On a WLAN, the HSB service sets up an HSB channel between two devices that back up each other, maintains the channel status, and backs up data. Which of the following can HSB back up in real time?
Based on IGMP snooping, IGMP snooping proxy enables a switch to act as a substitute for an upstream Layer 3 device to send IGMP Query messages to downstream hosts, and also to act as a substitute for downstream hosts to send IGMP Report/Leave messages to an upstream device. As such, this function conserves bandwidth between the upstream device and the local device.
VRRP is implemented based on thepriority and preemption functionsof VRRP routers.Which of the following statements is false about the VRRP solution?
A local router runs IS-IS and its command output is shown in the following figure. Which of the following statements is true?
IGMP group entries play an important role in multicast forwarding. An administrator runs a command to view information about a multicast entry. The information is as follows:
sql
Copy
Interface group report information
Vlanif100(10.1.6.2):
Total 1 IGMP Group reported
Group Address Last Reporter Uptime Expires
225.1.1.2 10.1.6.10 00:02:04 00:01:17
Given this, which of the following statements are true?
By default, a router interface sends PIM Hello messages at an interval of __________ seconds.
OSPF routers exchange Hello packets to establish neighbor relationships. The Hello packet sending modes vary by network type. On which of the following types of networks are Hello packets multicast?
In a route-policy, which of the following BGP attributes can be used in apply clauses?
A forwarding information database (FIB) can directly guide packet forwarding on a router.
STAs stay on different subnets before and after Layer 3 roaming. To enable the STAs to access the original network after roaming, network engineers need to configure user traffic to be forwarded to the original subnet over a CAPWAP tunnel.
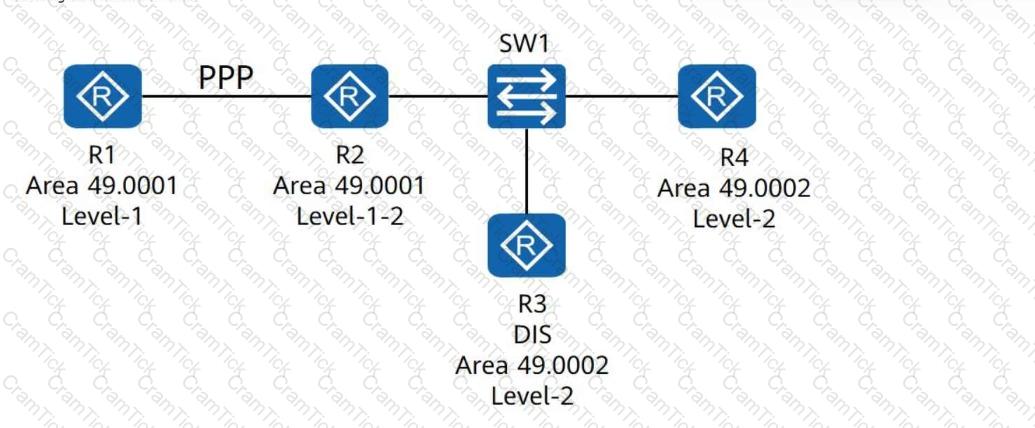
Four routers run IS-IS and have established adjacencies. The area IDs and router levels are marked in the following figure. R1 and R2 are connected through a PPP link, and R3 is the DIS. Which of the following statements are true?
Which of the following configurations are not mandatory when an administrator configures VRRP?
According to BGP route selection rules, the route with the higher Local_Pref is preferred.
A wide area network (WAN) is a remote network that connects local area networks (LANs) or metropolitan area networks (MANs) in different areas for communication purposes. It is typically used to interconnect campus networks or data center networks.
Depending on the type of algorithms used, routing protocols are classified into distance-vector protocols and link-state protocols. Which of the following routing protocols are link-state protocols?
When receiving a packet, a Huawei router matches the packet against ACL rules. The default ACL matching order used by the Huawei router is.
On an STP network, only the designated port processes inferior BPDUs. On an RSTP network, a port with any role processes inferior BPDUs.
