Your network contains an on-premises Active Directory domain named adatum.com that syncs to a Microsoft Entra tenant.
The Microsoft Entra tenant contains the users shown in the following table.
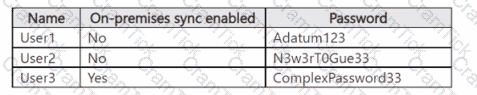
You configure the Microsoft Entra Password Protection settings for adatum.com as shown in the following exhibit.
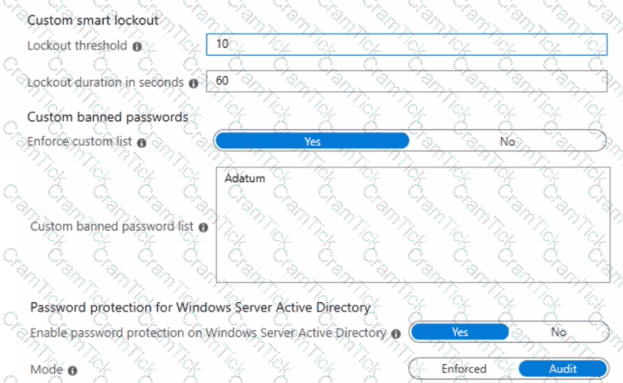
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have an Azure subscription that contains an Azure Data Lake Storage account named sa1.
You plan to deploy an app named App1 that will access sa1 and perform operations, including Read. List, Create Directory, and Delete Directory.
You need to ensure that App1 can connect securely to sa1 by using a private endpoint
What is the minimum number of private endpoints required for sa1?
You have an Azure Subscription that is connected to an on-premises datacenter and contains the resources shown in the following table.
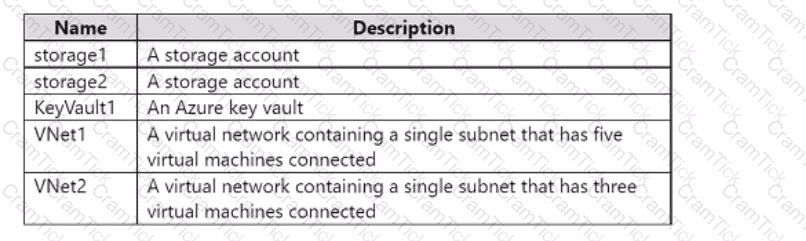
You need to configure virtual network service endpoints for VNet1 and VNet2. The solution must meet the following requirements:
• The virtual machines that connect to the subnet of VNet1 must access storage1, storage2, and Azure AD by using the Microsoft backbone network.
• The virtual machines that connect to the subnet of VNet2 must access storage1 and KeyVault1 by using the Microsoft backbone network.
• The virtual machines must use the Microsoft backbone network to communicate between VNet1 and VNet2.
How many service endpoints should you configure for each virtual network? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

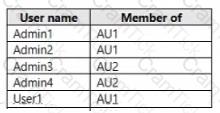
You have an Azure Active Directory (Azure AD) tenant that contains two administrative units named AU1 and AU2.
Users are assigned to the administrative units as shown in the following table.
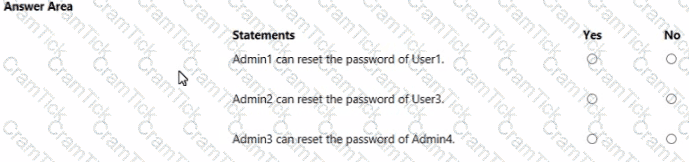
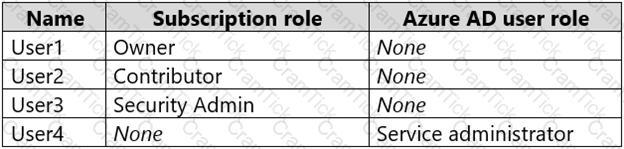
You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.
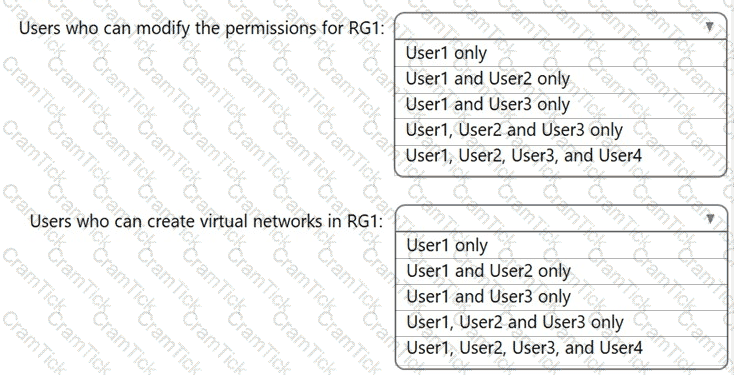
You create a resource group named RG1.
