A software development company recently implemented a new policy and control ruleset. The control ruleset defines the following:
• Account naming standards
• Password complexity standards
• SOLC practices
• Encryption baselines and standards
A review of the current applications used and developed by the company shows many production and mission-critical applications are not compliant with the new policies and control ruleset. Which of the following actions should be performed''
The OS on several servers crashed around the same time for an unknown reason. The servers were restored to working condition, and all file integrity was verified. Which of the following should the incident response team perform to understand the crash and prevent it in the future?
A product owner is working w*h a security engineer to improve the security surrounding certificate revocation which is important for the clients using a web application. The organization is currently using a CRL configuration to manage revocation, but it is looking for a solution that addresses the reporting delays associated with CRLs. The security engineer recommends OCSP but the product owner is concerned about the overhead associated with its use Which of the following would the security engineer MOST likely suggest to address the product owner's concerns?
While standing a proof-of-concept solution with a vendor, the following direction was given of connections to the default environments.

Which of the following is using used to secure the three environments from overlap if all of them reside on separate serves in the same DM2?
A penetration tester is given an assignment lo gain physical access to a secure facility with perimeter cameras. The secure facility does not accept visitors and entry is available only through a door protected by an RFID key and a guard stationed inside the door Which of the following would be BEST for the penetration tester to attempt?
A security technician wants to learn about the latest zero-day threats and newly discovered vulnerabilities but does not have the budget to purchase a commercial threat intelligence service. Which of the following would BEST meet the needs of the security technician? (Select TWO)
A company recently implemented a new cloud storage solution and installed the required synchronization client on all company devices. A few months later, a breach of sensitive data was discovered. Root cause analysis shows the data breach happened from a lost personal mobile device.
Which of the following controls can the organization implement to reduce the risk of similar breaches?
An application developer is including third-party background security fixes in an application. The fixes seem to resolve a currently identified security issue. However, when the application is released to the public, report come In that a previously vulnerability has returned. Which of the following should the developer integrate into the process to BEST prevent this type of behavior?
An organization has hardened its end points m the following ways
• USB ports are disabled except for approved input device IDs (e.g, mouse, keyboard)
• A desktop firewall is Mocking all outbound network connections, except to approved internal systems
• A VPN client is the only way to connect to the corporate network remotely and split tunneling is disabled
• Bluetooth is disabled
• Web browsing from end points is permitted but the traffic is directed through the VPN to the corporate gateway
• The email client is permitted to connect to the internal server over the VPN and DLP rules prohibit sending sensitive information to external recipients
The organization recently suffered a security breach »i which a file containing PlI somehow made it from a remote user's laptop to an unauthorized host Which of the following is the MOST likely explanation for how (his happened?
Staff members are reporting an unusual number of device thefts associated with time out of the office. Thefts increased soon after the company deployed a new social networking app. Which of the following should the Chief Information Security Officer (CISO) recommend implementing?
Ann, a corporate executive, has been the recent target of increasing attempts to obtain corporate secrets by competitors through advanced, well-funded means. Ann frequently leaves her laptop unattended and physically unsecure in hotel rooms during travel. A security engineer must find a practical solution for Ann that minimizes the need for user training. Which of the following is the BEST solution in this scenario?
A security analyst is trying to identify the source of a recent data loss incident. The analyst has reviewed all the for the time surrounding the identified all the assets on the network at the time of the data loss. The analyst suspects the key to finding the source was obfuscated in an application. Which of the following tools should the analyst use NEXT?
A security engineer is working to secure an organization’s VMs. While reviewing the workflow for creating VMs on demand, the engineer raises a concern about the integrity of the secure boot process of the VM guest.
Which of the following would BEST address this concern?
A network engineer recently configured a new wireless network that has issues with security stability and performance After auditing the configurations the engineer discovers some of them do not follow best practices Given the network information below
SSID = CompTIA Channel = 6 WPA-PSK
Which of the following would be the BEST approach to mitigate the issues?