On a WLAN, engineers can use the VLAN pool mechanism to assign access users to different VLANs, which helps reduce the number of broadcast domains and improve network performance. VLAN pools support two VLAN assignment algorithms: even and hash. Drag the advantages and disadvantages to the two algorithms.(Token is reusable)
When multiple access channels are set for the same access requirement, the insecure access channels are not used and secure access channels are selected in normal cases. Which of the following are secure access channels?
In addition to numerous normal service packets, the CPUs of devices on a network may also receive large numbers of attack packets. To ensure that the CPUs can properly respond to normal services, the devices provide the local attack defense function.
Which of the following statements are true about this function?(Select all that apply)
Which of the following statement regarding the display ospf peer command output is true?
On an OSPF network, one router with P2P as the network type is directly connected to another router with P2MP as the network type. If the Hello intervals on the two routers are changed to be the same, neighbor relationship establishment and LSDB synchronization are not affected.
After BGP initiates a TCP connection, the ConnectRetry timer is disabled if the TCP connection is successfully established. If the TCP connection fails to be established, the device tries to reestablish the TCP connection when the ConnectRetry timer expires.
Four routers run ISIS and have established adjacencies. The area IDs and router levels are marked in the following figure. If route leaking is configured on R3, which of the following is the cost of the route from R4 to 10.0.2.2/32?
By default, some security zones are created when Huawei firewalls are enabled. Which of the following security zones is created by users?
Which of the following statements regarding the firewall zone security level is false?
A campus network uses OSPF for network communication. The display ospf peer command is run on a router, and the command output is as follows:
vbnet
Copy
Edit
OSPF Process 1 with Router ID 10.0.2.2
Area 0.0.0.0 interface 10.0.235.2 (GigabitEthernet0/0/1)'s neighbors
Router ID: 10.0.5.5 Address: 10.0.235.5
State: Full Mode: Nbr is Master Priority: 1
DR: 10.0.235.5 BDR: 10.0.235.3 MTU: 0
Dead timer due in 40 sec
Area 0.0.0.0 interface 10.0.24.2 (Serial1/0/1)'s neighbors
Router ID: 10.0.4.4 Address: 10.0.24.4
State: Full Mode: Nbr is Master Priority: 1
DR: None BDR: None MTU: 0
Dead timer due in 35 sec
Which of the following statements are true about the device?
When configuring an ACL on a router, you can specify a unique number or name to identify the ACL. Once a named ACL is created, it cannot be modified. You can only delete the named ACL and reconfigure it.
This configuration is part of RTA configuration. Which of the following statements regarding the configuration are true?
[RTA] ospf 100
[RTA-ospf-100]silent-interface GigabitEthernet 1/0/0
A network entity title consists of an area address and a system ID. It is a special NSAP (the SEL has a fixed value of 00) and is mainly used for route calculation.
In special scenarios, when advertising routes to an IBGP peer, a BGP device needs to set the next hop to its IP address to prevent blackhole routes. Which of the following commands can be run in this case?
Which of the following statements regarding the display bgp routing-table command output is true?
As shown in the figure, data traffic is forwarded in tunnel mode along the path of STA -> HAP -> HAC -> upper-layer network before roaming. What is the flow direction of data traffic after Layer 3 roaming?
The typical characteristics of the AI era are that it focuses on data, explores data value, and improves AI efficiency. Therefore, the core requirement of AI for data center networks is speed, meaning low latency.
Which of the following statements are true about theLocal_Prefattribute in BGP? (Choose all that apply)
A route-policy consists of one or more nodes. What is the maximum number of nodes in a route-policy?
On the OSPF network shown in the figure, an adjacency has been established between R1 and R2. An engineer configures the commands in the figure on R2. In this case, which of the following routing entries may exist in the routing table of R2?
An engineer sets the CAPWAP heartbeat detection interval to 20 of the active link before an active/standby switchover occurs?
On aBGP network, aroute-policycan be used to modify route attributes. Which of the following statements isfalseaboutroute-policies?
Which of the following attributes cannot be directly referenced in an apply clause of a route-policy?
