Prism Central will be installed manually on an AHV cluster.
Which three disk images must be downloaded from the portal for the Prism Central VM? (Choose three.)
An administrator has a Custom backup application that requires a 2TB disk and runs m Windows. Throughput is considerably lower than expected.
The application was installed on a VM with the following configuration:
• FOU vCPUs with one core/vCPU
• 4GB of Memory
• One 50GB vDisk for the Windows installation
• One 2TB vDisk for the application
What is the recommended configuration change to improve throughput?
Which three upgrades should an administrator be able to perform using Lifecycle Management? (Choose Three)
What is the proper sequence to perform a one-click upgrade to a Nutanix cluster?
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements. Not all procedures are valid. Identify any invalid procedures using the drop-down option.

When a configuring a syslog server in Prism Central, what two pieces information are required? (Choose two.)
An administrator needs to relocate an AHV cluster to a new datacenter during a maintenance window. The cluster will use the same IPs in the new datacenter.
Which two steps should be taken to prepare for this task? (Choose two.)
Which two private key types are supported by the Nutanix SSL certificate implementation? (Choose two.)
An administrator is configuring data protection and DR for a multi-tier application. All VMs must be protected at the same time.
What must the administrator do to meet this requirement?
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)
C)

D)

Which AOS process determine if an I/O from a user will be written to OpLog or to an Extent Store?
Refer to the exhibit.

System Non-Root Partition Usage shows a warning or critical alert The administrator needs to change the frequency of checks and alerts to respond more quickly.
Where in Prism Element should the administrator change the frequency of checks and alerts?
An administrator is commissioning a Nutanix Enterprise Cloud. Once the user VMs have been deployed and are running, the administrator finds that VMs on the same host are able to communicate, but are unable to communicate between hosts.
What must be changed to enable full inter-VM communications?
Refer to Exhibit:
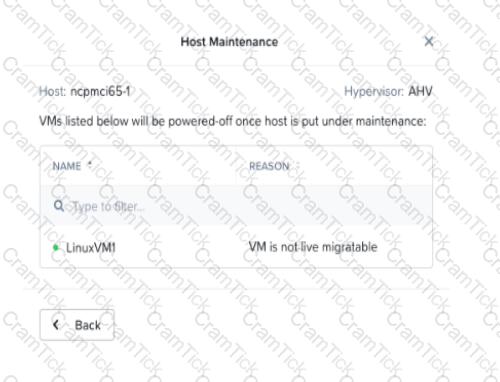
An administrator is trying to put a node into maintenance mode but receives the message shown in the exhibit.
What is a potential reason for this dialog?
A system administrator needs to add more VMs to their Nutanix cluster.
Which two actions should the administrator perform to determine if the current cluster can accommodate the new VMs? (Choose two)
An administrator has set up a local web server accessible to the Nutanix clusters.
Which two steps are required to set up LCM for an environment without Internet access? (Choose two.)
Which capability refers to the storage of VM data on the node where the VM is running and ensure that the read I/O does not have to traverse the network?
An administrator adds a node with older generation processors to an existing AHV cluster with newer generation processors. What is the effect on live migration?
The customer is seeing high memory utilization on a mission critical VM. Users report that the application is unavailable. The guest OS does not support hot add components.
How should the administrator fix this issue?
An administrator is setting up a Nutanix cluster and needs to configure the default VLAN.
Which configuration should the administrator choose?
An administrator has been tasked with increasing security on Nutanix cluster by disabling password authentication when accessing the CVM and AHV hosts and instead moving to key-based SSH,
What is the easiest way for the administrator to meet these needs?
Refer to Exhibit:
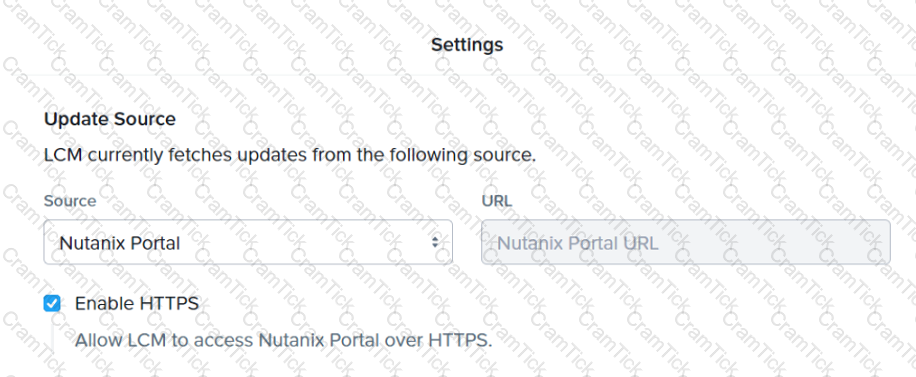
The Update Source for LCM has been configured as shown in the exhibit. Inventory is failing consistently.
