An engineer wants to utilize a digital signature in outgoing emails to validate to others that the email they are receiving was indeed sent and authorized by the owner of that domain Which two components should be configured on the Cisco Secure Email Gateway appliance to achieve this? (Choose two.)
A content dictionary was created for use with Forged Email Detection. Proper data that pertains to the CEO Example CEO:
What is the order of virus scanning when multilayer antivirus scanning is configured?
A list of company executives is routinely being spoofed, which puts the company at risk of malicious email attacks An administrator must ensure that executive messages are originating from legitimate sending addresses Which two steps must be taken to accomplish this task? (Choose two.)
An administrator identifies that, over the past week, the Cisco ESA is receiving many emails from certain senders and domains which are being consistently quarantined. The administrator wants to ensure that these senders and domain are unable to send anymore emails.
Which feature on Cisco ESA should be used to achieve this?
Which two certificate authority lists are available in Cisco ESA? (Choose two.)
An administrator notices that the Cisco Secure Email Gateway delivery queue on an appliance is consistently full. After further investigation, it is determined that the IP addresses currently in use by appliance are being rate-limited by some destinations. The administrator creates a new interface with an additional IP address using virtual gateway technology, but the issue is not solved Which configuration change resolves the issue?
An administrator notices that incoming emails with certain attachments do not get delivered to all recipients when the emails have multiple recipients in different domains like cisco.com and test.com. The same emails when sent only to recipients in cisco.com are delivered properly. How must the Cisco Secure Email Gateway be configured to avoid this behavior?
An engineer is tasked with creating a content filter to catch attachments, including credit card numbers, and hold them for review until further action is taken. Which component on a Cisco Secure Email Gateway must be configured to meet this requirement?
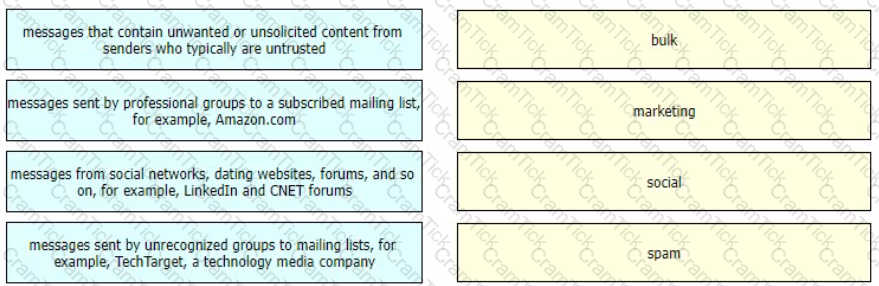
Drag and drop the graymail descriptions from the left onto the verdict categories they belong to on the right.
Which two features of Cisco Email Security are added to a Sender Group to protect an organization against email threats? (Choose two.)
A Cisco Secure Email Gateway administrator recently enabled the Outbreak Filters Global Service Setting to detect Viral as well as Non-Viral threat detection, with no detection of Non-viral threats after 24 hours of monitoring Outbreak Filters What is the reason that Non-Viral threat detection is not detecting any positive verdicts?
An Encryption Profile has been set up on the Cisco ESA.
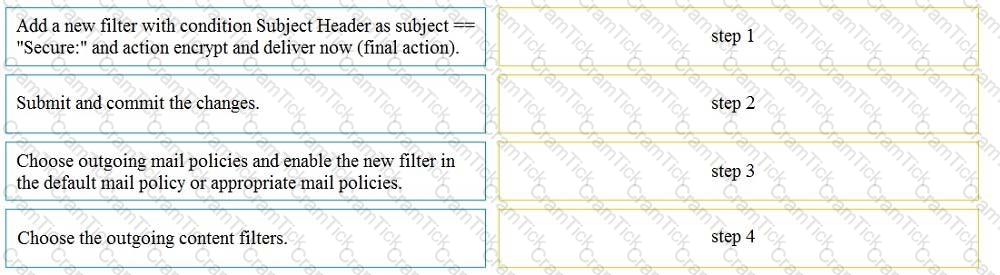
Drag and drop the steps from the left for creating an outgoing content filter to encrypt emails that contains the subject "Secure:" into the correct order on the right.
A network administrator is modifying an outgoing mail policy to enable domain protection for the organization. A DNS entry is created that has the public key.
Which two headers will be used as matching criteria in the outgoing mail policy? (Choose two.)
When email authentication is configured on Cisco ESA, which two key types should be selected on the signing profile? (Choose two.)
An organization wants to use its existing Cisco ESA to host a new domain and enforce a separate corporate policy for that domain.
What should be done on the Cisco ESA to achieve this?
When the Spam Quarantine is configured on the Cisco ESA, what validates end-users via LDAP during login to the End-User Quarantine?
Which feature must be activated on a Cisco Secure Email Gateway to combat backscatter?