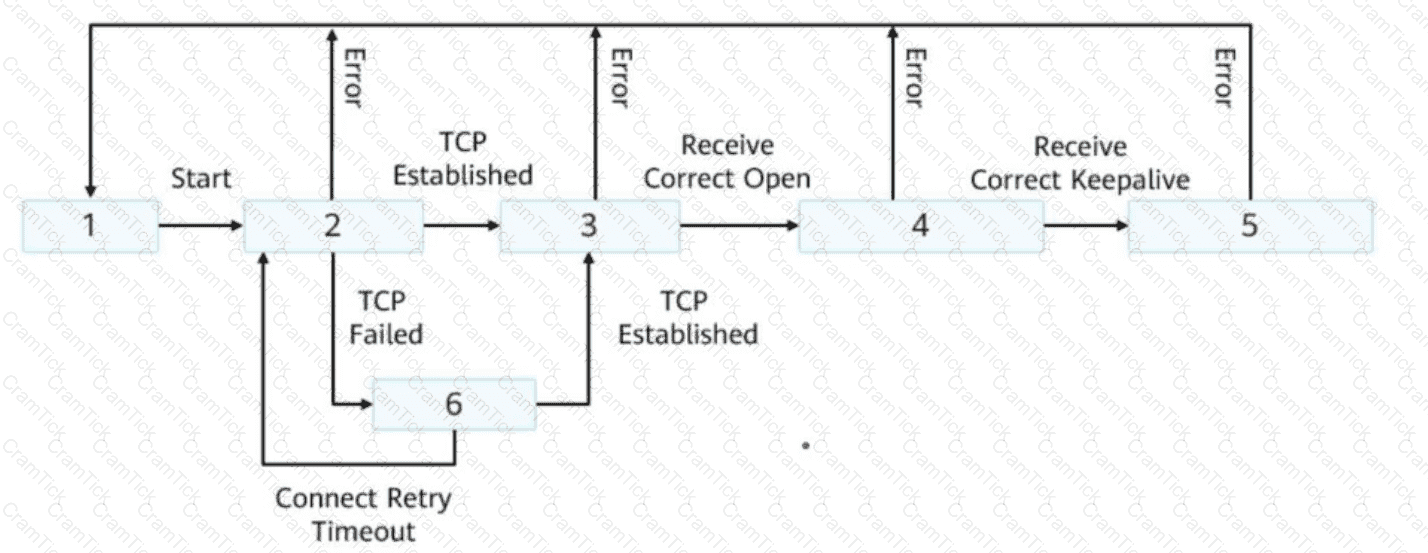
The following figure shows the BGP state switching mechanism. Drag the following BGP states to the corresponding sequence numbers.

On an IS-IS network, the length and components of aNETare the same as those of anNSAP. Which of the followingNETfields is used to uniquely identify a host or router in an area?
On a network, each router has a local core routing table and protocol routing tables. A routing entry in the local core routing table has multiple key fields. Which of the following are included?
OSPF has multiple types of routes with varying priorities. Which of the following types of routes has the lowest priority when they have the same prefix?
There are two BFD operating modes. In_______mode, the local end sends BFD Control packets at specified intervals, and the remote end checks whether the local end periodically sends BFD Control packets. (Use lowercase letters.)
To prevent loops on anSTP network, after adesignated portis elected, it mustwait for a long timeand can forward packetsonly after the status of all ports on the entire network is determined. To solve this problem,RSTP uses the P/A mechanismto speed up thedownstream port's transition to the Forwarding state.
On an IS-IS network, each router can generate LSPs. Which of the following events trigger the generation of a new LSP?
See the following figure. RTA, RTB, RTC, and RTD are in the same AS and establish IBGP peer relationships through direct links. RTB an RTC are route reflectors (RRs), RTA and RTC are the RR clients of RTB, and RTB and RTD are the RR clients of RTC. If RTA advertises the route 10.1.1.0/24 to the BGP process, the Originator ID of the BGP route received by RTD is------------------.
On an RSTP network, if a port receives an RST BPDU and finds that its buffered RST BPDU is superior to the received RST BPDU, the port discards the received RST BPDU without responding.
On an OSPF network, an IR in area 0 must be a BR, but an ASBR may not be an ABR.
During the DHCP interaction process, the DHCP server and client exchange various types of packets. Which of the following packets is not sent from the client to the server?
