A Linux engineer has been notified about the possible deletion of logs from the file /opt/app/logs. The engineer needs to ensure the log file can only be written into without removing previous entries.
Which of the following commands would be BEST to use to accomplish this task?
A systems administrator is tasked with installing GRUB on the legacy MBR of the SATA hard drive. Which of the following commands will help the administrator accomplish this task?
A Linux administrator was informed that the server time zone is incorrect. Which of the following commands should the administrator use to correct the time zone?
Which of the following commands should a technician use to create an administrative account for the username Joe?
A systems administrator wants to ensure all the latest patches and updates are automatically synced to the local repository every two hours on Sundays through Tuesdays in the month of May. Which of the following cron entries can the administrator use to achieve this goal? (Select two.)
Users report issues when trying to securely connect to a web server. The systems administrator receives the following outputs:
bash
firewall-cmd --list-all
(Only ports for ssh, cockpit, dhcp-client are listed.)
netstat -an | grep LISTEN
tcp 0 0 0.0.0.0:443 ... LISTEN
Which of the following actions will fix this issue?
A Linux administrator needs to restart a server and wants to see if any users are currently connected to it. Which of the following commands should the administrator run to find this information?
A Linux system is having issues. Given the following outputs:
# dig @192.168.2.2 mycomptiahost
; << >> DiG 9.9.4-RedHat-9.9.4-74.el7_6.1 << >> @192.168.2.2 mycomptiahost
; (1 server found)
;; global options: +cmd
;; connection timed out; no servers could be reached
# nc -v 192.168.2.2 53
Ncat: Version 7.70 ( https://nmap.org/ncat )
Ncat: Connection timed out.
# ping 192.168.2.2
PING 192.168.2.2 (192.168.2.2) 56(84) bytes of data.
64 bytes from 192.168.2.2: icmp_seq=1 ttl=117 time=4.94 ms
64 bytes from 192.168.2.2: icmp_seq=2 ttl=117 time=10.5 ms
Which of the following best describes this issue?
A systems administrator needs to check the size of the filesystem on the current application servers and ensure that the following filesystems are mounted:
/var
/var/log/audit
/tmp
/home/application
Which of the following commands should the administrator use for these tasks?
While troubleshooting server issues, a Linux systems administrator obtains the following output:
yaml
total used free shared buff/cache available
Mem: 3736 3538 33 2 48 25
Swap: 2047 1824 223
Which of the following best describes the state of the system?
The group named support is unable to make changes to the config file. An administrator is reviewing the permissions and sees the following:
S Is -1 config
-rw-rw----. 1 root app 4682 02-15 11:25 config
Which of the following should the administrator execute in order to give the support group access to modify the file while preserving the current ownership?
A systems administrator receives reports of issues in one of the Linux systems. The following output has been provided:
$ dig node.mycomptia.org
; <<>> DiG 9.11.36.x.x <<>> node.mycomptia.org
;; global options: +cmd
;; connection timed out; no servers could be reached
$ cat /etc/resolv.conf
search mycomptia.org
Which of the following actions will best resolve this issue? (Select two.)
A Linux administrator needs to redirect all HTTP traffic temporarily to the new proxy server 192.0.2.25 on port 3128. Which of the following commands will accomplish this task?
An administrator thinks that a package was installed using a snap. Which of the following commands can the administrator use to verify this information?
A Linux systems administrator needs to compress a file named passwords.txt. The compressed file should be saved as passwords.txt.gz. Which of the following commands should the administrator use to accomplish this task?
A Linux systems administrator is setting up a new web server and getting 404 - NOT FOUND errors while trying to access the web server pages from the browser. While working on the diagnosis of this issue, the Linux systems administrator executes the following commands:
Which of the following commands will BEST resolve this issue?
