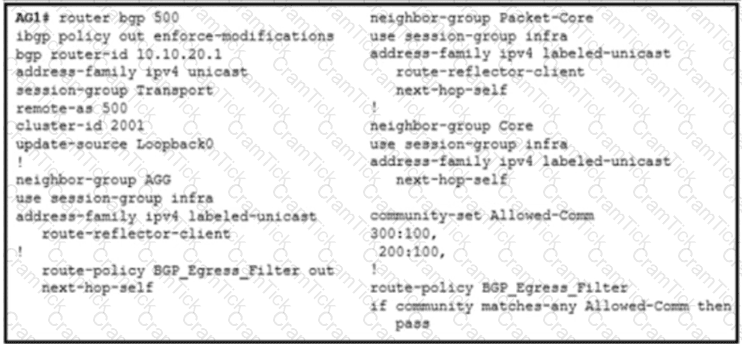
A NOC engineer is configuring label-based forwarding from CSR to the EPC gateway. Cell-site operation and maintenance for IPv4 traffic between 10.20.10.1 and 192.168.10.10 is already up. CR1 and CR2 are configured as route reflectors for AG1 and AG2. Which action completes the configuration?
Refer to the exhibit.
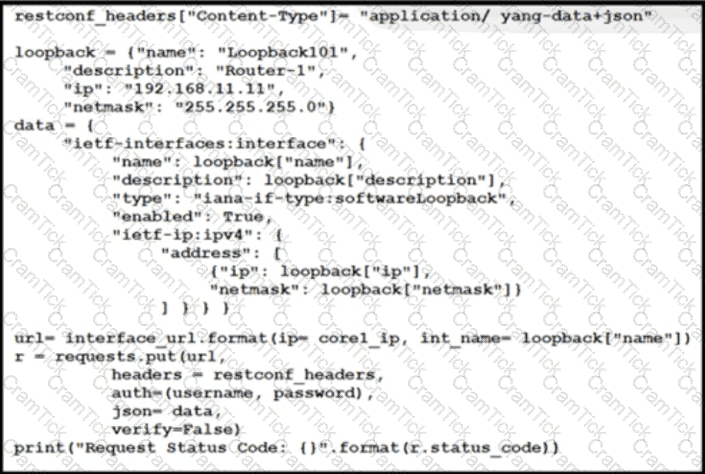
An engineer at a new ISP must configure many Cisco devices in the data center. To make the process more efficient, the engineer decides to automate the task with a REST API. Which action does this JSON script automate?
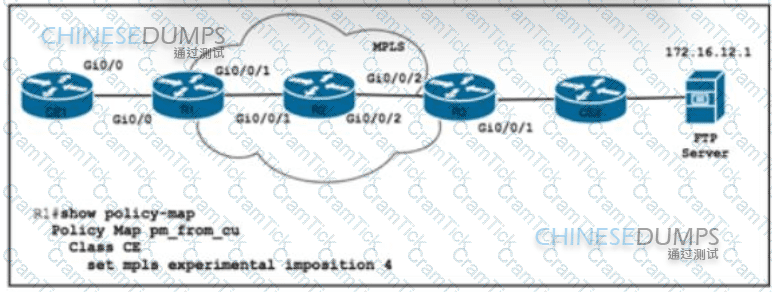
Refer to the exhibit. Router R1 is configured with class map CE with match Ip precedence critical to align with customer contract SLAs. The customer is sending all traffic from CE1 toward the FTP server with IP precedence 5 A network engineer must allow 10% of interface capacity on router R3 Which two actions must the engineer take to accomplish the task? (Choose two )
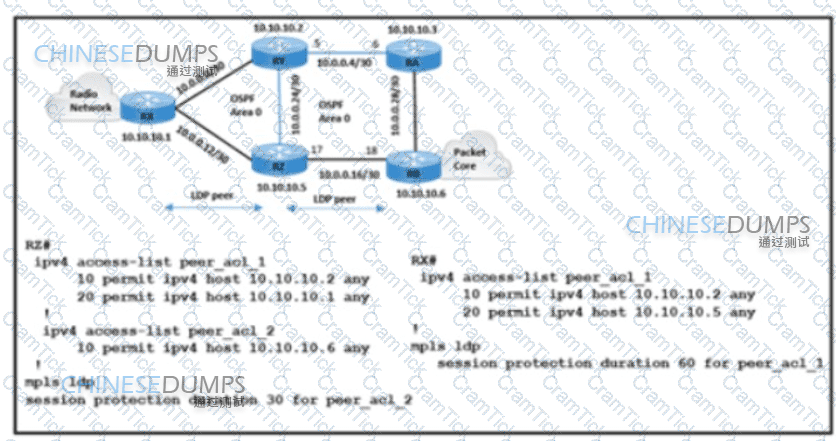
Refer to the exhibit. The radio network and packet core are using the route RX-RZ-RB to establish communication. The LDP session between 10.10.10.5 and 10.10.10.1 is experiencing link flapping at random intervals for 30-45 seconds each time. A network engineer must protect the LDP session and improve MPLS traffic convergence. Which action meets these requirements?
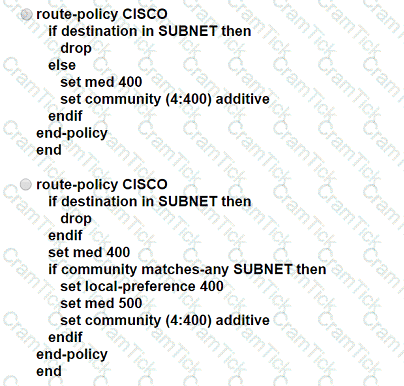
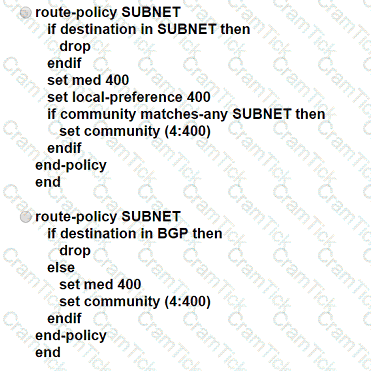
A network engineer is configuring a BGP route policy for the SUBNET prefix set. Matching traffic must be dropped, and other traffic must have its MED value set to 400 and community 4:400 added to the route. Which configuration must an engineer apply?
Which action occurs during the traceback phase of the six-phase approach to service provider security?
Refer to the exhibit.