A Chief Information Security Officer (CISO) of a large financial institution undergoing an IT transformation program wants to embed security across the business rapidly and across as many layers of the business as possible to achieve quick wins and reduce risk to the organization. Which of the following business areas should the CISO target FIRST to best meet the objective?
A company is implementing a new MFA initiative. The requirements for the second factor ate as folio.*.s
• It cannot be phished
• it must work as a second factor for laptop logins
• It must be something the user has
Which of the following solutions should the company choose?
A developer implements the following code snippet:
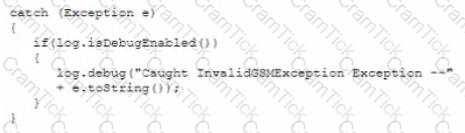
Which of the following vulnerabilities does this code snippet resolve?
A network engineer is concerned about hosting web SFTP. and email services m a single DMZ that is hosted in the same security zone. This could potentially allow lateral movement within the environment Which of the following should the engineer implement to mitigate the risk?
An analyst execute a vulnerability scan against an internet-facing DNS server and receives the following report:

Which of the following tools should the analyst use FIRST to validate the most critical vulnerability?
A security engineer is attempting to inventory all network devices Most unknown devices are not responsive to SNMP queries. Which of the following would be the MOST secure configuration?
As part of the asset management life cycle, a company engages a certified equipment disposal vendor to appropriately recycle and destroy company assets that are no longer in use. As part of the company’s vendor due diligence, which of the following would be MOST important to obtain from the vendor?
A Chief Information Security Officer (CISO) recently changed jobs into a new industry. The CISO’s first task is to write a new, relevant risk assessment for the organization. Which of the following help to the CISO find relevant risks to the organization? (Choose two.)
A security engineer is investigating a compromise that occurred between two internal computers. The engineer has determined during the investigation that one computer infected another. While reviewing the IDS logs, the engineer can view the outbound callback traffic, but sees no traffic between the two computers. Which of the following would BEST address the IDS visibility gap?
When implementing a penetration testing program, the Chief Information Security Officer (CISO) designates different organizational groups within the organization as having different responsibilities, attack vectors, and rules of engagement. First, the CISO designates a team to operate from within the corporate environment. This team is commonly referred to as:
A security consultant is conducting a penetration test against a customer enterprise local comprises local hosts and cloud-based servers The hosting service employs a multitenancy model with elastic provisioning to meet customer demand The customer runs multiple virtualized servers on each provisioned cloud host. The security consultant is able to obtain multiple sets of administrator credentials without penetrating the customer network. Which of the following is the MOST likely risk the tester exploited?
A company recently developed a new mobile application that will be used to access a sensitive system. The application and the system have the following requirements:
• The application contains sensitive encryption material and should not be accessible over the network
• The system should not be exposed to the Internet
• Communication must be encrypted and authenticated by both the server and the client
Which of the following can be used to install the application on the mobile device? (Select TWO).
An organization recently suffered a high-impact loss due to a zero-day vulnerability exploited in a concentrator enabling iPSec VPN access for users The attack included a pivot into the internal server subnet. The organization now wants to integrate new changes into its architecture to make a similar future attack less impactful Which of the following changes would BEST achieve this objective''
A small company is implementing a new technology that promises greater performance but does not abide by accepted RFCs. Which of the following should the company do to ensure the risks associated with Implementing the standard-violating technology is addressed?
Company leadership believes employees are experiencing an increased number of cyber attacks; however, the metrics do not show this. Currently, the company uses “Number of successful phishing attacks” as a KRI, but it does not show an increase.
Which of the following additional information should be the Chief Information Security Officer (CISO) include in the report?
