Refer to the exhibit.
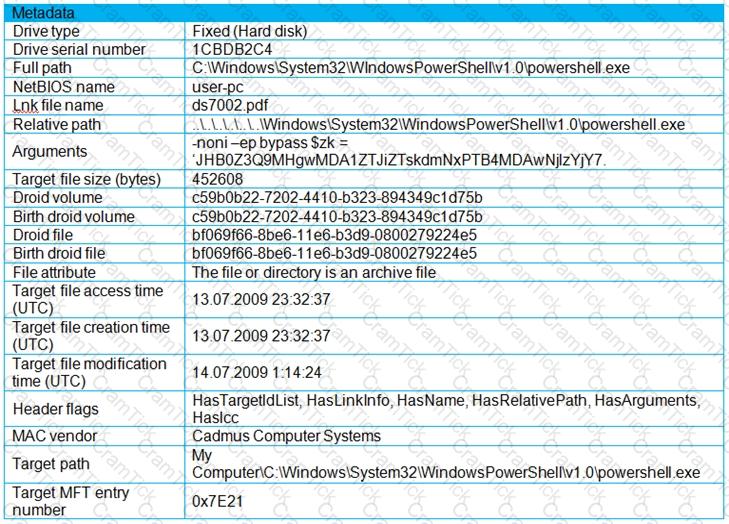
An engineer is analyzing a .LNK (shortcut) file recently received as an email attachment and blocked by email security as suspicious. What is the next step an engineer should take?
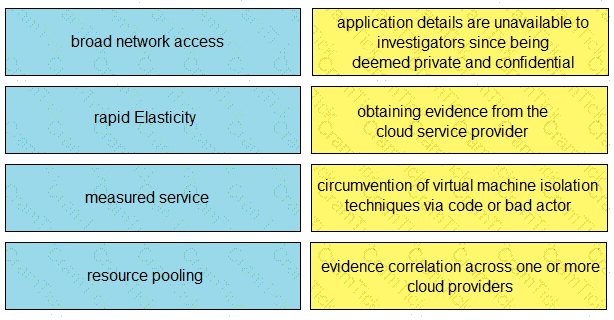
Drag and drop the cloud characteristic from the left onto the challenges presented for gathering evidence on the right.
A security team received an alert of suspicious activity on a user’s Internet browser. The user’s anti-virus software indicated that the file attempted to create a fake recycle bin folder and connect to an external IP address. Which two actions should be taken by the security analyst with the executable file for further analysis? (Choose two.)
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
What is an issue with digital forensics in cloud environments, from a security point of view?
A security team is discussing lessons learned and suggesting process changes after a security breach incident. During the incident, members of the security team failed to report the abnormal system activity due to a high project workload. Additionally, when the incident was identified, the response took six hours due to management being unavailable to provide the approvals needed. Which two steps will prevent these issues from occurring in the future? (Choose two.)
Refer to the exhibit.
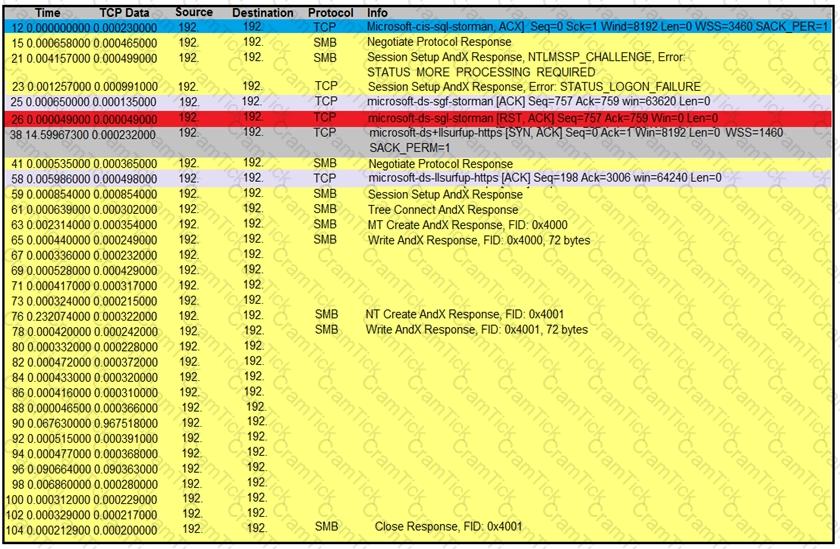
An engineer is analyzing a TCP stream in Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
A threat intelligence report identifies an outbreak of a new ransomware strain spreading via phishing emails that contain malicious URLs. A compromised cloud service provider, XYZCloud, is managing the SMTP servers that are sending the phishing emails. A security analyst reviews the potential phishing emails and identifies that the email is coming from XYZCloud. The user has not clicked the embedded malicious URL. What is the next step that the security analyst should take to identify risk to the organization?
A cybersecurity analyst detects fileless malware activity on secure endpoints. What should be done next?
Refer to the exhibit.

An alert came with a potentially suspicious activity from a machine in HR department. Which two IOCs should the security analyst flag? (Choose two.)
Snort detects traffic that is targeting vulnerabilities in files that belong to software in the Microsoft Office suite. On a SIEM tool, the SOC analyst sees an alert from Cisco FMC. Cisco FMC is implemented with Snort IDs. Which alert message is shown?

Refer to the exhibit. A security analyst notices that a web application running on NGINX is generating an unusual number of log messages. The application is operational and reachable. What is the cause of this activity?
A threat actor attempts to avoid detection by turning data into a code that shifts numbers to the right four times. Which anti-forensics technique is being used?