Which users can modify the permissions for RG1 and which users can create virtual networks in RG1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You create an Azure subscription with Azure AD Premium P2.
You need to ensure that you can use Azure Active Directory (Azure AD) Privileged Identity Management (PIM) to secure Azure roles.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

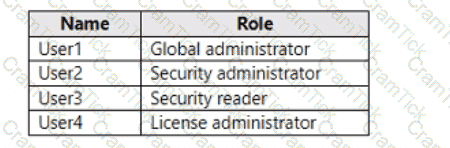
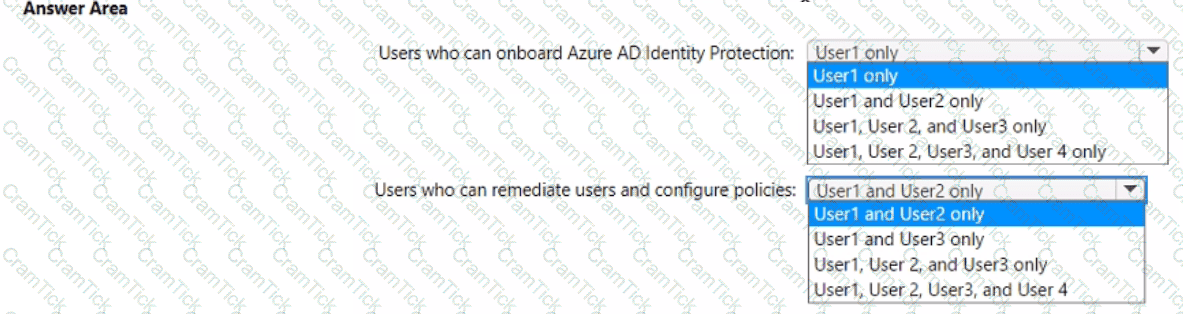
You have an Azure subscription named Sub 1 that is associated to an Azure AD Tenant named contoso.com. The tenant contains the users shown in the following table.
Each user is assigned an Azure AD Premium P2 license.
You plan to onboard and configure Azure AD Identity Protection.
Which users can onboard Azure AD Identity Protection, remediate users, and configure policies? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
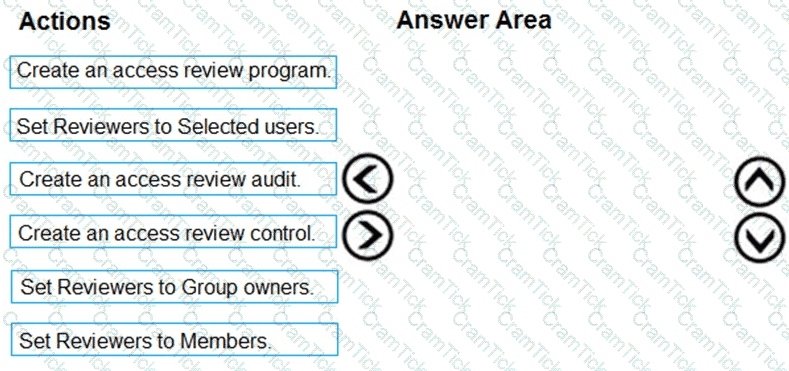
You need to configure an access review. The review will be assigned to a new collection of reviews and reviewed by resource owners.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Lab Task
use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password. place your cursor in the Enter password box and click on the password below.
Azure Username: Userl -28681041@ExamUsers.com
Azure Password: GpOAe4@lDg
If the Azure portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 28681041
Task 8
You need to prevent HTTP connections to the rg1lod28681041n1 Azure Storage account.
You have a Microsoft Entra tenant that contains the users shown in the following table.
AII the users have devices that contain certificates issued by a certification authority (CA) named ContosoCA. You create a Conditional Access policy that has the following settings:
• Name: CAPoltcy1
• Assignments
o Users and groups: Group1
o Target resources
* Include: All cloud apps
o Access controls
* Grant access: Require multi-factor authentication
o Enable policy: On
You enable and target certificate-based authentication as shown in the Enable and Target exhibit. (Click the Enable and Target tab.)