A company has launched a phishing awareness campaign that includes serving customized phishing email to employees Employees are encouraged to report all phishing attempts and/or delete the email without clicking on them The first phishing email asks employees to dick on a link that takes them to a website where they are asked to enter their credentials The management team wants metrics to determine the emails effectiveness Following is the initial report:
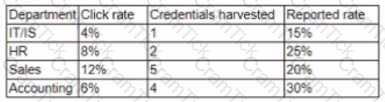
The management team wants to know how these results compare to those of other companies. They also want to improve the consistency of how the information is displayed Which of the following changes should be made to this report?
A security analyst is investigating an alert arising from an impossible travel pattern Within the span of 30 minutes, the email system saw successful authentication from two IP addresses, which geolocate more than 500mi (806km) away from each other Before locking the account which of the following actions should the analyst take?
A security administrator receives reports that several workstations are unable to access resources within one network segment. A packet capture shows the segment is flooded with ICMPv6 traffic from the source fe80::21ae;4571:42ab:1fdd and for the destination ff02::1. Which of the following should the security administrator integrate into the network to help prevent this from occurring?
A security analyst is attempting to break into a client’s secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the analyst’s NEXT step is to perform:
Which of the following attacks can be mitigated by proper data retention policies?
A Chief Information Security Officer (CISO) implemented MFA for all accounts in parallel with the BYOD policy. After the implementation, employees report the increased authentication method is causing increased time to tasks. This applies both to accessing the email client on the workstation and the online collaboration portal. Which of the following should be the CISO implement to address the employees’ concerns?
As part of an organization's ongoing vulnerability assessment program, the Chief Information Security Officer (CISO) wants to evaluate the organization's systems, personnel, and facilities for various threats As part of the assessment the CISO plans to engage an independent cybersecurity assessment firm to perform social engineering and physical penetration testing against the organization's corporate offices and remote locations. Which of the following techniques would MOST likely be employed as part of this assessment? (Select THREE).
The Chief Information Security Officer (CISO) of a company that has highly sensitive corporate locations wants its security engineers to find a solution to growing concerns regarding mobile devices The CISO mandates the following requirements:
• The devices must be owned by the company for legal purposes.
• The device must be as fully functional as possible when off site.
• Corporate email must be maintained separately from personal email
• Employees must be able to install their own applications.
Which of the following will BEST meet the CISO's mandate? (Select TWO).
An analyst has noticed unusual activities in the SIEM to a .cn domain name. Which of the following should the analyst use to identify the content of the traffic?
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded and unmanaged HVAC controller, which is used to monitor the company's datacenter
Port state
161/UDP open
162/UDP open
163/TCP open
The enterprise monitoring service requires SNMP and SNMPTRAP connectivity to operate. Which of the following should the security administrator implement to harden the system?
An organization is integrating an ICS and wants to ensure the system is cyber resilient. Unfortunately, many of the specialized components are legacy systems that cannot be patched. The existing enterprise consists of mission-critical systems that require 99.9% uptime. To assist in the appropriate design of the system given the constraints, which of the following MUST be assumed?
A company recently implemented a variety of security services to detect various types of traffic that pose a threat to the company. The following services were enabled within the network:
• Scan of specific subsets for vulnerabilities
• Categorizing and logging of website traffic
• Enabling specific ACLs based on application traffic
• Sending suspicious files to a third-party site for validation
A report was sent to the security team that identified multiple incidents of users sharing large amounts of data from an on-premise server to a public site. A small percentage of that data also contained malware and spyware
Which of the following services MOST likely identified the behavior and sent the report?
A security administrator is concerned about employees connecting their personal devices to the company network. Doing so is against company policy. The network does not have a NAC solution. The company uses a GPO that disables the firewall on all company-owned devices while they are connected to the internal network Additionally, all company-owned devices implement a standard naming convention that uses the device's serial number. The security administrator wants to identify active personal devices and write a custom script to disconnect them from the network Which of the following should the script use to BEST accomplish this task?
A project manager is working with system owners to develop maintenance windows for system pathing and upgrades in a cloud-based PaaS environment. Management has indicated one maintenance windows will be authorized per month, but clients have stated they require quarterly maintenance windows to meet their obligations. Which of the following documents should the project manager review?