The application team is having issues accessing their data in their /app filesystem. Given the following outputs:
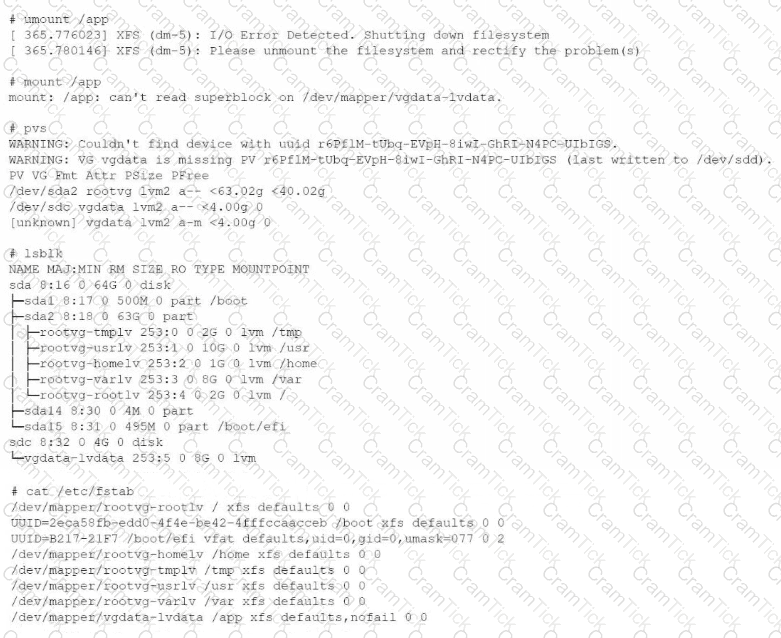
Which of the following is the reason for this issue?
A Linux administrator needs to remove software from the server. Which of the following RPM options should be used?
Users report that they are unable to reach the company website https://www.comptia.org. A systems administrator confirms the issue with the following command:
# curl https://www.comptia.org
curl: (7) Failed to connect to www.comptia.org port 443: No route to host
The administrator logs in to the company’s web server to check its configuration and sees the following output:
root@comptia.org:-># firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: dummy0 eth0
sources:
services: cockpit dhcpv6-client http ssh
ports: 3001/tcp
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
rule family="ipv4" source address="61.177.173.6" port port="ssh" protocol="tcp" reject type="icmp-port-unreachable"
rule family="ipv4" source address="185.143.45.164" port port="ssh" protocol="tcp" reject type="icmp-port-unreachable"
rule family="ipv4" source address="143.198.60.41" port port="ssh" protocol="tcp" reject type="icmp-port-unreachable"
root@comptia.org:-># ip route
default via 172.31.1.1 dev eth0 proto dhcp src 65.21.187.65 metric 100
10.0.6.0/24 dev dummy0 proto kernel scope link src 10.0.6.65 metric 550
172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1
172.18.0.0/16 dev br-28ac2eaeeca1 proto kernel scope link src 172.18.0.1
172.19.0.0/16 dev br-fb3897555ca3 proto kernel scope link src 172.19.0.1 linkdown
172.31.1.1 dev eth0 proto dhcp scope link src 65.21.187.65 metric 100
192.168.224.0/20 dev br-e949ab177d79 proto kernel scope link src 192.168.224.1 linkdown
192.168.240.0/20 dev br-6adf72ac0ae3 proto kernel scope link src 192.168.240.1 linkdown
Which of the following is causing the issue?
An organization's business office needs to collaborate on quarterly reports and asks the systems administrator to create a finance group. The administrator creates the following directory:
drwxrwxr-x business business 4096 Oct 15 16:40 q1
Which of the following commands will allow all members of the finance group to have group ownership of all files created in the q1 directory while ensuring that members of the business group preserve access? (Select two.)
The group owner of the / home/ test directory would like to preserve all group permissions on files created in the directory. Which of the following
commands should the group owner execute?
An engineer needs to insert a character at the end of the current line in the vi text editor. Which of the following will allow the engineer to complete this task?
A junior administrator is setting up a new Linux server that is intended to be used as a router at a remote site. Which of the following parameters will accomplish this goal?
Which of the following directories contains binaries that only a root user should run?
When trying to log in remotely to a server, a user receives the following message:
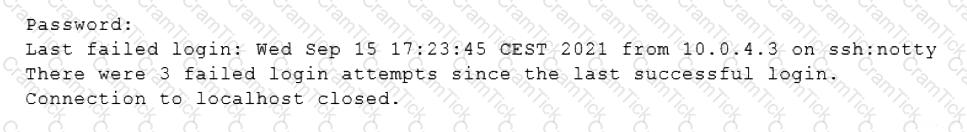
The server administrator is investigating the issue on the server and receives the following outputs:
Which of the following is causing the issue?
