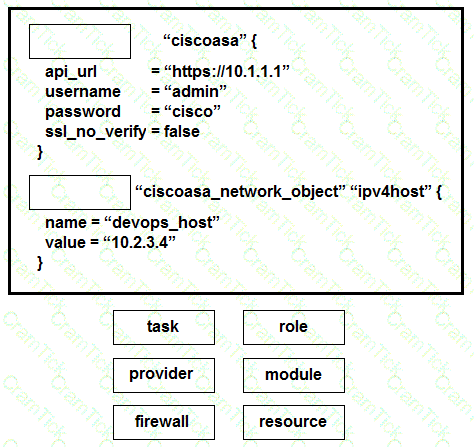
Drag and drop the commands from the bottom onto the correct Terraform code in the exhibit to push a network object to a Cisco ASA Firewall device.
A three-tier web application must be moved to containers. A webserver is already in place, and the middleware container can talk to a central database server. The hostname of the database server is known, but the name of the middleware server must be provided to the webserver.
In which file should the name of the middleware server be configured?
How long analysis systems such as Elasticsearch, Logstash, and Kibana Stack handle ingesting unstructured logs from different devices in various formats?
A DevOps engineer has built a new container and must open port 8080 for intercontainer communication. Which command must be added in a Dockerfile to accomplish this goal?
Which type of testing should be integrated into a CI/CD pipeline to ensure the correct behavior of all of the modules in the source code that were developed using TDD?
Fill in the blanks to complete the statement.
When creating multiple containers, in order to allow communication with each other, you must create a_____________ of type_____________.
ConfigMap keys have been mapped to different file names using the volumes.configMap.items field. What is the result if a wrong ConfigMap key is specified?
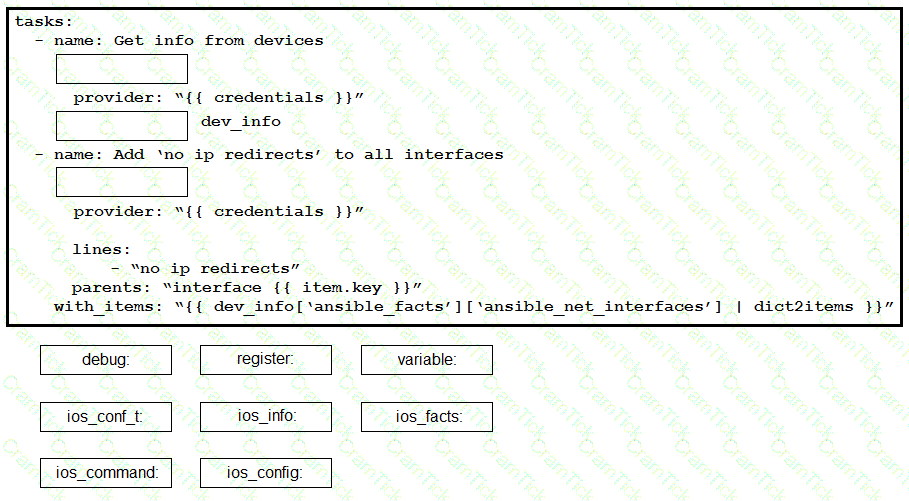
Construct an Ansible script to gather information about target routers and then use it to apply no ip redirects to every interface on each device. Drag and drop the code from the bottom onto the correct location in the exhibit to complete the tasks section of the Ansible playbook so that it accomplishes your goal.
Configuration changes to the production network devices are performed by a CI/CD pipeline. The code repository and the CI tool are running on separate servers. Some configuration changes are pushed to the code repository, but the pipeline did not start.
Why did the pipeline fail to start?