A network engineer at a large ISP Is configuring telemetry streams to monitor the health status of PE routers on the network using gRPC dial-out. The PE routers are located at several data centers in different physical locations, and they are using IS-IS and BGP for routing. Which additional configuration must the engineer implement on the PE routers to meet the goal?
Refer to the exhibit:
An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
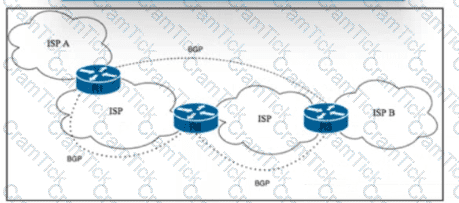
Refer to the exhibit. Tier 1 ISP A is connected to small Tier 3 ISP B. The EBGP routing protocol is used for route exchange. The networking team at ISP A noticed the flapping of BGP sessions with ISP B. The team decides to Improve stability on the network by suppressing the subnet for 30 minutes when a session begins to flap. Which action must the team perform to meet this goal?
A network engineer must enable multicast on the network to support a new series of webcasts. The PIM protocol has been enabled on the LAN side, with PIM and MSDP capabilities on edge router R1. The multicast source has been configured with IP address FF3A:121, and IP protocol 58 has been enabled and successfully tested in the network. Due to the limitations of some devices on the network, the data flow should take the most efficient path.
Which task must the engineer perform to achieve the goal?
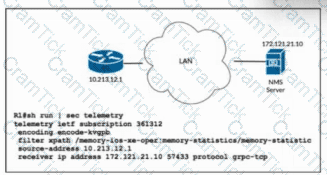
Refer to the exhibit. The network administrator is configuring memory telemetry on router R1. Only kvGPB encoding and gRPC protocol based on RFC 7540 should be used. Updates should be sent every two seconds. Which two commands must the administrator apply to complete the task? (Choose two.)
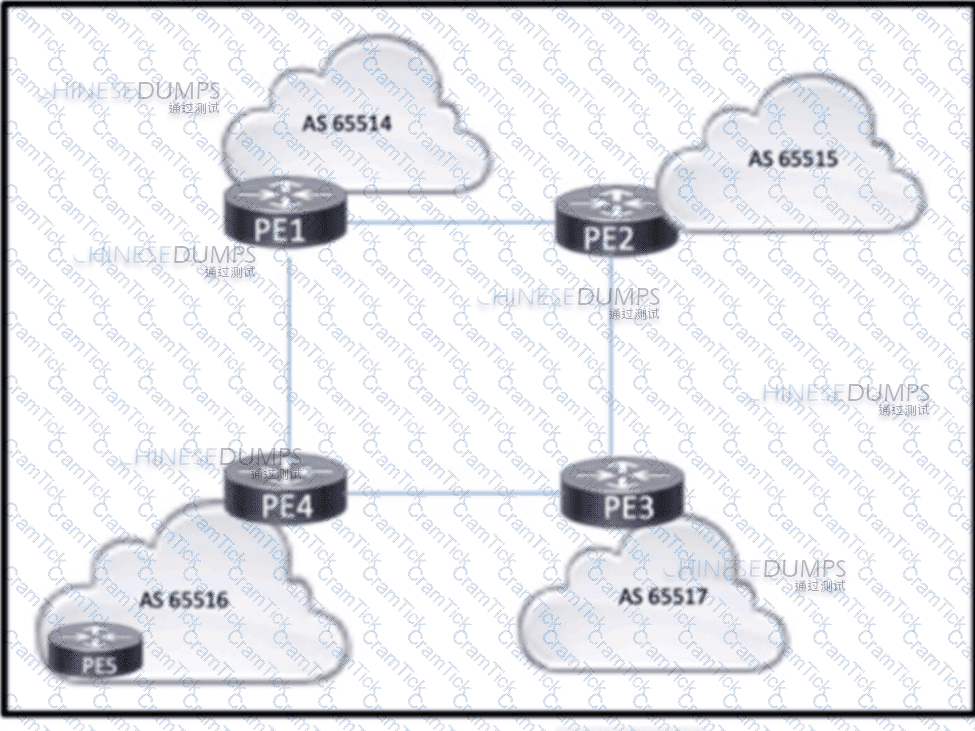
Refer to the exhibit. Four midsize service providers provide access to different customers that use Layer 3 VPN services to enable communication across geographic regions. The service providers are connected as shown in the exhibit, and the PEs have established eBGP relationships. PE4 has an IBGP relationship with PE5. The routes that PE4 learns from PE5 must reach the other PE routers, but they are absent from the routing tables on the other PES. Which action should the engineers take to correct the problem?
Refer to the exhibit:
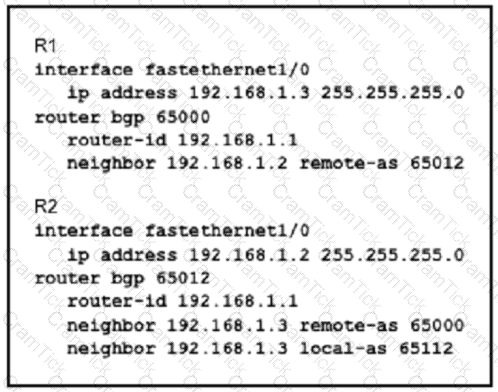
Assume all other configurations are correct and the network is otherwise operating normally. Which conclusion can you draw about the neighbor relationship between routers R1 and R2?
Refer to the exhibit:

Which command is used to complete this configuration for QoS class-based marking?
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS L3VPN services For which reason do you make this decision?
An ISP that provides private network services across the country has recently migrated their infrastructure to support MPLS technology. A network engineer configured mpls ip on all routers and implemented the OSPF routing protocol with TE extensions in the backbone area. The ISP wants to ensure that label exchange is performed only on MPLS-enabled interfaces that are associated with the IGP instance.
Which action must the engineer take to accomplish the goal?
Refer to the exhibit.
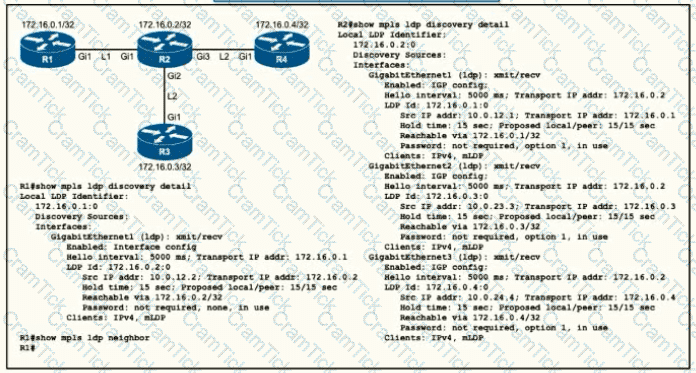
An engineer began to configure LDP between R1 and R2, but R1 and R2 cannot yet establish an LDP TCP connection. Which additional task must be completed to finish the implementation?
An organization with big data requirements is implementing NETCONF as part of its migration to a new cloud-based environment. The organization has multiple offices across widespread geography. A network engineer is configuring NETCONF on one of the border routers. Which configuration must the engineer apply to save the running configuration?
A company uses PIM-SM multicast with IGMPv2 to stream training videos from a server in one network to hosts in a different network. As the company has grown, the networking team decided to implement SSM to improve efficiency for multicast within Layer 2. Which action must the team take to begin the process?
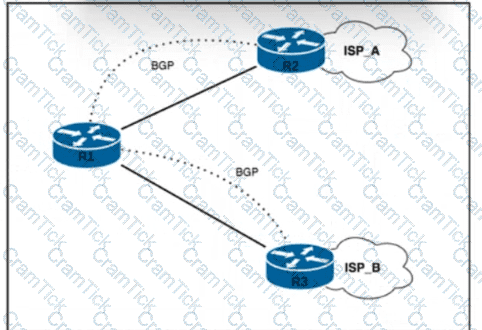
Refer to the exhibit. R1 has two upstream Tier 1 service providers. BGP is in use as the exterior routing protocol, and ISP_A and ISP_B are sending the full BGP table. A network engineer must assign local-preference 70 to all routes with multiple exit discriminator 30. Which configuration must the network engineer apply?

