A company has recently migrated their branch office's PA-220S to a centralized Panorama. This Panorama manages a number of PA-7000 Series and PA-5200 Series devices All device group and template configuration is managed solely within Panorama
They notice that commit times have drastically increased for the PA-220S after the migration
What can they do to reduce commit times?
Which version of GlobalProtect supports split tunneling based on destination domain, client process, and HTTP/HTTPS video streaming application?
An administrator Just enabled HA Heartbeat Backup on two devices However, the status on tie firewall's dashboard is showing as down High Availability.
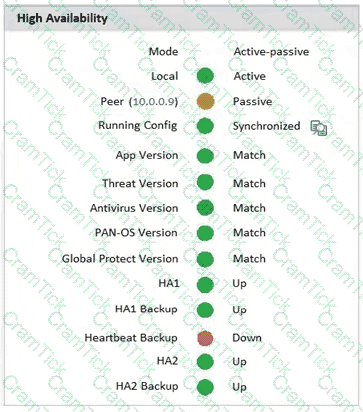
What could an administrator do to troubleshoot the issue?
During the implementation of SSL Forward Proxy decryption, an administrator imports the company's Enterprise Root CA and Intermediate CA certificates onto the firewall. The company's Root and Intermediate CA certificates are also distributed to trusted devices using Group Policy and GlobalProtect. Additional device certificates and/or Subordinate certificates requiring an Enterprise CA chain of trust are signed by the company's Intermediate CA.
Which method should the administrator use when creating Forward Trust and Forward Untrust certificates on the firewall for use with decryption?
A network security engineer is going to enable Zone Protection on several security zones How can the engineer ensure that Zone Protection events appear in the firewall's logs?
A company wants to deploy IPv6 on its network which requires that all company Palo Alto Networks firewalls process IPv6 traffic and to be configured with IPv6 addresses. Which consideration should the engineers take into account when planning to enable IPv6?
What are three prerequisites to enable Credential Phishing Prevention over SSL? (Choose three
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment
Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
Which link is responsible for synchronizing sessions between high availability (HA) peers?
