Which two responses from the RADIUS server to NAS are valid during the authentication process? (Choose two)
A network administrator adds network access devices to Cisco ISE. After a security breach, the management team mandates that all network devices must comply with certain standards. All network devices must authenticate through Cisco ISE. Some devices use nondefault CoA ports.
What must be configured in Cisco ISE?
The security engineer for a company has recently deployed Cisco ISE to perform centralized authentication of all network device logins using TACACS+ against the local AD domain. Some of the other network engineers are having a hard time remembering to enter their AD account password instead of the local admin password that they have used for years. The security engineer wants to change the password prompt to "Use Local AD Password:" as a way of providing a hint to the network engineers when logging in. Under which page in Cisco ISE would this change be made?
NO: 37
In which two ways can users and endpoints be classified for TrustSec?
(Choose Two.)
An enterprise uses a separate PSN for each of its four remote sites. Recently, a user reported receiving an "EAP-TLS authentication failed" message when moving between remote sites. Which configuration must be applied on Cisco ISE?
A customer wants to set up the Sponsor portal and delegate the authentication flow to a third party for added security while using Kerberos Which database should be used to accomplish this goal?
A network administrator must configure Cisco SE Personas in the company to share session information via syslog. Which Cisco ISE personas must be added to syslog receivers to accomplish this goal?
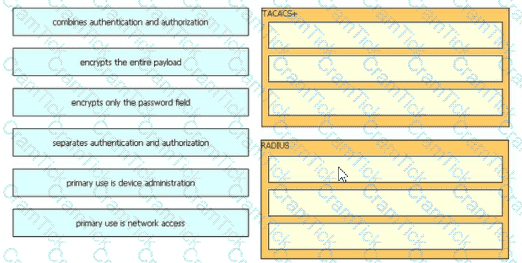
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.
An administrator replaced a PSN in the distributed Cisco ISE environment. When endpoints authenticate to it, the devices are not getting the right profiles or attributes and as a result, are not hitting the correct policies. This was working correctly on the previous PSN. Which action must be taken to ensure the endpoints get identified?
A user changes the status of a device to stolen in the My Devices Portal of Cisco ISE. The device was originally onboarded in the BYOD wireless Portal without a certificate. The device is found later, but the user cannot re-onboard the device because Cisco ISE assigned the device to the Blocklist endpoint identity group. What must the user do in the My Devices Portal to resolve this issue?
An administrator is troubleshooting an endpoint that is supposed to bypass 802 1X and use MAB. The endpoint is bypassing 802.1X and successfully getting network access using MAB. however the endpoint cannot communicate because it cannot obtain an IP address. What is the problem?
An engineer is configuring 802.1X and is testing out their policy sets. After authentication, some endpoints are given an access-reject message but are still allowed onto the network. What is causing this issue to occur?
An administrator is trying to collect metadata information about the traffic going across the network to gam added visibility into the hosts. This Information will be used to create profiling policies for devices us mg Cisco ISE so that network access policies can be used What must be done to accomplish this task?
An organization has a fully distributed Cisco ISE deployment When implementing probes, an administrator must scan for unknown endpoints to learn the IP-to-MAC address bindings. The scan is complete on one FPSN. but the information is not available on the others. What must be done to make the information available?
What are two differences between the RADIUS and TACACS+ protocols'? (Choose two.)
A network administrator must use Cisco ISE to check whether endpoints have the correct version of antivirus installed Which action must be taken to allow this capability?
An administrator is configuring sponsored guest access using Cisco ISE Access must be restricted to the sponsor portal to ensure that only necessary employees can issue sponsored accounts and employees must be classified to do so What must be done to accomplish this task?
ESTION NO: 100
An organization wants to improve their BYOD processes to have Cisco ISE issue certificates to the BYOD endpoints. Currently, they have an active certificate authority and do not want to replace it with Cisco ISE. What must be configured within Cisco ISE to accomplish this goal?
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? (Choose two.)
An engineer is assigned to enhance security across the campus network. The task is to enable MAB across all access switches in the network. Which command must be entered on the switch to enable MAB?
During BYOD flow, from where does a Microsoft Windows PC download the Network Setup Assistant?
Which two features must be used on Cisco ISE to enable the TACACS. feature? (Choose two)
An engineer is implementing Cisco ISE and needs to configure 802.1X. The port settings are configured for port-based authentication. Which command should be used to complete this configuration?
Refer to the exhibit.