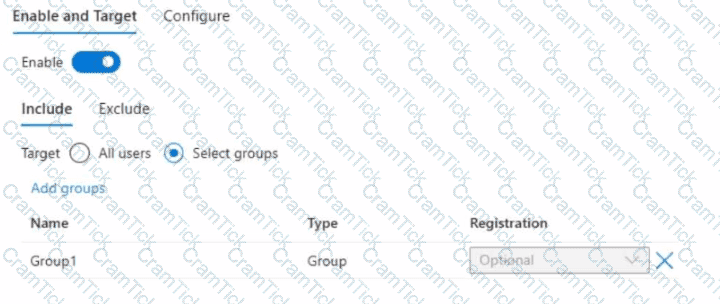
You configure certificate-based authentication as shown in the Configure exhibit. (Click the Configure tab.)
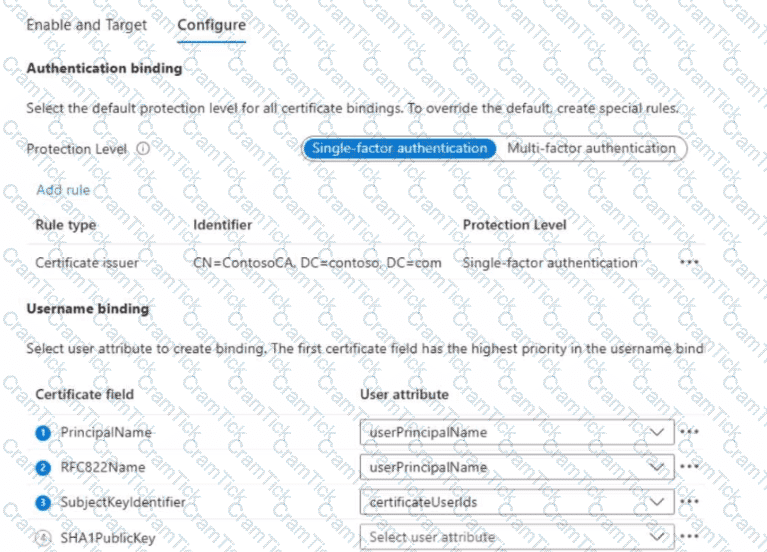
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

You have an Azure subscription.
You need to ensure that you receive notifications regarding suspicious Azure DNS activity.
Which Microsoft Defender plan for Cloud Workload Protection (CWP) should you enable?
You have an Azure subscription that contains a resource group named RG1 and the network security groups (NSGs) shown in the following table.
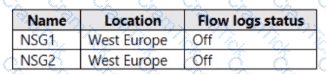
You create the Azure policy shown in the following exhibit.
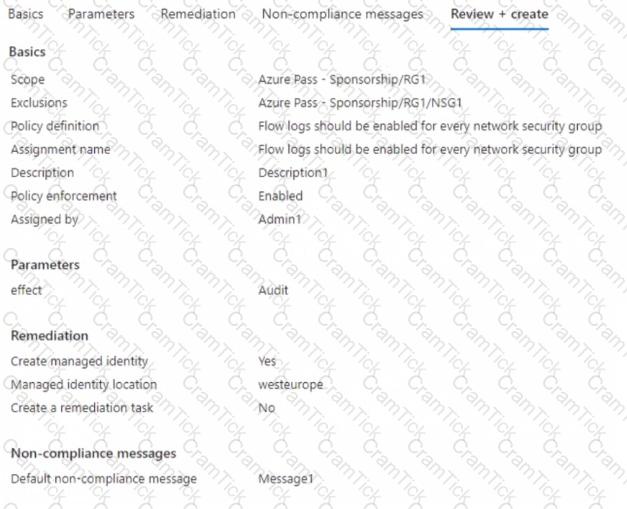
You assign the policy to RG1.
What will occur if you assign the policy to NSG1 and NSG2?
You have an Azure subscription that contains an Azure App Services web app named WebApp1 and an Azure key vault named Vault1. Vault1 has the certificates shown in the following table.
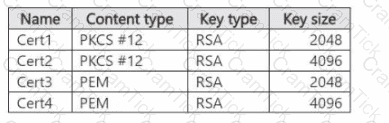
You plan to implement TLS for WebApp1.
You need to add a certificate to WebApp1.