An engineer is troubleshooting a traffic-routing issue.
What is the correct packet-flow sequence?
How can a firewall be set up to automatically block users as soon as they are found to exhibit malicious behavior via a threat log?
Which three multi-factor authentication methods can be used to authenticate access to the firewall? (Choose three.)
An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group.
What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
Where is Palo Alto Networks Device Telemetry data stored on a firewall with a device certificate installed?
In which two scenarios is it necessary to use Proxy IDs when configuring site-to-site VPN tunnels? (Choose two.)
Which two profiles should be configured when sharing tags from threat logs with a User-ID agent? (Choose two.)
View the screenshots
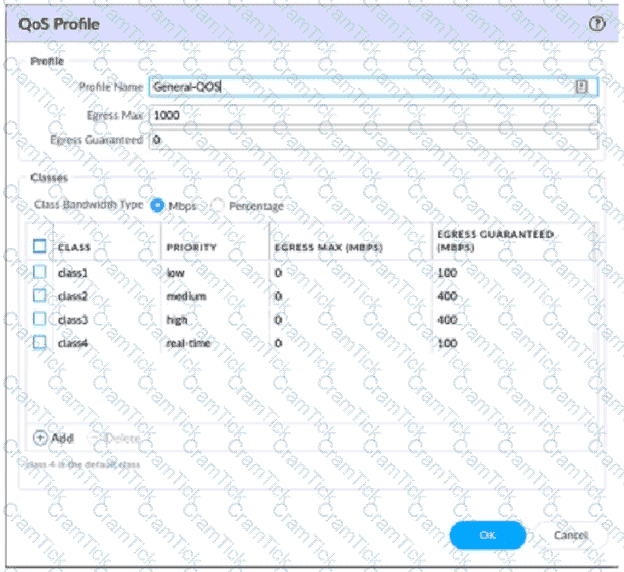
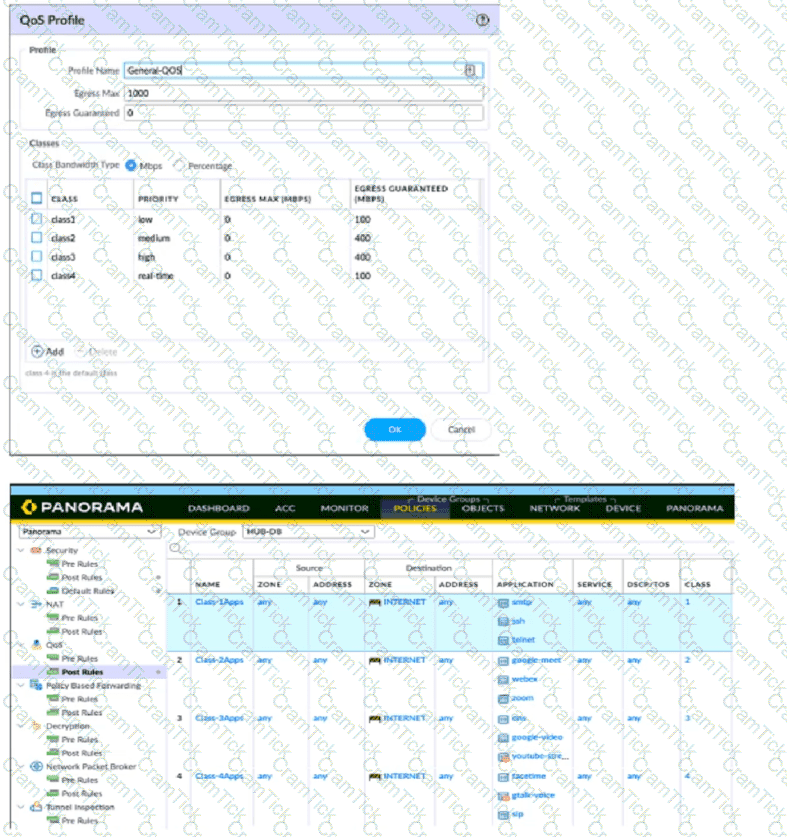
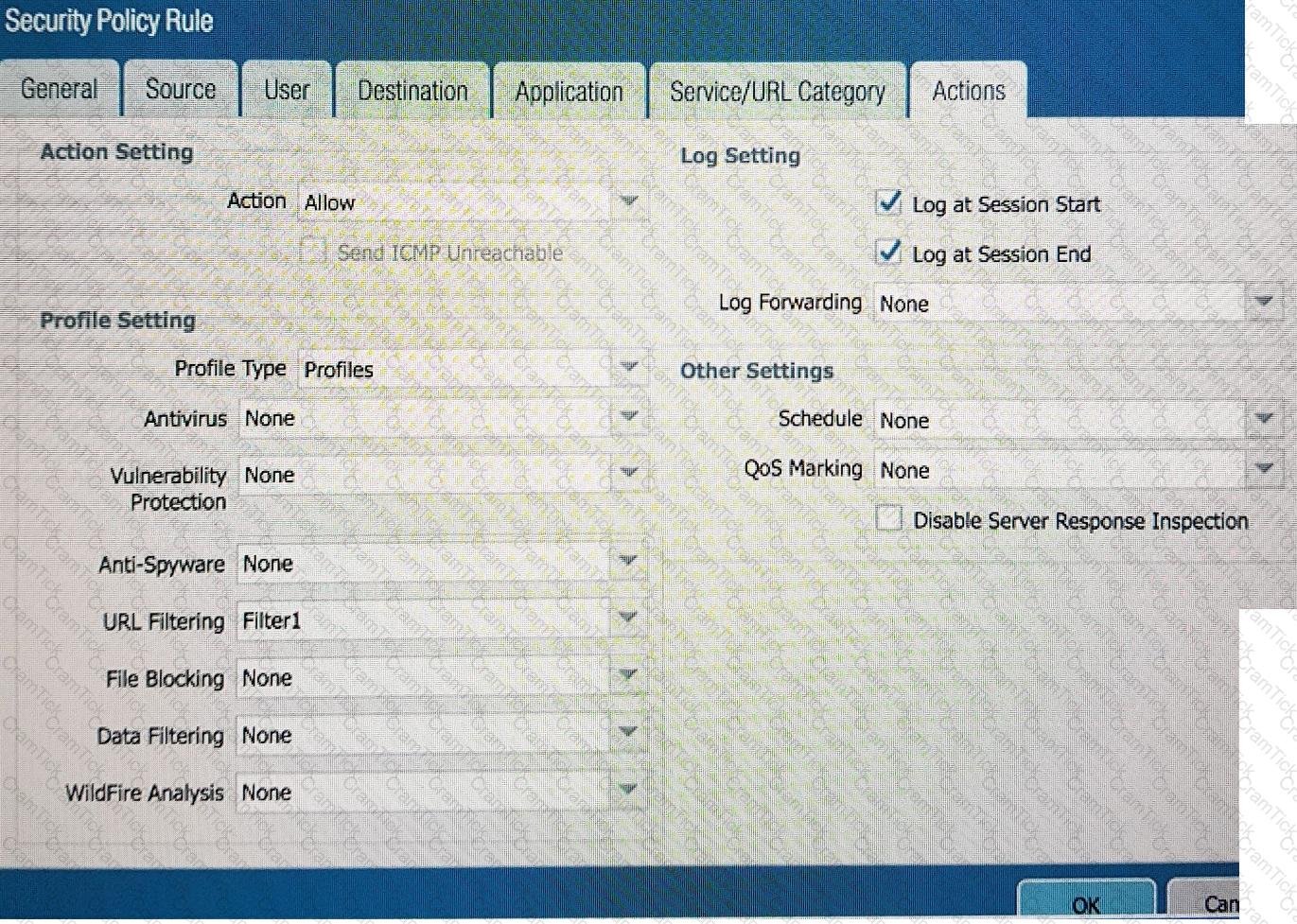
A QoS profile and policy rules are configured as shown. Based on this information which two statements are correct?
An engineer configures a destination NAT policy to allow inbound access to an internal server in the DMZ. The NAT policy is configured with the following values:
- Source zone: Outside and source IP address 1.2.2.2
- Destination zone: Outside and destination IP address 2.2.2.1
The destination NAT policy translates IP address 2.2.2.1 to the real IP address 10.10.10.1 in the DMZ zone.
Which destination IP address and zone should the engineer use to configure the security policy?
An engineer configures a new template stack for a firewall that needs to be deployed. The template stack should consist of four templates arranged according to the diagram

Which template values will be configured on the firewall If each template has an SSL/TLS Service profile configured named Management?
An engineer has been given approval to upgrade their environment to the latest version of PAN-OS. The environment consists of both physical and virtual firewalls, a virtual Panorama, and virtual log collectors. What is the recommended order of operational steps when upgrading?