A Linux administrator needs to determine whether a hostname is in the DNS. Which of the following would supply the information that is needed?
A user is attempting to log in to a Linux server that has Kerberos SSO ena-bled. Which of the following commands should the user run to authenticate
and then show the ticket grants? (Select TWO).
A server administrator has scheduled a cron job to run YUM updates on all servers without manual intervention, but kernel packages must be excluded from the updates at all times. Which of the following configuration files needs to be modified to make these changes persistent?
A systems administrator is tasked with setting up key-based SSH authentication. In which of the following locations should the administrator place the public keys for the server?
A systems administrator is deploying three identical, cloud-based servers. The administrator is using the following code to complete the task:
Which of the following technologies is the administrator using?
An administrator has source code and needs to rebuild a kernel module. Which of the following command sequences is most commonly used to rebuild this
type of module?
A newly hired junior administrator is studying the format of the /var/log/messages file. Which of the following commands should the administrator use to preserve the contents of the original file while also creating an identical file in the /home/admin directory?
A systems administrator is trying to track down a rogue process that has a TCP listener on a network interface for remote command-and-control instructions.
Which of the following commands should the systems administrator use to generate a list of rogue process names? (Select two).
A Linux administrator has set up a new DNS forwarder and is configuring all internal servers to use the new forwarder to look up external DNS requests. The administrator needs to modify the firewall on the server for the DNS forwarder to allow the internal servers to communicate to it and make the changes persistent between server reboots. Which of the following commands should be run on the DNS forwarder server to accomplish this task?
An administrator accidentally deleted the /boot/vmlinuz file and must resolve the issue before the server is rebooted. Which of the following commands should the administrator use to identify the correct
version of this file?
A security team discovers that a web server has been running with elevated privileges and identifies it as a security violation. Which of the following items needs to be added to the webserver.service file to remediate the issue?
A systems administrator engineer wants to configure a Linux server's time zone to America/Chicago. The engineer verifies that the server's time zone is configured for Asia/Tokyo:

Which of the following commands should the engineer execute to make this change?
A Linux administrator is troubleshooting a memory-related issue. Based on the output of the commands:
Which of the following commands would address the issue?
A Linux administrator is trying to start the database service on a Linux server but is not able to run it. The administrator executes a few commands and receives the following output:
Which of the following should the administrator run to resolve this issue? (Select two).
A Linux administrator wants to set the SUID of a file named dev_team.text with 744 access rights. Which of the following commands will achieve this goal?
An administrator would like to securely connect to a server and forward port 8080 on a local machine to port 80 on the server. Which of the following commands should the administrator use to satisfy both requirements?
A Linux administrator is enabling root log-in over SSH on a server. Which of the following combinations of files and parameters should the administrator modify to accomplish this task?
A systems administrator configured firewall rules using firewalld. However, after the system is rebooted, the firewall rules are not present:
The systems administrator makes additional checks:
Which of the following is the reason the firewall rules are not active?
A systems administrator is reconfiguring existing user accounts in a Linux system. Which of the following commands should the administrator use to include "myuser" in the finance group?
A systems administrator is checking the system logs. The administrator wants to look at the last 20 lines of a log. Which of the following will execute the command?
A Linux administrator would like to use systemd to schedule a job to run every two hours. The administrator creates timer and service definitions and restarts the server to load these new configurations. After the restart, the administrator checks the log file and notices that the job is only running daily. Which of the following is MOST likely causing the issue?
A Linux administrator encounters the following error in the Apache log files:
css
SQLSTATE[HY000] [2002] Permission denied
Which of the following commands should the administrator run to safely fix this issue?
An administrator added a new disk to expand the current storage. Which of the following commands should the administrator run first to add the new disk to the LVM?
A Linux administrator is configuring crontab and needs to schedule a task to run only on Saturday and Sunday at 9:00 a.m. every week of the year. Which of the following should the administrator use?
A Linux administrator needs to set the permissions on a server. The administrator wants to have the files within the directory set to read-write permissions and the directory set to read-write-execute permissions. Which of the following commands should the administrator use?
Which of the following actions is required to establish passwordless SSH authentication?
A cloud engineer needs to remove all dangling images and delete all the images that do not have an associated container. Which of the following commands will help to accomplish this task?