A new zero-day vulnerability is discovered in the web application. Vulnerability does not require physical access and can be exploited remotely. Attackers are exploiting the new vulnerability by submitting a form with malicious content that grants them access to the server. After exploitation, attackers delete the log files to hide traces. Which two actions should the security engineer take next? (Choose two.)
Refer to the exhibit.
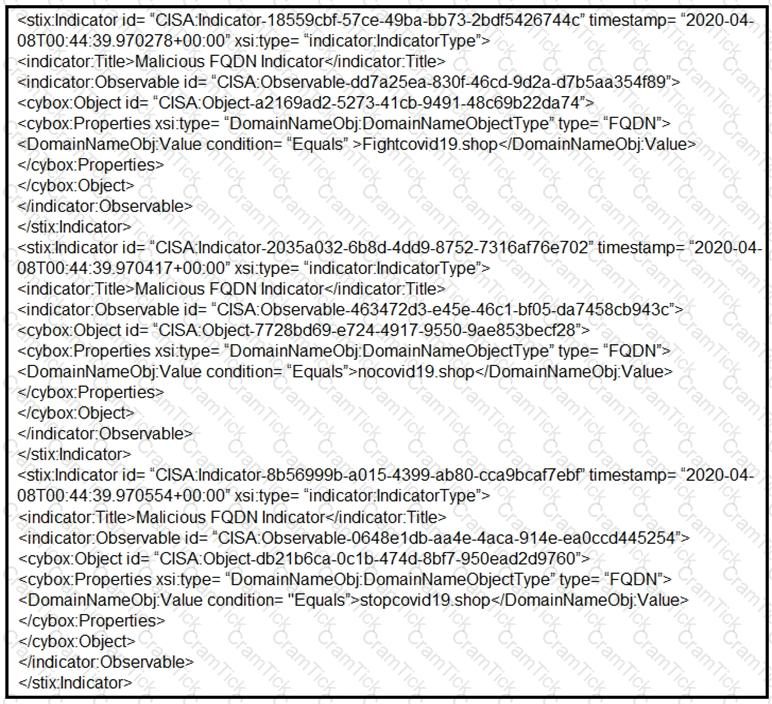
Which two actions should be taken based on the intelligence information? (Choose two.)
Which two tools conduct network traffic analysis in the absence of a graphical user interface? (Choose two.)
Refer to the exhibit.
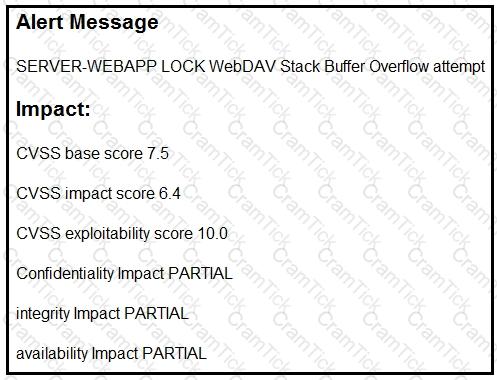
After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business-critical, web-based application and violated its availability. Which two mitigation techniques should the engineer recommend? (Choose two.)
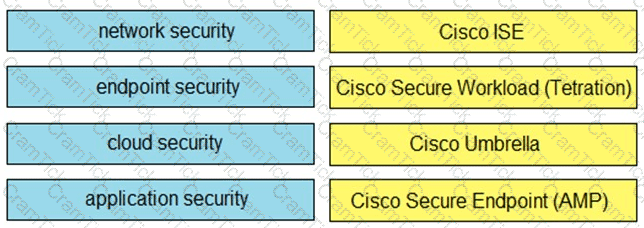
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
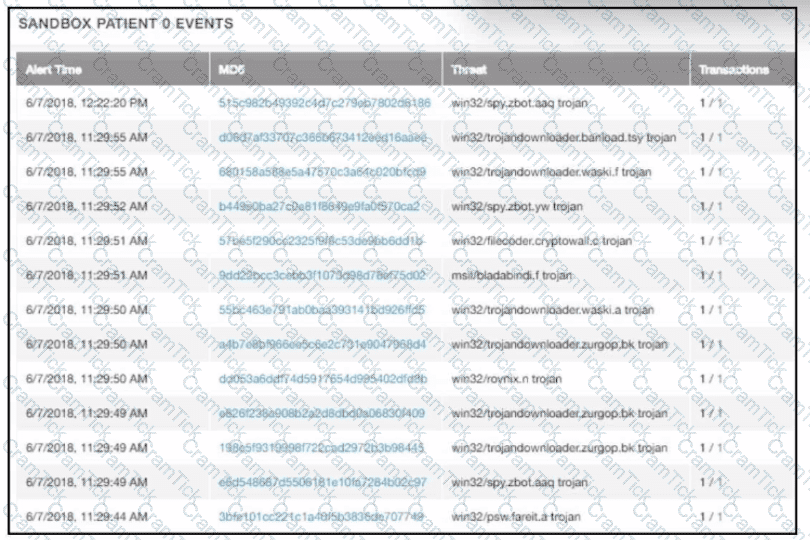
multiple machines behave abnormally. A sandbox analysis reveals malware. What must the administrator determine next?
CyberOps Professional | 300-215 Written Exam | 300-215 Questions Answers | 300-215 Test Prep | 300-215 CyberOps Professional Actual Questions | Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) Exam Questions PDF | CyberOps Professional Free Questions | 300-215 Online Exam | 300-215 Practice Test | 300-215 PDF | 300-215 CyberOps Professional Dumps | 300-215 Test Questions | 300-215 Study Material | 300-215 Exam Preparation | 300-215 Valid Dumps | 300-215 Real Questions | 300-215 CyberOps Professional Practice Test | CyberOps Professional 300-215 Dumps | Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) Exam Questions