Following a complete outage of the electronic medical record system for more than 18 hours, the hospital’s Chief Executive Officer (CEO) has requested that the Chief Information Security Officer (CISO) perform an investigation into the possibility of a disgruntled employee causing the outage maliciously. To begin the investigation, the CISO pulls all event logs and device configurations from the time of the outage. The CISO immediately notices the configuration of a top-of-rack switch from one day prior to the outage does not match the configuration that was in place at the time of the outage. However, none of the event logs show who changed the switch configuration, and seven people have the ability to change it. Because of this, the investigation is inconclusive.
Which of the following processes should be implemented to ensure this information is available for future investigations?
The finance department has started to use a new payment system that requires strict PII security restrictions on various network devices. The company decides to enforce the restrictions and configure all devices appropriately. Which of the following risk response strategies is being used?
A vulnerability was recently announced that allows a malicious user to gain root privileges on other virtual machines running within the same hardware cluster. Customers of which of the following cloud-based solutions should be MOST concerned about this vulnerability?
A Chief Information Security Officer (CISO) needs to establish a KRI for a particular system. The system holds archives of contracts that are no longer in use. The contracts contain intellectual property and have a data classification of non-public. Which of the following be the BEST risk indicator for this system?
A government organization operates and maintains several ICS environments. The categorization of one of the ICS environments led to a moderate baseline. The organization has complied a set of applicable security controls based on this categorization.
Given that this is a unique environment, which of the following should the organization do NEXT to determine if other security controls should be considered?
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.
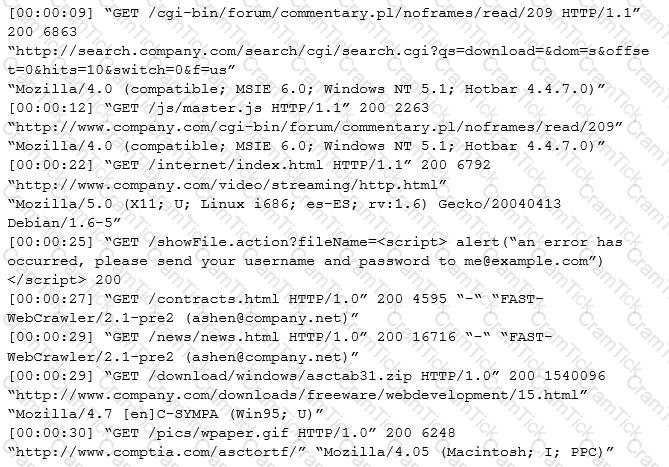
Which of the following types of attack vector did the penetration tester use?
A newly hired Chief Information Security Officer (CISO) is reviewing the organization’s security budget from the previous year. The CISO notices $100,000 worth of fines were paid for not properly encrypting outbound email messages. The CISO expects next year’s costs associated with fines to double and the volume of messages to increase by 100%. The organization sent out approximately 25,000 messages per year over the last three years. Given the table below:
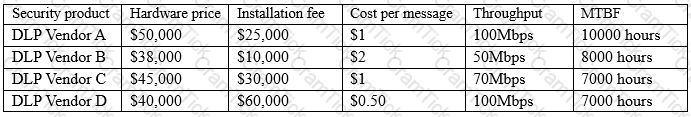
Which of the following would be BEST for the CISO to include in this year’s budget?
An architect was recently hired by a power utility to increase the security posture of the company’s power generation and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported software driving critical operations. These systems must exchange data with each other, be highly synchronized, and pull from the Internet time sources. Which of the following architectural decisions would BEST reduce the likelihood of a successful attack without harming operational capability? (Choose two.)
The Chief Executive Officers (CEOs) from two different companies are discussing the highly sensitive prospect of merging their respective companies together. Both have invited their Chief Information Officers (CIOs) to discern how they can securely and digitally communicate, and the following criteria are collectively determined:
Which of the following communication methods would be BEST to recommend?