Users connecting to a MySQL database on a Linux system report frequent errors. An administrator reviews the following partial output of the /proc/meminfo and free commands:
total used free
Mem: 1011966 151930 860036
Swap: 1191972 1181716 10256
MemTotal: 1011966 kB
MemFree:
SwapTotal: 1191972 kB
SwapFree: 10256 kB
Which of the following should the administrator do to ensure that the MySQL service will continue to run even if the system runs out of swap space? (Select two.)
A security analyst is monitoring the network to identify latency or slowdowns during a vulnerability scan. Which of the following functions will best achieve this?
bash
function x() {
info=$(ping -c 1 $1 | awk -F "/" 'END {print $5}')
echo "$1 | $info"
}
A Linux administrator updated the configuration file for the httpd web service. The administrator needs to apply the updated changes to the service without interrupting any running sessions. Which of the following commands should the administrator run to accomplish this task?
A Linux engineer is setting the sticky bit on a directory called devops with 755 file permission. Which of the following commands will accomplish this task?
A Linux systems administrator is working to obtain the installed kernel version of several hundred systems. Which of the following utilities should the administrator use for this task?
To harden one of the servers, an administrator needs to remove the possibility of remote administrative login via the SSH service. Which of the following should the administrator do?
A Linux administrator recently downloaded a software package that is currently in a compressed file. Which of the following commands will extract the files?
A cloud engineer wants to delete all unused networks that are not referenced by any container. Which of the following commands will achieve this goal?
A Linux systems administrator is trying to execute a particular shell script on a server. The administrator reviews the following outputs:
shell
$ ./startup.sh
bash: ./startup.sh: Permission denied
$ ls -l startup.sh
-rw-rw-r-- 1 companyabc companyabc 18 October 15:35 startup.sh
Which of the following commands should the administrator use to allow the script to run?
Joe, a user, is unable to log in to the system. The Linux administrator checks the /etc/passwd file and reviews the following output:
Joe:x:1002:1002::/home/Joe:/sbin/nologin
Which of the following should the administrator do to fix this issue?
A systems engineer is adding a new 1GB XFS filesystem that should be temporarily mounted under /ops/app. Which of the following is the correct list of commands to achieve this goal?
A systems technician is configuring an application server to accept packets from a trusted source with the IP address 192.168.10.22. Which of the following commands will allow communication between the two servers?
A Linux administrator needs to transfer a local file named accounts . pdf to a remote / tmp directory of a server with the IP address 10.10.10.80. Which of the following commands needs to be executed to transfer this file?
Several users reported that they were unable to write data to the /oracle1 directory. The following output has been provided:
Which of the following commands should the administrator use to diagnose the issue?
A network administrator issues the dig www.foo.com command and receives an NXDOMAIN response. Which of the following files should the administrator check first?
A development team asks an engineer to guarantee the persistency of journal log files across system reboots. Which of the following commands would accomplish this task?
In order to copy data from another VLAN, a systems administrator wants to temporarily assign IP address 10.0.6 5/24 to the newly added network interface enp1s0f1. Which of the following commands should the administrator run to achieve the goal?
NO: 41:
A systems administrator needs to install the file installer_0.17-41.2_amd64.deb. Which of the following commands should the administrator use?
A user created the following script file:
# ! /bin/bash
# FILENAME: /home/user/ script . sh
echo "hello world"
exit 1
However, when the user tried to run the script file using the command "script . sh, an error returned indicating permission was denied. Which of the follow-ing should the user execute in
order for the script to run properly?
A Linux systems administrator needs to persistently enable IPv4 forwarding in one of the Linux systems. Which of the following commands can be used together to accomplish this task? (Choose two.)
A new disk was presented to a server as /dev/ sdd. The systems administrator needs to check if a partition table is on that disk. Which of the following commands can show this information?
A Linux administrator cloned an existing Linux server and built a new server from that clone. The administrator encountered the following error after booting the cloned server:
The administrator performed the commands listed below to further troubleshoot and mount the missing filesystem:
Which of the following should administrator use to resolve the device mismatch issue and mount the disk?
A systems administrator is tasked with preventing logins from accounts other than root, while the file /etc/nologin exists. Which of the following PAM modules will accomplish this task?
