In SecOps, what are two of the components included in the identify stage? (Choose two.)
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
Which option describes the “selective network security virtualization” phase of incrementally transforming data centers?
A firewall administrator needs to efficiently deploy corporate account configurations and VPN settings to targeted mobile devices within the network.
Which technology meets this requirement?
What is a key method used to secure sensitive data in Software-as-a-Service (SaaS) applications?
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
If an endpoint does not know how to reach its destination, what path will it take to get there?
Which tool's analysis data gives security operations teams insight into their environment's risks from exposed services?
Identify a weakness of a perimeter-based network security strategy to protect an organization's endpoint systems.
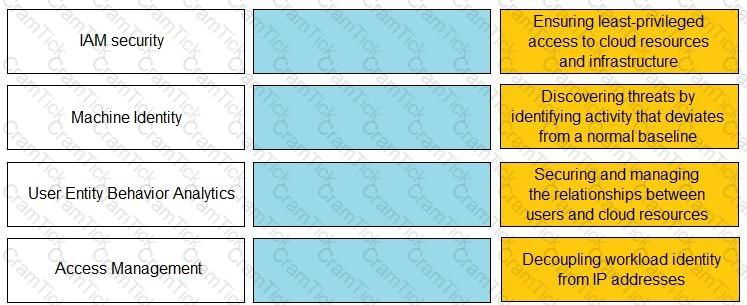
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Which two pieces of information are considered personally identifiable information (PII)? (Choose two.)
In which type of Wi-Fi attack does the attacker intercept and redirect the victim’s web traffic to serve content from a web server it controls?
Which component of cloud security is used to identify misconfigurations during the development process?
The customer is responsible only for which type of security when using a SaaS application?
A high-profile company executive receives an urgent email containing a malicious link. The sender appears to be from the IT department of the company, and the email requests an update of the executive's login credentials for a system update.
Which type of phishing attack does this represent?
Layer 4 of the TCP/IP Model corresponds to which three Layer(s) of the OSI Model? (Choose three.)
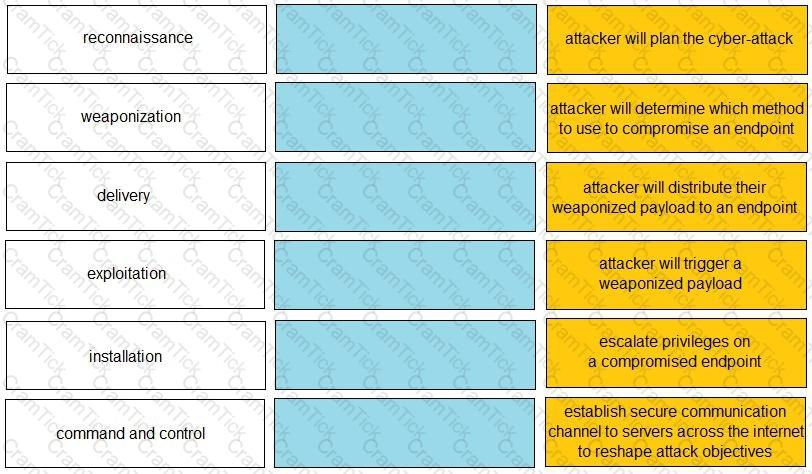
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
Which technology helps Security Operations Center (SOC) teams identify heap spray attacks on company-owned laptops?
Which type of firewall should be implemented when a company headquarters is required to have redundant power and high processing power?
Which element of the security operations process is concerned with using external functions to help achieve goals?
Which internet of things (loT) connectivity technology operates on the 2.4GHz and 5GHz bands, as well as all bands between 1 and 6GHz when they become available for 802.11 use. at ranges up to 11 Gbit/s?
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
Which type of portable architecture can package software with dependencies in an isolated unit?
How does Cortex XSOAR Threat Intelligence Management (TIM) provide relevant threat data to analysts?
Which activities do local organization security policies cover for a SaaS application?
Which security component should you configure to block viruses not seen and blocked by the perimeter firewall?
Which pillar of Prisma Cloud application security does vulnerability management fall under?
Which capability of a Zero Trust network security architecture leverages the combination of application, user, and content identification to prevent unauthorized access?
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next- generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
Which protocol is used by both internet service providers (ISPs) and network service providers (NSPs)?
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
Which architecture model uses virtual machines (VMs) in a public cloud environment?
Based on how much is managed by the vendor, where can CaaS be situated in the spread of cloud computing services?
What does Palo Alto Networks Cortex XDR do first when an endpoint is asked to run an executable?
What are two advantages of security orchestration, automation, and response (SOAR)? (Choose two.)
Which capability does Cloud Security Posture Management (CSPM) provide for threat detection within Prisma Cloud?