What is the likely cause of this issue?
An administrator is preparing to deploy a new application on an AHV cluster, Security requirements dictate that all virtual servers supporting this application must be prevented from communicating with unauthorized hosts.
Which option would achieve this goal?
The Stargate service becomes unavailable on a single CVM on an AHV node. What is used to maintain I/O operations in the cluster?
Which data savings technique utilizes stripes and parity calculation in a Nutanix cluster?
An administrator manages an AHV cluster that is dedicated to a dev/test environment. The administrator receiving complaints from users that they are unable to create new VMs on the cluster.
After the reviewing the cluster, the administrator finds that the memory resources are almost fully utilized, with many VMs over-provisioned on memory.
What option is the most efficient resolution to enable additional VMs to be created?
A newly-hired Nutanix administrator was tasked by the CIO to create a single VM on a test network. The network administrator stated that a native VLAN was used on the Cisco TOR switches with the following parameters:
IP address:172,16.1.2
Network Mask: 255.255.255.0
Default gateway: 172.16.1.1
VLAN:1
The same parameters were used to create a network profile on Nutanix, but the when the VM was on …
What should the Nutanix administrator do to fix this issue?
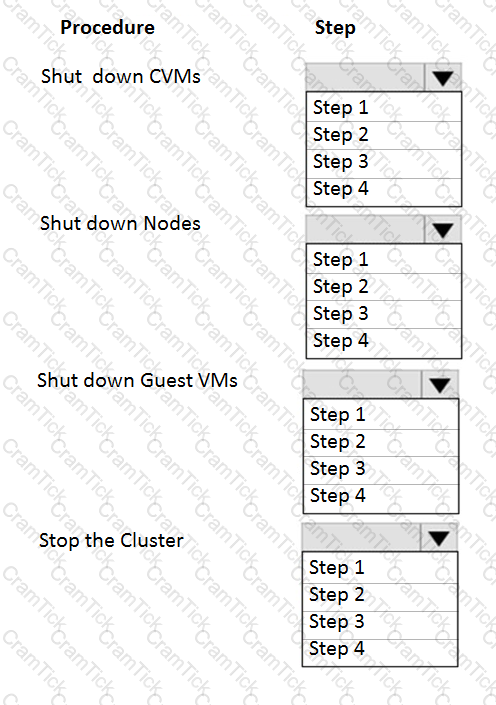
An administrator needs to shut down an AHV cluster to relocate hardware. The administrator upgrades NCC and runs health checks.
Which steps should the administrator perform next?
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements.
When a VM is connected to a Nutanix managed network, when is the IP addressed assigned?
Which best practice should be followed when creating a bond in a Nutanix cluster?
Which scenario would benefit most from Erasure Coding being enabled on a container?
An administrator needs to deploy an application with a large amount of data connected via Nutanix volumes.
Which two actions should the administrator take when designing the Volume Group? (Choose two.)
Refer to the exhibit.
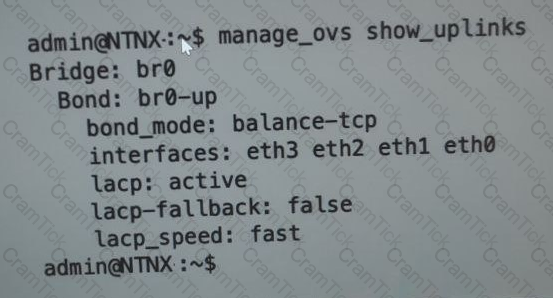
An administrator is adding a new node to a cluster. The node has been imaged to the same versions of AHV and AOS that the cluster running, configured with appropriate IP addresses, and br0-up has been configured the same the existing uplink bonds
When attempting to add the node to the cluster with the Expand Cluster function in Prism , the cluster is unable to find the new node.
