in a NAS environment, which file system provides a public or open variation of the Server Message Block (SMB) protocol and uses the TCP/IP protocol?
In a modern data center environment, which mechanism secures internal assets while allowing Internet-based access to selected resources?
What does using a service-focused approach provide to managing the storage infrastructure?
What is the functionality of the application server in a Mobile Device Management?
What is true about scale-out NAS storage architecture? (First Choose Correct option and give detailed explanation delltechnologies.com)
Which product enables employees to enroll their mobile devices in an enterprise environment and ensures secure access from the devices to the enterprise resources?
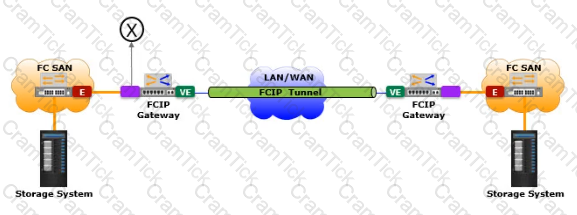
Based on the exhibit, what does the "X" represent in the FCIP tunnel configuration?
What is a function of the metadata service in an object-based storage device (OSD)?
What is a key benefit for deploying a remote data protection and recovery solution in a data center environment?
What triggers an appropriate workflow upon receiving a service provisioning or management request?
Refer to the Exhibit:
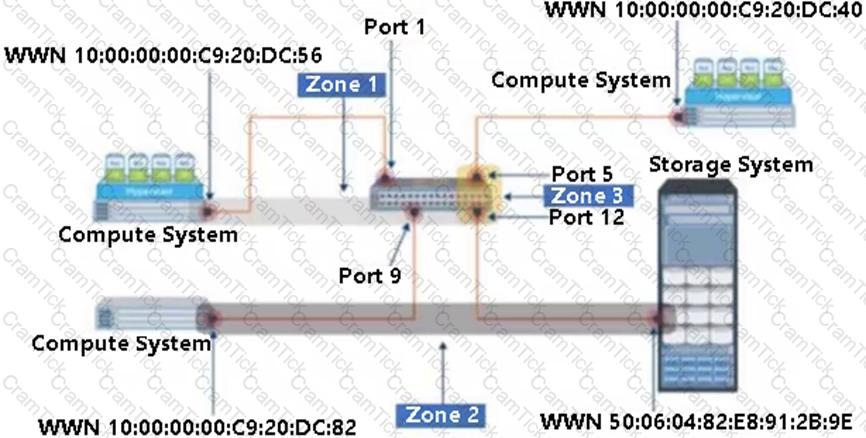
Select the option that represents the three Zone Types for each of the labeled zones.
Which Dell EMC product is a disk-based backup and recovery solution that provides inherent source-based deduplication?
What type of backup method allows a client to be installed in a VM that sends the data to the backup device?
Which layer of the OSI reference model is responsible for logical addressing and routing?
What kind of ML explicitly requires splitting the data into training and testing datasets before running an algorithm against that data?
Which backup component sends metadata and tracking information about each backup to the system that maintains this information?
Refer to the Exhibit:
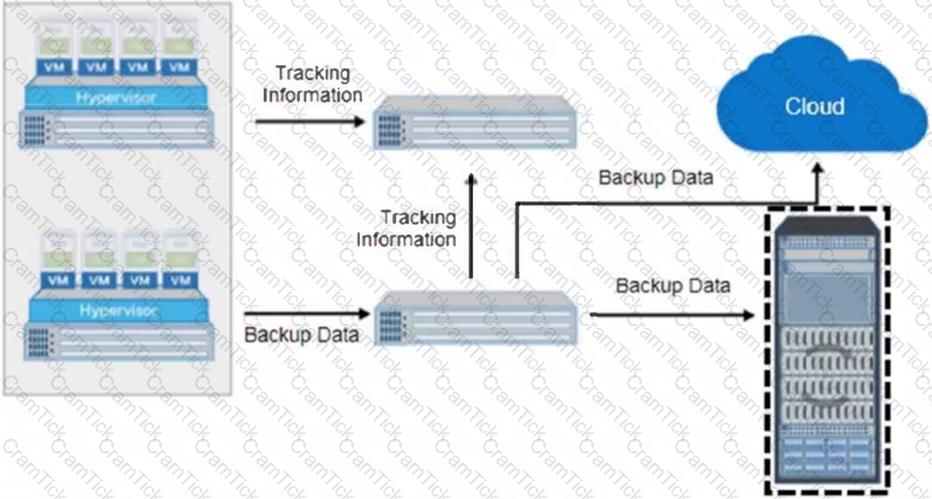
What is the name of the selected backup architecture component?
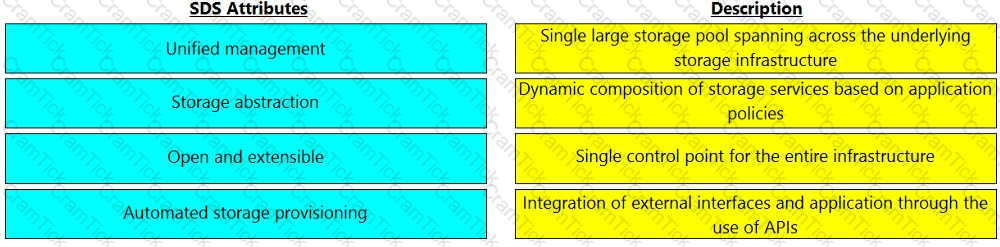
Match the software-defined storage (SDS) attributes with their respective description.
An organization is planning to adopt pre integrated systems to deploy compute, network, storage, and management functions as a single engineered solution.
Which approach should the organization adopt?
What type of technology is used in SSD devices to provide non-volatile data storage?
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 2 occurs on a particular week as follows:
Monday = 10 AM to 12 PM Wednesday = 4 PM to 9 PM Thursday = 4 PM to 7 PM
Friday = 3 PM to 6 PM Saturday = 9 AM to 1 PM
What is the availability of Port 2 in that week?
A company finance department needs 250 GB of storage for their business applications. A LUN is created with 250 GB, and RAID 1 protection. The LUN is configured to support application I/O performance.
If storage cost is $2 per GB, what is the chargeback amount to the department for application storage?
Which file system provides a streaming interface using the MapReduce framework?
What is an advantage of deploying intelligent storage systems in the data center?
How should vulnerabilities be managed in a data center environment? (Verify the Correct answer from Associate - Information Storage and Management Study Manual from dellemc.com)
Which security mechanism ensures secure access to internal assets while enabling Internet-based access to selected resources?
An organization wants to replicate data over a public network to a cloud.
Which security control mechanism helps to secure the data during replication?
Which network performance attribute is achieved when using flow control in FOP?
What is a benefit of using a Scale-Out NAS system vs. general purpose file servers?
A backup administrator has defined a backup policy The policy requires full backups to be performed at 9 PM every Sunday and incremental backups performed at 9 PM the remaining days If files were accidentally deleted Thursday morning, how many backup copies are required to restore the files?
Which three parameters define information availability in a modern data center environment?
A company's assets are continuously under attack.
To deploy a security control mechanism to protect these assets, what should be considered?
DCA-ISM |