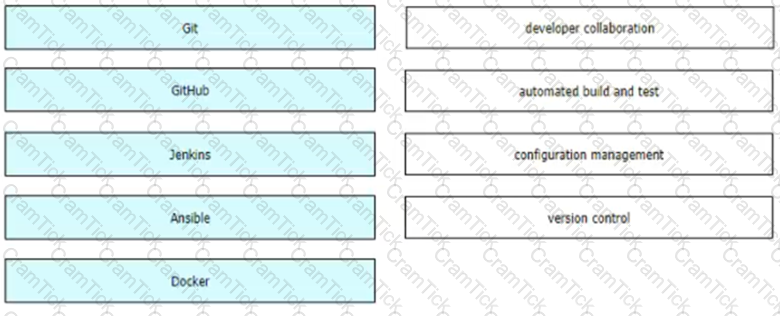
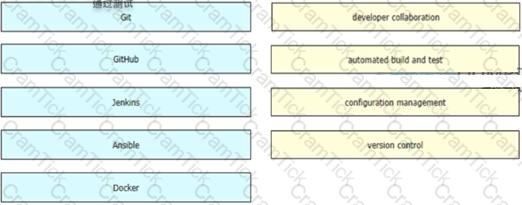
Drag and drop the tools from the left onto the tool's function on the right. Not all options are used.
An interface on a router as a Layer 3 link has been configured to another device by updating an Ansible playbook that is executed via a CI/CD pipeline. The Ansible playbook was written to push the configuration change using the ios_config module. Which automated test validates that the interface is functioning as it should?
A DevOps engineer must build a Docker image to containerize an application. Then the image must be pushed to a repository on Docker Hub in a CI/CD pipeline using GitHub Actions.
Which approach securely encrypts the Docker Hub access token as an environment variable within the CI/CD pipeline?
A DevOps engineer must validate the working state of the network before implementing a CI/CD pipeline model. Which configuration management tool is designed to accomplish this?
A developer has created a deployment that should launch a pod to run their database service. The pod should launch with a metadata name of “Cisco-DB," and the developer has added it to the "Cisco" namespace in their deployment.
Which Kubernetes command confirms that the service is running and usable?
Refer to the exhibit.

The text represents a syslog message sent from a Linux server to a centralized log system.
Based on the format of the log message, how must the functionality of the log parser be extended to improve search capabilities?
A new banking application is being developed as the main currency exchange resource for all the customers on a global scale. The application must comply with the security based on the deployed region. Therefore, the CI/CD pipeline must be created with the highest security possible.
Which approach accomplishes this goal?
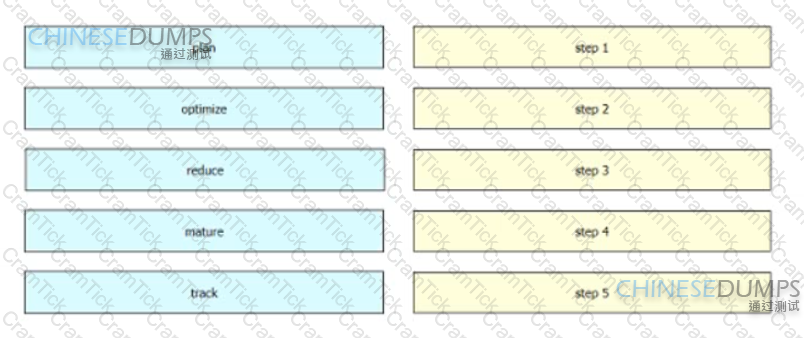
Drag and drop the steps in Garter’s public cloud management framework from the left into the order on the right.
Drag and drop the tools from the left onto the tools function on the right Not all options are used.
When DevOps practices are integrated into an existing organization, which two characteristics are positive indicators of DevOps maturity? (Choose two.)
Fill in the blank to complete the statement.
A user wants a Kubernetes deployment to run three separate pods of a web application at one time. In the deployment YAML, the user must configure the___________field in the________subsection.
Refer to the exhibit.
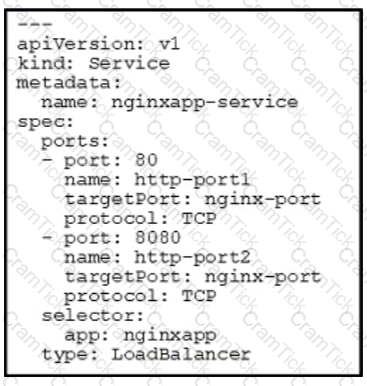
What are the properties of the load balancer in a Kubernetes environment?