Which switch configuration change will allow only one voice and one data endpoint on each port?
An engineer is testing Cisco ISE policies in a lab environment with no support for a deployment server. In order to push supplicant profiles to the workstations for testing, firewall ports will need to be opened. From which Cisco ISE persona should this traffic be originating?
An engineer must use Cisco ISE to provide network access to endpoints that cannot support 802.1X. The endpoint MAC addresses must be allowlisted by configuring an endpoint identity group. These configurations were performed:
Configured an identity group named allowlist
Configured the endpoints to use the MAC address of incompatible 802.1X devices
Added the endpoints to the allowlist identity group
Configured an authentication policy for MAB users
What must be configured?
An engineer is deploying a new guest WLAN for a company. The company wants this WLAN to use a sponsored guest portal for secure guest access. The wireless LAN controller must direct the guests to a web page on Cisco ISE for authentication. Which type of authentication must be configured for the guest portal in Cisco ISE?
A Cisco ISE administrator must restrict specific endpoints from accessing the network while in closed mode. The requirement is to have Cisco ISE centrally store the endpoints to restrict access from. What must be done to accomplish this task''
An administrator has added a new Cisco ISE PSN to their distributed deployment. Which two features must the administrator enable to accept authentication requests and profile the endpoints correctly, and add them to their respective endpoint identity groups? (Choose two )
An engineer must organize endpoints in a Cisco ISE identity management store to improve the operational management of IP phone endpoints. The endpoints must meet these requirements:
• classify endpoints for finance, sales, and marketing departments
• tag each endpoint as profiled
Which action organizes the endpoints?
An administrator is configuring a switch port for use with 802 1X What must be done so that the port will allow voice and multiple data endpoints?
A network engineer needs to deploy 802.1x using Cisco ISE in a wired network environment where thin clients download their system image upon bootup using PXE. For which mode must the switch ports be configured?
A network administrator is configuring a secondary cisco ISE node from the backup configuration of the primary cisco ISE node to create a high availability pair The Cisco ISE CA certificates and keys must be manually backed up from the primary Cisco ISE and copied into the secondary Cisco ISE Which command most be issued for this to work?
An engineer is configuring 802.1X and wants it to be transparent from the users' point of view. The implementation should provide open authentication on the switch ports while providing strong levels of security for non-authenticated devices. Which deployment mode should be used to achieve this?
A network engineer is configuring Cisco TrustSec and needs to ensure that the Security Group Tag is being transmitted between two devices Where in the Layer 2 frame should this be verified?
An administrator is configuring TACACS+ on a Cisco switch but cannot authenticate users with Cisco ISE. The configuration contains the correct key of Cisc039712287. but the switch is not receiving a response from the Cisco ISE instance What must be done to validate the AAA configuration and identify the problem with the TACACS+ servers?
An administrator is editing a csv list of endpoints and wants to reprofile some of the devices indefinitely before importing the list into Cisco ISE. Which field and Boolean value must be changed for the devices before the list is reimported?
A network engineer must configure a policy rule to check the endpoint. The policy must ensure disk encryption is enabled and the appropriate antivirus software version is installed. Which configuration must the engineer apply to the rule?
Refer to the exhibit:
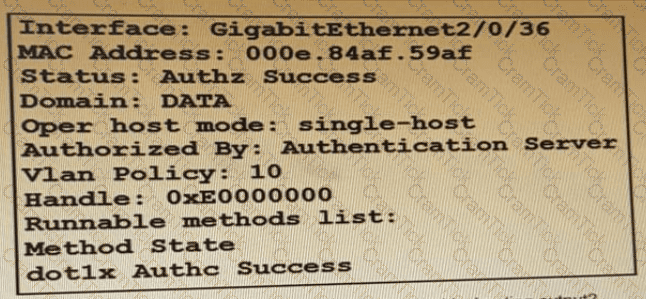
Which command is typed within the CU of a switch to view the troubleshooting output?
An engineer is configuring Cisco ISE to reprofile endpoints based only on new requests of INIT-REBOOT and SELECTING message types. Which probe should be used to accomplish this task?
An administrator must deploy the Cisco Secure Client posture agent to employee endpoints that access a wireless network by using URL redirection in Cisco ISE. The compliance module must be downloaded from Cisco and uploaded to the Cisco ISE client provisioning resource. What must be used to upload the compliance module?
