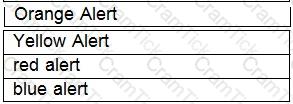
Drag the warning level of the network security emergency response on the left into the box on the right, and arrange it from top to bottom in order of severity.[fill in the blank]*
DES is a stream encryption algorithm, because the cipher capacity is only 56 bits, so it is not enough to deal with the weakness of insufficient security, and later 3DES was proposed.
In the TCP/P protocol core, which of the following protocols works at the application layer? ( )[Multiple choice]*
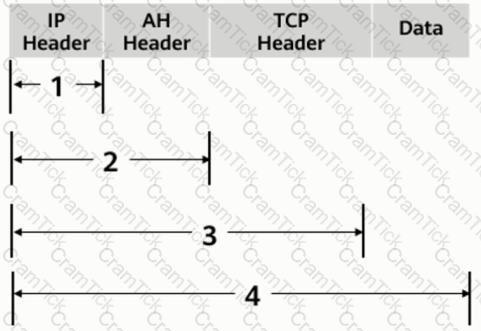
As shown in the figure, what is the range of the AH protocol authentication range in transmission mode?
Please match the following information security risks to information security incidents one by one.[fill in the blank]*
physical security riskEnterprise server permissions are loosely set
Information Security Management RiskInfected Panda Burning Incense
Information Access RiskFire destroyed equipment in computer room
application riskTalk to people about leaking company secrets