Which certificates from Vault1 can you add to WebApp1?
You have an Azure subscription that uses Azure AD Privileged Identity Management (PIM).
A user named User1 is eligible for the Billing administrator role.
You need to ensure that the role can only be used for a maximum of two hours.
What should you do?
You have an Azure subscription that contains an Azure key vault named Vault1 and a virtual machine named VM1. VM1 has the Key Vault VM extension installed.
For Vault1, you rotate the keys, secrets, and certificates.
What will be updated automatically on VM1?
You have an Azure subscription that contains several Azure SQL databases and an Azure Sentinel
workspace.
You need to create a saved query in the workspace to find events reported by Advanced Threat Protection for Azure SQL Database.
What should you do?
You have an Azure key vault named sk2311 configured as shown in the following exhibit.
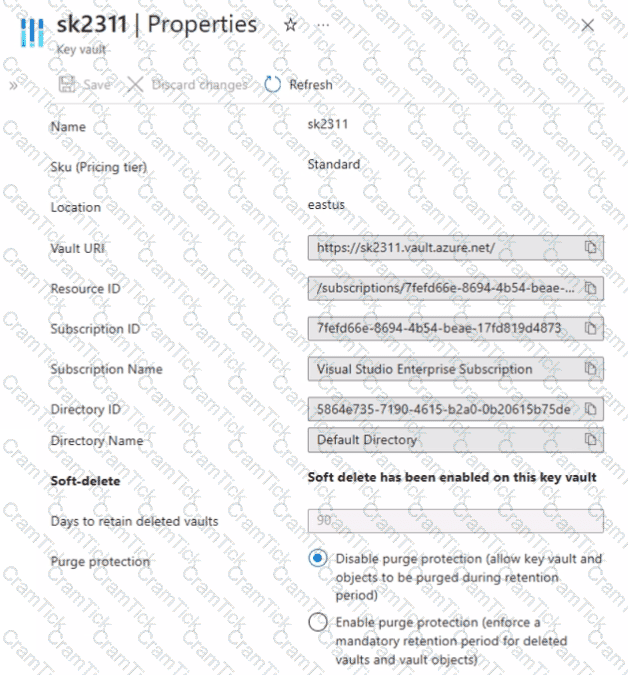
Sk2311 contains the items shown in the following table.

In sk2311, the following events occur in sequence:
• Item1 is deleted.
• Item2 and Policy1 ate deleted.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have an Azure subscription that contains a virtual machine named VM1.
You create an Azure key vault that has the following configurations:
Name: Vault5
Region: West US
Resource group: RG1
You need to use Vault5 to enable Azure Disk Encryption on VM1. The solution must support backing up VM1 by using Azure Backup.
Which key vault settings should you configure?
You have an Azure subscription that contains the resources shown in the following table.
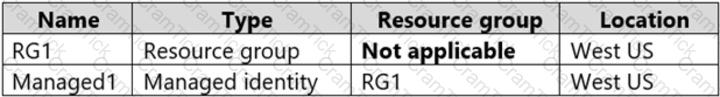
The subscription is linked to an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
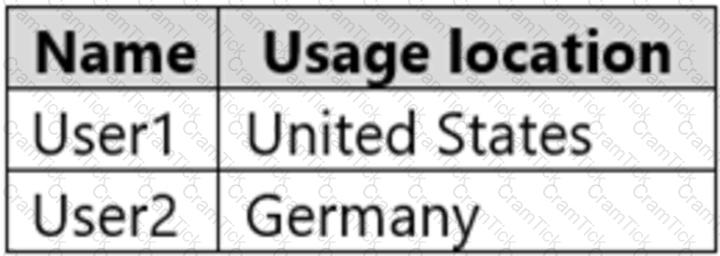
You create the groups shown in the following table.
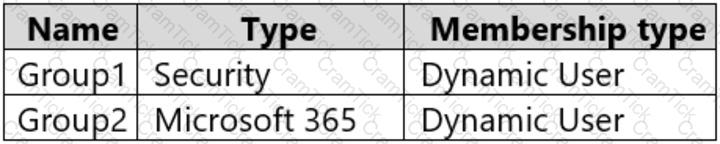
The membership rules for Group1 and Group2 are configured as shown in the following exhibit.