What are two requirements of generating a single signing in Cisco ISE by using a certificate provisioning portal, without generating a certificate request? (Choose two )
A network engineer must configure BYOD using Cisco ISE. In the deployment, the users must be able to submit CSR through the end devices. Which two features must be enabled to meet the requirement?
(Choose two.)
An engineer is configuring the remote access VPN to use Cisco ISE for AAA and needs to conduct posture checks on the connecting endpoints After the endpoint connects, it receives its initial authorization result and continues onto the compliance scan What must be done for this AAA configuration to allow compliant access to the network?
What is the maximum number of PSN nodes supported in a medium-sized deployment?
An adminístrator is migrating device administration access to Cisco ISE from the legacy TACACS+ solution that used only privilege 1 and 15 access levels. The organization requires more granular controls of the privileges and wants to customize access levels 2-5 to correspond with different roles and access needs. Besides defining a new shell profile in Cisco ISE. what must be done to accomplish this configuration?
An engineer is deploying Cisco ISE in a network that contains an existing Cisco Secure Firewall ASA. The customer requested that Cisco TrustSec be configured so that Cisco ISE and the firewall can share SGT information.
Which protocol must be configured on Cisco ISE to meet the requirement?
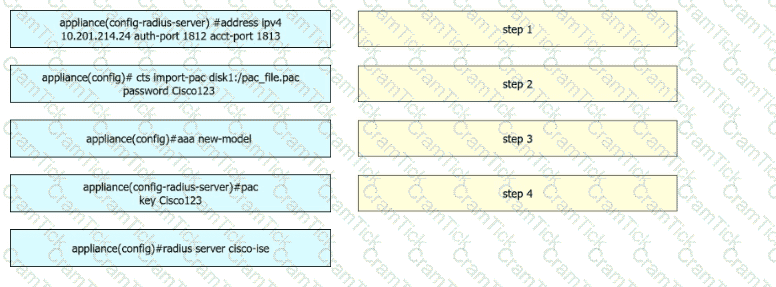
A security engineer configures a Cisco Catalyst switch to use Cisco TrustSec. The engineer must define the PAC key to authenticate the switch to Cisco IISE. Drag and drop the commands from the left into sequence on the right. Not all options are used.
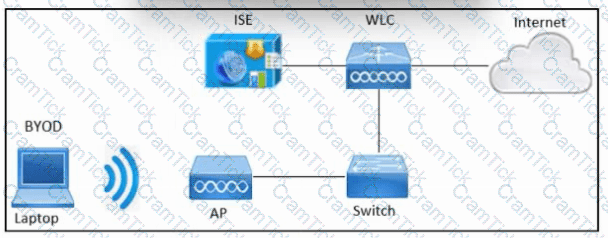
Refer to the exhibit. An engineer must configure BYOD in Cisco ISE. A single SSID must be used to allow BYOD devices to connect to the network. These configurations have been performed on Wireless LAN Controller already:
RADIUS server
BYOD-Dot1x SSID
Which two configurations must be done in Cisco ISE to meet the requirement? (Choose two.)
An administrator is configuring a Cisco WLC for web authentication Which two client profiling methods are enabled by default if the Apply Cisco ISE Default Settings check box has been selected'? (Choose two.)
Refer to the exhibit.
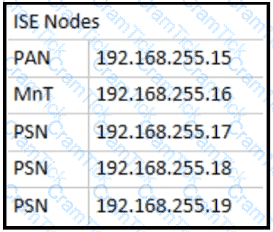
Which two configurations are needed on a catalyst switch for it to be added as a network access device in a Cisco ISE that is being used for 802 1X authentications? (Choose two )
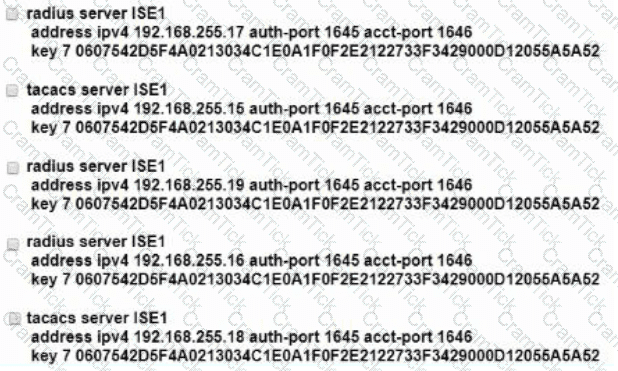
A security administrator is using Cisco ISE to create a BYOD onboarding solution for all employees who use personal devices on the corporate network. The administrator generates a Certificate Signing Request and signs the request using an external Certificate Authority server. Which certificate usage option must be selected when importing the certificate into ISE?