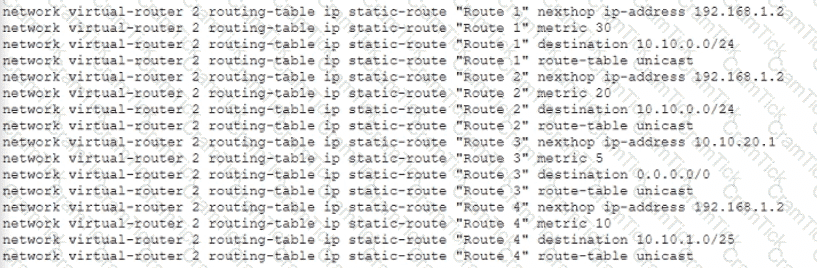
Given the following configuration, which route is used for destination 10 10 0 4?
Which type of zone will allow different virtual systems to communicate with each other?
An administrator needs to assign a specific DNS server to an existing template variable. Where would the administrator go to edit a template variable at the device level?
A company wants to add threat prevention to the network without redesigning the network routing.
What are two best practice deployment modes for the firewall? (Choose two.)
An administrator troubleshoots an issue that causes packet drops.
Which log type will help the engineer verify whether packet buffer protection was activated?
An administrator pushes a new configuration from Panorama to a pair of firewalls that are configured as an active/passive HA pair. Which NGFW receives the configuration from Panorama?
An engineer needs to collect User-ID mappings from the company’s existing proxies. What two methods can be used to pull this data from third-party proxies? (Choose two)
A security engineer wants to upgrade the company's deployed firewalls from PAN-OS 10.1 to 11.0.x to take advantage of the new TLSvl.3 support for management access.
What is the recommended upgrade path procedure from PAN-OS 10.1 to 11.0.x?
An administrator wants to use LDAP, TACACS+, and Kerberos as external authentication services for authenticating users. What should the administrator be aware of regarding the authentication sequence, based on the Authentication profile in the order Kerberos LDAP, and TACACS+?
Refer to the exhibit.
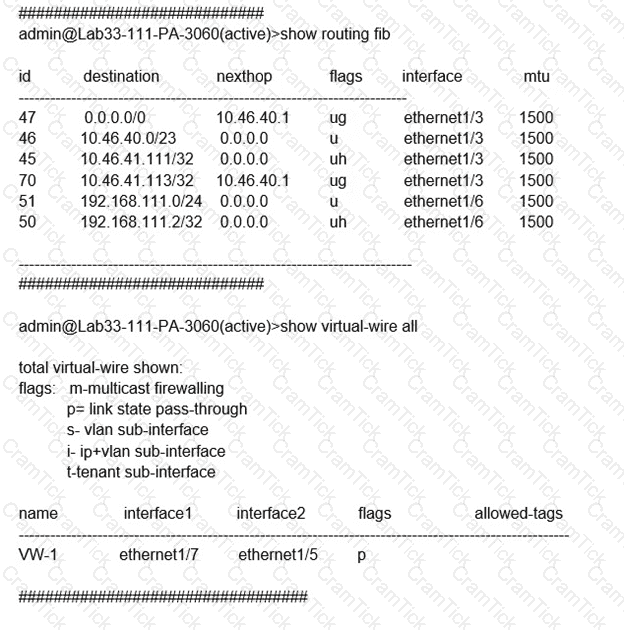
Which will be the egress interface if the traffic's ingress interface is ethernet1/7 sourcing from 192.168.111.3 and to the destination 10.46.41.113?
Which two actions can the administrative role called "vsysadmin" perform? (Choose two)
Why are external zones required to be configured on a Palo Alto Networks NGFW in an environment with multiple virtual systems?
The decision to upgrade PAN-OS has been approved. The engineer begins the process by upgrading the Panorama servers, but gets an error when attempting the install.
When performing an upgrade on Panorama to PAN-OS. what is the potential cause of a failed install?
An administrator is defining protection settings on the Palo Alto Networks NGFW to guard against resource exhaustion. When platform utilization is considered, which steps must the administrator take to configure and apply packet buffer protection?
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed.
What is one way the administrator can meet this requirement?
What does the User-ID agent use to find login and logout events in syslog messages?
The firewall is not downloading IP addresses from MineMeld. Based, on the image, what most likely is wrong?
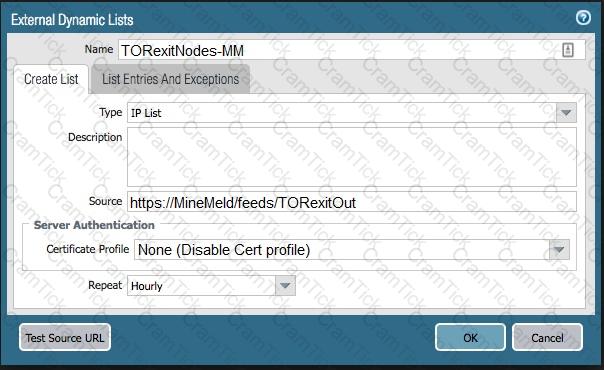
An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the world. Panorama will manage the firewalls.
The firewalls will provide access to mobile users and act as edge locations to on-premises infrastructure. The administrator wants to scale the configuration out quickly and wants all of the firewalls to use the same template configuration.