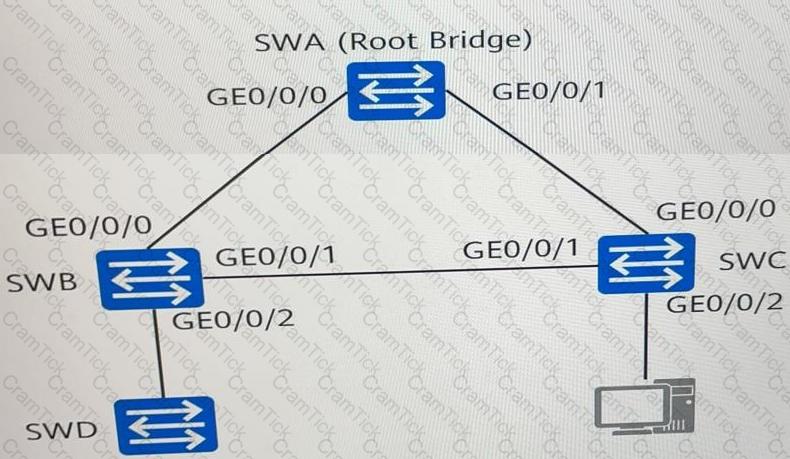
As shown in the figure, SWA, SWB, SWC, and SWD run the Rapid Spanning Tree Protocol (RSTP). Which of the following statements are true?
On an RSTP network, port priorities may be compared during root port or designated port election. Which of the following values is the default priority of a port on a Huawei switch?
On a broadcast IS-IS network, a DIS needs to be elected to create and update pseudonodes. Which of the following values is the default DIS priority of an IS-IS interface?
On an IS-IS network, routers send LSPs to exchange link state information. LSPs are classified into Level-1 LSPs and Level-2 LSPs and have the same format. Which of the following parts constitute the LSP ID in an LSP?
On an IS-IS network, each device needs to be configured with anetwork entity title (NET), which consists of three parts, each containing different fields. Which of the following fields are contained in theArea Address part?
A Layer 2 switch supports multiple types of Ethernet interfaces. Similar to a trunk interface, a hybrid interface allows data frames from multiple VLANs to pass through. In addition, you can determine whether data frames from a VLAN sent out from a hybrid interface are tagged or untagged.
On an OSPF network, if the network type isNBMA, a router unicasts all protocol packets; if the network type isbroadcast, a router multicasts all protocol packets.
The Internet Assigned Numbers Authority (IANA) allocates Class D addresses to IPv4 multicast. An IPv4 address is 32 bits long, and the four most significant bits of a Class D address are 1110.
During BGP route summarization configuration, the keyword can be used to suppress all specific routes so that only the summary route is advertised. The summary route carries the Atomic-aggregate attribute rather than the community attributes of specific routes.
A router uses an advanced ACL to filter data. The ACL configuration is shown below. Which of the following statements is false about the configuration?
csharp
CopyEdit
[Huawei] acl 3001
[Huawei-acl-adv-3001] rule permit icmp source 192.168.1.3 0 destination 192.168.2.0 0.0.0.255
On a WLAN, MAC address authentication controls network access rights of a user based on the user's access interface and terminal MAC address.
Which of the following statements is false about MAC address authentication?
During routine O&M, an engineer finds that theHold Timeparameters of two devices are inconsistent. In this case, which of the following situations occurs?
Security policy is the core feature of firewalls. Only valid traffic that complies with security policies can be forwarded by firewalls. Which of the following statements are true about security policy matching rules?
Which of the following statements isfalseabout thesession table mechanismon firewalls?
ACLs are a common matching tool in routing policies. An ACL can be configured on a router to match routes.
An enterprise office network runs OSPF and is divided into multiple OSPF areas. Enterprise network engineers can configure route summarization on ASBRs to reduce the number of inter-area Type 3 LSAs, which in turn reduces the routing table size and improves device resource utilization.
The Origin attribute is used to define the origin of BGP path information. There are three types of Origin attributes. Which of the following lists the Origin attributes in descending order of priority?
A Huawei firewall by default creates security zones named untrust, dmz, _________ and local. (Use Lowercase letters.)
In BGP, the Origin attribute is used to identify the origin of a route. Which of the following statements are true about the Origin attribute?
