Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is occurring?
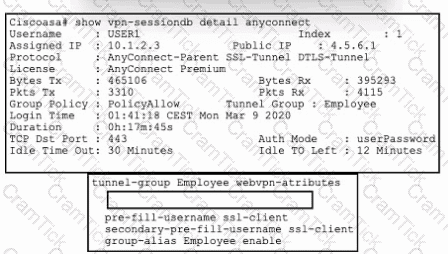
Refer to the exhibit. An engineer must implement a remote access VPN solution that provides user and device verification. The company uses Active Directory for user authentication and ID certificates for device identity. Users are currently able to connect using only a valid username and password, even if their computer is missing the required certificate.
Which command from the Cisco ASA tunnel-group completes the requirement of verifying device identity in addition to user identity?
Which SAFE component logically arranges the security capabilities into blueprints?

Refer to the exhibit. An engineer must create a segmentation policy in Cisco Secure Workload to block HTTP traffic. The indicated configuration was applied; however, HTTP traffic is still allowed. What should be done to meet the requirement?
Which types of algorithm does a web application firewall use for zero-day DDoS protection?
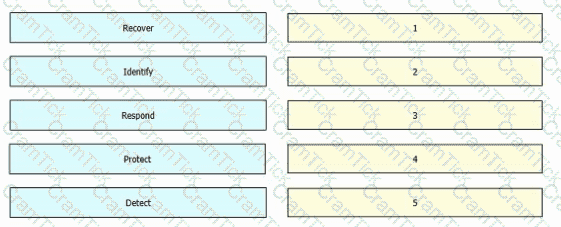
Drag and drop the five core functions from the left into the order defined by the NIST Cyber security Framework on the right.
Which common strategy should be used to mitigate directory traversal attacks in a cloud environment?
A security analyst detects an employee endpoint making connections to a malicious IP on the internet and downloaded a file named Test0511127691C.pdf. The analyst discovers the machine is infected by trojan malware. What must the analyst do to mitigate the threat using Cisco Secure Endpoint?
An administrator received an incident report indicating suspicious activity of a user using a corporate device. The manager requested that the credentials of user user1@cisco.com be reset and synced via the Active Directory. Removing the account should be avoided and used for further investigation on data leak. Which configuration must the administrator apply on the Duo Admin Panel?
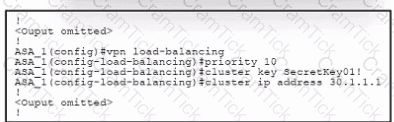
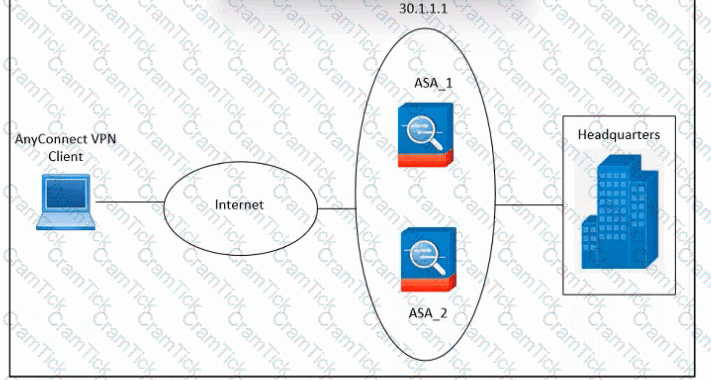
Refer to the exhibit. An engineer must configure VPN load balancing across two Cisco ASA. The indicated configuration was applied to each firewall; however, the load-balancing encryption scheme fails to work. Which two commands must be run on each firewall to meet the requirements? (Choose two.)
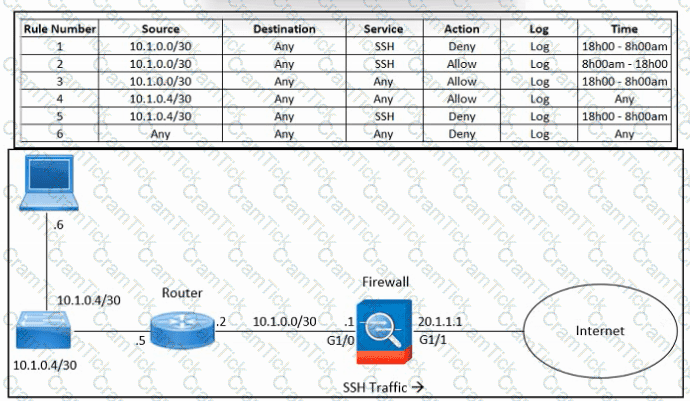
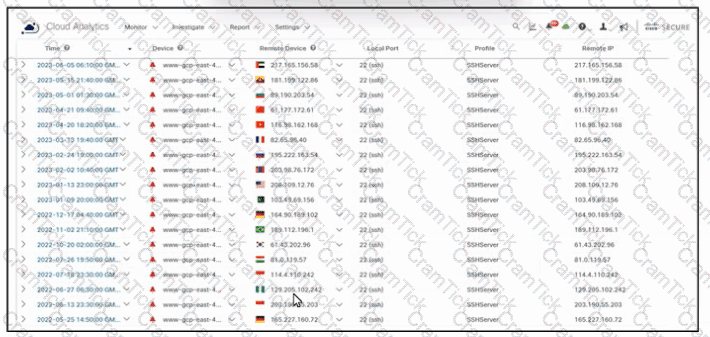
Refer to the exhibit. An engineer must troubleshoot an issue with excessive SSH traffic leaving the internal network between the hours of 18:00 and 08:00. The engineer applies a policy to the Cisco ASA firewall to block outbound SSH during the indicated hours; however, the issue persists. What should be done to meet the requirement?
A recent InfraGard news release indicates the need to establish a risk ranking for all on-premises and cloud services. The ACME Corporation already performs risk assessments for on-premises services and has applied a risk ranking to them. However, the cloud services that were used lack risk rankings. What Cisco Umbrella function should be used to meet the requirement?
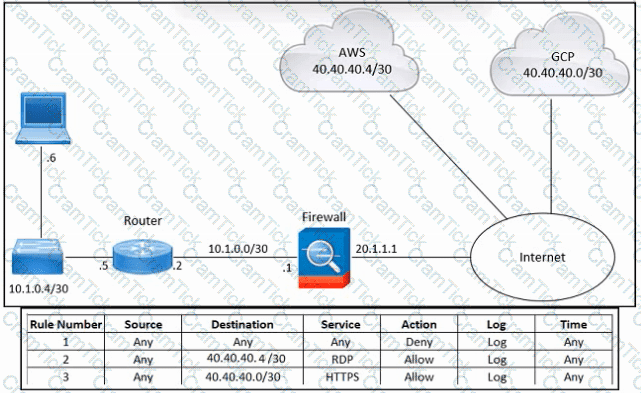
Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The indicated rules were applied to the firewall; however, none of the virtual machines in AWS and Google Cloud Platform are accessible. What should be done to meet the requirement?