Which two solutions can the administrator use to scale this configuration? (Choose two.)
Which interface type should a firewall administrator configure as an upstream to the ingress trusted interface when configuring transparent web proxy on a Palo Alto Networks firewall?
Users are intermittently being cut off from local resources whenever they connect to GlobalProtect. After researching, it is determined that this is caused by an incorrect setting on one of the NGFWs. Which action will resolve this issue?
A firewall administrator manages sets of firewalls which have two unique idle timeout values. Datacenter firewalls needs to be set to 20 minutes and BranchOffice firewalls need to be set to 30 minutes. How can the administrator assign these settings through the use of template stacks?
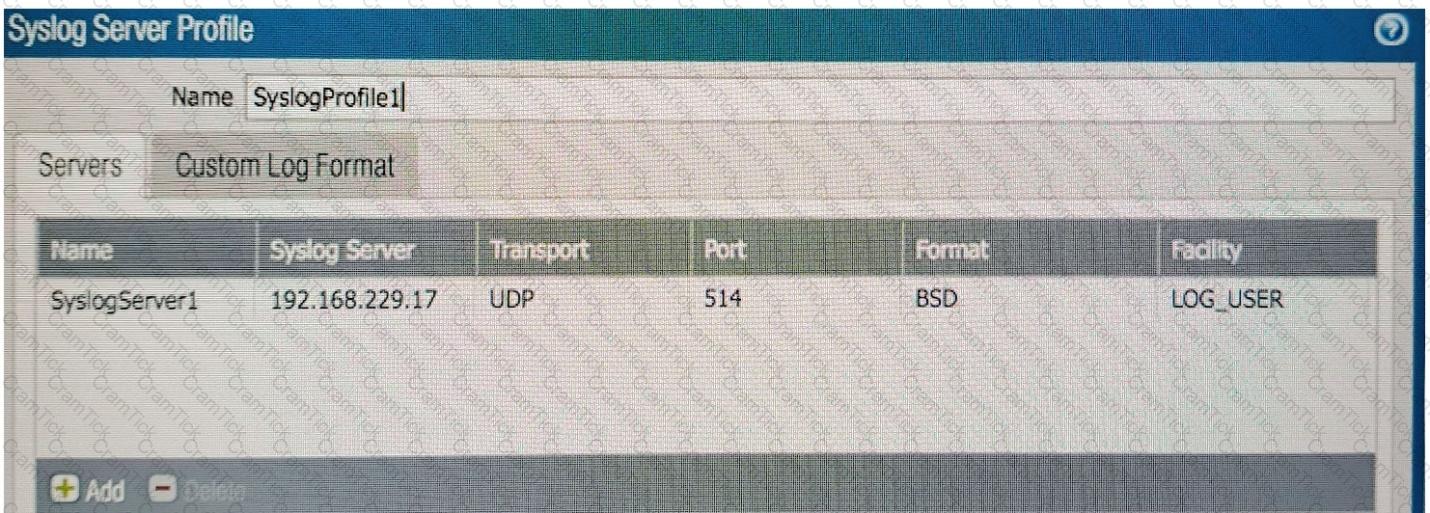
A company is expanding its existing log storage and alerting solutions All company Palo Alto Networks firewalls currently forward logs to Panorama. Which two additional log forwarding methods will PAN-OS support? (Choose two)
Which sessions does Packet Buffer Protection apply to when used on ingress zones to protect against single-session DoS attacks?
An administrator pushes a new configuration from Panorama to a par of firewalls that are configured as an active/passive HA pair. Which NGFW receives the from Panorama?
For company compliance purposes, three new contractors will be working with different device-groups in their hierarchy to deploy policies and objects.