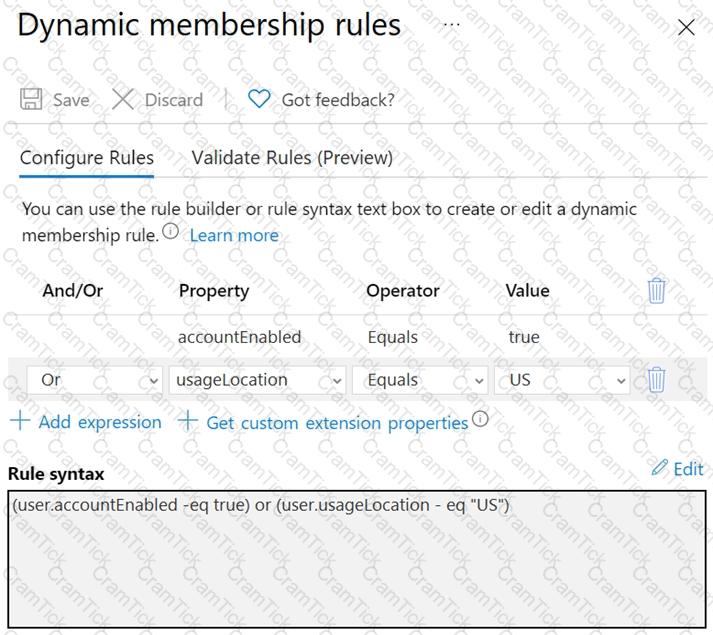
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have an Azure subscription named Sub1.
You create a virtual network that contains one subnet. On the subnet, you provision the virtual machines shown in the following table.
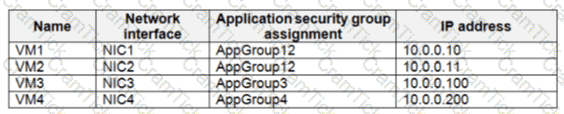
Currently, you have not provisioned any network security groups (NSGs).
You need to implement network security to meet the following requirements:
Allow traffic to VM4 from VM3 only.
Allow traffic from the Internet to VM1 and VM2 only.
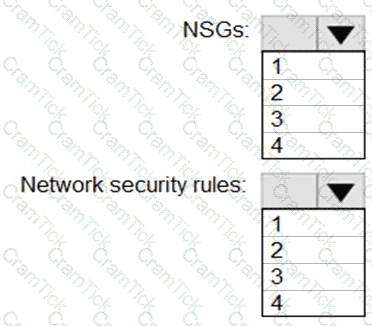
Minimize the number of NSGs and network security rules.
How many NSGs and network security rules should you create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Lab Task
Task 3
You need to ensure that a user named Danny-31330471 can sign in to any SQL database on a Microsoft SQL server named web31330471 by using SQL Server Management Studio (SSMS) and Azure AD credentials.
You have an Azure subscription that contains a web app named Appl. App1 provides users with product images and videos. Users access App1 by using a URL of HTTPS://appl.contoso.com. You deploy two server pools named Pool! and Pool2. Pool1 hosts product images. Pool2 hosts product videos. You need to optimize The performance of Appl. The solution must meet the following requirements:
• Minimize the performance impact of TLS connections on Pool1 and Pool2.
• Route user requests to the server pools based on the requested URL path.
What should you include in the solution?
You have an Azure subscription that uses Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
A PIM user that is assigned the User Access Administrator role reports receiving an authorization error when performing a role assignment or viewing the list of assignments.
You need to resolve the issue by ensuring that the PIM service principal has the correct permissions for the subscription. The solution must use the principle of least privilege.
Which role should you assign to the PIM service principle?
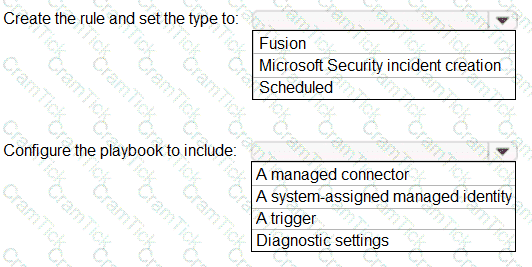
You have an Azure Sentinel workspace that contains an Azure Active Directory (Azure AD) connector, an Azure Log Analytics query named Query1 and a playbook named Playbook1.
Query1 returns a subset of security events generated by Azure AD.
You plan to create an Azure Sentinel analytic rule based on Query1 that will trigger Playbook1.