The marketing department has developed a new marketing campaign involving significant social media outreach. The campaign includes allowing employees and customers to submit blog posts and pictures of their day-to-day experiences at the company. The information security manager has been asked to provide an informative letter to all participants regarding the security risks and how to avoid privacy and operational security issues. Which of the following is the MOST important information to reference in the letter?
After a large organization has completed the acquisition of a smaller company, the smaller company must implement new host-based security controls to connect its employees’ devices to the network. Given that the network requires 802.1X EAP-PEAP to identify and authenticate devices, which of the following should the security administrator do to integrate the new employees’ devices into the network securely?
A security engineer is attempting to convey the importance of including job rotation in a company’s standard security policies. Which of the following would be the BEST justification?
A company has adopted and established a continuous-monitoring capability, which has proven to be effective in vulnerability management, diagnostics, and mitigation. The company wants to increase the likelihood that it is able to discover and therefore respond to emerging threats earlier in the life cycle.
Which of the following methodologies would BEST help the company to meet this objective? (Choose two.)
The Chief Executive Officer (CEO) of a small startup company has an urgent need for a security policy and assessment to address governance, risk management, and compliance. The company has a resource-constrained IT department, but has no information security staff. The CEO has asked for this to be completed in three months.
Which of the following would be the MOST cost-effective solution to meet the company’s needs?
A Chief Information Officer (CIO) publicly announces the implementation of a new financial system. As part of a security assessment that includes a social engineering task, which of the following tasks should be conducted to demonstrate the BEST means to gain information to use for a report on social vulnerability details about the financial system?
A security consultant is improving the physical security of a sensitive site and takes pictures of the unbranded building to include in the report. Two weeks later, the security consultant misplaces the phone, which only has one hour of charge left on it. The person who finds the phone removes the MicroSD card in an attempt to discover the owner to return it.
The person extracts the following data from the phone and EXIF data from some files:
DCIM Images folder
Audio books folder
Torrentz
My TAX.xls
Consultancy HR Manual.doc
Camera: SM-G950F
Exposure time: 1/60s
Location: 3500 Lacey Road USA
Which of the following BEST describes the security problem?
A recent penetration test identified that a web server has a major vulnerability. The web server hosts a critical shipping application for the company and requires 99.99% availability. Attempts to fix the vulnerability would likely break the application. The shipping application is due to be replaced in the next three months. Which of the following would BEST secure the web server until the replacement web server is ready?
A security manager is determining the best DLP solution for an enterprise. A list of requirements was created to use during the source selection. The security manager wants to confirm a solution exists for the requirements that have been defined. Which of the following should the security manager use?
An organization has established the following controls matrix: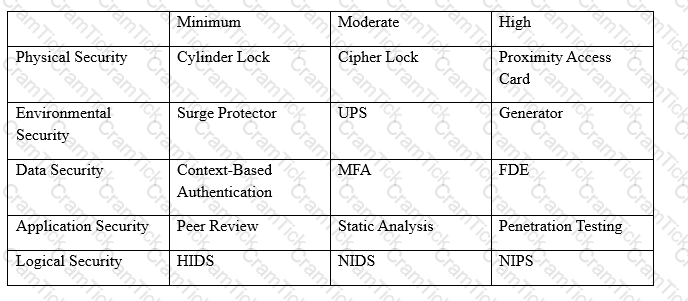
The following control sets have been defined by the organization and are applied in aggregate fashion:
The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
An electric car company hires an IT consulting company to improve the cybersecurity of us vehicles. Which of the following should achieve the BEST long-term result for the company?
A network printer needs Internet access to function. Corporate policy states all devices allowed on the network must be authenticated. Which of the following is the MOST secure method to allow the printer on the network without violating policy?