Which type of role-based access is most appropriate for this project?
Refer to the exhibit.
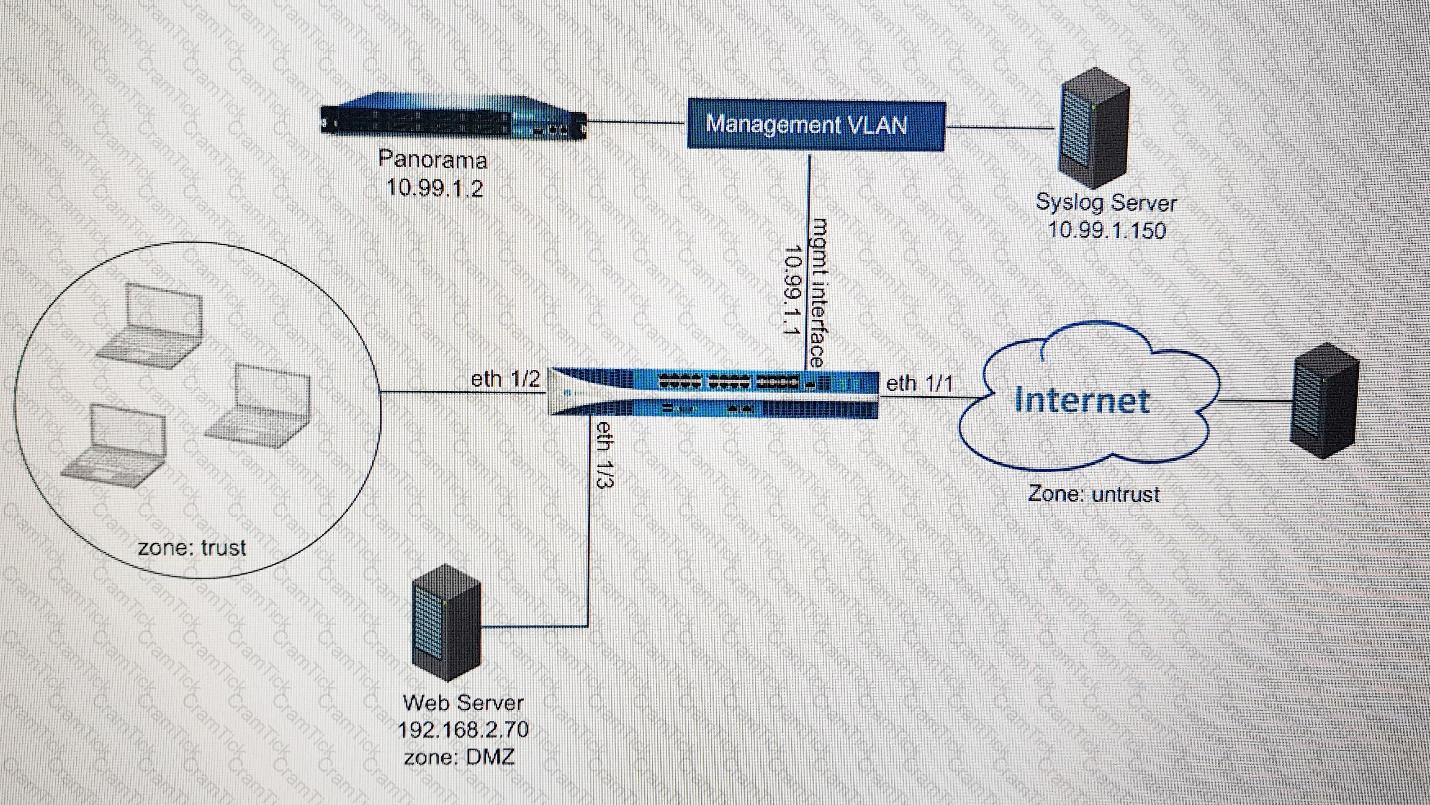
An administrator cannot see any of the Traffic logs from the Palo Alto Networks NGFW on Panorama. The configuration problem seems to be on the firewall side. Where is the best place on the Palo Alto Networks NGFW to check whether the configuration is correct?
A)
B)
C)
D)
Refer to Exhibit:
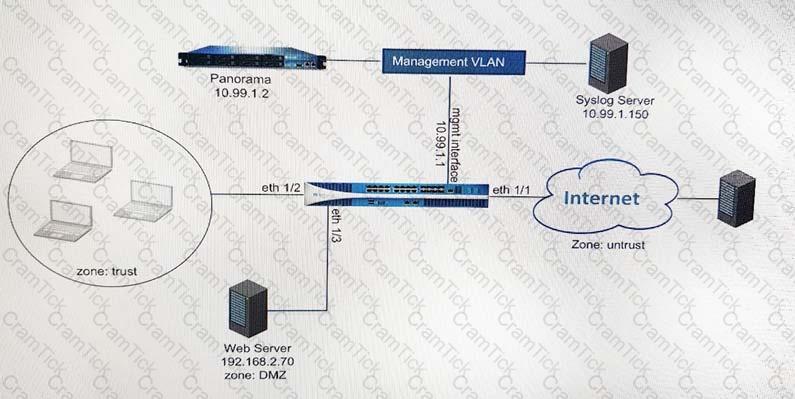
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall. Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
A)
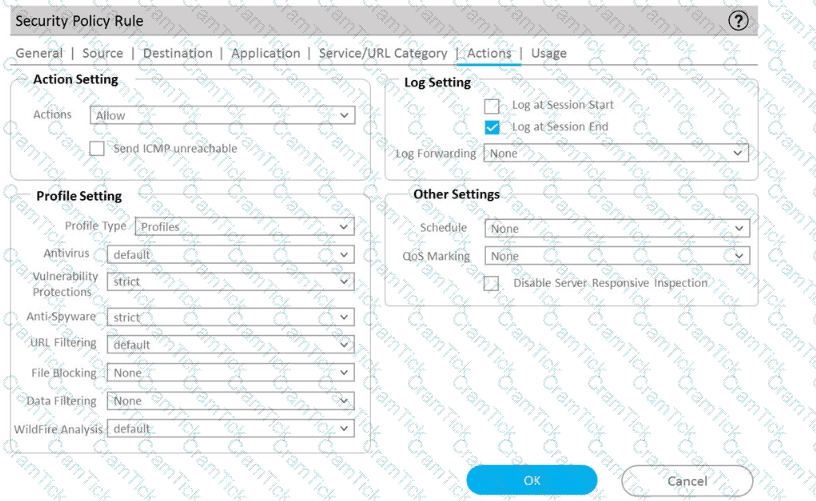
B)
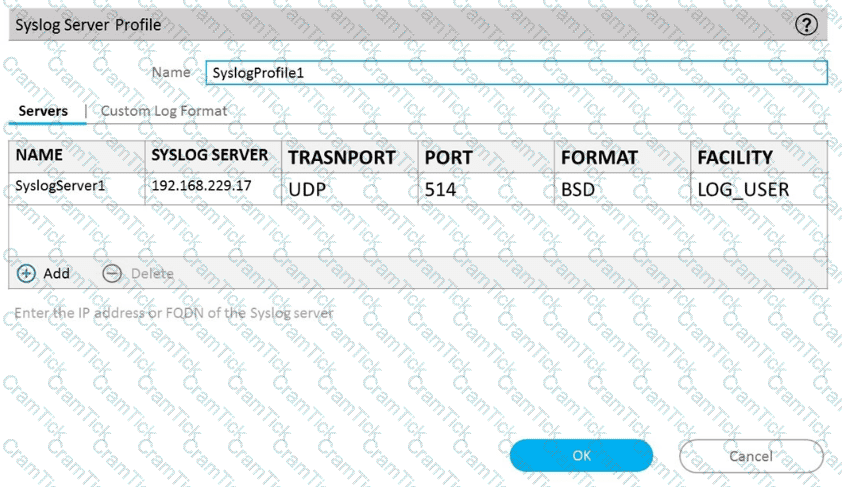
C)
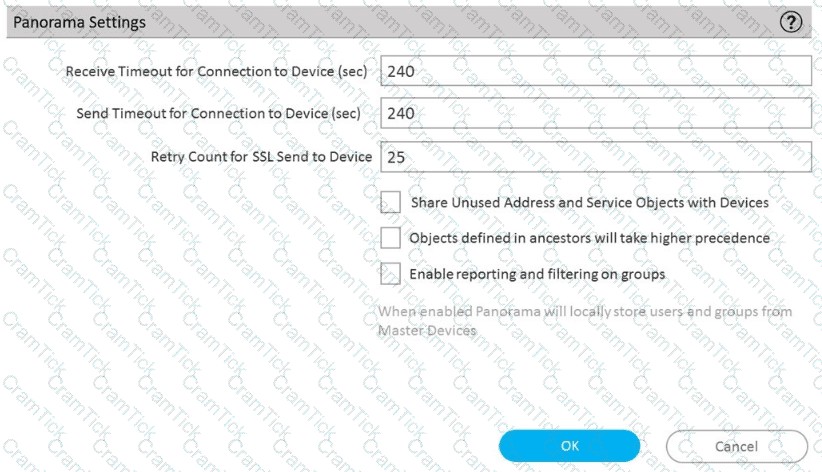
D)
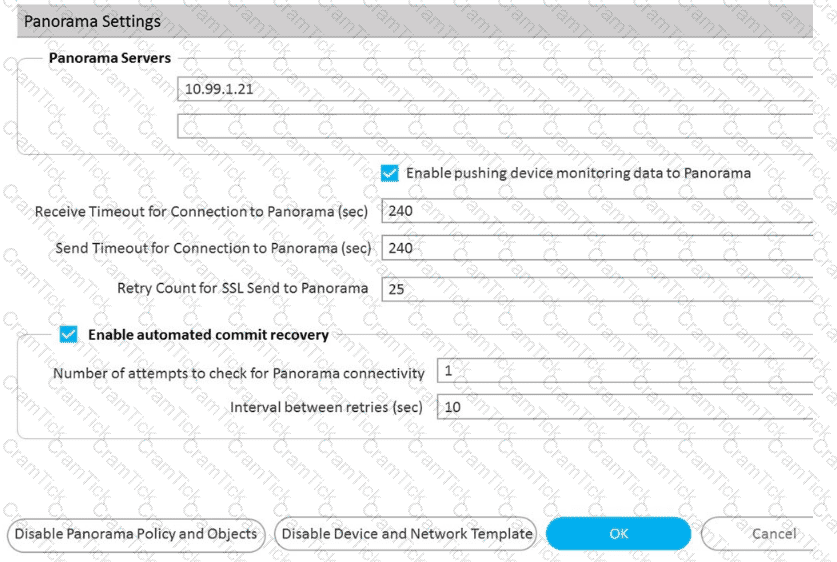
An engineer is configuring a Protection profile to defend specific endpoints and resources against malicious activity.
The profile is configured to provide granular defense against targeted flood attacks for specific critical systems that are accessed by users from the internet.
Which profile is the engineer configuring?
A company needs to preconfigure firewalls to be sent to remote sites with the least amount of reconfiguration. Once deployed, each firewall must establish secure tunnels back to multiple regional data centers to include the future regional data centers.
Which VPN configuration would adapt to changes when deployed to the future site?
Which User-ID mapping method should be used in a high-security environment where all IP address-to-user mappings should always be explicitly known?
A company CISO updates the business Security policy to identify vulnerable assets and services and deploy protection for quantum-related attacks. As a part of this update, the firewall team is reviewing the cryptography used by any devices they manage. The firewall architect is reviewing the Palo Alto Networks NGFWs for their VPN tunnel configurations. It is noted in the review that the NGFWs are running PAN-OS 11.2. Which two NGFW settings could the firewall architect recommend to deploy protections per the new policy? (Choose two)
To connect the Palo Alto Networks firewall to AutoFocus, which setting must be enabled?
An engineer needs to configure a standardized template for all Panorama-managed firewalls. These settings will be configured on a template named "Global" and will be included in all template stacks.
Which three settings can be configured in this template? (Choose three.)
An administrator is configuring a Panorama device group. Which two objects are configurable? (Choose two.)
A company configures its WildFire analysis profile to forward any file type to the WildFire public cloud. A company employee receives an email containing an unknown link that downloads a malicious Portable Executable (PE) file.
What does Advanced WildFire do when the link is clicked?