You need to ensure that you can add Playbook1 to the new rule.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
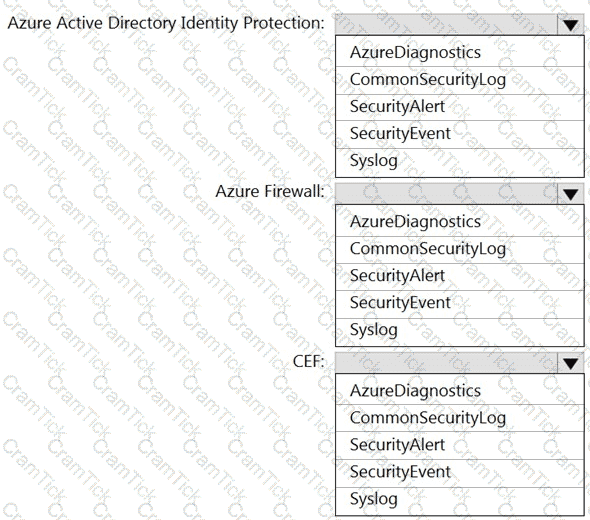
You have an Azure Sentinel workspace that has the following data connectors:
Azure Active Directory Identity Protection
Common Event Format (CEF)
Azure Firewall
You need to ensure that data is being ingested from each connector.
From the Logs query window, which table should you query for each connector? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a user named UseR1. You need to ensure that UseR1 can perform the following tasks:
• Create groups.
• Create access reviews for role-assignable groups.
• Assign Azure AD roles to groups.
The solution must use the principle of least privilege. Which role should you assign to User1?
You need to ensure that users can access VM0. The solution must meet the platform protection requirements.
What should you do?
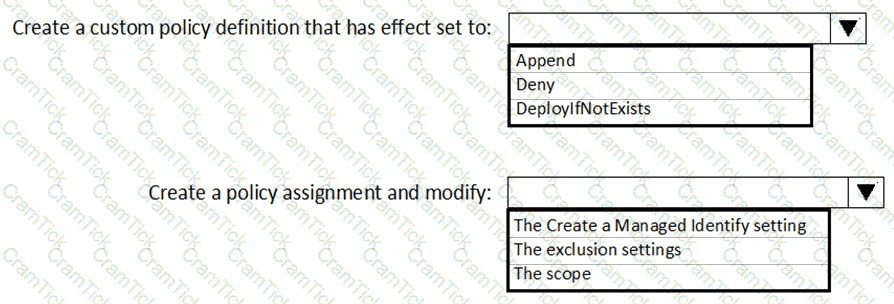
You need to deploy AKS1 to meet the platform protection requirements.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.
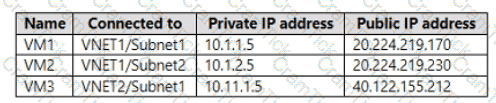
You have an Azure subscription that is linked to an Azure AD tenant and contains the virtual machines shown in the following table.
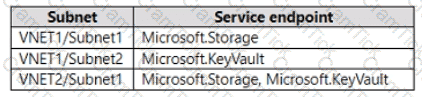
The subnets of the virtual networks have the service endpoints shown in the following table.
You create the resources shown in the following table.
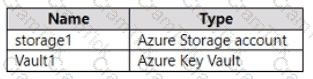
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
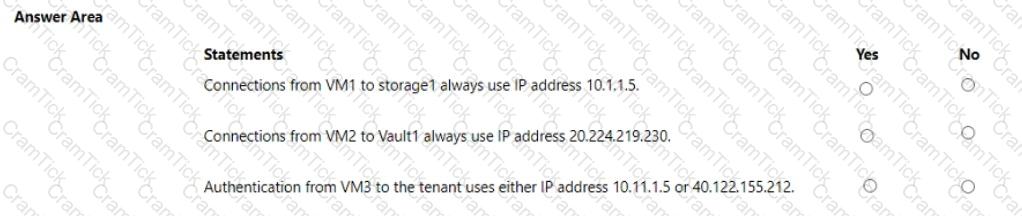
You need to create Role1 to meet the platform protection requirements.
How should you complete the role definition of Role1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the identity and access requirements for Group1.
What should you do?
