Which of the following is an example of an application publisher including undisclosed additional software in an installation package?
Which of the following concepts should a technician consider when discussing confidential work projects with individuals outside the company?
A user receives a new personal computer but is unable to run an application. An error displays saying that .NET Framework 3.5 is required and not found. Which of the following actions is the best way to resolve this issue?
A customer calls the help desk to report issues with internet connectivity. The customer is frustrated after speaking with multiple representatives who were unable to resolve the issue. A technician reviews the customer’s file and sees several unresolved tickets. Which of the following actions should the technician take to communicate properly and professionally?
A company's IT department discovers that unauthorized software has been installed on several workstations. The IT manager requests a review and an update of the workstation security posture, focusing on preventing future unauthorized software installations. Which of the following should the company do?
A technician needs to change hibernation settings on a Windows computer via a batch file. Domain policies are unavailable. Which is the best method?
A user is trying to install new software. The application downloads successfully, but when the user attempts to install it, the user receives a prompt for credentials. Which of the following would the technician most likely do to resolve this issue?
A company recently transitioned to a cloud-based productivity suite and wants to secure the environment from external threat actors. Which of the following is the most effective method?
What is the next step a technician should take after completing malware cleanup?
A technician is troubleshooting an issue in which a service runs momentarily and stops at certain points in the process. The technician needs to determine the root cause of this issue. Which of the following tools should the technician use?
When a corporate laptop is connected to the company network, it can reach external websites. However, it cannot reach any internal websites, displaying the error message “Cannot reach this page.” Which of the following should a technician configure?
A client reports that their browser's home page changed. Every time they run an internet search, the results are returned from unfamiliar websites. Which of the following actions should a technician take first to resolve the issue? (Select two)
An administrator must rename the administrator account on a Windows desktop. Which tool is best for this?
A company wants to prevent unauthorized physical access to its mobile devices. Which of the following should the company do? (Select two).