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
The firewall team has been asked to deploy a new Panorama server and to forward all firewall logs to this server By default, which component of the Palo Alto Networks firewall architect is responsible for log forwarding and should be checked for early signs of overutilization?
After importing a pre-configured firewall configuration to Panorama, what step is required to ensure a commit/push is successful without duplicating local configurations?
A network security engineer needs to ensure that virtual systems can communicate with one another within a Palo Alto Networks firewall. Separate virtual routers (VRs) are created for each virtual system.
In addition to confirming security policies, which three configuration details should the engineer focus on to ensure communication between virtual systems? (Choose three.)
Which three options does Panorama offer for deploying dynamic updates to its managed devices? (Choose three.)
An organization wants to begin decrypting guest and BYOD traffic.
Which NGFW feature can be used to identify guests and BYOD users, instruct them how to download and install the CA certificate, and clearly notify them that their traffic will be decrypted?
A customer wants to deploy User-ID on a Palo Alto Network NGFW with multiple vsys. One of the vsys will support a GlobalProtect portal and gateway. the customer uses Windows
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD.
Which three dynamic routing protocols support BFD? (Choose three.)
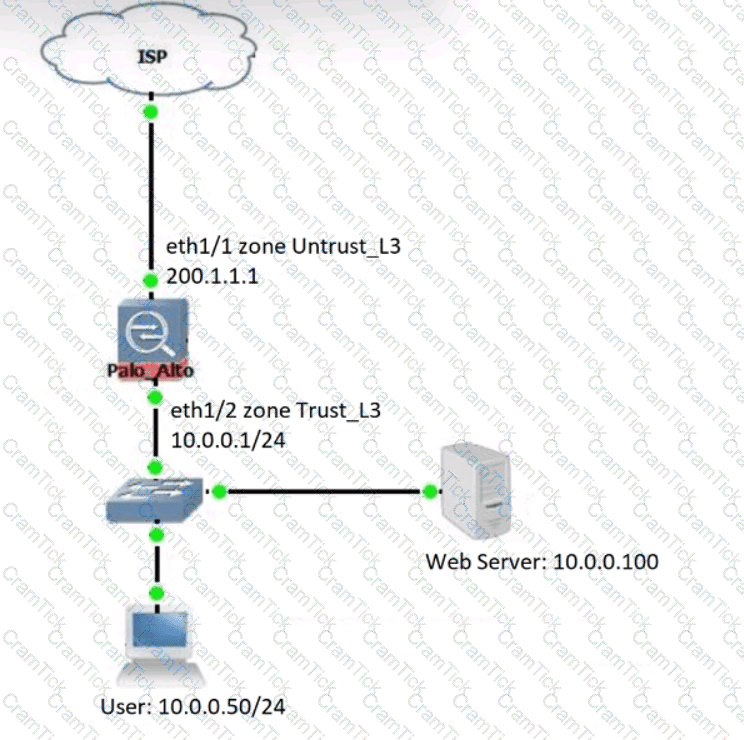
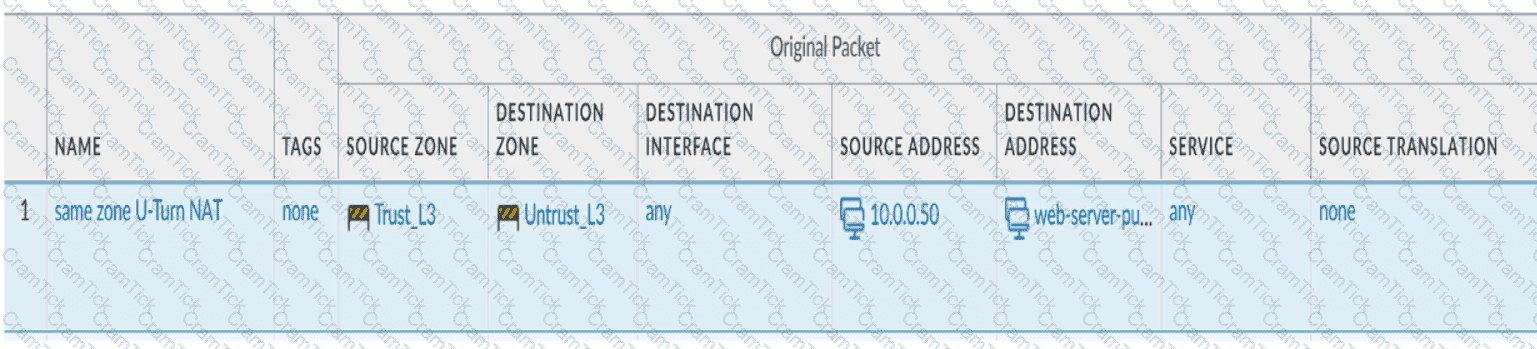
Review the information below. A firewall engineer creates a U-NAT rule to allow users in the trust zone access to a server in the same zone by using an external,
public NAT IP for that server.
Given the rule below, what change should be made to make sure the NAT works as expected?
A firewall administrator configures the HIP profiles on the edge firewall where GlobalProtect is enabled, and adds the profiles to security rules. The administrator wants to redistribute the HIP reports to the data center firewalls to apply the same access restrictions using HIP profiles. However, the administrator can only see the HIP match logs on the edge firewall but not on the data center firewall
What are two reasons why the administrator is not seeing HIP match logs on the data center firewall? (Choose two.)