You need to configure WebApp1 to meet the data and application requirements.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
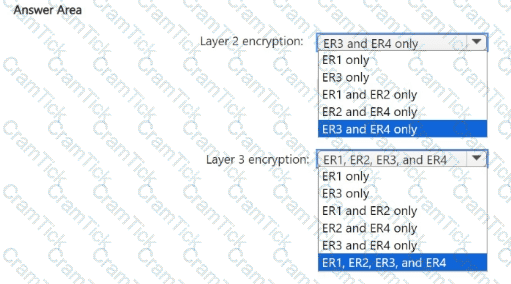
You need to recommend an encryption solution for the planned ExpressRoute implementation. The solution must meet the technical requirements.
Which ExpressRoute circuit should you recommend for each type of encryption? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
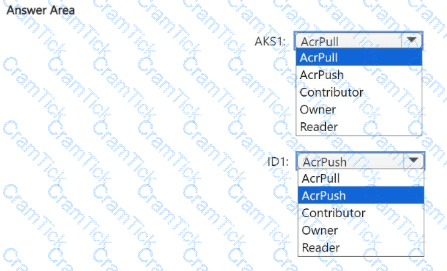
You need to configure the AKS1 and ID1 managed identities to meet the technical requirements. The solution must follow the principle of least privilege.
Which role should you assign to each identity? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement the planned change for VM1 to access storage1.
The solution must meet the technical requirements.
What should you do first?
You implement the planned changes for the key vaults.
To which key vaults can you restore AKV1 backups?
You need to deploy Microsoft Antimalware to meet the platform protection requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to encrypt storage1 to meet the technical requirements. Which key vaults can you use?
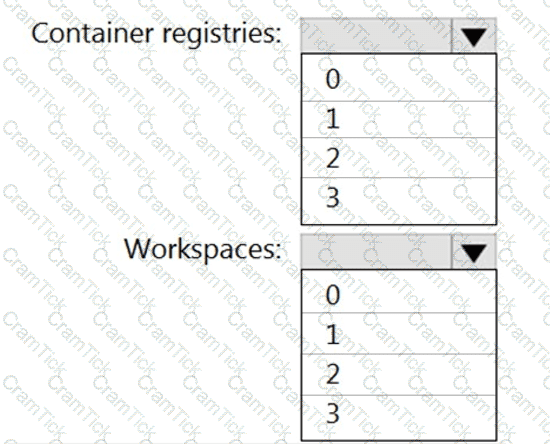
You need to configure support for Azure Sentinel notebooks to meet the technical requirements.
What is the minimum number of Azure container registries and Azure Machine Learning workspaces required?
You plan to configure Azure Disk Encryption for VM4. Which key vault can you use to store the encryption key?
You need to meet the technical requirements for the finance department users.
Which CAPolicy1 settings should you modify?
You implement the planned changes for ASG1 and ASG2.
In which NSGs can you use ASG1. and the network interfaces of which virtual machines can you assign to ASG2?

From Azure Security Center, you need to deploy SecPol1.
What should you do first?
You need to delegate a user to implement the planned change for Defender for Cloud.
The solution must follow the principle of least privilege.
Which user should you choose?
You need to implement the planned change for SQLdb1.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
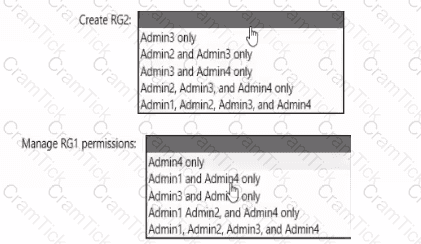
You need to delegate the creation of RG2 and the management of permissions for RG1. Which users can perform each task? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point
You need to implement the planned change for WAF1.
The solution must minimize administrative effort
What should you do?
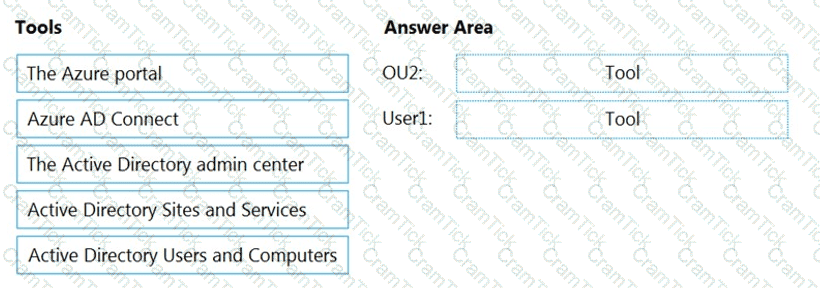
You need to perform the planned changes for OU2 and User1.