A project team needs special access on a shared repository to add new content, edit existing content, and prevent content deletion. Which of the following should an administrator do to configure this setup with the least amount of effort?
A user needs to download some files from a vendor website. Downloading the specific file type is blocked when using the Microsoft Edge web browser. A technician determines that the files the user wants to download are safe. Which of the following should the technician configure to allow these files to be downloaded?
A user wants to dispose of a failed hard drive in a way that ensures the data is unrecoverable. Which of the following is the best at-home method?
A user is unable to use the latest version of an application on a legacy personal tablet. Which of the following is most likely the reason?
Which of the following file types is best for performing automated tasks on startup on a Windows computer?
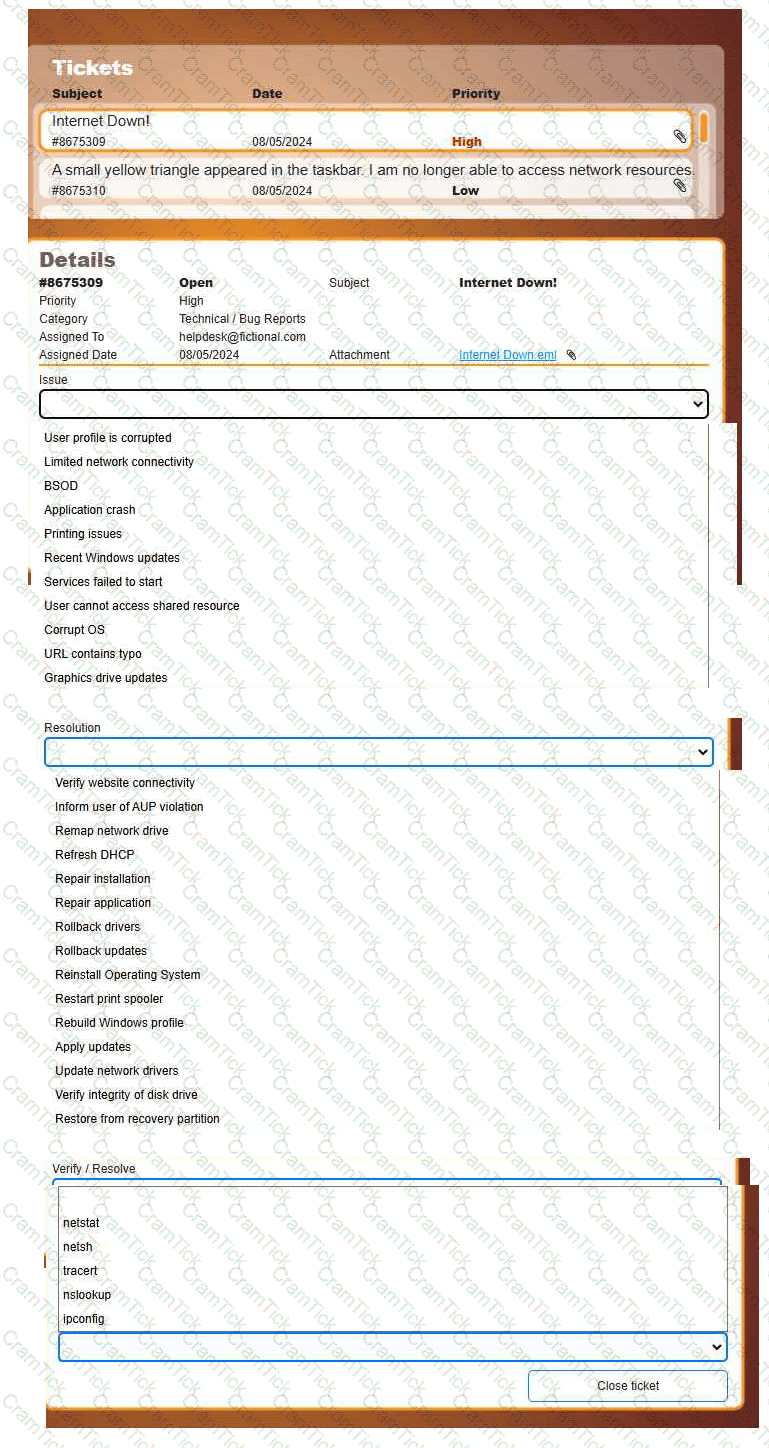
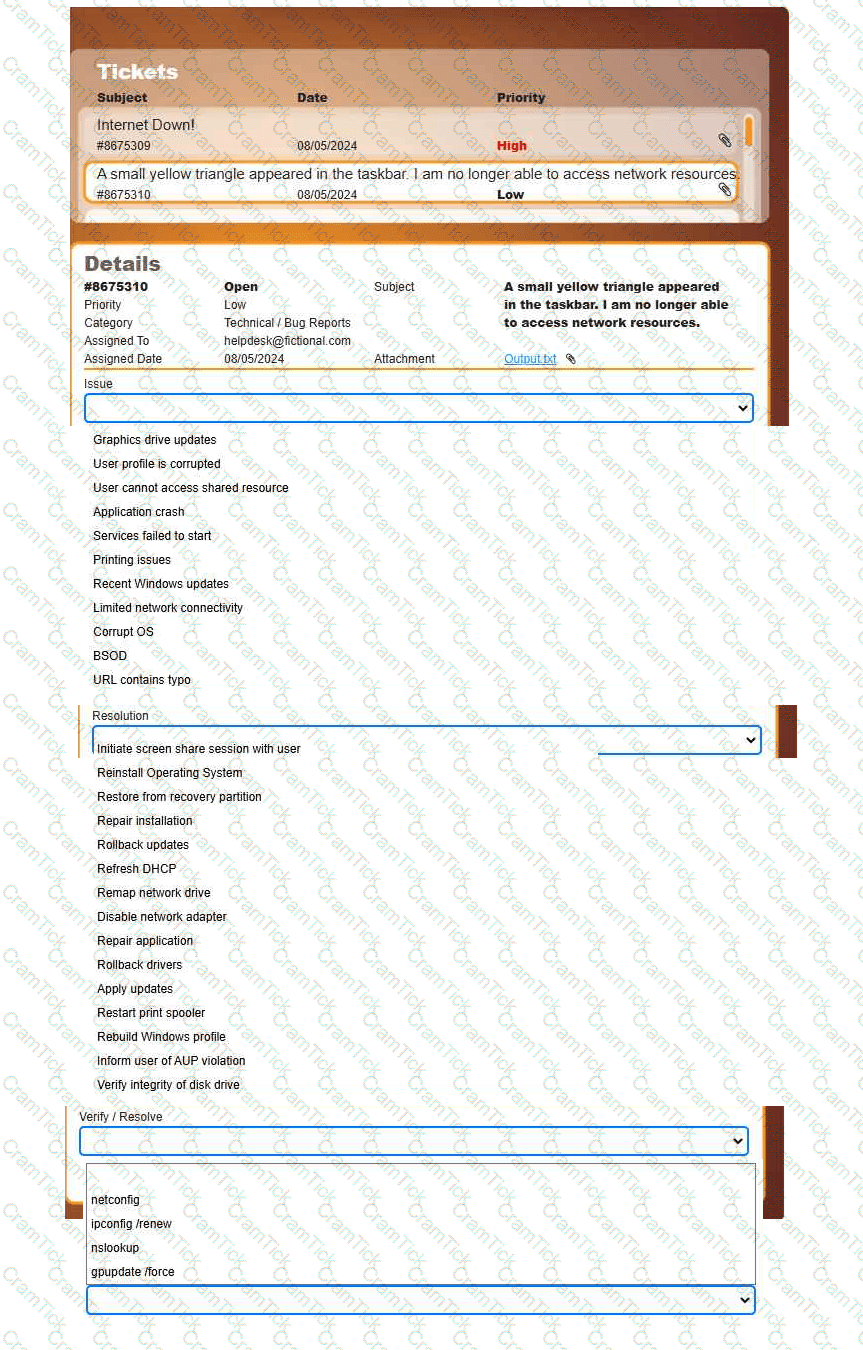
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
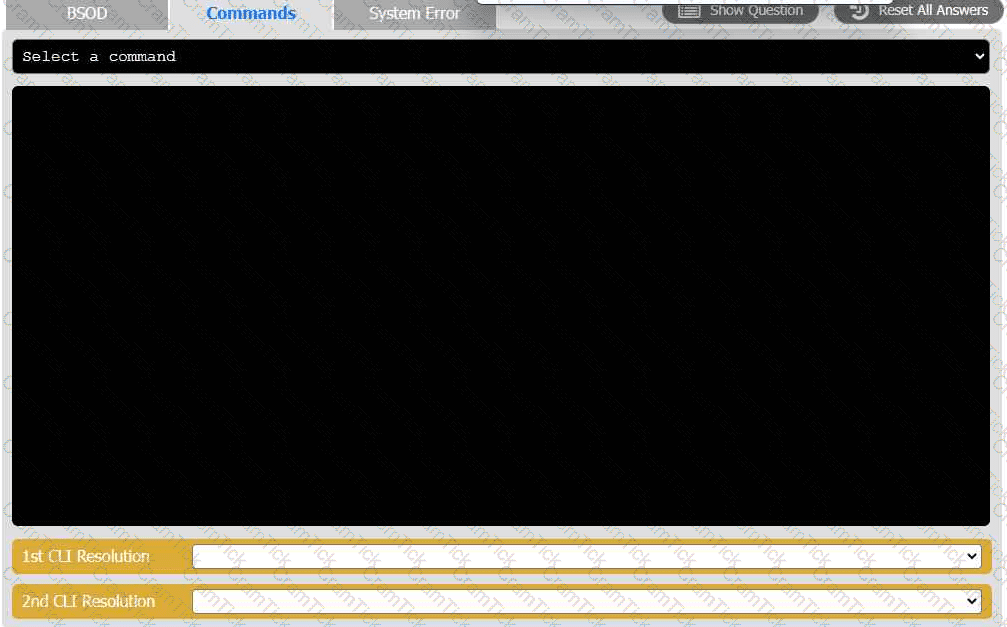
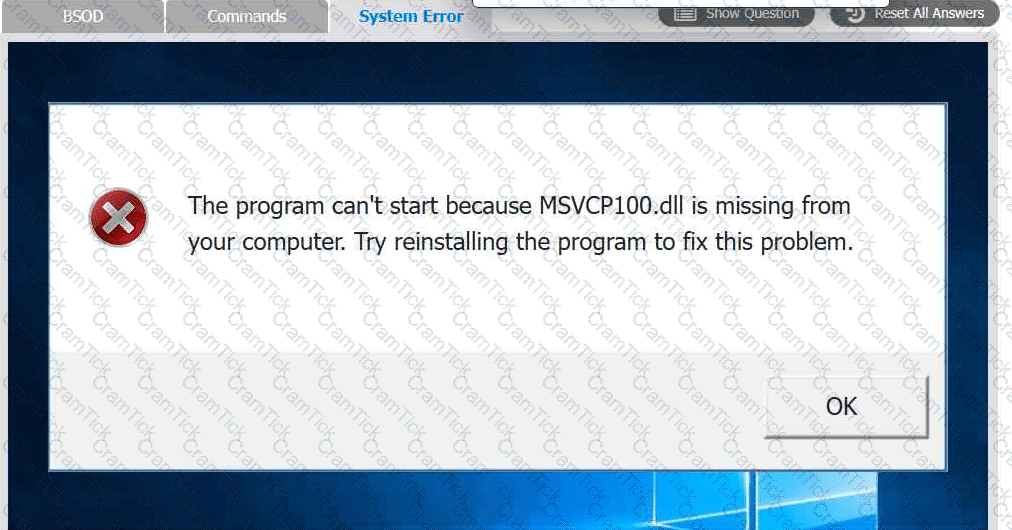
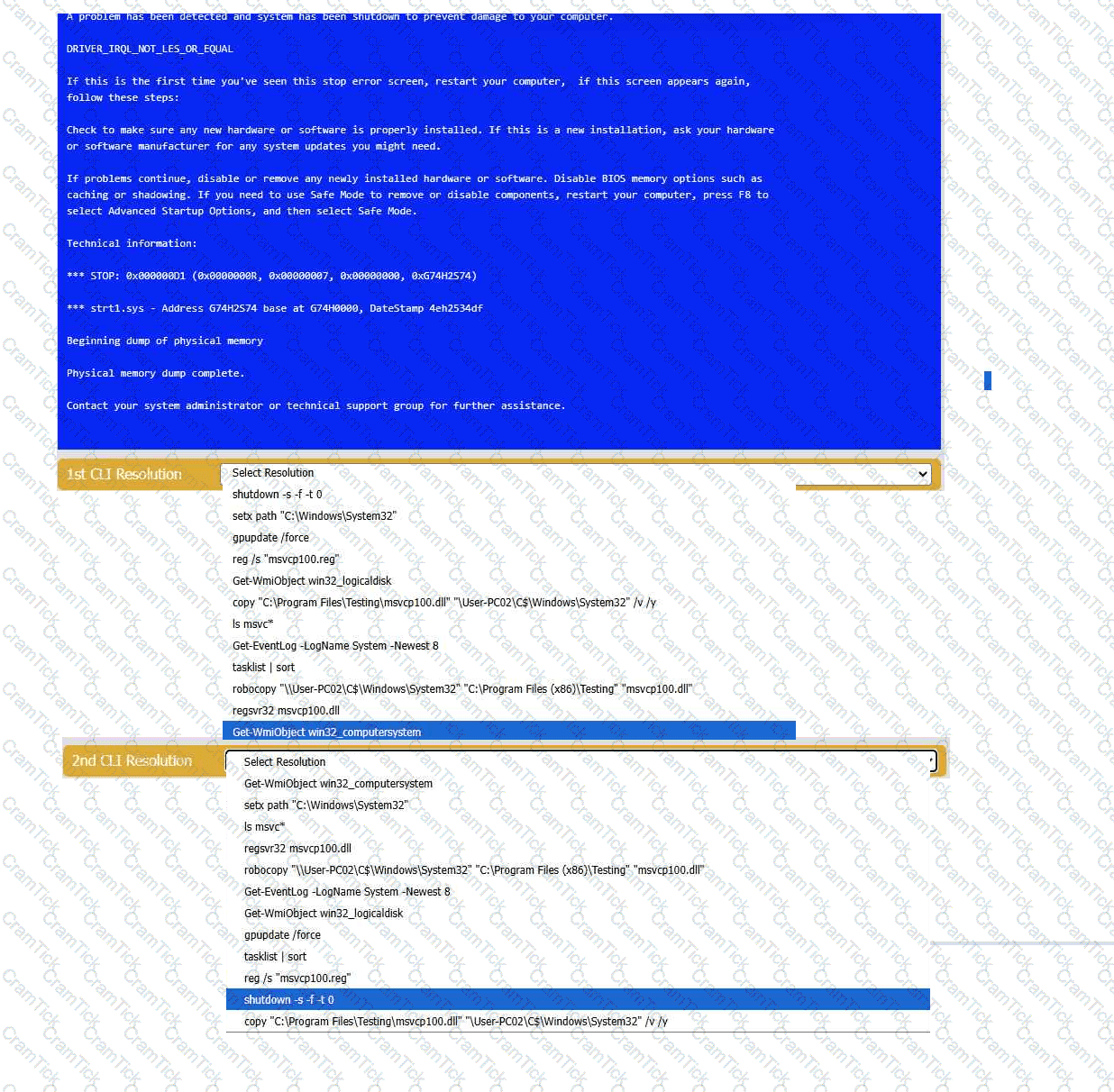
A user reports that after a recent software deployment to upgrade the Testing application, they can no longer use it. However, other employees can successfully
use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve
any issues discovered by selecting the:
· First command to resolve the issue
· Second command to resolve the issue
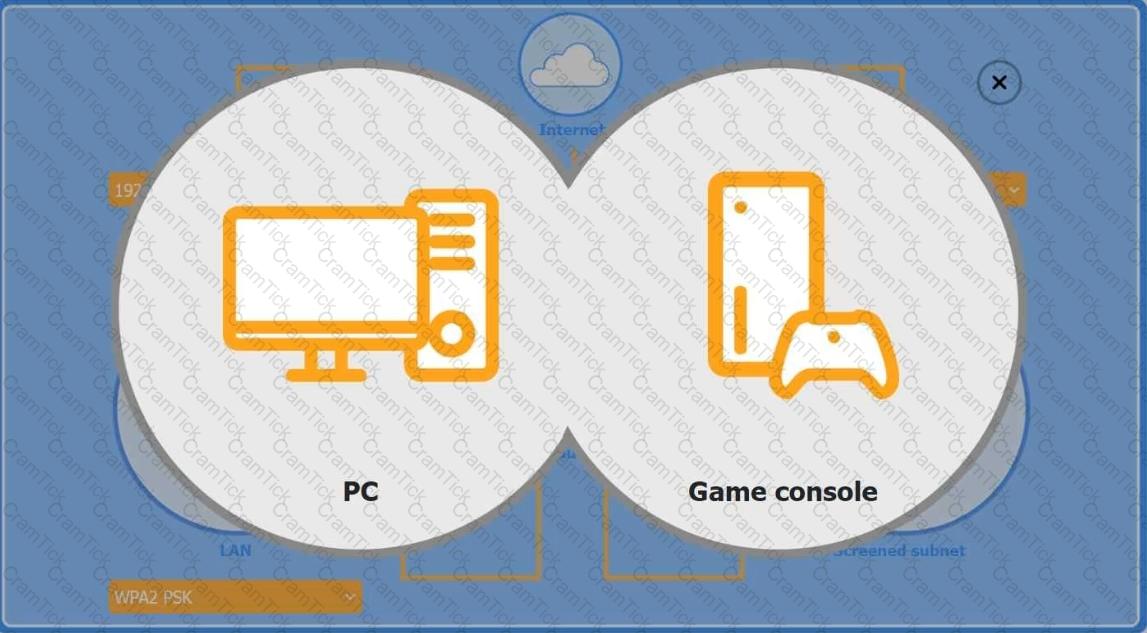
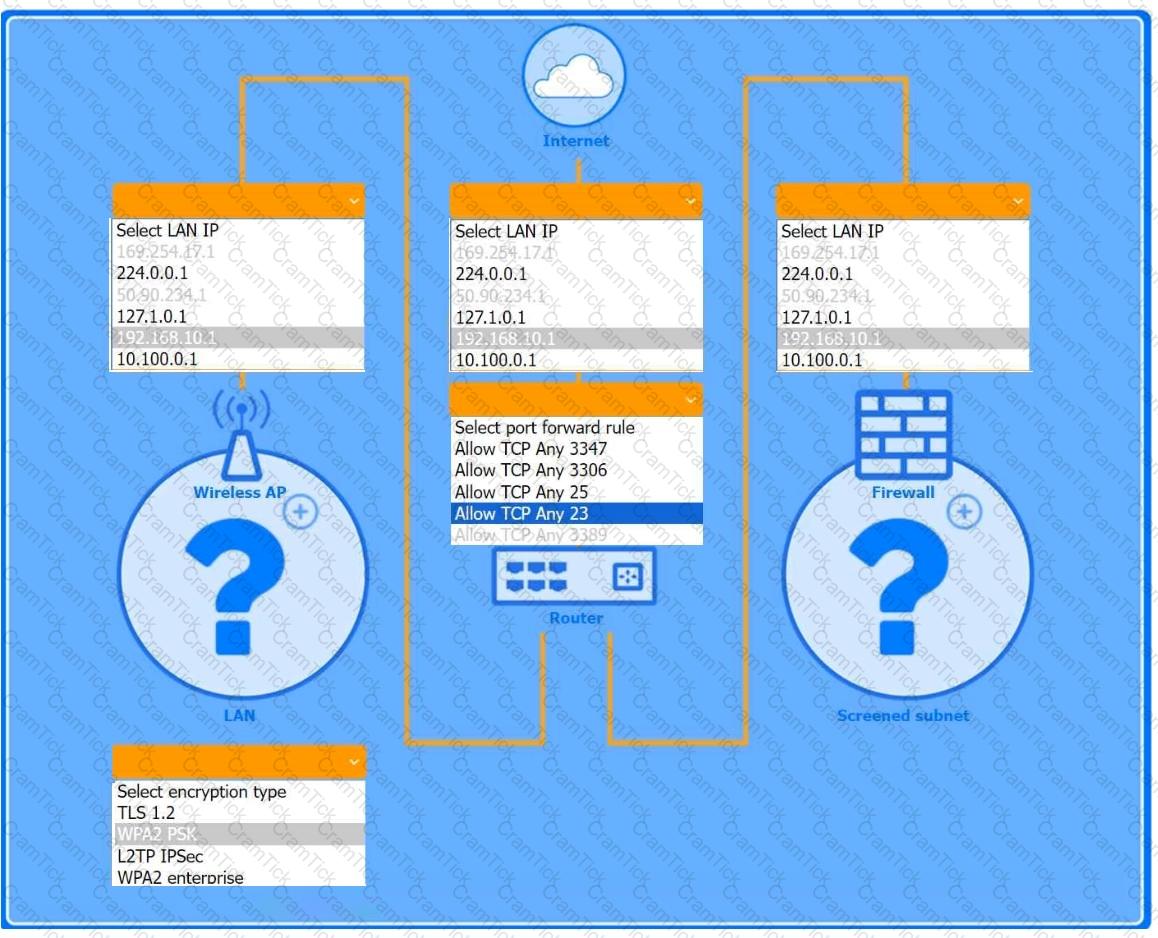
You are configuring a home network for a customer. The customer has requested the ability to access a Windows PC remotely, and needs all chat and optional functions to work in their game console.
INSTRUCTIONS