A company is expanding its existing office space to a new floor of the building, and the networking team is installing a new set of switches. The new switches are running IGMPv2, and the engineers configured them for VLAN10 only. The rest of the existing network includes numerous Layer 2 switches in multiple other VLANs, all running IGMPv3. Which additional task must the team perform when deploying the new switches so that traffic is switched correctly through the entire network?
Refer to the exhibit.
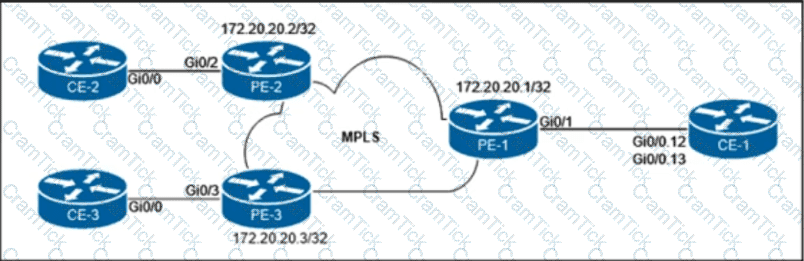
The customer that owns the CE-1, CE-2, and CE-3 routers purchased point-to-point E-Line services from the Carrier Ethernet provider. The service provider is delivering multiplexed UNI at the customer HQ location on PE-1 and untagged UNIs at the PE-2 and PE-3 locations. Additionally, the customer provided these VLAN to EVC mapping requirements:
• EVC 1 between CE-1 and CE-2 must be provisioned with C-VLAN 12 at the HQ location.
• EVC 2 between CE-1 and CE-3 must be provisioned with C-VLAN 13 at the HQ location.
Which configuration must the network engineer implement on the PE routers to provide end-to-end Carrier Ethernet service to the customer?
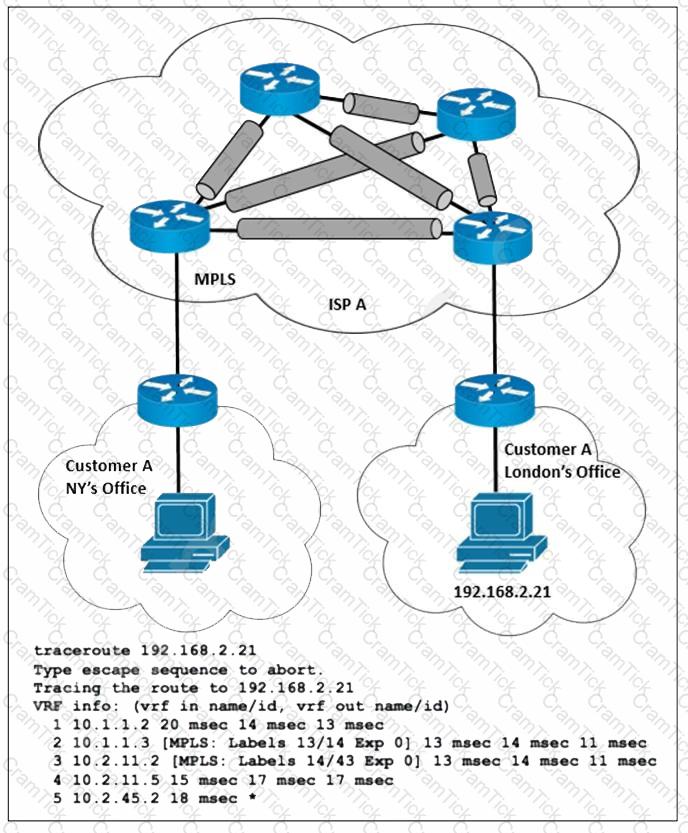
Refer to the exhibit. ISP A provides MPLS L3VPN service to customer A with BGP as the external routing protocol. Customer A has just opened a new branch office in London and requested the service provider to implement lossless service between its two offices. The LDP is enabled over the MPLS backbone and label exchange is working normally. Which action must the ISP engineering team take to enable the service?
An engineer is setting up overlapping VPNs to allow VRF ABC and XYZ to communicate with VRF CENTRAL but wants to make sure that VRF ABC and XYZ cannot communicate. Which configuration accomplishes these objectives?




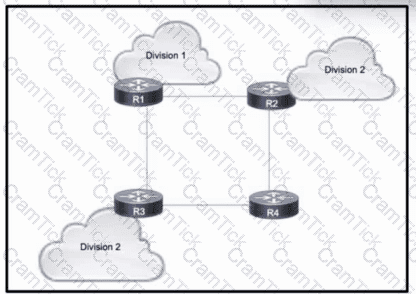
Refer to the exhibit. A large enterprise is migrating its network to use MPLS VPNs between different business divisions. Within the core, routes are shared between the routers using OSPF, and each connected link maintains an MPLS neighbor relationship.
Which action must the migration team take so that LDP neighbor relationships are maintained if a directly-connected link goes down?
Refer to the exhibit.
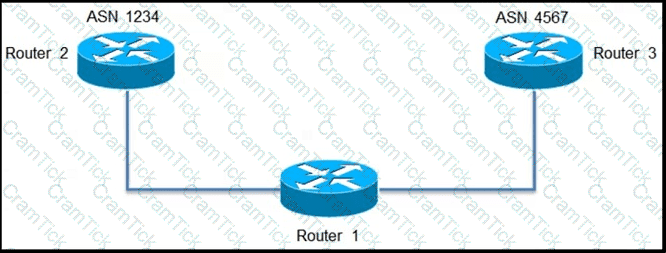
An engineer is configuring path selection on router R1 for two ASNs as shown. Which additional task must the engineer perform on Router 1 so that all outbound traffic utilizes the link between R1 and R3 to reach ASN 4567?
Which two features will be used when defining SR-TE explicit path hops if the devices are using IP unnumbered interfaces? (Choose two.)
What happens when a segment-routing TE tunnel loses the link and there is no secondary path in place?
Refer to the exhibit.
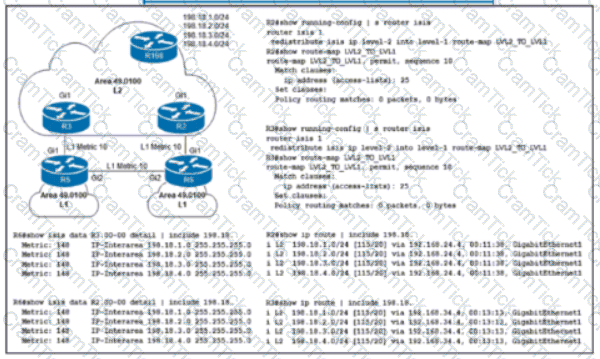
Routers R2 and R3 are Level 1/Level 2 IS-IS routers that redistribute 198 18.x.x/24 prefixes to routers R5 and R6 In the Level 1 area R2 Is to be the preferred router for all redistributed prefixes in the Level 1 area. Which configuration sets this preference?
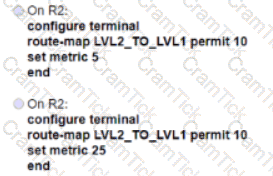
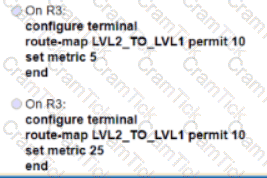
Refer to the exhibit.
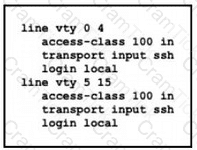
An engineer has started to configure a router for secure remote access as shown. All users who require network access need to be authenticated by the SSH Protocol.Which two actions must the engineer implement to complete the SSH configuration? (Choose two.)
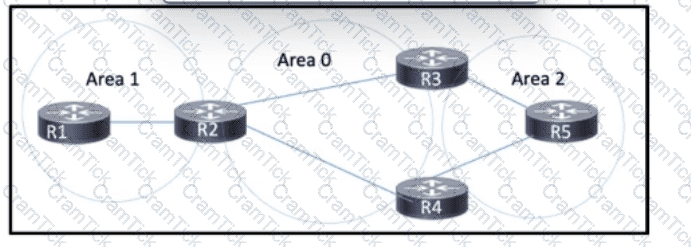
Refer to the exhibit. OSPF is running in the network, which is segmented into three areas. MPLS is enabled on all routers to support Layer 3 VPN. The network architect is concerned about potential packet loss when new OSPF adjacencies form. Which two tasks should the architect perform to implement MPLS LDP synchronization? (Choose two.)
Which CLI mode must be used to configure the BGP keychain in Cisco IOS XR software?
Refer to the exhibit:
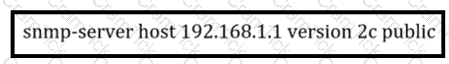
A network administrator wants to enhance the security for SNMP for this configuration.
Which action can the network administrator implement?
Refer to the exhibit.
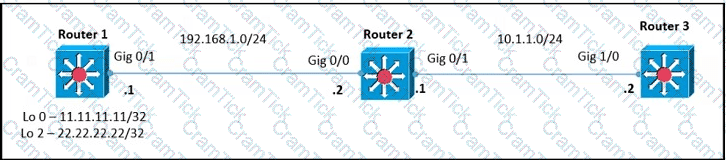
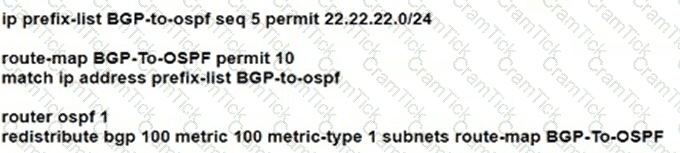
Router 1 and router 2 are running IBGP. and router 2 and router 3 are running OSPF Area 0. Router 1 is advertising loopback interlaces Lo0 and Lo2 and router 2 is redistributing BGP into OSPF Area 0. Which configuration must an administrator apply so that router 2 uses a route map to redistribute only the internal route from Lo 2?
A)
B)