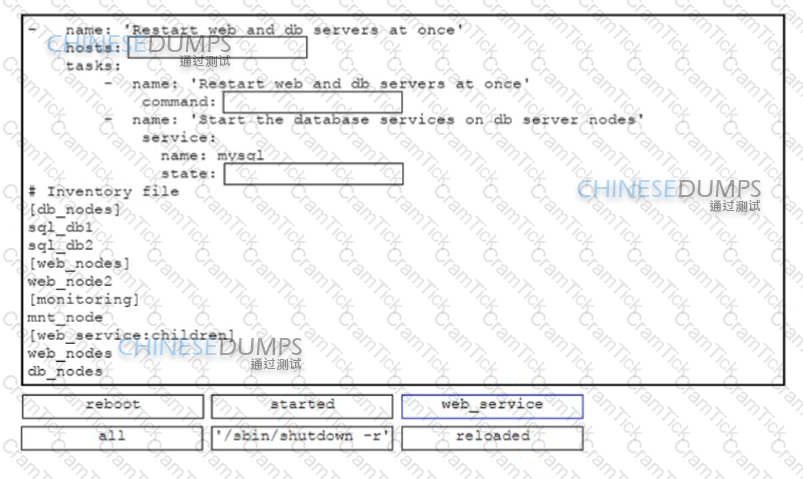
Drag and drop the code snippets from the bottom onto the boxes in the code in the Ansible playbook to restart multiple services in the correct sequence Not all options are used
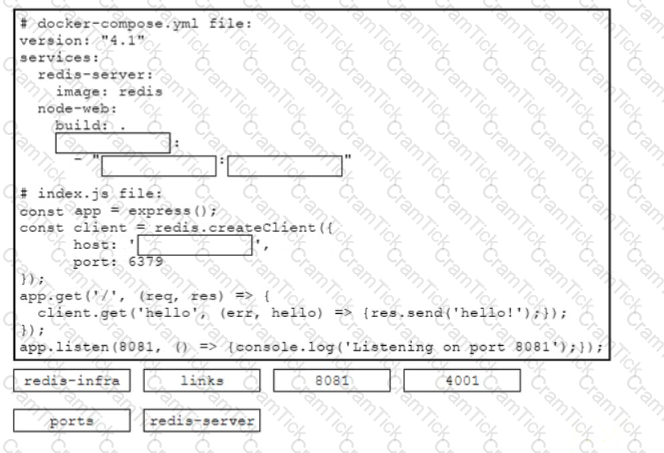
Drag and drop the code snippets from the bottom onto the boxes in the code to complete the docker-compose y ml and the mdex.js files to enable network communication between the containers of a Redis instance and a Node js web application The application must be reachable on the host via port 4001 Not all options are used
Refer to the exhibit.
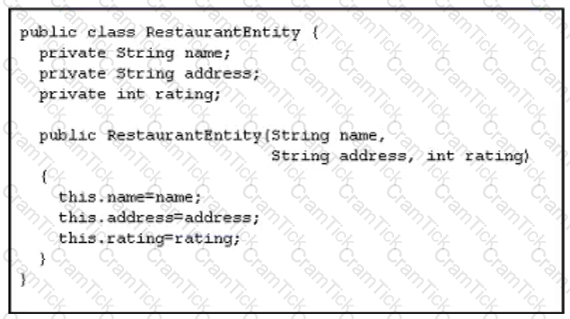
An application has been developed as a fileserver. To create this application as a fileserver. the class is used to store data in an SQL database.
Which two steps help minimize the risk of attack and compromise of the application? (Choose two.)
An application is being developed to be used by the HR department of a company on a global scale. The application will be used as a central repository for employee contracts. For user access, a RADIUS server will be used with authorized user groups.
Which action must be used to prevent developers from accidentally committing secrets in the code?
Refer to the exhibit.
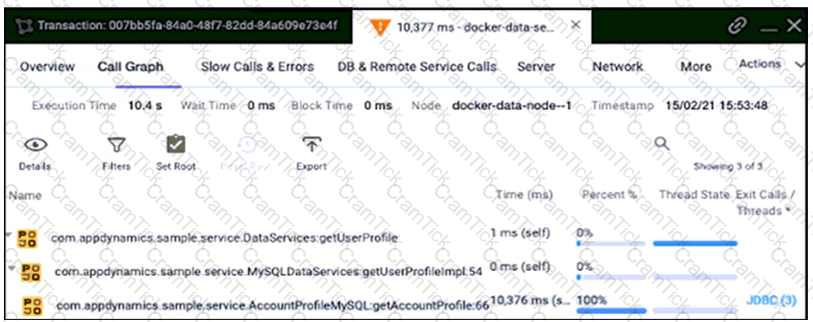
A distributed application contains data services that connect to databases via JDBC and to other remote services via HTTP. The overall response time is too long, and AppDynamics is used to investigate the root cause. From the application flow map, a specific data service running on Docker has been identified whose response time is over 10 seconds.