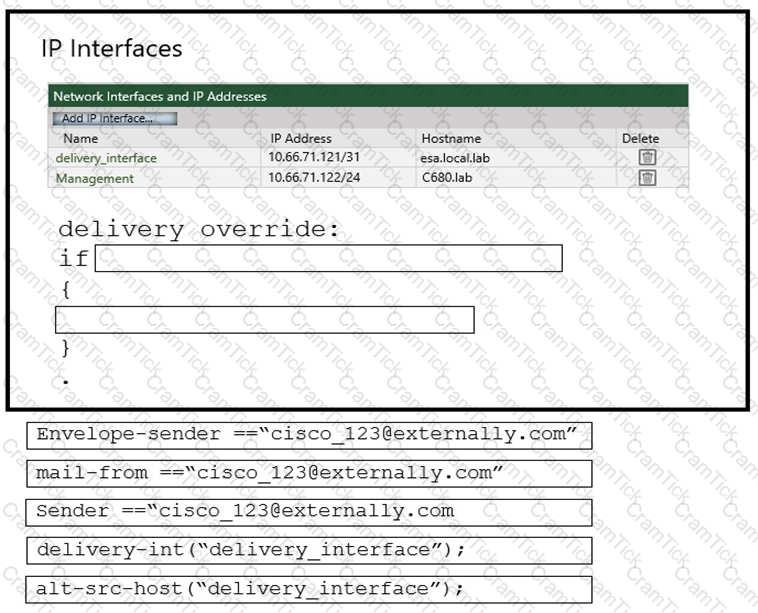
An administrator must ensure that emails sent from cisco_123@externally.com are routed through an alternate virtual gateway. Drag and drop the snippet from the bottom onto the blank in the graphic to finish the message filter syntax. Not all snippets are used.
What is the maximum message size that can be configured for encryption on the Cisco ESA?
An organization wants to prevent proprietary patent documents from being shared externally via email. The network administrator reviewed the DLP policies on the Cisco Secure Email Gateway and could not find an existing policy with the appropriate matching patterns. Which type of DLP policy template must be used to create a policy that meets this requirement?
A Cisco Secure Email Gateway administrator must provide outbound email authenticity and configures a DKIM signing profile to handle this task. What is the next step to allow this organization to use DKIM for their outbound email?
Which two features of Cisco Email Security are added to a Sender Group to protect an organization against email threats? (Choose two.)
Which component must be added to the content filter to trigger on failed SPF Verification or DKIM Authentication verdicts?
Email encryption is configured on a Cisco ESA that uses CRES.
Which action is taken on a message when CRES is unavailable?
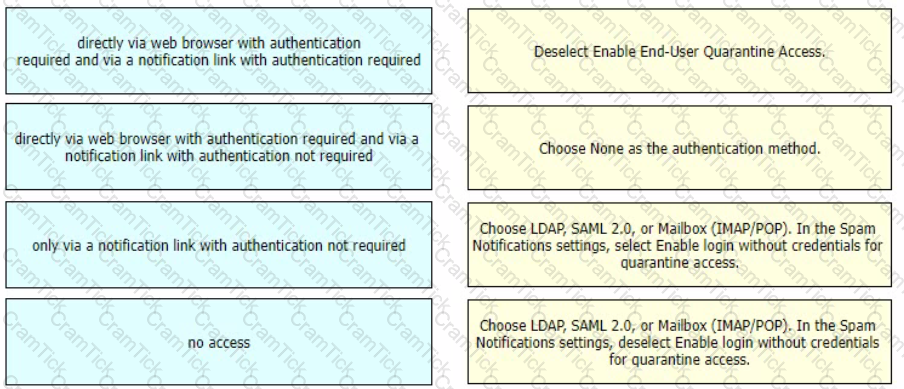
Drag and drop authentication options for End-User Quarantine Access from the left onto the corresponding configuration steps on the right.
The company security policy requires that the finance department have an easy way to apply encryption to their outbound messages that contain sensitive data Users must be able to flag the messages that require encryption versus a Cisco Secure Email Gateway appliance scanning all messages and automatically encrypting via detection Which action enables this capability?
Spammers routinely try to send emails with the recipient field filled with a list of all possible combinations of letters and numbers. These combinations, appended with a company domain name are malicious attempts at learning all possible valid email addresses. Which action must be taken on a Cisco Secure Email Gateway to prevent this from occurring?
An engineer tries to implement phishing simul-ations to test end users, but they are being blocked by the Cisco Secure Email Gateway appliance. Which two components, when added to the allow list, allow these simul-ations to bypass antispam scanning? (Choose two.)
A content dictionary was created for use with Forged Email Detection. Proper data that pertains to the CEO Example CEO:
When outbreak filters are configured, which two actions are used to protect users from outbreaks? (Choose two.)
Which two configurations are used on multiple LDAP servers to connect with Cisco ESA? (Choose two.)
An administrator needs to configure Cisco ESA to ensure that emails are sent and authorized by the owner of the domain. Which two steps must be performed to accomplish this task? (Choose two.)
An organization has multiple Cisco Secure Email Gateway appliances deployed, resulting in several spam quarantines to manage. To manage the quarantined messages, the administrator enabled the centralized spam quarantine on the Cisco Secure Email and Web Manager appliance and configured the external spam quarantine on the Cisco Secure Email Gateway appliances. However, messages are still being directed to the local quarantine on the Cisco Secure Email Gateway appliances What change is necessary to complete the configuration?
CCNP Security | 300-720 Written Exam | 300-720 Questions Answers | 300-720 Test Prep | 300-720 CCNP Security Actual Questions | Securing Email with Cisco Email Security Appliance (300-720 SESA) Exam Questions PDF | 300-720 Online Exam | 300-720 Practice Test | 300-720 PDF | 300-720 CCNP Security Dumps | 300-720 Test Questions | 300-720 Study Material | 300-720 Exam Preparation | 300-720 Valid Dumps | 300-720 Real Questions | 300-720 CCNP Security Practice Test | CCNP Security 300-720 Dumps | Securing Email with Cisco Email Security Appliance (300-720 SESA) Exam Questions


