In a Windows environment using AD machine authentication, how does FortiAuthenticator ensure that a previously authenticated device is maintaining its network access once the device resumes operating after sleep or hibernation?
You are deploying a FortiSwitch device managed by FortiGate in a secure network environment. To ensure accurate communication, you must identify which protocols are required for communication and control between FortiGate and FortiSwitch.
Which three protocols are used by FortiGate to manage and control FortiSwitch devices? (Choose three.)
Connectivity tests are being performed on a newly configured VLAN. The VLAN is configured on a FortiSwitch device that is managed by FortiGate. During testing, it is observed that devices
within the VLAN can successfully ping FortiGate. and FortiGate can also ping these devices.
Inter-VLAN communication is working as expected. However, devices within the same VLAN are unable to communicate with each other.
What could be causing this issue?
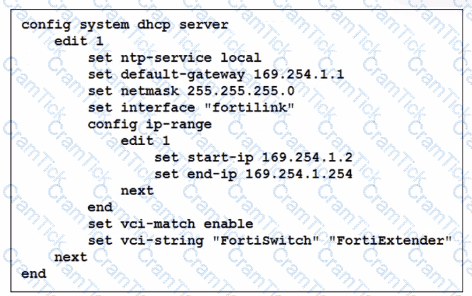
You've configured the FortiLink interface, and the DHCP server is enabled by default. The resulting DHCP server settings are shown in the exhibit. What is the role of the vci-string setting in this configuration?
Which VLAN is used by FortiGate to place devices that fail to match any configured NAC policies? CRSPAN
APs have been manually configured to connect to FortiGate over an IPsec network, and FortiGate successfully detects and authorizes them. However, the APs remain unmanaged because FortiGate is unable to establish a CAPWAP tunnel with them.
What configuration change can resolve this issue and enable FortiGate to establish the CAPWAP tunnel over the IPsec connection?
Refer to the exhibits.
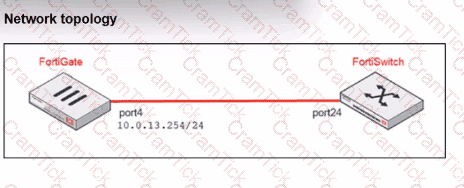

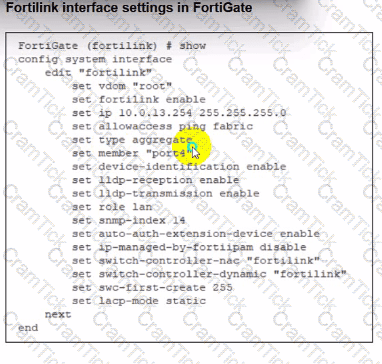
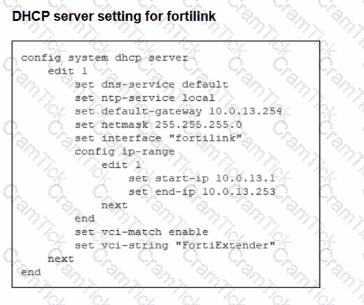
You are adding a new FortiSwitch to FortiGate for management. All necessary settings have been configured on FortiGate, but FortiSwitch remains offline. The cabling has been verified and is correctly connected.
Which misconfiguration might be preventing FortiGate from detecting FortiSwitch?
Which FortiGuard licenses are required for FortiLink device detection to enable device identification and vulnerability detection?