Use the drop-down menus to complete the network configuration for the customer. Each option may only be used once, and not all options will be used.
Then, click the + sign to place each device in its appropriate location.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Wireless AP LAN
Firewall Screened Subnet
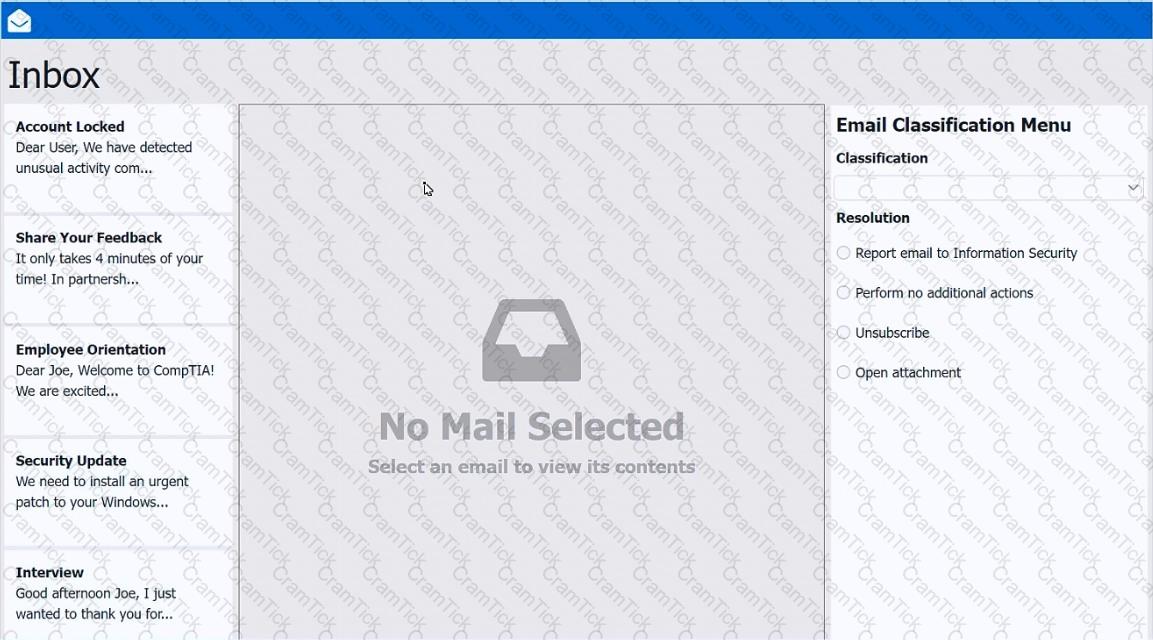
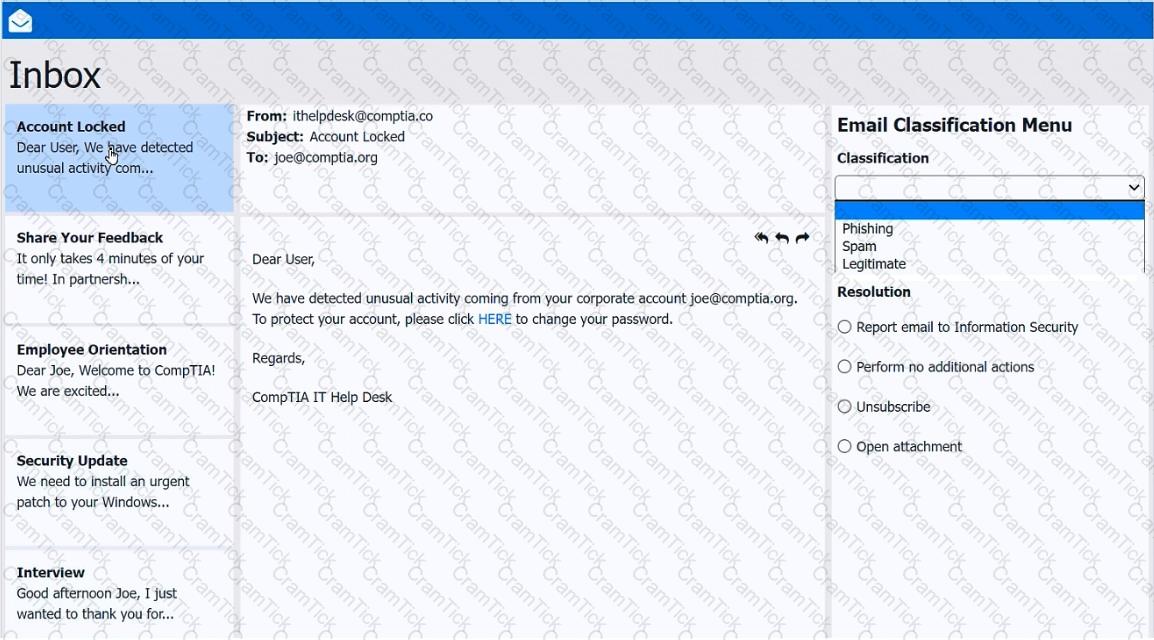
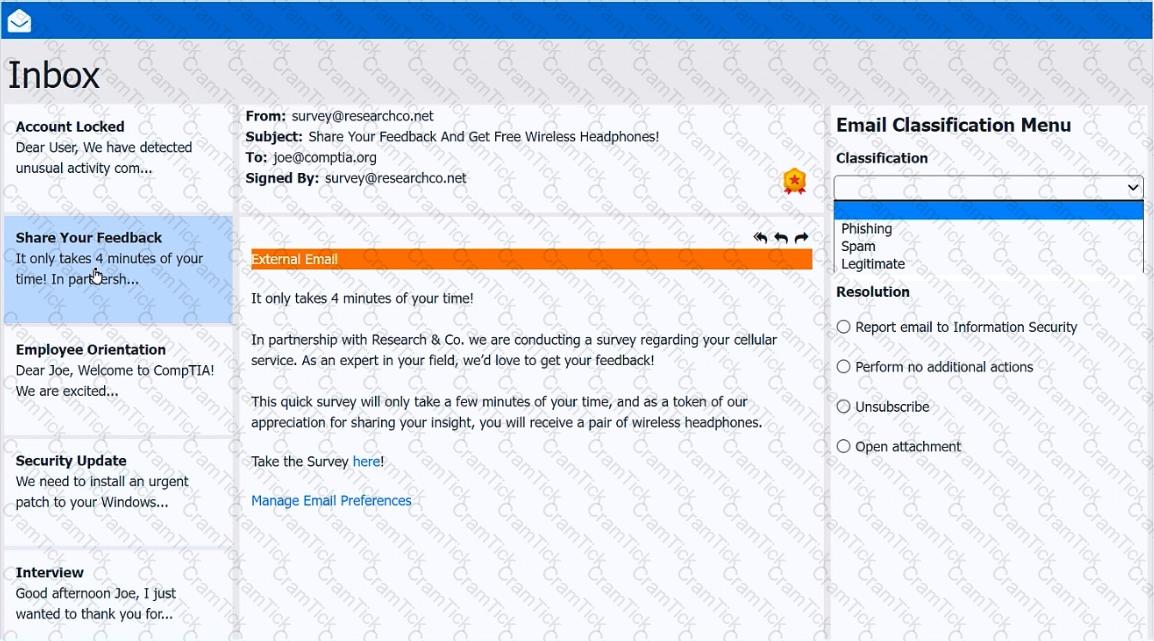
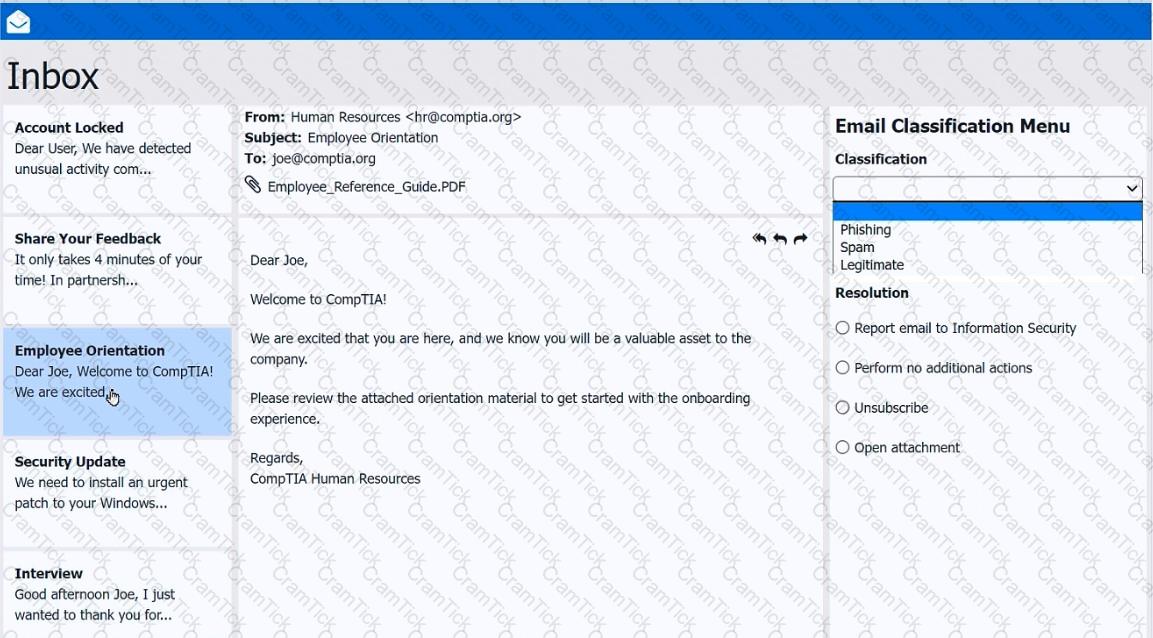
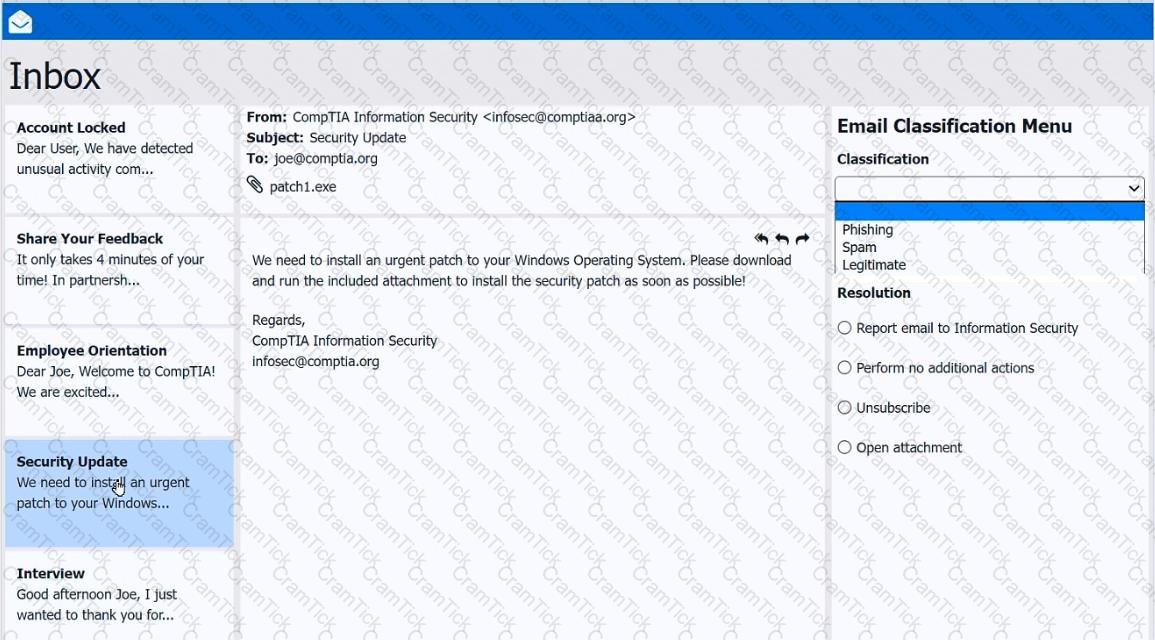
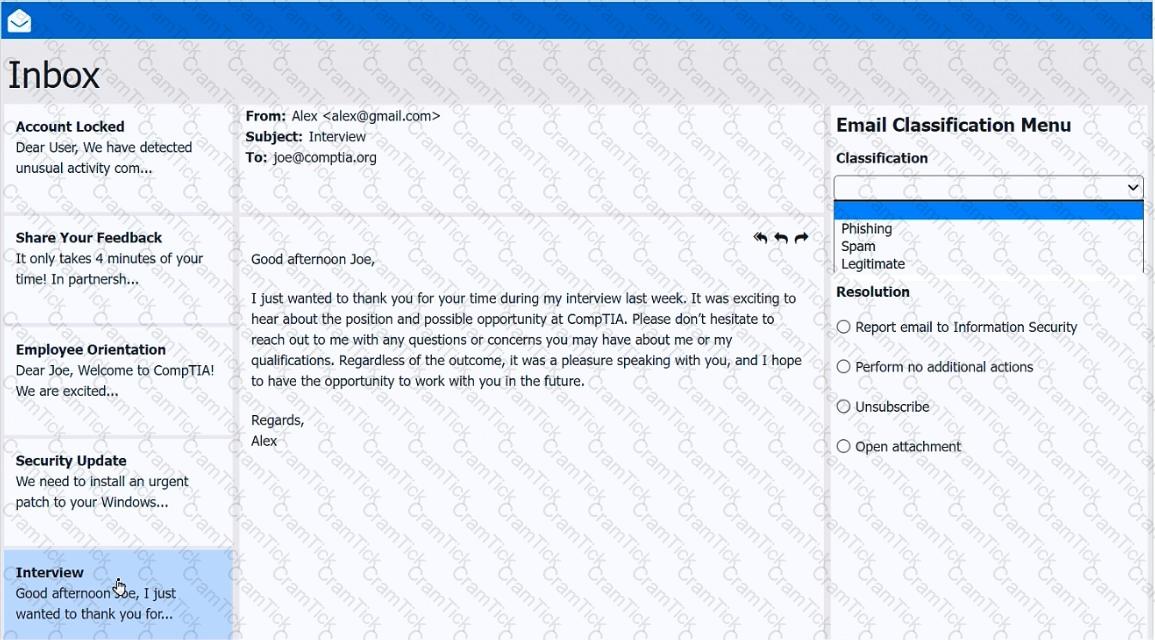
As a corporate technician, you are asked to evaluate several suspect email messages on a client's computer. Corporate policy requires the following:
>All phishing attempts must be reported.
>Future spam emails to users must be prevented.
INSTRUCTIONS
Review each email and perform the following within the email:
>Classify the emails
>Identify suspicious items, if applicable, in each email