An administrator is configuring posture with Cisco ISE and wants to check that specific services are present on the workstations that are attempting to access the network. What must be configured to accomplish this goal?
What sends the redirect ACL that is configured in the authorization profile back to the Cisco WLC?
An administrator is manually adding a device to a Cisco ISE identity group to ensure that it is able to access the network when needed without authentication Upon testing, the administrator notices that the device never hits the correct authorization policy line using the condition EndPoints LogicalProfile EQUALS static_list Why is this occurring?
An administrator is configuring a new profiling policy within Cisco ISE The organization has several endpoints that are the same device type and all have the same Block ID in their MAC address. The profiler does not currently have a profiling policy created to categorize these endpoints. therefore a custom profiling policy must be created Which condition must the administrator use in order to properly profile an ACME Al Connector endpoint for network access with MAC address
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information — system-description and platform-type — to profile Cisco IP phones and allow access.
Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
An engineer is configuring Cisco ISE and needs to dynamically identify the network endpoints and ensure that endpoint access is protected. Which service should be used to accomplish this task?
Profiling
An organization is migrating its current guest network to Cisco ISE and has 1000 guest users in the current database There are no resources to enter this information into the Cisco ISE database manually. What must be done to accomplish this task effciently?
An engineer is unable to use SSH to connect to a switch after adding the required CLI commands to the device to enable TACACS+. The device administration license has been added to Cisco ISE, and the required policies have been created. Which action is needed to enable access to the switch?
A network administrator is currently using Cisco ISE to authenticate devices and users via 802 1X There is now a need to also authorize devices and users using EAP-TLS. Which two additional components must be configured in Cisco ISE to accomplish this'? (Choose two.)
A network administrator has just added a front desk receptionist account to the Cisco ISE Guest Service sponsor group. Using the Cisco ISE Guest Sponsor Portal, which guest services can the receptionist provide?
An engineer is migrating users from MAB to 802.1X on the network. This must be done during normal business hours with minimal impact to users. Which CoA method should be used?
A user reports that the RADIUS accounting packets are not being seen on the Cisco ISE server.
Which command is the user missing in the switch’s configuration?
What allows an endpoint to obtain a digital certificate from Cisco ISE during a BYOD flow?
An administrator is configuring RADIUS on a Cisco switch with a key set to Cisc403012128 but is receiving the error “Authentication failed: 22040 Wrong password or invalid shared secret. “what must be done to address this issue?
An engineer is configuring ISE for network device administration and has devices that support both protocols. What are two benefits of choosing TACACS+ over RADUs for these devices? (Choose two.)
A network administrator is configuring client provisioning resource policies for client machines and must ensure that an agent pop-up is presented to the client when attempting to connect to the network Which configuration item needs to be added to allow for this'?
A network engineer needs to ensure that the access credentials are not exposed during the 802.1x authentication among components. Which two protocols should complete this task?
An engineer must configure guest access on Cisco ISE for company visitors. Which step must be taken on the Cisco ISE PSNs before a guest portal is configured?
An engineer is configuring a posture policy for Windows 10 endpoints and wants to ensure that users in each AD group have different conditions to meet to be compliant. What must be done to accomplish this task?
What must be configured on the WLC to configure Central Web Authentication using Cisco ISE and a WLC?
An administrator is attempting to join a new node to the primary Cisco ISE node, but receives the error message "Node is Unreachable". What is causing this error?
An administrator made changes in Cisco ISE and needs to apply new permissions for endpoints that have already been authenticated by sending a CoA packet to the network devices. Which IOS command must be configured on the devices to accomplish this goal?
CCNP Security | 300-715 Written Exam | 300-715 Questions Answers | 300-715 Test Prep | 300-715 CCNP Security Actual Questions | Implementing and Configuring Cisco Identity Services Engine (SISE) Exam Questions PDF | 300-715 Online Exam | 300-715 Practice Test | 300-715 PDF | 300-715 CCNP Security Dumps | 300-715 Test Questions | 300-715 Study Material | 300-715 Exam Preparation | 300-715 Valid Dumps | 300-715 Real Questions | 300-715 CCNP Security Practice Test | CCNP Security 300-715 Dumps | Implementing and Configuring Cisco Identity Services Engine (SISE) Exam Questions