The director of sales asked the development team for some small changes to increase the usability of an application used by the sales team. Prior security reviews of the code showed no significant vulnerabilities, and since the changes were small, they were given a peer review and then pushed to the live environment. Subsequent vulnerability scans now show numerous flaws that were not present in the previous versions of the code. Which of the following is an SDLC best practice that should have been followed?
A security manager recently categorized an information system. During the categorization effort, the manager determined the loss of integrity of a specific information type would impact business significantly. Based on this, the security manager recommends the implementation of several solutions. Which of the following, when combined, would BEST mitigate this risk? (Select TWO.)
An attacker has discovered an organization's web server is vulnerability to Shellshock. The attack runs the following command on a Linux box against the server:
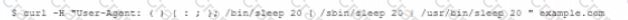
Which of the following BEST describes how to prevent the attack?
A legacy SCADA system is m place in a manufacturing facility to ensure proper facility operations Recent industry reports made available to the security team state similar legacy systems are being used as part of an attack chain in the same industry market Due to the age of these devices security control options are limned Which of the following would BEST provide continuous monitoring for these threats'
A school contracts with a vendor to devise a solution that will enable the school library to lend out tablet computers to students while on site. The tablets must adhere to string security and privacy practices. The school’s key requirements are to:
Which of the following should be configured to BEST meet the requirements? (Choose two.)
A security administrator wants to stand up a NIPS that is multilayered and can incorporate many security technologies into a single platform The product should have diverse capabilities, such as antivirus, VPN, and firewall services, and be able to be updated in a timely manner to meet evolving threats. Which of the following network prevention system types can be used to satisfy the requirements?
Which of the following is an external pressure that causes companies to hire security assessors and penetration testers?
A company is developing requirements for a customized OS build that will be used in an embedded environment. The company procured hardware that is capable of reducing the likelihood of successful buffer overruns while executables are processing. Which of the following capabilities must be included for the OS to take advantage of this critical hardware-based countermeasure?
A development team is testing an in-house-developed application for bugs. During the test, the application crashes several times due to null pointer exceptions. Which of the following tools, if integrated into an IDE during coding, would identify these bugs routinely?
A developer emails the following output to a security administrator for review:
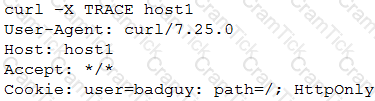
Which of the following tools might the security administrator use to perform further security assessment of this issue?
A security administrator wants to implement two-factor authentication for network switches and routers. The solution should integrate with the company’s RADIUS server, which is used for authentication to the network infrastructure devices. The security administrator implements the following:
The configuration is successfully tested using a software supplicant and enforced across all network devices. Network administrators report they are unable to log onto the network devices because they are not being prompted for the second factor.
Which of the following should be implemented to BEST resolve the issue?
Given the following output from a local PC:
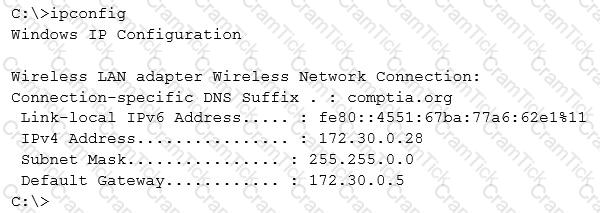
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
A major OS vendor implements an IDE-integrated tool that alerts developers on the use of insecure and deprecated C code functions Using which of the following functions would yield an alert to the developer?
A security analyst is examining threats with the following code function:
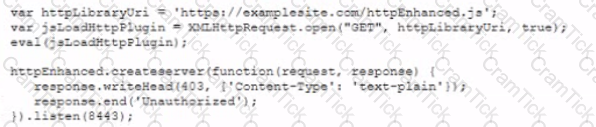
Which of the following threats should the security analyst report1?
During the migration of a company’s human resources application to a PaaS provider, the Chief Privacy Officer (CPO) expresses concern the vendor’s staff may be able to access data within the migrating applications. The application stack includes a multitier architecture and uses commercially available, vendor-supported software packages. Which of the following BEST addresses the CPO’s concerns?