Which tools should you use? To answer, drag the appropriate tools to the correct resources. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
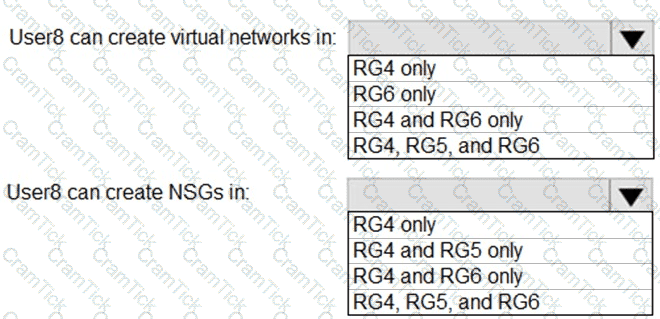
You assign User8 the Owner role for RG4, RG5, and RG6.
In which resource groups can User8 create virtual networks and NSGs? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
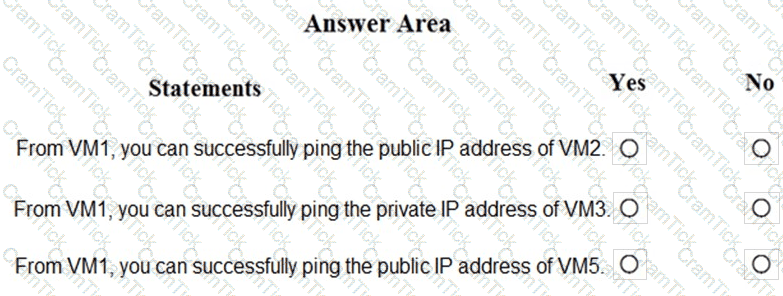
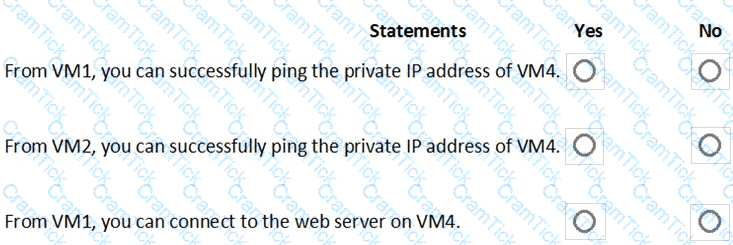
You are evaluating the security of the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
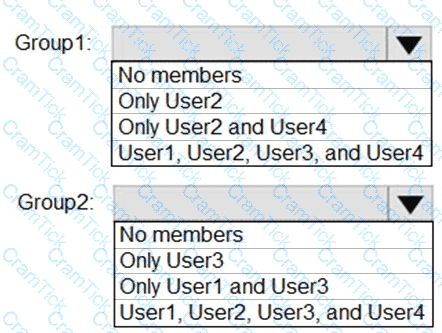
What is the membership of Group1 and Group2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirements for VNetwork1.
What should you do first?
You are evaluating the effect of the application security groups on the network communication between the virtual machines in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
: 2 HOTSPOT
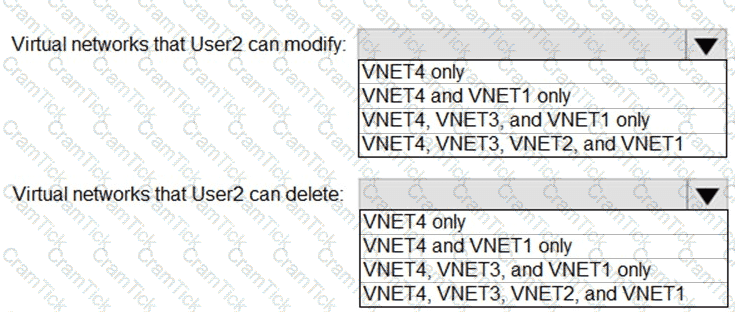
Which virtual networks in Sub1 can User2 modify and delete in their current state? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You are evaluating the security of VM1, VM2, and VM3 in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Azure Security Engineer Associate | AZ-500 Exam Topics | AZ-500 Questions answers | AZ-500 Test Prep | Microsoft Azure Security Technologies Exam Questions PDF | AZ-500 Online Exam | AZ-500 Practice Test | AZ-500 PDF | AZ-500 Test Questions | AZ-500 Study Material | AZ-500 Exam Preparation | AZ-500 Valid Dumps | AZ-500 Real Questions | Azure Security Engineer Associate AZ-500 Exam Questions