A Linux administrator is troubleshooting an issue in which an application service failed to start on a Linux server. The administrator runs a few commands and gets the following outputs:
Based on the above outputs, which of the following is the MOST likely action the administrator should take to resolve this issue?
Joe, a user, is unable to log in to the Linux system Given the following output:

Which of the following command would resolve the issue?
A systems administrator detected corruption in the /data filesystem. Given the following output:
Which of the following commands can the administrator use to best address this issue?
A systems administrator needs to verify whether the built container has the app.go file in its root directory. Which of the following can the administrator use to verify the root directory has this file?
A systems administrator created a web server for the company and is required to add a tag for the API so end users can connect. Which of the following would the administrator do to complete this requirement?
After starting an Apache web server, the administrator receives the following error:
Apr 23 localhost.localdomain httpd 4618] : (98) Address already in use: AH00072: make_sock: could not bind to address [: :]80
Which of the following commands should the administrator use to further trou-bleshoot this issue?
Users have been unable to reach www.comptia.org from a Linux server. A systems administrator is troubleshooting the issue and does the following:
Based on the information above, which of the following is causing the issue?
A Linux engineer receives reports that files created within a certain group are being modified by users who are not group members. The engineer wants to reconfigure the server so that only file owners and group members can modify new files by default. Which of the following commands would accomplish this task?
A user reported issues when trying to log in to a Linux server. The following outputs were received:
Given the outputs above. which of the following is the reason the user is una-ble to log in to the server?
A systems administrator is tasked with mounting a USB drive on a system. The USB drive has a single partition, and it has been mapped by the system to the device /dev/sdb. Which of the following commands will mount the USB to /media/usb?
A systems administrator checked out the code from the repository, created a new branch, made changes to the code, and then updated the main branch. The systems administrator wants to ensure that the Terraform state files do not appear in the main branch. Which of following should the administrator use to meet this requirement?
A Linux administrator created the directory /project/access2all. By creating this directory, the administrator is trying to avoid the deletion or modification of files from non-owners. Which of the following will accomplish this goal?
A newly created container has been unable to start properly, and a Linux administrator is analyzing the cause of the failure. Which of the following will allow the administrator to determine the FIRST command that is executed inside the container right after it starts?
A systems administrator is troubleshooting connectivity issues and trying to find out why a Linux server is not able to reach other servers on the same subnet it is connected to. When listing link parameters, the following is presented:
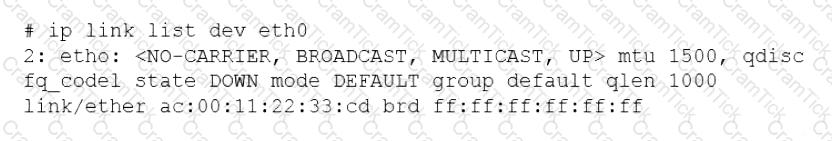
Based on the output above, which of following is the MOST probable cause of the issue?
An administrator attempts to connect to a remote server by running the following command:
$ nmap 192.168.10.36
Starting Nmap 7.60 ( https://nmap.org ) at 2022-03-29 20:20 UTC
Nmap scan report for www1 (192.168.10.36)
Host is up (0.000091s latency).
Not shown: 979 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp filtered ssh
631/tcp open ipp
Nmap done: 1 IP address (1 host up) scanned in 0.06 seconds
Which of the following can be said about the remote server?
A user is asking the systems administrator for assistance with writing a script to verify whether a file exists. Given the following:
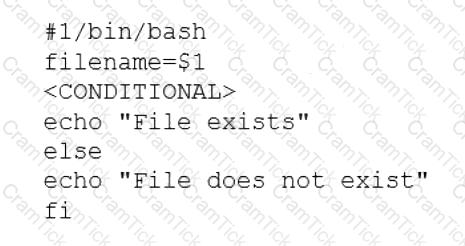
Which of the following commands should replace the
A junior Linux administrator is tasked with installing an application. The installation guide states the application should only be installed in a run level 5 environment.
Which of the following commands would ensure the server is set to runlevel 5?
A Linux systems administrator is troubleshooting an I/O latency on a single CPU server. The administrator runs a top command and receives the following output:
%Cpu(s): 0.2 us, 33.1 sy, 0.0 ni, 0.0 id, 52.4 wa, 0.0 hi, 0.2 si, 0.0 st
Which of the following is correct based on the output received from the exe-cuted command?