A financial services company wants to migrate its email services from on-premises servers to a cloud-based email solution. The Chief information Security Officer (CISO) must brief board of directors on the potential security concerns related to this migration. The board is concerned about the following.
* Transactions being required by unauthorized individual
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attacker using email to distribute malware and ransom ware.
* Exfiltration of sensitivity company information.
The cloud-based email solution will provide an6-malware, reputation-based scanning, signature-based scanning, and sandboxing. Which of the following is the BEST option to resolve the board’s concerns for this email migration?
As a result of a recent breach a systems administrator is asked to review the security controls in place for an organization's cloud-based environment. The organization runs numerous instances and maintains several separate accounts for managing cloud-based resources. As part of the review the systems administrator finds MFA Is enabled for production-level systems but not staging systems. Which of the following is the primary risk associated with this configuration?
A company's Internet connection is commonly saturated during business hours, affecting Internet availability. The company requires all Internet traffic to be business related After analyzing the traffic over a period of a few hours, the security administrator observes the following:
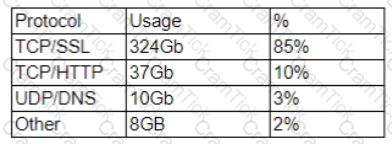
The majority of the IP addresses associated with the TCP/SSL traffic resolve to CDNs Which of the following should the administrator recommend for the CDN traffic to meet the corporate security requirements?
A company uses AD and RADIUS to authenticate VPN and WiFi connections The Chief Information Security Officer (CISO) initiates a project to extend a third-party MFA solution to VPN. During the pilot phase, VPN users successfully get an MFA challenge, however they also get the challenge when connecting to WiFi. which is not desirable Which of the following BEST explains why users are getting the MFA challenge when using WiFi?
A company’s claims processed department has a mobile workforce that receives a large number of email submissions from personal email addresses. An employees recently received an email that approved to be claim form, but it installed malicious software on the employee’s laptop when was opened.
A company is trying to resolve the following issues related to its web servers and Internet presence:
• The company's security rating declined on multiple occasions when it failed to renew a TLS certificate on one or more infrequently used web servers
• The company is running out of public IPs assigned by its ISP
• The company is implementing a WAF. and the WAF vendor charges by back-end hosts to which the WAF routes
Which of the following solutions will help the company mitigate these issues'? (Select TWO).
A Chief Information Security Officer (CISO) is running a test to evaluate the security of the corporate network and attached devices. Which of the following components should be executed by an outside vendor?
Which of the following are the MOST likely vectors for the unauthorized or unintentional inclusion of vulnerable code in a software company’s final software releases? (Choose two.)
Following the most recent patch deployment, a security engineer receives reports that the ERP application is no longer accessible. The security engineer reviews the situation and determines a critical security patch that was applied to the ERP server is the cause. The patch is subsequently backed out Which of the following security controls would be BEST to implement to mitigate the threat caused by the missing patch?
A company is in the process of re-architecting its sensitive system infrastructure to take advantage of on-demand computing through a public cloud provider The system to be migrated is sensitive with respect to latency availability, and integrity The infrastructure team agreed to the following
• Application and middleware servers will migrate to the cloud " Database servers will remain on-site
• Data backup wilt be stored in the cloud
Which of the following solutions would ensure system and security requirements are met?
The information security manager of an e-commerce company receives an alert over the weekend that all the servers in a datacenter have gone offline Upon discussing this situation with the facilities manager, the information security manager learns there was planned electrical maintenance. The information security manager is upset at not being part of the maintenance planning, as this could have resulted in a loss of:
The Chief Information Security Officer (CISO) of a new company is looking for a comprehensive assessment of the company's application services Which of the following would provide the MOST accurate number of weaknesses?