C)
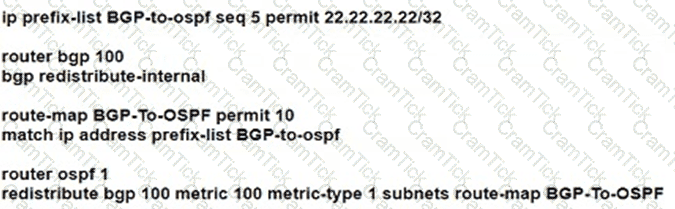
D)
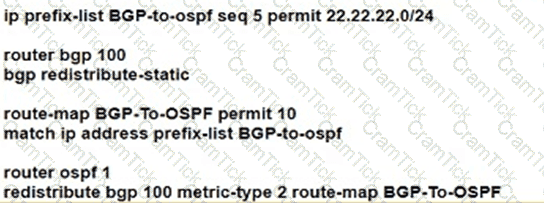
Refer to the exhibit:
Which three outcomes occur if the prefix list is added to the neighbor? (Choose three)
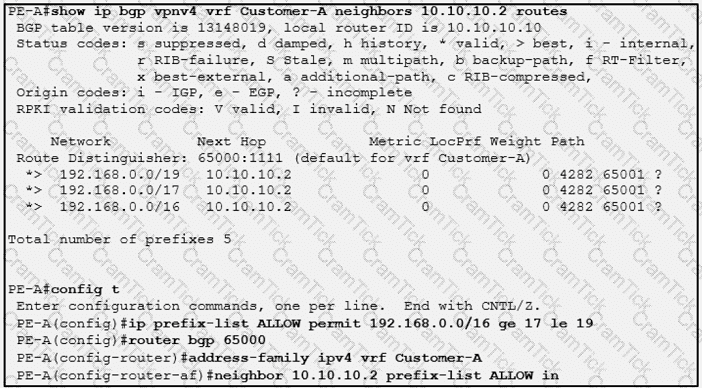
Refer to the exhibit.
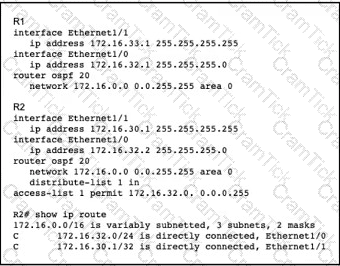
A network engineer notices that router R2 is failing to install network 172.16.33.1/32 in the routing table. Which configuration must the engineer apply to R2 to fix the problem?
Refer to the exhibit.
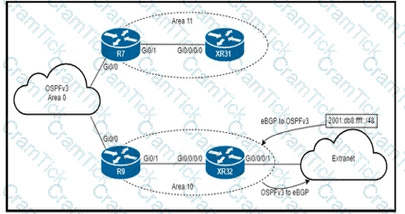
An engineer is updating this network to meet these conditions:
• Area 10 will receive inter-area routes and support mutual redistribution of external routes with the extranet.
• The ::/0 route is prohibited in Area 10.
• Area 11 will receive only the ::/0 route from the ABR.
• External route redistribution is not supported in Area 11.
• The ABR in Area 11 will advertise no interarea routes.
Which two configurations must be performed to meet the requirements? (Choose two.)
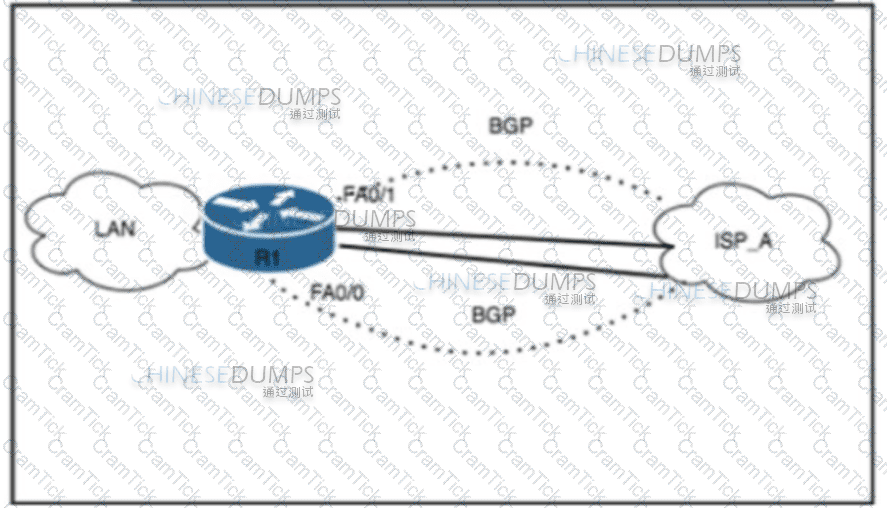
Refer to the exhibit. A network engineer must deny access from spoofed addresses to the LAN. The edge router currently has two active BGP sessions established with Tier 1 ISP_A. Due to asymmetric routing, no ACL is configured on either interface. Which two configurations must the engineer perform on the edge router to complete the task? (Choose two.)
After a series of unexpected device failures on the network. a Cisco engineer is deploying NSF on the network devices so that packets continue to be forwarded during switchovers The network devices reside in the same holding, but they are physically separated into two different data centers Which task must the engineer perform as part of the deployment?