Based on the above output from the new node, what is most likely the cause of this issue?
Refer to Exhibit:
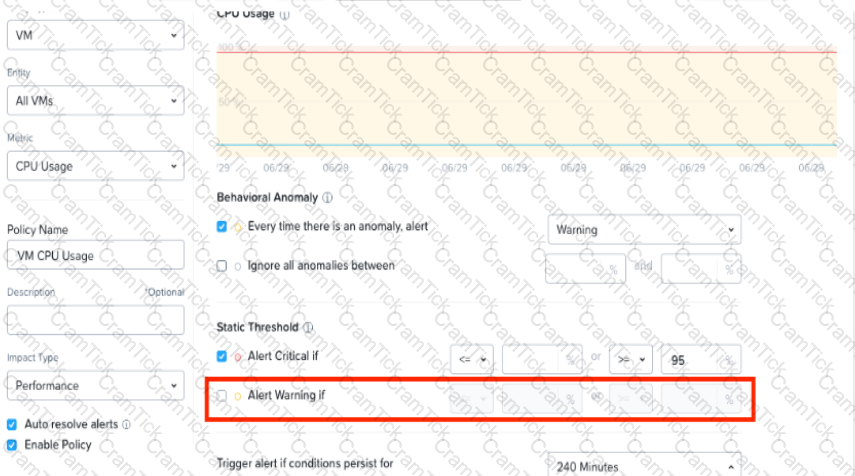
An administrator is trying to create a custom alert policy for all VMs.
Why is the Alert warning if field greyed cut?
An administrator needs to configure Prism to send encrypted messages to a set of recipients.
Which setting must be applied?
An administrator needs to provide access for a user to view real-time performance metric for all VMs on all clusters across the datacenter.
Which method accomplishes this with the least effort and ongoing maintenance?
A VM in a 12-node Nutanix cluster is hosting an application that has specific Physical GPU requirements. Only three nodes in the cluster meet this requirement.
The administrator wants to allow a general workload to be distributed across all nodes in the cluster and must make sure that the node hosting the VM meets its requirements.
How should the administrator perform this task?
A guest VM should be able to tolerate simultaneous failure of two nodes or drives.
What are the minimum requirements for the Nutanix cluster?
An administrator needs to periodically send information about cluster efficiency via email to a set of users.
What should be configured to accomplish this task?
The Linux administration team has requested access rights to any current or future Linux VM in the environment
What entity should be selected when assigning this new role?
An administrator would like to leverage the Reliable Event Logging Protocol (RELP) with their Remote Syslog Server. After completing the configuration, it is observed that RELP logging is not working as expected.
What is the likely cause of this issue?
A customer wants to isolate a group of VMs within their Nutanix environment for security reasons. The customer creates a VM with two NICs to act as a firewall and installs the appropriate software and certificates.
However, no one from the outside can access the application.
What is the likely cause of this problem?
What is the expected operation during node addition when the new node has a different AOS version?
An administrator needs to ensure logs, alerts and information is consistent across clusters that are located in different countries.
Which service needs to be configured?
Upon logging into Prism Central, an administrator notices high cluster latency.
How can the administrator analyze data with the least number of steps or actions?
When installing Nutanix Guest Tools (NGT) on an ESXi-hosted VM, which port should be enabled on the VM to allow communication with the NGT-Controller VM service?
Refer to Exhibit:
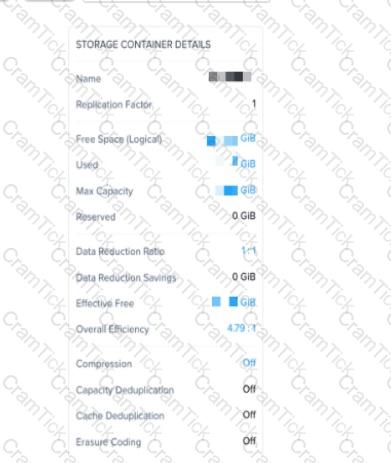
An administrator needs to enable inline deduplication for a pre-existing storage container. When trying to enable deduplication on the storage container. this feature is grayed-out.
What is the reason for this behavior?


