(A developer needs to integrate a trigger to execute an action in a database. Which of the following SQL snippets is a correct use of a trigger?)
(A database administrator realizes that certain data was not captured correctly when it was imported. Which of the following commands should the administrator use to fix the issue?)
A database's daily backup failed. Previous backups were completed successfully. Which of the following should the database administrator examine first to troubleshoot the issue?
(A financial institution is running a database that contains PII. Database administrators need to provide table access to junior developers. Which of the following is the best option?)
(A shared folder can only be accessed by authorized users. Which of the following policies was applied in this scenario?)
Which of the following services is responsible for assigning, managing, and reclaiming IP addresses on a TCP/IP-based network?
(A database administrator wants users to be able to access resources remotely from home. Which of the following best describes how the administrator can enable this access without compromising the security of the stored data?)
A database administrator is new to a company and wants to create a document that illustrates the interaction between tables. Which of the following should the administrator create?
(Evidence from logs shows multiple ongoing attempts to connect with a default account that was disabled. Which of the following best describes this type of attack?)
A database administrator is concerned about transactions in case the system fails. Which of the following properties addresses this concern?
A business analyst is using a client table and an invoice table to create a database view that shows clients who have not made purchases yet. Which of the following joins is most appropriate for the analyst to use to create this database view?
A database professional is considering denormalizing a database. Which of the following documents should be used to analyze the database's structure?
(Which of the following is used to store product quantities in a table while ensuring the minimal amount of storage is consumed?)
A company is launching a proof-of-concept, cloud-based application. One of the requirements is to select a database engine that will allow administrators to perform quick and simple queries on unstructured data. Which of the following would be best suited for this task?
Which of the following firewall types allows an administrator to control traffic and make decisions based on factors such as connection information and data flow communications?
A programmer wants to configure a database to only allow read or write access when requests are coming from specific IP addresses. Which of the following can be used to configure IP addresses to allow access to the database?
Which of the following is the best way to migrate a large data load from one table to another, considering total time and blocking?
(Which of the following is the purpose of including a COLLATE clause in a column definition?)
A database administrator needs a tool to document and explain the relationships between data in an organization's database. Which of the following is the best tool to accomplish this task?
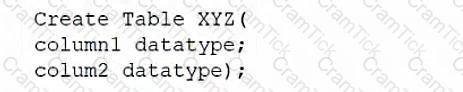
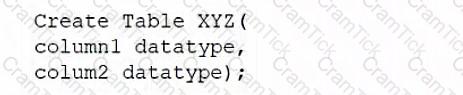
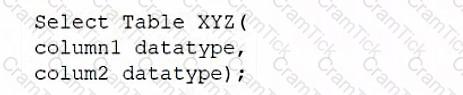
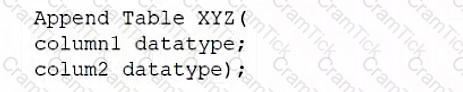
A database administrator would like to create a table named XYZ. Which of the following queries should the database administrator use to create the table?
A)
B)
C)
D)
Following a security breach, a database administrator needs to ensure users cannot change data unless a request is approved by the management team. Which of the following principles addresses this issue?
(A business analyst queries the same few tables every quarter and does not want to write new SQL code every time. Which of the following would best support the business analyst’s needs and allow the database administrator to optimize disk space?)
A database administrator needs to provide access to data from two different tables to multiple group users in order to facilitate ongoing reporting. However, some columns in each table are restricted, and users should not be able to see the values in these columns.
Which of the following is the best action for the administrator to take?