Refer to the exhibit. An engineer started to configure a router for OSPF. Which configuration must the engineer perform on the router without changing any interface configuration so that the router establishes an OSPF neighbor relationship with its peer?
Refer to the exhibit:
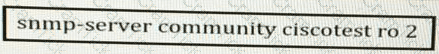
What is significant about the number 2 in the configuration?
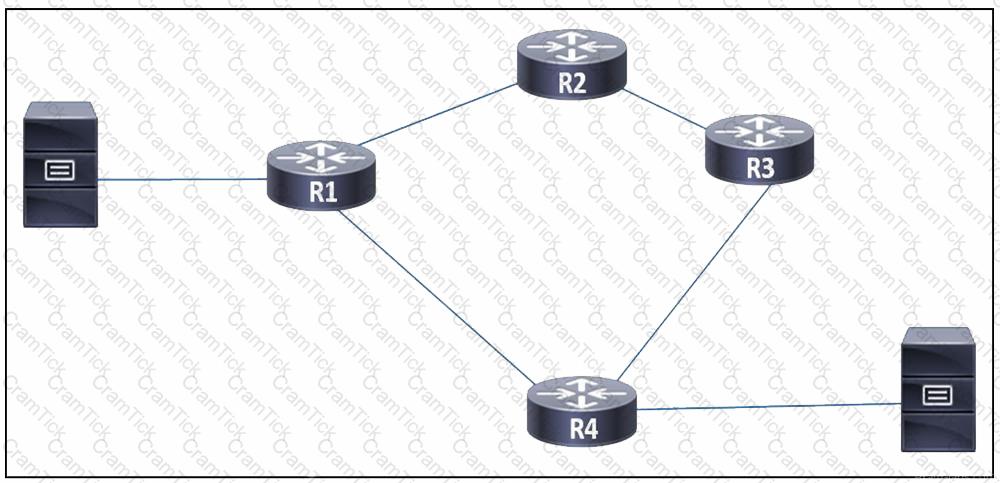
Refer to the exhibit. A network engineer observed congestion between routers R1 and R4, which are connected on a point-to-point link. Two servers that reside on networks on R1 and R4 generate heavy traffic between them with most traffic going from R4 to R1. To improve overall performance, the engineer wants to drop inbound packets that exceed a configured threshold, without disrupting traffic that passes from R4 to R3. Which action must the engineer take to resolve the issue?
Refer to the exhibits:
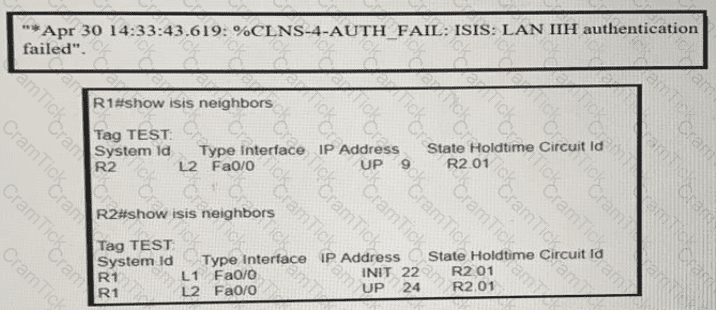
R1 and R2 are directly connected and IS-IS routing has been enabled between R1 and R2 R1 message periodically Based on this output, which statement is true?