OSPF networks are classified into four types of networks by link layer protocol. Drag the following link layer protocols to the corresponding network types.(Token is reusable)
On anRSTP network, port roles are optimized to overcome thedisadvantages of STP. Which of the followingport rolesare supported inRSTP?
STP ensures a loop-free network but has a slow network topology convergence speed, affecting communication quality. RSTP has made some improvements based on STP. Which of the following improvements is not included?
As shown in the figure, R1 imports the direct route 10.1.1.0/24 to OSPF. An engineer enables bidirectional route re-advertisement on R2 and R3, and configures the following commands on R3. After the network becomes stable, which of the following is thePrevalue of the route 10.1.1.0/24 in the routing table of R4?
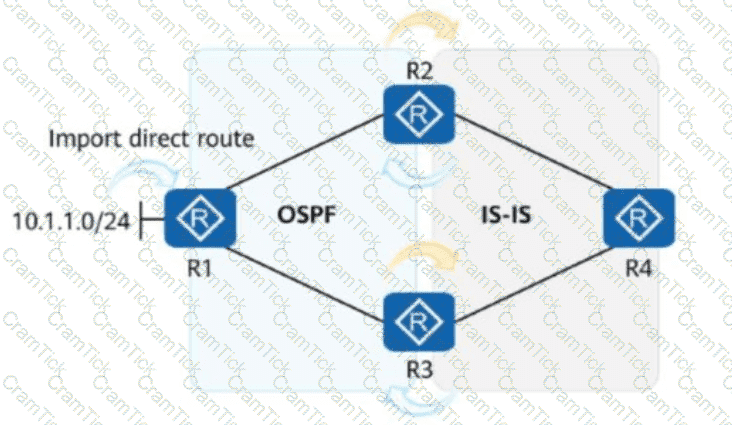
[R3]acl 2000
[R3-acl-basic-2000] rule permit source 10.1.1.0 0
[R3-acl-basic-2000] quit
[R3]route-policy hcip permit node 10
[R3-route-policy-10] if-match acl 2000
[R3-route-policy-10] apply preference 14
[R3-route-policy-10] quit
[R3]ospf 1
[R3-ospf-1] preference ase route-policy hcip
A non-client is an IBGP peer that functions as neither an RR nor a client. A non-client must establish fully meshed connections with the RR and all the other non-clients.
ASPF enables the firewall to support multi-channel protocols such as FTP and to define security policies for complex applications.
If a router ID is configured in both the system via and the BGP view, BGP uses the router ID configured in the BGP view because the BGP view takes precedence over the system view.
The VRID of the VRRP virtual router is 3 and the virtual IP address is 100.1.1.10. What is the virtual MAC address?
Which of the following statements regarding the BGP error display of a router false?
Which of the following TLVs is used by ISIS to describe the IP address of an interface?
Compress the 2001:0DBB:B8:0000:C030:0000:0000:09A0:CDEF address.___________(if the answer contains letters, capitalize them.)
In IPv6, interface IDs can be manually configured, automatically generated by the system, or generated based on the IEEE EUI-64 standard.
After a BGP peer relationship is established between two ends, changing the router ID of one end resets the BGP peer relationship.
After the administrator of an enterprise deploys a DHCP server, employees complain that their clients cannot obtain IP addresses from the DHCP server. Which of the following may cause this problem?
An enterprise uses OSPF to implement network communication. To ensure data validity and security, all authentication modes supported by OSPF are enabled on routers. In this case, interface authentication is preferentially used by the routers.
Route attributes are specific descriptions of routes. BGP route attributes can be classified into four types. Which of the following are well-known discretionary attributes?
After aBGP deviceestablishes apeer relationship, it advertises routes. Which of the following statements aretrueabout BGP route advertisement?
HCIP-Datacom | H12-821_V1.0 Questions Answers | H12-821_V1.0 Test Prep | HCIP-Datacom-Core Technology V1.0 Questions PDF | H12-821_V1.0 Online Exam | H12-821_V1.0 Practice Test | H12-821_V1.0 PDF | H12-821_V1.0 Test Questions | H12-821_V1.0 Study Material | H12-821_V1.0 Exam Preparation | H12-821_V1.0 Valid Dumps | H12-821_V1.0 Real Questions | HCIP-Datacom H12-821_V1.0 Exam Questions