A systems administrator wants to check for running containers. Which of the following commands can be used to show this information?
A Linux engineer needs to create a custom script, cleanup.sh, to run at boot as part of the system services. Which of the following processes would accomplish this task?
Due to low disk space, a Linux administrator finding and removing all log files that were modified more than 180 days ago. Which of the following commands will accomplish this task?
A Linux administrator needs to ensure that Java 7 and Java 8 are both locally available for developers to use when deploying containers. Currently only Java 8 is available. Which of the following commands should the administrator run to ensure both versions are available?
User1 is a member of the accounting group. Members of this group need to be able to execute but not make changes to a script maintained by User2. The script should not be accessible to other users or groups. Which of the following will give proper access to the script?
A database administrator requested the installation of a custom database on one of the servers. Which of the following should the Linux administrator configure so the requested packages can be installed?
A developer has been unable to remove a particular data folder that a team no longer uses. The developer escalated the issue to the systems administrator. The following output was received:
Which of the following commands can be used to resolve this issue?
A systems administrator is implementing a new service task with systems at startup and needs to execute a script entitled test.sh with the following content:
The administrator tries to run the script after making it executable with chmod +x; however, the script will not run. Which of the following should the administrator do to address this issue? (Choose two.)
A new Linux systems administrator just generated a pair of SSH keys that should allow connection to the servers. Which of the following commands can be used to copy a key file to remote servers? (Choose two.)
A Linux system is failing to boot with the following error:
Which of the following actions will resolve this issue? (Choose two.)
After installing some RPM packages, a systems administrator discovers the last package that was installed was not needed. Which of the following commands can be used to remove the package?
A systems administrator is enabling LUKS on a USB storage device with an ext4 filesystem format. The administrator runs dmesg and notices the following output:
Given this scenario, which of the following should the administrator perform to meet these requirements? (Select three).
Employees in the finance department are having trouble accessing the file /opt/work/file. All IT employees can read and write the file. Systems administrator reviews the following output:
Which of the following commands would permanently fix the access issue while limiting access to IT and finance department employees?
Which of the following tools is BEST suited to orchestrate a large number of containers across many different servers?
A Linux administrator is providing a new Nginx image from the registry to local cache. Which of the following commands would allow this to happen?
Users have reported that the interactive sessions were lost on a Linux server. A Linux administrator verifies the server was switched to rescue.target mode for maintenance. Which of the following commands will restore the server to its usual target?
During a security scan, the password of an SSH key file appeared to be too weak and was cracked. Which of the following commands would allow a user to choose a stronger password and set it on the existing SSH key file?
After installing a new version of a package, a systems administrator notices a new version of the corresponding, service file was Installed In order to use the new version of the, service file, which of the following commands must be Issued FIRST?
Users report that connections to a MariaDB service are being closed unexpectedly. A systems administrator troubleshoots the issue and finds the following message in /var/log/messages:
Which of the following is causing the connection issue?
An administrator transferred a key for SSH authentication to a home directory on a remote server. The key file was moved to .ssh/authorized_keys location in order to establish SSH connection without a password. However, the SSH command still asked for the password. Given the following output:
Which of the following commands would resolve the issue?
A Linux engineer set up two local DNS servers (10.10.10.10 and 10.10.10.20) and was testing email connectivity to the local mail server using the mail command on a local machine when the following error appeared:
The local machine DNS settings are:
Which of the following commands could the engineer use to query the DNS server to get mail server information?
A Linux system fails to start and delivers the following error message:
Which of the following commands can be used to address this issue?
A cloud engineer needs to launch a container named web-01 in background mode. Which of the following commands will accomplish this task''
A user generated a pair of private-public keys on a workstation. Which of the following commands will allow the user to upload the public key to a remote server and enable passwordless login?
A systems administrator is troubleshooting a connectivity issue pertaining to access to a system named db.example.com. The system IP address should be 192.168.20.88. The administrator issues the dig command and receives the following output:
The administrator runs grep db.example.com /etc/hosts and receives the following output:
Given this scenario, which of the following should the administrator do to address this issue?
Joe, a user, is unable to log in to the Linux system. Given the following output:
Which of the following commands would resolve the issue?