A PaaS provider deployed a new product using a DevOps methodology Because DevOps is used to support both development and production assets inherent separation of duties is limited To ensure compliance with security frameworks that require a specific set of controls relating to separation of duties the organization must design and implement an appropriate compensating control Which of the following would be MOST suitable in this scenario?
A security administrator wants to implement an MDM solution to secure access to company email and files in a BYOD environment. The solution must support the following requirements:
* Company administrators should not have access to employees' personal information.
* A rooted or jailbroken device should not have access to company sensitive information.
Which of the following BEST addresses the associated risks?
Within change management, winch of the following ensures functions are earned out by multiple employees?
Following the merger of two large companies the newly combined security team is overwhelmed by the volume of logs flowing from the IT systems The company's data retention schedule complicates the issue by requiring detailed logs to be collected and available for months. Which of the following designs BEST meets the company's security and retention requirement?
A developer implement the following code snippet.

Which of the following vulnerabilities does the code snippet resolve?
Several days after deploying an MDM for smartphone control, an organization began noticing anomalous behavior across the enterprise Security analysts observed the following:
• Unauthorized certificate issuance
• Access to mutually authenticated resources utilizing valid but unauthorized certificates
• Granted access to internal resources via the SSL VPN
To address the immediate problem security analysts revoked the erroneous certificates. Which of the following describes the MOST likely root cause of the problem and offers a solution?
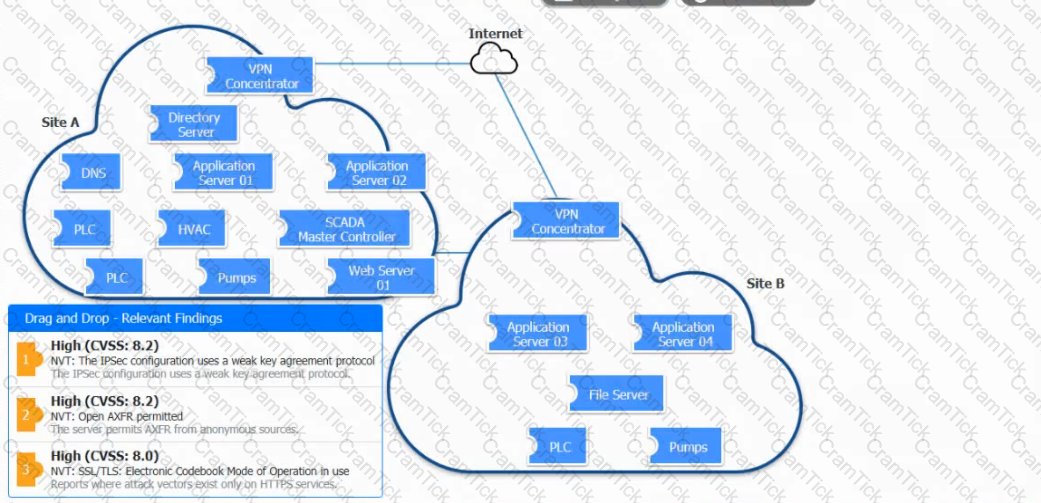
A vulnerability scan with the latest definitions was performed across Sites A and B.
Match each relevant finding to the affected host-After associating the finding with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
A large industrial system’s smart generator monitors the system status and sends alerts to third-party
maintenance personnel when critical failures occur. While reviewing the network logs, the company’s security manager notices the generator’s IP is sending packets to an internal file server’s IP. Which of the following mitigations would be BEST for the security manager to implement while maintaining alerting capabilities?
CompTIA CASP | CAS-003 Questions Answers | CAS-003 Test Prep | CompTIA Advanced Security Practitioner (CASP) Exam Questions PDF | CAS-003 Online Exam | CAS-003 Practice Test | CAS-003 PDF | CAS-003 Test Questions | CAS-003 Study Material | CAS-003 Exam Preparation | CAS-003 Valid Dumps | CAS-003 Real Questions | CompTIA CASP CAS-003 Exam Questions