What is the correct method for ensuring key-sensitive data related to SSNs and credit card numbers cannot be viewed in Dashboard > Data view during investigations?
A customer wants to harden its environment from misconfiguration.
Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
Which three serverless runtimes are supported by Prisma Cloud for vulnerability and compliance scans? (Choose three.)
In WAAS Access control file upload controls, which three file types are supported out of the box? (Choose three.)
Which IAM RQL query would correctly generate an output to view users who enabled console access with both access keys and passwords?
The security auditors need to ensure that given compliance checks are being run on the host. Which option is a valid host compliance policy?
Which IAM Azure RQL query would correctly generate an output to view users who have sufficient permissions to create security groups within Azure AD and create applications?
Which resources can be added in scope while creating a vulnerability policy for continuous integration?
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
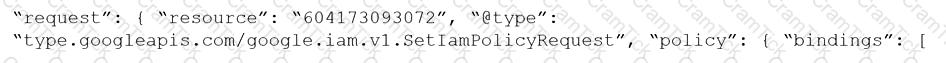
B)
C)
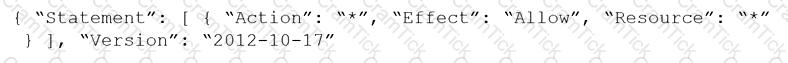
D)

An administrator wants to enforce a rate limit for users not being able to post five (5) .tar.gz files within five (5) seconds.
What does the administrator need to configure?
In which two ways can Prisma Cloud images be retrieved in Prisma Cloud Compute Self-Hosted Edition? (Choose two.)
Which file extension type is supported for Malware scanning in Prisma Cloud Data Security (PCDS)?
A Prisma Cloud administrator is tasked with pulling a report via API. The Prisma Cloud tenant is located on app2.prismacloud.io.
What is the correct API endpoint?
What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon Web Services (AWS) cloud accounts are being used? (Choose two.)
What should be used to associate Prisma Cloud policies with compliance frameworks?
Which two frequency options are available to create a compliance report within the console? (Choose two.)
Creation of a new custom compliance standard that is based on other individual custom compliance standards needs to be automated.
Assuming the necessary data from other standards has been collected, which API order should be used for this new compliance standard?
Which of the below actions would indicate – “The timestamp on the compliance dashboard?
An administrator has added a Cloud account on Prisma Cloud and then deleted it.
What will happen if the deleted account is added back on Prisma Cloud within a 24-hour period?
A Prisma Cloud Administrator needs to enable a Registry Scanning for a registry that stores Windows images. Which of the following statement is correct regarding this process?
A user from an organization is unable to log in to Prisma Cloud Console after having logged in the previous day.
Which area on the Console will provide input on this issue?
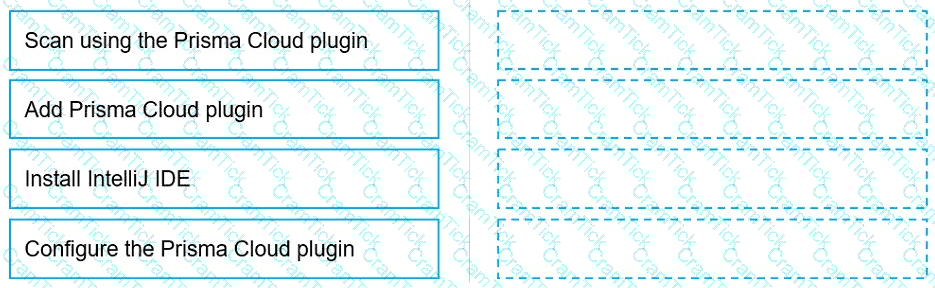
Put the steps involved to configure and scan using the IntelliJ plugin in the correct order.
Given the following RQL:
Which audit event snippet is identified by the RQL?
A)
B)
C)
D)
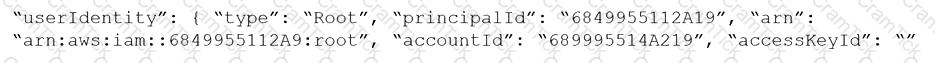
The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely.
Which strategy should the administrator use to achieve this goal?
Which policy type provides information about connections from suspicious IPs in a customer database?
Which resource and policy type are used to calculate AWS Net Effective Permissions? (Choose two.)
A customer's Security Operations Center (SOC) team wants to receive alerts from Prisma Cloud via email once a day about all policies that have a violation, rather than receiving an alert every time a new violation occurs.
Which alert rule configuration meets this requirement?
Which two actions are required in order to use the automated method within Amazon Web Services (AWS) Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose two.)
What is the maximum number of access keys a user can generate in Prisma Cloud with a System Admin role?
Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?
During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in their environment.
Which statement correctly describes the default vulnerability policy?
Which intensity setting for anomaly alerts is used for the measurement of 100 events over 30 days?
The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
An administrator has a requirement to ingest all Console and Defender logs to Splunk.
Which option will satisfy this requirement in Prisma Cloud Compute?
The security team wants to enable the “block” option under compliance checks on the host.
What effect will this option have if it violates the compliance check?
Prisma Cloud Compute has been installed on Onebox. After Prisma Cloud Console has been accessed. Defender is disconnected and keeps returning the error "No console connectivity" in the logs.
What could be causing the disconnection between Console and Defender in this scenario?
A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer’s request?
In Prisma Cloud for Azure Net Effective Permissions Calculation, the following Azure permission levels are supported by which three permissions? (Choose three).
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
A container and image compliance rule has been configured by enabling all checks; however, upon review, the container's compliance view reveals only the entries in the image below.
What is the appropriate action to take next?
A customer has configured the JIT, and the user created by the process is trying to log in to the Prisma Cloud console. The user encounters the following error message:
What is the reason for the error message?
Which alert deposition severity must be chosen to generate low and high severity alerts in the Anomaly settings when user wants to report on an unknown browser and OS, impossible time travel, or both due to account hijacking attempts?
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company’s AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually.
The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts.
Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
In which Console menu would an administrator verify whether a custom compliance check is failing or passing?
Web-Application and API Security (WAAS) provides protection for which two protocols? (Choose two.)
Which Prisma Cloud policy type detects port scanning activities in a customer environment?
Which two bot categories belong to unknown bots under Web-Application and API Security (WAAS) bot protection? (Choose two.)
When would a policy apply if the policy is set under Defend > Vulnerability > Images > Deployed?
An administrator for Prisma Cloud needs to obtain a graphical view to monitor all connections, including connections across hosts and connections to any configured network objects.
Which setting does the administrator enable or configure to accomplish this task?
A customer has Defenders connected to Prisma Cloud Enterprise. The Defenders are deployed as a DaemonSet in OpenShift.
How should the administrator get a report of vulnerabilities on hosts?
Which action would be applicable after enabling anomalous compute provisioning?
While writing a custom RQL with array objects in the investigate page, which type of auto-suggestion a user can leverage?
A customer wants to monitor its Amazon Web Services (AWS) accounts via Prisma Cloud, but only needs the resource configuration to be monitored at present.
Which two pieces of information are needed to onboard this account? (Choose two.)
A customer has a development environment with 50 connected Defenders. A maintenance window is set for Monday to upgrade 30 stand-alone Defenders in the development environment, but there is no maintenance window available until Sunday to upgrade the remaining 20 stand-alone Defenders.
Which recommended action manages this situation?
An organization wants to be notified immediately to any “High Severity” alerts for the account group “Clinical Trials” via Slack.
Which option shows the steps the organization can use to achieve this goal?