Refer to the exhibit. A multinational corporation with a Cisco-based network wants to leverage Cisco security features to enhance the security of their LAN and protect against eavesdropping and man-in-the-middle attacks. The solution must comply with the IEEE 802.1AE standard. A network engineer must implement the new security configurations on a pair of interconnected Cisco switches. The engineer already completed the configuration to enable AAA new-model and set up a basic AAA configuration for user authentication. Management VLAN 10 is in place for network administration. Which action must the engineer take to meet the requirements?
Drag and drop the BGP Best Path Algorithm rules from the left into the corresponding order of importance on the right.
Refer to the exhibit:

It the NetFlow configuration is updated to version 9, which additional piece of information can be reported"?
BGP has been implemented on a IOS XR router. Which configuration sends BGP IPv4 labels to build inter-domain LSPs?
Refer to the exhibit. The NOC is configuring PE router R4 for BGP-originated traffic. R4 is connected to a CE device at a customer location. The customer requires:
BGP peers must establish a neighborship with NSR and NSF capability.
BGP must maintain state with the CE and provide continuous forwarding during ISSU and RP switchover events.
Which action meets the NSR requirement on PE routers?
Refer to the exhibit.
A network engineer must configure an LDP neighborship between two newly installed routers that are located in two different offices. Router 1 is the core router in the network and it has already established OSPF adjacency with router 2. On router 1 and router 2. interface fa0/0 is configured for BFD. Which additional configuration must the engineer apply to the two devices to meet the requirement?
Which MPLS design attribute can you use to provide Internet access to a major customer through a separate dedicated VPN?
A mod-size service provider uses L2VPN as its standard for connectivity between offices. A small company wants the service provider to connect the company’s two sites across the service provider core. To meet service requirements, the service provider must extend the layer 2 domain between the company’s two locations. Which configuration must the engineer apply to implement an attachment circuit between the two sites using a VLAN tag of 12?

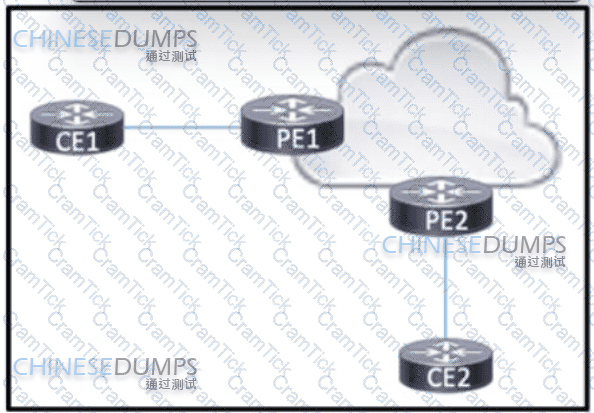
Refer to the exhibit BGP is running in the core of the service provider to exchange routes for its customers, and OSPF serves as the PE-CE routing protocol. The service provider s existing customer at CE1 is opening a new office in a different geographical location connected via CE2. A network engineer must update the BGP implementation so that PE1 and PE2 will share routes and provide communication between CE1 and CE2 Which action must the engineer take?
Refer to the exhibit.

An engineer needs to implement this QoS policy on customer's network due to ongoing slow network issues. What will be the effect on the network when the engineer implements this configuration?
Refer to the exhibit:

This configuration is being applied on an IOS XR router.
Which statement about this configuration is true?
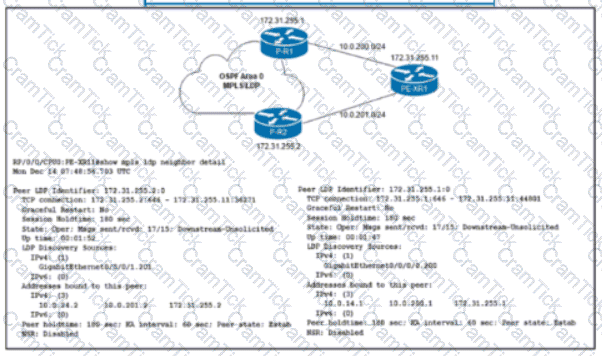
Refer to the exhibit. The network team must implement MPLS LDP session protection with two requirements:
Session protection is provided for core loopback IP addresses only.
The LDP session must remain operational for one hour when the WAN link on PE-XR1 fails.
Which configuration must the team implement on PE-XR1?
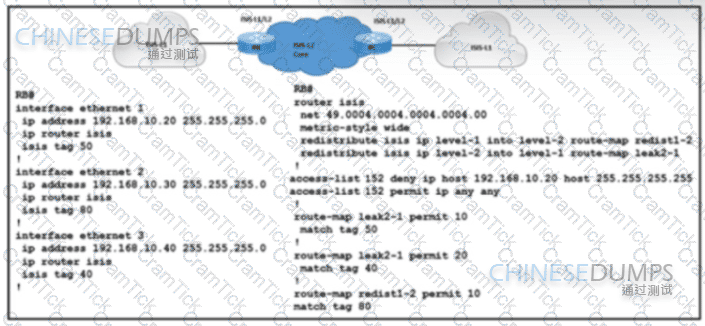
Refer to the exhibit. A network engineer with an employee ID 4379:43:595 is setting up an IS-IS network with these requirements:
Routes with a tag of 80 and IP prefixes other than 192.168.10.20/24 must be redistributed from Level 1 into Level 2.
Route leaking must be configured from Level 2 into the Level 1 domain for routes that are tagged with only 50 or 40.
Which configuration must be implemented on RB to meet the requirements?
An engineer is configuring IEEE 802.1 ad on the access port on a new Cisco router. The access port handles traffic from multiple customer VLANs, and it is expected to mark all customer traffic to the same VLAN without dropping any traffic. Which configuration must the engineer apply?
A)