Which of the following actions are considered good security practices when hardening a Linux server? (Select two).
A junior administrator updated the PostgreSQL service unit file per the data-base administrator's recommendation. The service has been restarted, but changes have not been applied. Which of the following should the administrator run for the changes to take effect?
A systems administrator made some changes in the ~/.bashrc file and added an alias command. When the administrator tried to use the alias command, it did not work. Which of the following should be executed FIRST?
A developer needs to launch an Nginx image container, name it Web001, and ex-pose port 8080 externally while mapping to port 80 inside the container. Which of the following commands will accomplish this task?
A Linux administrator rebooted a server. Users then reported some of their files were missing. After doing some troubleshooting, the administrator found one of the filesystems was missing. The filesystem was not listed in /etc/f stab and might have been mounted manually by someone prior to reboot. Which of the following would prevent this issue from reoccurring in the future?
A Linux administrator has logged in to a server for the first time and needs to know which services are allowed through the firewall. Which of the following options will return the results for which the administrator is looking?
A Linux administrator was asked to run a container with the httpd server inside. This container should be exposed at port 443 of a Linux host machine while it internally listens on port 8443. Which of the following commands will accomplish this task?
A systems administrator requires that all files that are created by the user named web have read-only permissions by the owner. Which of the following commands will satisfy this requirement?
Rugged appliances are small appliances with ruggedized hardware and like Quantum Spark appliance they use which operating system?
A systems administrator created a new Docker image called test. After building the image, the administrator forgot to version the release. Which of the following will allow the administrator to assign the v1 version to the image?
A systems administrator made some unapproved changes prior to leaving the company. The newly hired administrator has been tasked with revealing the system to a compliant state. Which of the following commands will list and remove the correspondent packages?
A systems technician is working on deploying several microservices to various RPM-based systems, some of which could run up to two hours. Which of the following commands will allow the technician to execute those services and continue deploying other microservices within the same terminal section?
An administrator recently updated the BIND software package and would like to review the default configuration that shipped with this version. Which of the following files should the administrator review?
A server is experiencing intermittent connection issues. Some connections to the Internet work as intended, but some fail as if there is no connectivity. The systems administrator inspects the server configuration:
Which of the following is MOST likely the cause of the issue?
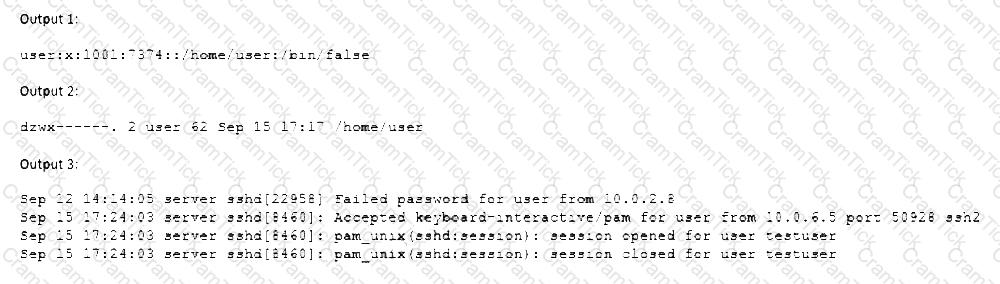
A Linux systems administrator receives reports from various users that an application hosted on a server has stopped responding at similar times for several days in a row. The administrator logs in to the system and obtains the following output:
Output 1:
Output 2:
Output 3:
Which of the following should the administrator do to provide the BEST solution for the reported issue?
A Linux administrator has been tasked with installing the most recent versions of packages on a RPM-based OS. Which of the following commands will accomplish this task?
A Linux user reported the following error after trying to connect to the system remotely:
ssh: connect to host 10.0.1.10 port 22: Resource temporarily unavailable
The Linux systems administrator executed the following commands in the Linux system while trying to diagnose this issue:
Which of the following commands will resolve this issue?
Using AD Query, the security gateway connections to the Active Directory Domain Controllers using what protocol?
A systems administrator has been unable to terminate a process. Which of the following should the administrator use to forcibly stop the process?
A Linux administrator is adding a new configuration file to a Git repository. Which of the following describes the correct order of Git commands to accomplish the task successfully?
Linux+ |