Which action resolves the issue?
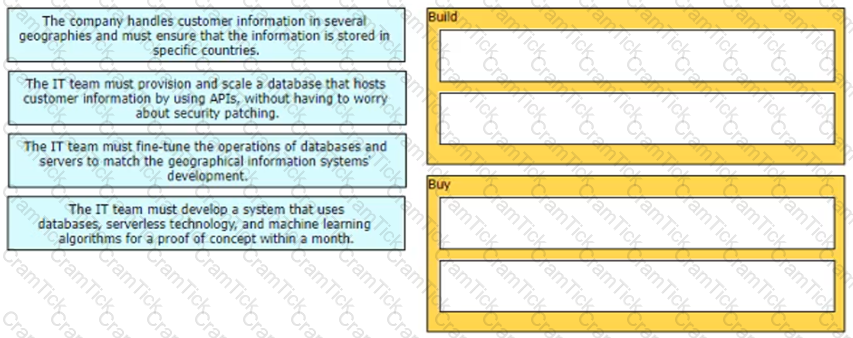
Drag and drop the scenarios from the left onto the cloud strategy categories on the right.
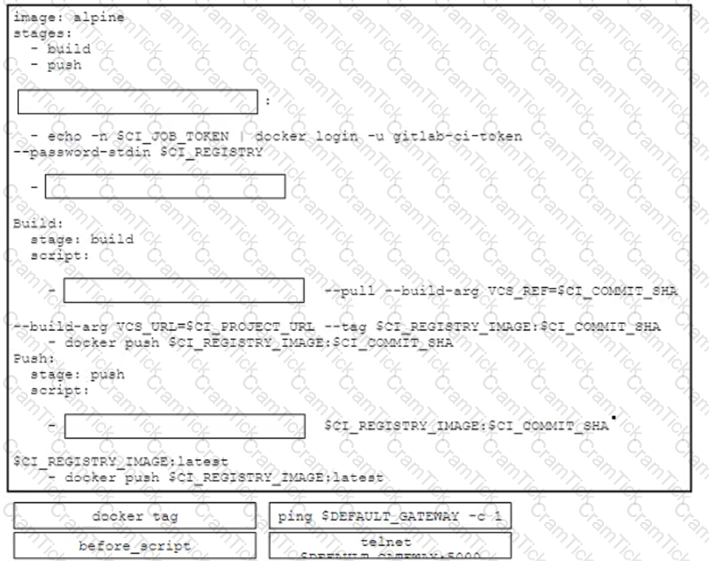
A DevOps engineer is designing a precheck validation of the network state in a CI/CD pipeline and must implement this workflow:
• Take a source Docker image named alpine
• Define two stages named build and push
• Check network connectivity before the stages run
• Fetch the latest Docker image
• Create a new Docker image and push it to the registry
• Tag the new Docker image as the latest version
Drag and drop the code snippets from the bottom onto the boxes in the GitLab CI configuration to achieve the requirements for the design. Not all options are used.
Which type of security testing should be performed as a part of a CI/CD pipeline by analyzing the source code itself without compiling the code into a running executable?
Cisco Certified DevNet Professional | 300-910 Written Exam | 300-910 Questions Answers | 300-910 Test Prep | 300-910 Cisco Certified DevNet Professional Actual Questions | Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS) Exam Questions PDF | Cisco Certified DevNet Professional Free Questions | 300-910 Online Exam | 300-910 Practice Test | 300-910 PDF | 300-910 Cisco Certified DevNet Professional Dumps | 300-910 Test Questions | 300-910 Study Material | 300-910 Exam Preparation | 300-910 Valid Dumps | 300-910 Real Questions | 300-910 Cisco Certified DevNet Professional Practice Test | Cisco Certified DevNet Professional 300-910 Dumps | Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS) Exam Questions