B)

C)

D)

Refer to the exhibit.
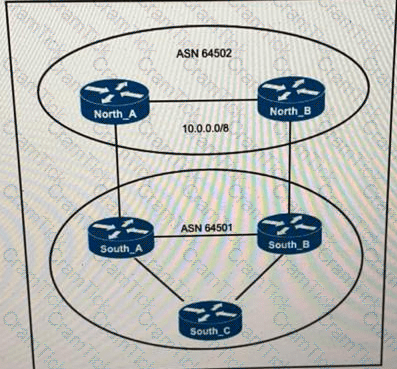
ASN 64501 currently reaches the networks under the 10.0.0.0/8 prefix via the North_B router, which is a slow backup link. The administrator of ASN 64502 wants traffic from ASN 64501 to 10.0.0.0/8 to travel via the primary link North_A. Which change to the network configuration accomplishes this task?
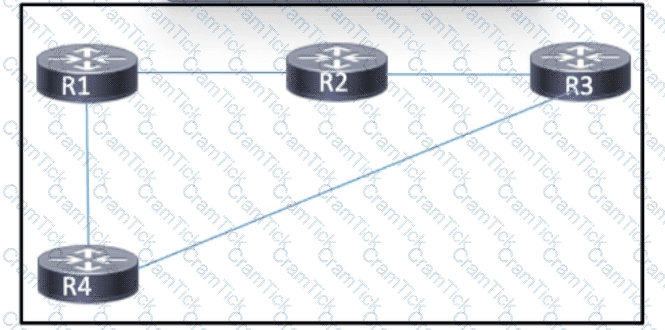
Refer to the exhibit. MPLS is configured within the network. The routers use OSPF to exchange routing information. Hosts that are connected to routers R1 and R3 use routers R2 and R4 to access servers that run a variety of intranet applications. A network engineer must ensure that R1 and R3 maintain an LDP session between them to support the flow of traffic between hosts and servers in case of failure on the path between R1 and R3. Which task should the engineer perform to provide LDP bindings in case of failure on the path between R1 and R3?
Refer to the exhibit.
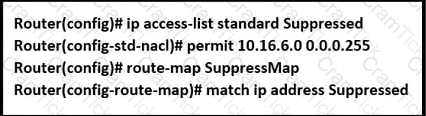
An engineer is implementing BGP selective prefix suppression. The router must advertise only 10.16.4.0/24,10.16.5.0/24. and summarized route 10.16.0.0/21. and suppress 10.16.6.0/24. Which configuration must the engineer apply to the router?
A)

B)
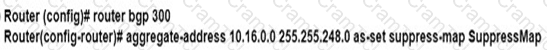
C)
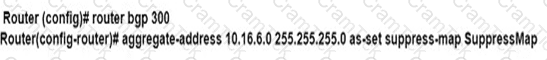
D)

Guidelines -
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology:
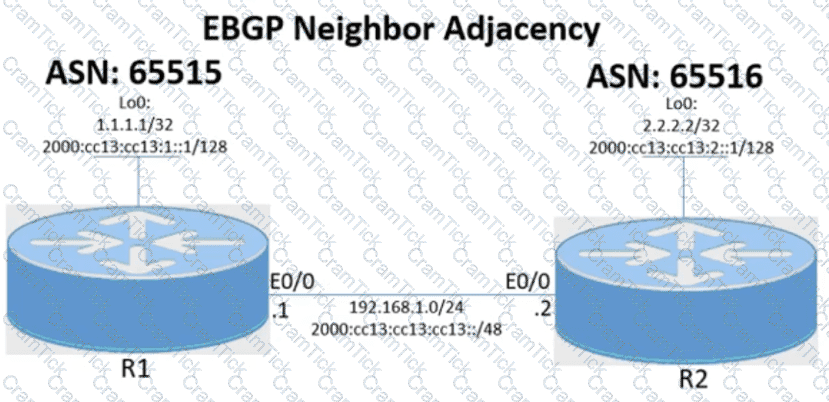
Tasks -
Configure the BGP routing protocol for R1 and R2 according to the topology to achieve these goals:
1. Configure EBGP neighbor adjacency for the IPv4 and IPv6 address family between R1 and R2 using Loopback0 IPv4 and IPv6 addresses. All BGP updates must come from the Loopback0 interface as the source. Do not use IGP routing protocols to complete this task.
2. Configure MD5 Authentication for the EBGP adjacency between R1 and R2. The password is clear text C1sc0!.
CCNP Service Provider | 350-501 Written Exam | 350-501 Questions Answers | 350-501 Test Prep | 350-501 CCNP Service Provider Actual Questions | Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) Exam Questions PDF | 350-501 Online Exam | 350-501 Practice Test | 350-501 PDF | 350-501 CCNP Service Provider Dumps | 350-501 Test Questions | 350-501 Study Material | 350-501 Exam Preparation | 350-501 Valid Dumps | 350-501 Real Questions | 350-501 CCNP Service Provider Practice Test | CCNP Service Provider 350-501 Dumps | Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) Exam Questions