>Select the appropriate resolution
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
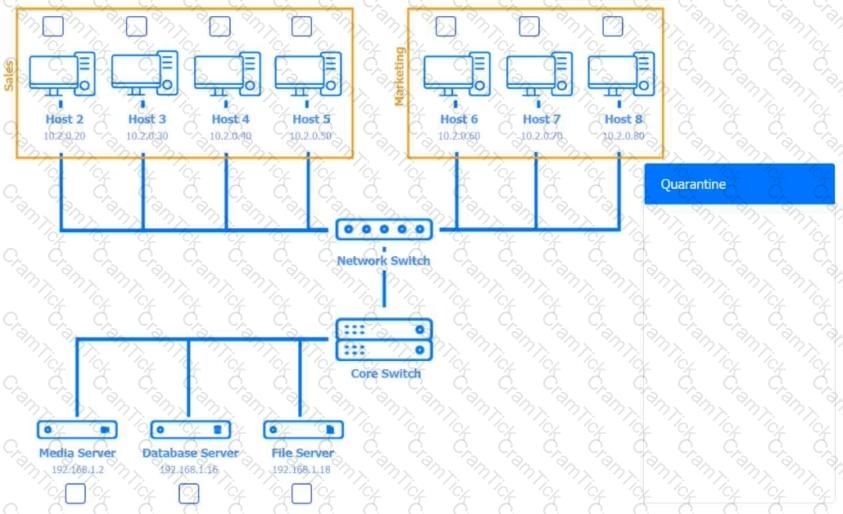
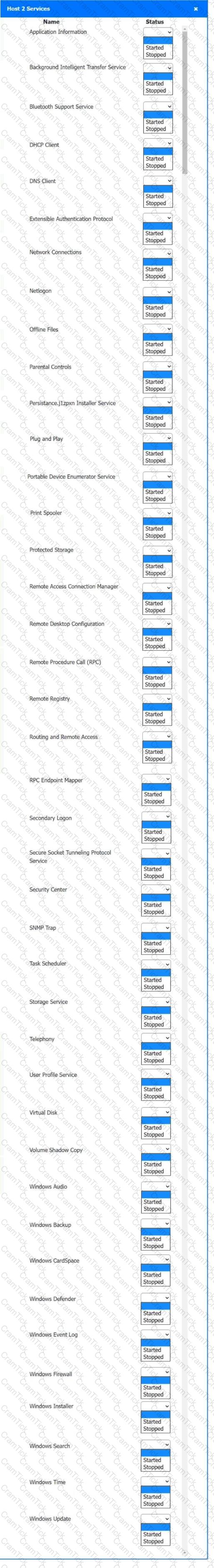
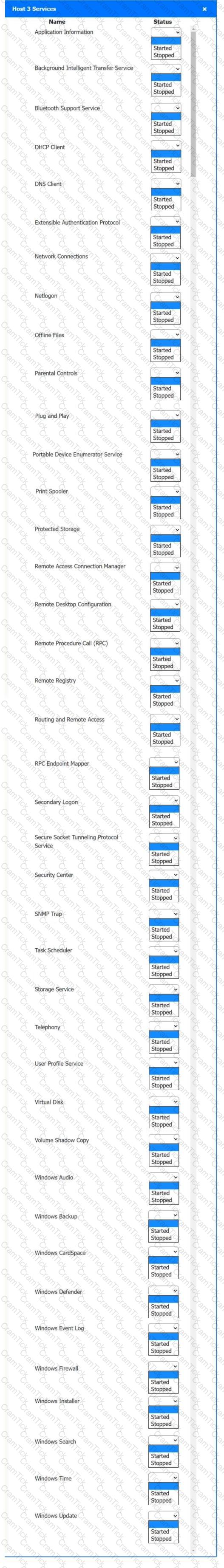
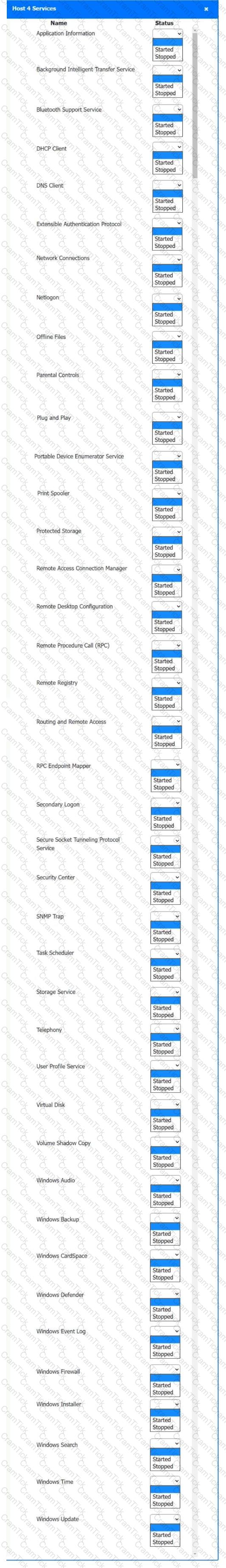
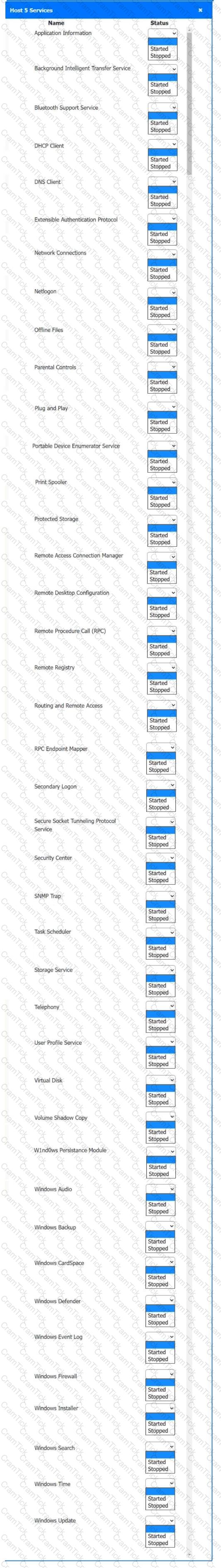
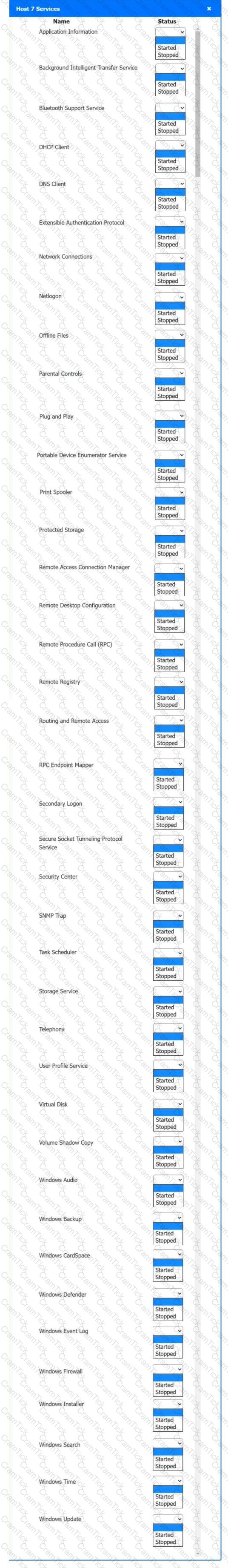
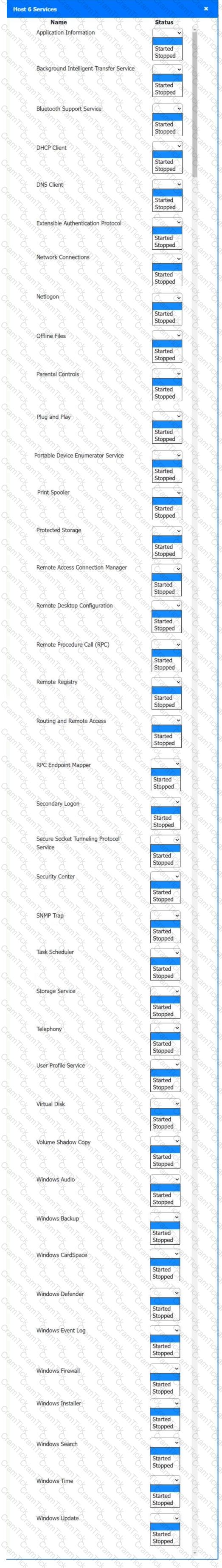
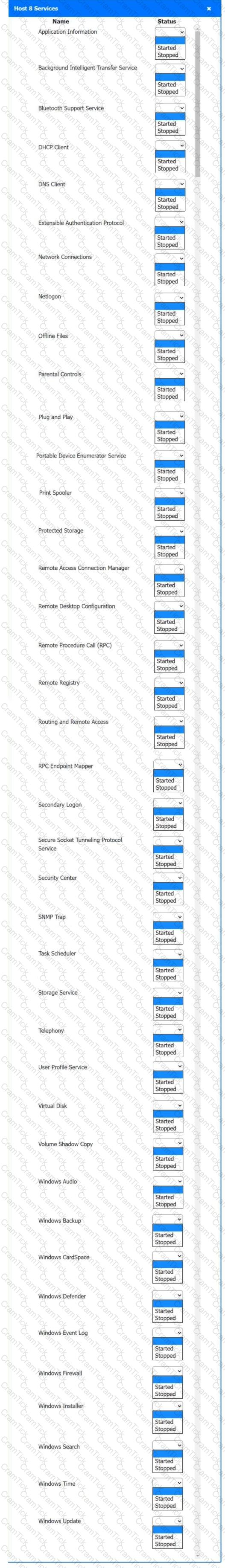
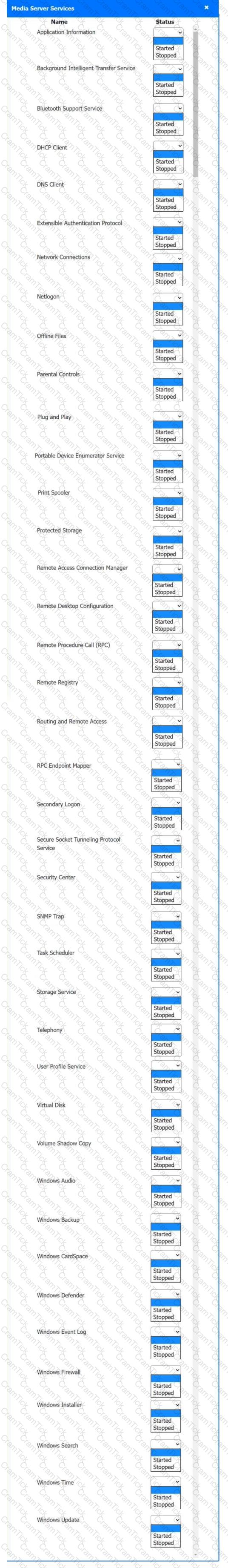
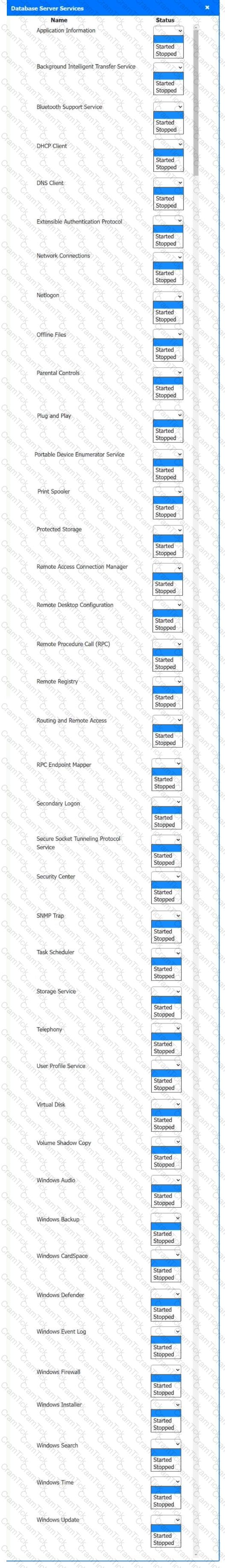
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users’ audio issues are resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
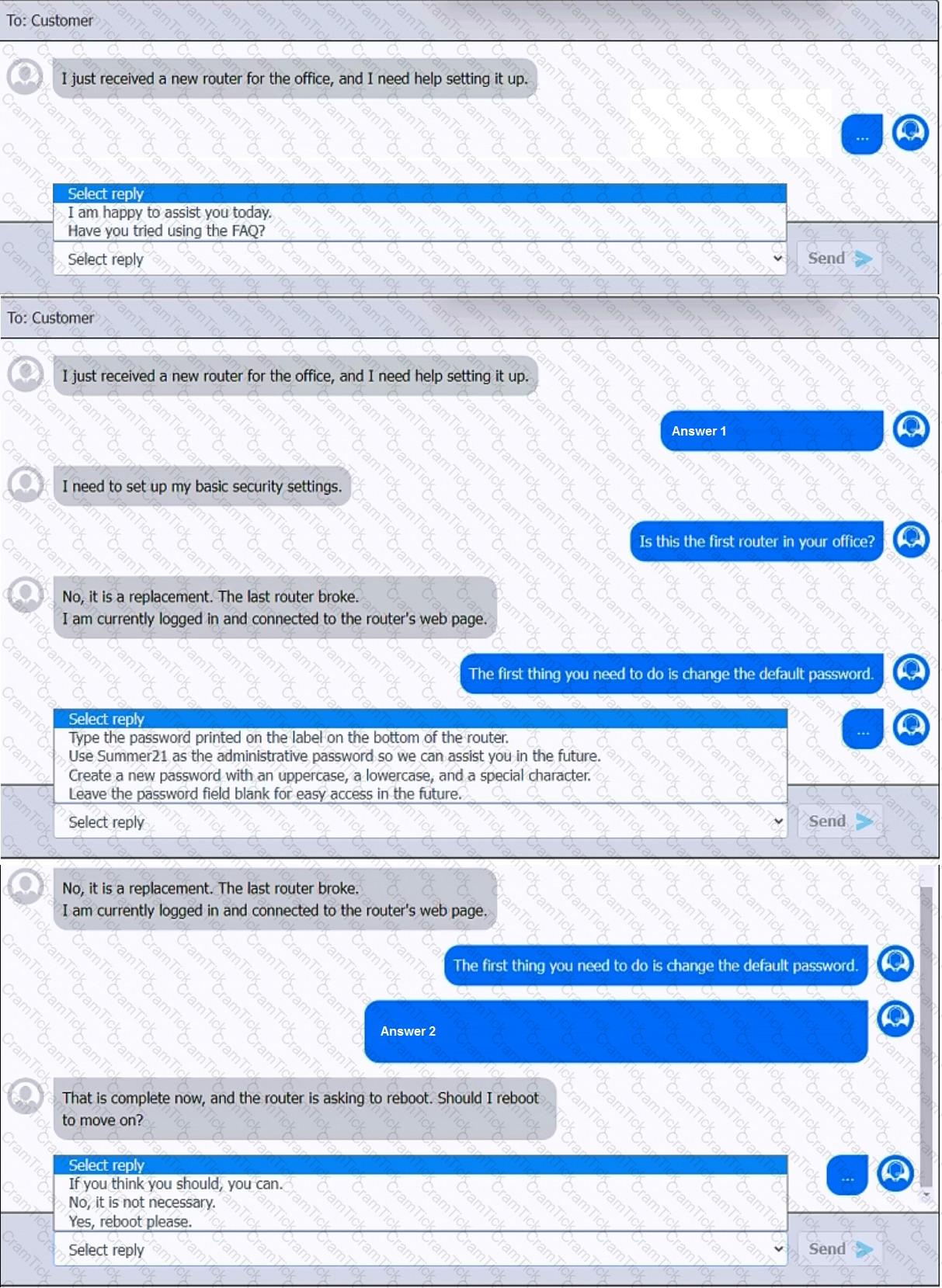
You have been contacted through the help desk chat application. A user is setting up a replacement SOHO router. Assist the user with setting up the router.
INSTRUCTIONS
Select the most appropriate statement for each response. Click the send button after each response to continue the chat.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An end user's laptop is having network drive connectivity issues in the office. The end user submits a help desk ticket, and a support technician is able to establish a remote connection and fix the issue. The following day, however, the network drive is disconnected again. Which of the following should the technician do next?
Which of the following types of social engineering attacks sends an unsolicited text message to a user's mobile device?
Which of the following describes a vulnerability that has been exploited before a patch or remediation is available?
A user logs in daily and cannot print a report. Help desk fixes it each day, but the issue recurs. What should be done so the issue doesn’t recur? (Select two)
A technician needs to disable guest log-ins on domain-joined desktop machines. Which of the following should be used?
A+ |