A firewall engineer is investigating high dataplane CPU utilization. To decrease the load on this CPU, what should be reduced?
An organization is interested in migrating from their existing web proxy architecture to the Web Proxy feature of their PAN-OS 11.0 firewalls. Currently. HTTP and SSL requests contain the c IP address of the web server and the client browser is redirected to the proxy
Which PAN-OS proxy method should be configured to maintain this type of traffic flow?
When using certificate authentication for firewall administration, which method is used for authorization?
An administrator receives the following error message:
"IKE phase-2 negotiation failed when processing Proxy ID. Received local id 192.168 33 33/24 type IPv4 address protocol 0 port 0, received remote id 172.16 33.33/24 type IPv4 address protocol 0 port 0."
How should the administrator identify the root cause of this error message?
A standalone firewall with local objects and policies needs to be migrated into Panorama. What procedure should you use so Panorama is fully managing the firewall?
An administrator wants to configure the Palo Alto Networks Windows User-D agent to map IP addresses to u: ‘The company uses four Microsoft Active ‘servers and two Microsoft Exchange servers, which can provide logs for login events. All six servers have IP addresses assigned from the following subnet: 192.168.28.32/27. The Microsoft Active Directory in 192.168.28.22/128, and the Microsoft Exchange reside in 192,168.28 48/28. What the 0 the User
A firewall administrator to have visibility on one segment of the company network. The traffic on the segment is routed on the Backbone switch. The administrator is planning to apply security rules on segment X after getting the visibility. There is already a PAN-OS firewall used in L3 mode as an internet gateway, and there are enough system resources to get extra traffic on the firewall. The administrator needs to complete this operation with minimum service interruptions and without making any IP changes. What is the best option for the administrator to take?
Which three split tunnel methods are supported by a globalProtect gateway? (Choose three.)
An administrator is troubleshooting intermittent connectivity problems with a user's GlobalProtect connection. Packet captures at the firewall reveal missing UDP packets, suggesting potential packet loss on the connection. The administrator aims to resolve the issue by enforcing an SSL tunnel over TCP specifically for this user.
What configuration change is necessary to implement this troubleshooting solution for the user?
A network security administrator wants to inspect HTTPS traffic from users as it egresses through a firewall to the Internet/Untrust zone from trusted network zones.
The security admin wishes to ensure that if users are presented with invalid or untrusted security certificates, the user will see an untrusted certificate warning.
What is the best choice for an SSL Forward Untrust certificate?
Which three items must be configured to implement application override? (Choose three )
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an internal syslog server.
Where can the firewall engineer define the data to be added into each forwarded log?
A network administrator wants to deploy SSL Forward Proxy decryption. What two attributes should a forward trust certificate have? (Choose two.)
An organization conducts research on the benefits of leveraging the Web Proxy feature of PAN-OS 11.0.
What are two benefits of using an explicit proxy method versus a transparent proxy method? (Choose two.)
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is experiencing a failure of a monitored path?
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances. Which profile should be configured in order to achieve this?
An administrator needs to validate that policies that will be deployed will match the appropriate rules in the device-group hierarchy. Which tool can the administrator use to review the policy creation logic and verify that unwanted traffic is not allowed?
An administrator would like to determine which action the firewall will take for a specific CVE. Given the screenshot below, where should the administrator navigate to view this information?
An administrator is using Panorama to manage multiple firewalls. After upgrading all devices to the latest PAN-OS software, the administrator enables log forwarding from the firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
Which two factors should be considered when sizing a decryption firewall deployment? (Choose two.)
Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
Panorama is being used to upgrade the PAN-OS version on a pair of firewalls in an active/passive high availability (HA) configuration. The Palo Alto Networks best practice upgrade steps have been completed in Panorama (Panorama upgraded, backups made, content updates, and disabling "Preemptive" pushed), and the firewalls are ready for upgrade. What is the next best step to minimize downtime and ensure a smooth transition?
An administrator is receiving complaints about application performance degradation. After checking the ACC, the administrator observes that there is an excessive amount of VoIP traffic.
Which three elements should the administrator configure to address this issue? (Choose three.)
Which two policy components are required to block traffic in real time using a dynamic user group (DUG)? (Choose two.)
A security engineer needs to mitigate packet floods that occur on a RSF servers behind the internet facing interface of the firewall. Which Security Profile should be applied to a policy to prevent these packet floods?
A customer would like to support Apple Bonjour in their environment for ease of configuration.
Which type of interface in needed on their PA-3200 Series firewall to enable Bonjour Reflector in a segmented network?
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
An engineer is configuring secure web access (HTTPS) to a Palo Alto Networks firewall for management.
Which profile should be configured to ensure that management access via web browsers is encrypted with a trusted certificate?
A firewall engineer needs to patch the company’s Palo Alto Network firewalls to the latest version of PAN-OS. The company manages its firewalls by using panorama. Logs are forwarded to Dedicated Log Collectors, and file samples are forwarded to WildFire appliances for analysis. What must the engineer consider when planning deployment?
Palo Alto Certifications and Accreditations | PCNSE Questions Answers | PCNSE Test Prep | Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 10.0 Questions PDF | PCNSE Online Exam | PCNSE Practice Test | PCNSE PDF | PCNSE Test Questions | PCNSE Study Material | PCNSE Exam Preparation | PCNSE Valid Dumps | PCNSE Real Questions | Palo Alto Certifications and Accreditations PCNSE Exam Questions